UFED6.4 Releasenotes EN.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

RADA Sense Mobile Application End-User Licence Agreement
RADA Sense Mobile Application End-User Licence Agreement PLEASE READ THESE LICENCE TERMS CAREFULLY BY CONTINUING TO USE THIS APP YOU AGREE TO THESE TERMS WHICH WILL BIND YOU. IF YOU DO NOT AGREE TO THESE TERMS, PLEASE IMMEDIATELY DISCONTINUE USING THIS APP. WHO WE ARE AND WHAT THIS AGREEMENT DOES We Kohler Mira Limited of Cromwell Road, Cheltenham, GL52 5EP license you to use: • Rada Sense mobile application software, the data supplied with the software, (App) and any updates or supplements to it. • The service you connect to via the App and the content we provide to you through it (Service). as permitted in these terms. YOUR PRIVACY Under data protection legislation, we are required to provide you with certain information about who we are, how we process your personal data and for what purposes and your rights in relation to your personal data and how to exercise them. This information is provided in https://www.radacontrols.com/en/privacy/ and it is important that you read that information. Please be aware that internet transmissions are never completely private or secure and that any message or information you send using the App or any Service may be read or intercepted by others, even if there is a special notice that a particular transmission is encrypted. APPLE APP STORE’S TERMS ALSO APPLY The ways in which you can use the App and Documentation may also be controlled by the Apple App Store’s rules and policies https://www.apple.com/uk/legal/internet-services/itunes/uk/terms.html and Apple App Store’s rules and policies will apply instead of these terms where there are differences between the two. -

Case: 1:19-Cv-00941 Document #: 87 Filed: 12/16/20 Page 1 of 31 Pageid #:2163
Case: 1:19-cv-00941 Document #: 87 Filed: 12/16/20 Page 1 of 31 PageID #:2163 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF ILLINOIS EASTERN DIVISION WI-LAN INC.; WI-LAN USA, INC.; & Civil Action No.: 1:19-cv-00941 WI-LAN LABS, INC., Judge John F. Kness Plaintiffs, Magistrate Judge Gabriel A. Fuentes vs. Jury Trial Demanded MOTOROLA MOBILITY LLC; & MOTOROLA MOBILITY HOLDINGS, LLC, Defendants. FIRST AMENDED COMPLAINT FOR PATENT INFRINGEMENT Plaintiffs Wi-LAN Inc., Wi-LAN USA, Inc., and Wi-LAN Labs, Inc. (collectively, “Wi- LAN”) hereby submit this First Amended Complaint against Defendants Motorola Mobility LLC and Motorola Mobility Holdings, LLC, (collectively, “Motorola” or “Defendants”). NATURE OF ACTION 1. This is an action for infringement of U.S. Patent Nos. 8,787,924 (“the ’924 Patent”) and 9,497,743 (“the ’743 Patent”) (collectively, the “patents-in-suit”). A true and correct copy of the ’924 Patent is attached as Exhibit A. A true and correct copy of the ’743 Patent is attached as Exhibit B. THE PARTIES 2. Plaintiff Wi-LAN Inc. is a corporation organized and existing under the laws of Canada, with a Canadian Corporation Number of 854057-8 and Business Number (BN) of 811594530RC0001, with its principal place of business at 1891 Robertson Road, Suite 100, Ottawa, ON, K2H 5B7, Canada. 3. Plaintiff Wi-LAN USA, Inc. is a corporation organized and existing under the laws Case: 1:19-cv-00941 Document #: 87 Filed: 12/16/20 Page 2 of 31 PageID #:2164 of Florida with its principal executive office at 1891 Robertson Road, Suite 100, Ottawa, ON, K2H 5B7, Canada, and a principal business office at 555 Anton Boulevard Suites 263 & 266, Costa Mesa, CA, 92626. -

MPP System Control Module User Guide /V1.0 Nulllindeni Nulllindeni Nulllindeni Nulllindeni Nulllindeni Nulllindeni Nulllindeni Nulllindeni
nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni MPP System Control Module User Guide /V1.0 nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni Document version:V1.0 Release Date:2017.4.13 nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni Copyright © Zhuhai Allwinner Technology Co., Ltd. 2018. All rights reserved. No part or all of the contents of this document may be copied or reproduced without the written permission of the company, and may not be used.What form of communication. nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni nulllindeni Trademark statement 、Allwinner and other Allwinner trademarks are trademarks of Zhuhai Allwinner Technology Co., Ltd.All other trademarks or registered trademarks mentioned in this document are the property of their respective owners. Note The products, services or features you purchase are subject to the terms and conditions of the company and all or part of the products, services or features described in this document may not be covered by your purchase or use. Unless otherwise agreed by the contract, Allwinner Company makes no representations or warranties, nulllindeni expressnulllindenior implied, regarnulllindeniding the contentsnulllindeniof this document.nulllindeni nulllindeni nulllindeni nulllindeni The contents of this document -

