Computing Curricula 2020 (CC2020)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Application for a Certificate of Eligibility to Employ Child Performers
Division of Labor Standards Permit and Certificate Unit Harriman State Office Campus Building 12, Room 185B Albany, NY 12240 www.labor.ny.gov Application for a Certificate of Eligibility to Employ Child Performers A. Submission Instructions A Certificate of Eligibility to Employ Child Performers must be obtained prior to employing any child performer. Certificates are renew able every three (3) years. To obtain or renew a certificate: • Complete Parts B, C, D and E of this application. • Attach proof of New York State Workers’ Compensation and Disability Insurance. o If you currently have employees in New York, you must provide proof of coverage for those New York State w orkers by attaching copies of Form C-105.2 and DB-120.1, obtainable from your insurance carrier. o If you are currently exempt from this requirement, complete Form CE-200 attesting that you are not required to obtain New York State Workers’ Compensation and Disability Insurance Coverage. Information on and copies of this form are available from any district office of the Workers’ Compensation Board or from their w ebsite at w ww.wcb.ny.gov, Click on “WC/DB Exemptions,” then click on “Request for WC/DB Exemptions.” • Attach a check for the correct amount from Section D, made payable to the Commissioner of Labor. • Sign and mail this completed application and all required documents to the address listed above. If you have any questions, call (518) 457-1942, email [email protected] or visit the Department’s w ebsite at w ww.labor.ny.gov B. Type of Request (check one) New Renew al Current certificate number _______________________________________________ Are you seeking this certificate to employ child models? Yes No C. -

Program #6: Word Count
CSc 227 — Program Design and Development Spring 2014 (McCann) http://www.cs.arizona.edu/classes/cs227/spring14/ Program #6: Word Count Due Date: March 11 th, 2014, at 9:00 p.m. MST Overview: The UNIX operating system (and its variants, of which Linux is one) includes quite a few useful utility programs. One of those is wc, which is short for Word Count. The purpose of wc is to give users an easy way to determine the size of a text file in terms of the number of lines, words, and bytes it contains. (It can do a bit more, but that’s all of the functionality that we are concerned with for this assignment.) Counting lines is done by looking for “end of line” characters (\n (ASCII 10) for UNIX text files, or the pair \r\n (ASCII 13 and 10) for Windows/DOS text files). Counting words is also straight–forward: Any sequence of characters not interrupted by “whitespace” (spaces, tabs, end–of–line characters) is a word. Of course, whitespace characters are characters, and need to be counted as such. A problem with wc is that it generates a very minimal output format. Here’s an example of what wc produces on a Linux system when asked to count the content of a pair of files; we can do better! $ wc prog6a.dat prog6b.dat 2 6 38 prog6a.dat 32 321 1883 prog6b.dat 34 327 1921 total Assignment: Write a Java program (completely documented according to the class documentation guidelines, of course) that counts lines, words, and bytes (characters) of text files. -

Data Quality Management in Large-Scale Cyber-Physical Systems
Data Quality Management in Large-Scale Cyber-Physical Systems Ahmed Abdulhasan Alwan School of Architecture, Computing and Engineering University of East London A thesis presented for the degree of Doctor of Philosophy July 19, 2021 Abstract Cyber-Physical Systems (CPSs) are cross-domain, multi-model, advance informa- tion systems that play a significant role in many large-scale infrastructure sectors of smart cities public services such as traffic control, smart transportation control, and environmental and noise monitoring systems. Such systems, typically, involve a substantial number of sensor nodes and other devices that stream and exchange data in real-time and usually are deployed in uncontrolled, broad environments. Thus, unexpected measurements may occur due to several internal and external factors, including noise, communication errors, and hardware failures, which may compromise these systems quality of data and raise serious concerns related to safety, reliability, performance, and security. In all cases, these unexpected measurements need to be carefully interpreted and managed based on domain knowledge and computational models. Therefore, in this research, data quality challenges were investigated, and a com- prehensive, proof of concept, data quality management system was developed to tackle unaddressed data quality challenges in large-scale CPSs. The data quality management system was designed to address data quality challenges associated with detecting: sensor nodes measurement errors, sensor nodes hardware failures, and mismatches in sensor nodes spatial and temporal contextual attributes. De- tecting sensor nodes measurement errors associated with the primary data quality dimensions of accuracy, timeliness, completeness, and consistency in large-scale CPSs were investigated using predictive and anomaly analysis models via utilising statistical and machine-learning techniques. -

A Comparison of Mechanisms for Improving TCP Performance Over Wireless Links
A Comparison of Mechanisms for Improving TCP Performance over Wireless Links Hari Balakrishnan, Venkata N. Padmanabhan, Srinivasan Seshan and Randy H. Katz1 {hari,padmanab,ss,randy}@cs.berkeley.edu Computer Science Division, Department of EECS, University of California at Berkeley Abstract the estimated round-trip delay and the mean linear deviation from it. The sender identifies the loss of a packet either by Reliable transport protocols such as TCP are tuned to per- the arrival of several duplicate cumulative acknowledg- form well in traditional networks where packet losses occur ments or the absence of an acknowledgment for the packet mostly because of congestion. However, networks with within a timeout interval equal to the sum of the smoothed wireless and other lossy links also suffer from significant round-trip delay and four times its mean deviation. TCP losses due to bit errors and handoffs. TCP responds to all reacts to packet losses by dropping its transmission (conges- losses by invoking congestion control and avoidance algo- tion) window size before retransmitting packets, initiating rithms, resulting in degraded end-to-end performance in congestion control or avoidance mechanisms (e.g., slow wireless and lossy systems. In this paper, we compare sev- start [13]) and backing off its retransmission timer (Karn’s eral schemes designed to improve the performance of TCP Algorithm [16]). These measures result in a reduction in the in such networks. We classify these schemes into three load on the intermediate links, thereby controlling the con- broad categories: end-to-end protocols, where loss recovery gestion in the network. is performed by the sender; link-layer protocols, that pro- vide local reliability; and split-connection protocols, that Unfortunately, when packets are lost in networks for rea- break the end-to-end connection into two parts at the base sons other than congestion, these measures result in an station. -

PDF Download
Table of Contents About ICSEC 2019 ................................................................................................................... I Message from President of Prince of Songkla University .................................................. III Message from Rector of University North, Croatia ............................................................ IV Message from General Chair ................................................................................................ VI Keynote Speakers ................................................................................................................. VII Organizing Committee .......................................................................................................... XI Conference Venue ............................................................................................................... XIII Program at a Glance ........................................................................................................... XVI Technical Sessions Main Track ............................................................................................................................. 1 Special Session on Advanced Digital Media ....................................................................... 33 Special Session on Future SDN: Security, Virtualization, Systems and Architectures ....... 35 Author Index .......................................................................................................................... 36 List of Reviewers -

Download The
LEADING THE FUTURE OF TECHNOLOGY 2016 ANNUAL REPORT TABLE OF CONTENTS 1 MESSAGE FROM THE IEEE PRESIDENT AND THE EXECUTIVE DIRECTOR 3 LEADING THE FUTURE OF TECHNOLOGY 5 GROWING GLOBAL AND INDUSTRY PARTNERSHIPS 11 ADVANCING TECHNOLOGY 17 INCREASING AWARENESS 23 AWARDING EXCELLENCE 29 EXPANSION AND OUTREACH 33 ELEVATING ENGAGEMENT 37 MESSAGE FROM THE TREASURER AND REPORT OF INDEPENDENT CERTIFIED PUBLIC ACCOUNTANTS 39 CONSOLIDATED FINANCIAL STATEMENTS Barry L. Shoop 2016 IEEE President and CEO IEEE Xplore® Digital Library to enable personalized importantly, we must be willing to rise again, learn experiences based on second-generation analytics. from our experiences, and advance. As our members drive ever-faster technological revolutions, each of us MESSAGE FROM As IEEE’s membership continues to grow must play a role in guaranteeing that our professional internationally, we have expanded our global presence society remains relevant, that it is as innovative as our THE IEEE PRESIDENT AND and engagement by opening offices in key geographic members are, and that it continues to evolve to meet locations around the world. In 2016, IEEE opened a the challenges of the ever-changing world around us. second office in China, due to growth in the country THE EXECUTIVE DIRECTOR and to better support engineers in Shenzhen, China’s From Big Data and Cloud Computing to Smart Grid, Silicon Valley. We expanded our office in Bangalore, Cybersecurity and our Brain Initiative, IEEE members India, and are preparing for the opening of a new IEEE are working across varied disciplines, pursuing Technology continues to be a transformative power We continue to make great strides in our efforts to office in Vienna, Austria. -