Appendix Contents
Appendix This appendix contains the textual transcripts of the fifty smartphone advertisements selected for the analysis. The smartphones are arranged in an alphabetical order and numbered in concord with the numbering of the advertisements used in the thesis. Contents Appendix .................................................................................................................................... 1 1 Acer Liquid Z220 commercial ......................................................................................... 4 2 Acer Liquid Z520 commercial ......................................................................................... 4 3 Alcatel Onetouch Idol 2 S commercial ............................................................................ 5 4 ALCATEL ONETOUCH PIXI 3 Family commercial ................................................... 6 5 ARCHOS Helium Plus commercial ................................................................................. 8 6 ASUS ZenFone 2 and ZenFone Zoom commercial ........................................................ 9 7 ASUS ZenFone Max commercial ................................................................................... 10 8 BlackBerry Classic commercial ..................................................................................... 12 9 BlackBerry PRIV commercial ....................................................................................... 13 10 BLU Life Pure Mini commercial ................................................................................ -

Detective 11.0 October 2018
OXYGEN FORENSIC® DETECTIVE 11.0 OCTOBER 2018 USE NEW WHATSAPP EXTRACTION METHOD AQCUIRE IOT DEVICES WhatsApp is without doubt the most popular messenger Digital assistants are already a part of everyday life and in the world with over 1.5 billion users globally. Thus, have been successfully used to solve several crimes. extracting complete WhatsApp content from all possible Oxygen Forensic® Detective v.11 brings support for the sources is essential for any investigation. two most popular digital assistants – Amazon Alexa and Google Home. Commonly used methods of WhatsApp data acquisition involve extracting data from mobile devices and their You can access Amazon Alexa cloud using a username cloud backups. Oxygen Forensic® Detective v.11 and password or token. A token can be found on the introduces an industry-first alternative method of device’s associated computer with Oxygen Forensic® WhatsApp data extraction. KeyScout and used in Cloud Extractor. The software acquires a complete evidence set from Amazon Alexa, In the new software version, you can access complete including account and device details, contacts, messages, WhatsApp data by scanning a QR code from a mobile calendars, notifications, lists, activities, skills, etc. app or using the WhatsApp token from a PC. This token can be extracted by our KeyScout utility from the Google Home data can be extracted via Google WhatsApp desktop app or from desktop Web browsers. username/password or a master token found in mobile devices. Extracted Google Home data includes account Once data is extracted, you will be able to download and device details, voice commands, and information WhatsApp communications from the subject’s account about users.Google Home data can also be acquired from any time later when an investigation requires by using a the Google Home mobile app on Apple iOS and Android specially generated WhatsApp QR token available in the devices. -

Firefox OS Overview Ewa Janczukowicz
Firefox OS Overview Ewa Janczukowicz To cite this version: Ewa Janczukowicz. Firefox OS Overview. [Research Report] Télécom Bretagne. 2013, pp.28. hal- 00961321 HAL Id: hal-00961321 https://hal.archives-ouvertes.fr/hal-00961321 Submitted on 24 Apr 2014 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Collection des rapports de recherche de Télécom Bretagne RR-2013-04-RSM Firefox OS Overview Ewa JANCZUKOWICZ (Télécom Bretagne) This work is part of the project " Étude des APIs Mozilla Firefox OS" supported by Orange Labs / TC PASS (CRE API MOZILLA FIREFOX OS - CTNG13025) ACKNOWLEGMENTS Above all, I would like to thank Ahmed Bouabdallah and Arnaud Braud for their assistance, support and guidance throughout the contract. I am very grateful to Gaël Fromentoux and Stéphane Tuffin for giving me the possibility of working on the Firefox OS project. I would like to show my gratitude to Jean-Marie Bonnin, to all members of Orange NCA/ARC team and RSM department for their help and guidance. RR-2013-04-RSM 1 RR-2013-04-RSM 2 SUMMARY Firefox OS is an operating system for mobile devices such as smartphones and tablets. -