Lecture 8: Overview of Computer Networking Roadmap
Lecture 8: Overview of Computer Networking Slides adapted from those of Computer Networking: A Top Down Approach, 5th edition. Jim Kurose, Keith Ross, Addison-Wesley, April 2009. Roadmap ! what’s the Internet? ! network edge: hosts, access net ! network core: packet/circuit switching, Internet structure ! performance: loss, delay, throughput ! media distribution: UDP, TCP/IP 1 What’s the Internet: “nuts and bolts” view PC ! millions of connected Mobile network computing devices: server Global ISP hosts = end systems wireless laptop " running network apps cellular handheld Home network ! communication links Regional ISP " fiber, copper, radio, satellite access " points transmission rate = bandwidth Institutional network wired links ! routers: forward packets (chunks of router data) What’s the Internet: “nuts and bolts” view ! protocols control sending, receiving Mobile network of msgs Global ISP " e.g., TCP, IP, HTTP, Skype, Ethernet ! Internet: “network of networks” Home network " loosely hierarchical Regional ISP " public Internet versus private intranet Institutional network ! Internet standards " RFC: Request for comments " IETF: Internet Engineering Task Force 2 A closer look at network structure: ! network edge: applications and hosts ! access networks, physical media: wired, wireless communication links ! network core: " interconnected routers " network of networks The network edge: ! end systems (hosts): " run application programs " e.g. Web, email " at “edge of network” peer-peer ! client/server model " client host requests, receives -

Software Quality Management
Software Quality Management 2004-2005 Marco Scotto ([email protected]) Software Quality Management Contents ¾Definitions ¾Quality of the software product ¾Special features of software ¾ Early software quality models •Boehm model • McCall model ¾ Standard ISO 9126 Software Quality Management 2 Definitions ¾ Software: intellectual product consisting of information stored on a storage device (ISO/DIS 9000: 2000) • Software may occur as concepts, transactions, procedures. One example of software is a computer program • Software is "intellectual creation comprising the programs, procedures, rules and any associated documentation pertaining to the operation of a data processing system" •A software product is the "complete set of computer programs, procedures and associated documentation and data designated for delivery to a user" [ISO 9000-3] • Software is independent of the medium on which it is recorded Software Quality Management 3 Quality of the software product ¾The product should, on the highest level… • Ensure the satisfaction of the user needs • Ensure its proper use ¾ Earlier: 1 developer, 1 user • The program should run and produce results similar to those expected ¾ Later: more developers, more users • Need to economical use of the storage devices • Understandability, portability • User-friendliness, learnability ¾ Nowadays: • Efficiency, reliability, no errors, able to restart without using data Software Quality Management 4 Special features of software (1/6) ¾ Why is software ”different”? • Does not really have “physical” existence -

The Engineering Council 2002 to 2010
The Engineering Council 2002 to 2010 A Review by Andrew Ramsay MA CEng FCIS Contents Foreword 3 Prologue 5 The Early Days of ECUK 7 Year by Year 15 International Recognition 30 Annex A: Timeline 41 Annex B: SARTOR 3 42 Annex C: Incorporated Engineer Title – a Summary 44 Engineering Council Board 2002 to 2010 46 PEIs 2002 and 2010 48 List of Acronyms 49 Index 51 Acknowledgements 55 Page | 2 Foreword This review of the progress of the Engineering Council offers an inevitably personal view of issues, events and people who contributed to what must be judged as a successful period. However, while the Engineering Council is never itself going to be the UK engineering profession, it certainly moved towards a more central and less controversial position in its work and profile during this time. I am indebted to the detailed and lucid account of the earlier years of the Engineering Council written by Colin Chapman and Professor Jack Levy. Entitled Chronicle: An Engine for Change, this was published by the Engineering Council in 2004 and at the time of writing is still available on their website (shortcut link http://bit.ly/IY4ZLf ). However, for the shorter timeframe of this review I have adopted a less episodic structure than that of the Chronicle. It seemed to me that the extraordinary events that led up to creation of a “new regulatory body” in 2002, and in the 21 months that followed, deserved particular examination. Similarly, the way in which the Council was able to influence important developments in international recognition of UK-registered engineers can only really be understood in a continuous narrative – hence a separate section for this. -
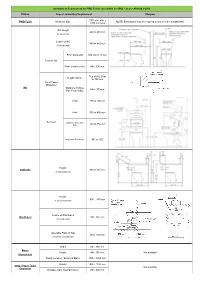
Summary of Requirement for PWD Toilets (Not Within an SOU) – As Per AS1428.1-2009
Summary of Requirement for PWD Toilets (not within an SOU) – as per AS1428.1-2009 Fixture Aspect and/or Key Requirement Diagram 1900 mm wide x PWD Toilet Minimum Size NOTE: Extra space may be required to allow for the a washbasin. 2300 mm long WC Height 460 to 480 mm (to top of seat) Centre of WC 450 to 460 mm (from side wall) From back wall 800 mm ± 10 mm Front of WC From cistern or like Min. 600 mm Top of WC Seat Height of Zone to 700 mm Toilet Paper Dispenser WC Distance of Zone Max. 300mm from Front of QC Height 150 to 200 mm Width 350 to 400 mm Backrest Distance above WC Seat 120 to 150 mm Angle from Seat Hinge 90° to 100° Height Grabrails 800 to 810 mm (to top of grab rail) Height 800 – 830 mm (to top of washbasin) Centre of Washbasin Washbasin Min. 425 mm (from side wall) Operable Parts of Tap Max. 300 mm (from front of washbasin) Width Min. 350 mm Mirror Height Min. 950 mm Not available (if provided) Fixing Location / Extent of Mirror 900 – 1850 mm Height 900 – 1100 mm Soap / Paper Towel Not available Dispenser Distance from Internal Corner Min. 500 mm Summary of Requirement for PWD Toilets (not within an SOU) – as per AS1428.1-2009 Fixture Aspect and/or Key Requirement Diagram Height 1200 – 1350 mm PWD Clothes Hook Not available Distance from Internal Corner Min. 500 mm Height 800 – 830 mm As vanity bench top Width Min. 120 mm Depth 300 – 400 mm Shelves Not available Height 900 – 1000 mm As separate fixture (if within any required Width 120 – 150 mm circulation space) Length 300 – 400 mm Width Min. -

2008 Cse Course List 56
It is CSE’s intention every year to make the Annual Report representative of the whole Department. With this ideal in mind, a design contest is held every year open to Graduate and Undergraduate students. This year’s winner was James Dickson, a junior CSE major who hails from Granville, Ohio. CONTENTS 2008 ACHIEVEMENT & HIGHLIGHTS 1 ANNUAL CSE DEPARTMENT AWARDS 11 INDUSTRIAL ADVISORY BOARD 12 RETIREMENT DOUBLE HIT 13 RESEARCH 14 GRANTS, AWARDS & GIFTS 19 COLLOQUIUM 27 STUDENTS 29 FaCULTY AND STAFF 38 SELECT FaCULTY PUBLICATIONS 49 2007 - 2008 CSE COURSE LIST 56 395 Dreese Labs 2015 Neil Avenue Columbus, Ohio 43210-1277 (614) 292-5813 WWW.CSE.OHIO-STATE.EDU i Mission Statement ± The Department of Computer Science and Engineering will impact the information age as a national leader in computing research and education. ± We will prepare computing graduates who are highly sought after, productive, and well-respected for their work, and who contribute to new developments in computing. ± We will give students in other disciplines an appropriate foundation in computing for their education, research, and experiences after graduation, consistent with computing’s increasingly fundamental role in society. ± In our areas of research focus, we will contribute key ideas to the development of the computing basis of the information age, advancing the state of the art for the benefit of society, the State of Ohio, and The Ohio State University. ± We will work with key academic partners within and outside of OSU, and with key industrial partners, in pursuit of our research and educational endeavors. ii GREETIN G S FROM THE CHAIR ’S OFFI C E Dear Colleges, Alumni, Friends, and Parents, As we reach the end of the 2007-2008 academic year, I am glad to introduce you a new annual report of the department. -

Adaptability Evaluation at Software Architecture Level Pentti Tarvainen*
The Open Software Engineering Journal, 2008, 2, 1-30 1 Open Access Adaptability Evaluation at Software Architecture Level Pentti Tarvainen* VTT Technical Research Centre of Finland, Kaitoväylä 1, P.O. Box 1100, FIN-90571 Oulu, Finland Abstract: Quality of software is one of the major issues in software intensive systems and it is important to analyze it as early as possible. An increasingly important quality attribute of complex software systems is adaptability. Software archi- tecture for adaptive software systems should be flexible enough to allow components to change their behaviors depending upon the environmental and stakeholders' changes and goals of the system. Evaluating adaptability at software architec- ture level to identify the weaknesses of the architecture and further to improve adaptability of the architecture are very important tasks for software architects today. Our contribution is an Adaptability Evaluation Method (AEM) that defines, before system implementation, how adaptability requirements can be negotiated and mapped to the architecture, how they can be represented in architectural models, and how the architecture can be evaluated and analyzed in order to validate whether or not the requirements are met. AEM fills the gap from requirements engineering to evaluation and provides an approach for adaptability evaluation at the software architecture level. In this paper AEM is described and validated with a real-world wireless environment control system. Furthermore, adaptability aspects, role of quality attributes, and diversity of adaptability definitions at software architecture level are discussed. Keywords: Adaptability, adaptation, adaptive software architecture, software quality, software quality attribute. INTRODUCTION understand the system [6]. Examples of design decisions are the decisions such as “we shall separate user interface from Today, quality of a software system plays an increasingly the rest of the application to make both user interface and important role in the domain of software engineering.