Google Nexus 6P (H1512) Google Nexus 7
GPSMAP 276Cx Google Google Nexus 5X (H791) Google Nexus 6P (H1512) Google Nexus 7 Google Nexus 6 HTC HTC One (M7) HTC One (M9) HTC One (M10) HTC One (M8) HTC One (A9) HTC Butterfly S LG LG V10 H962 LG G3 Titan LG G5 H860 LG E988 Gpro LG G4 H815 Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Samsung Samsung Galaxy Note 2 Samsung Galaxy S4 Active Samsung Galaxy S6 edge + (SM-G9287) Samsung Galaxy Note 3 Samsung Galaxy S5 Samsung Galaxy S7 edge (SM- G935FD) Samsung Galaxy Note 4 Samsung Galaxy S5 Active Samsung GALAXY J Samsung Galaxy Note 5 (SM- Samsung Galaxy S5 Mini Samsung Galaxy A5 Duos N9208) Samsung Galaxy S3 Samsung Galaxy S6 Samsung Galaxy A9 (SM- A9000) Samsung Galaxy S4 Sony Sony Ericsson Xperia Z Sony Xperia Z3 Sony Xperia X Sony Ericsson Xperia Z Ultra Sony Xperia Z3 Compact Sony XPERIA Z5 Sony Xperia Z2 Sony XPERIA E1 Asus ASUS Zenfone 2 ASUS Zenfone 5 ASUS Zenfone 6 Huawei HUAWEI P8 HUAWEI M100 HUAWEI P9 HUAWEI CRR_L09 XIAOMI XIAOMI 2S XIAOMI 3 XIAOMI 5 XIAOMI Note GPSMAP 64s Google Google Nexus 4 Google Nexus 6P (H1512) Google Pixel Google Nexus 6 Google Nexus 7 HTC HTC One (M7) HTC One (A9) HTC Butterfly S HTC One (M8) HTC One (M10) HTC U11 HTC One (M9) LG LG Flex LG E988 Gpro LG G5 H860 LG V10 H962 LG G4 H815 LG G6 H870 Motorola Motorola RAZR M Motorola DROID Turbo Motorola Moto G (2st Gen) Motorola Droid MAXX Motorola Moto G (1st Gen) Motorola Moto Z Samsung Samsung Galaxy Note 2 Samsung Galaxy S5 Samsung Galaxy J5 Samsung Galaxy Note 3 Samsung Galaxy -
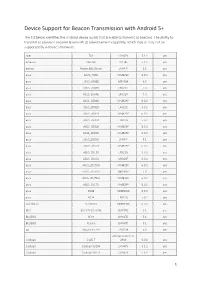
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Motorola Moto G User Guide
Available applications and services are subject to change at any time. Table of Contents Get Started 1 Your Phone at a Glance 1 Charge Your Phone Battery 1 Activation and Service 3 Complete the Setup Screens 3 Set Up Voicemail 5 Retrieve Data from Your Old Phone 5 Phone Basics 7 Your Phone’s Layout 7 Turn Your Phone On and Off 8 Turn Your Screen On and Off 9 Adjust the Sound Volume 10 Find Your Phone Number 11 Touchscreen Navigation 11 Your Home Screen 11 Status Bar 13 Active Notifications 14 App List 14 Search 15 Google Now 16 Motorola Assist 16 Enter Text 17 Touchscreen Keyboard 17 Text Entry Settings and Dictionary 19 Tips for Editing Text 19 Voice Typing 20 Phone Calls 21 Make Phone Calls 21 Call Using the Phone Dialer 21 Call from History 22 Call from Contacts 22 Call a Number in a Text Message or Email Message 23 Call from Favorites 23 i Call Emergency Numbers 23 Receive Phone Calls 24 Voicemail 25 Retrieve Your Voicemail Messages 25 Visual Voicemail 25 Set Up Visual Voicemail 26 Review Visual Voicemail 26 Visual Voicemail Settings 28 Change Your Main Greeting via the Voicemail Menu 29 Edit the Display Name via the Voicemail Menu 29 Phone Call Options 29 Make a 3-Way Call 30 Contacts 31 Get Started with Contacts 31 Add a Contact 32 Save a Phone Number 32 Edit a Contact 32 Sync or Transfer Contacts 33 Call or Text Contacts 33 Make Groups 33 Accounts and Messaging 35 Gmail and Google 35 Email 37 Add an Email Account 38 Compose and Send Email 38 Delete an Email Account 40 Text and Multimedia Messaging 40 Send a Text Message 40 Send -

Vehicle Phone Scout Feature *
llPROTECTED 関係者外秘 Summary of Scout Compatible Phones The summary on this page includes recently released phones that support Scout application in Entune App Suite. Some phones also support additional features. Please refer to the following pages for a Complete List of Phones tested to date and their detailed compatibility test results for Scout application. Vehicle Phone Scout Feature Vehicle Head Unit Carrier Manufacturer Model Operating System Turn by Turn only Full Navigation iPhone 6 plus iOS 11.3,11.4 iPhone 7 iOS 11.3 iPhone 7 plus iOS 11.3 iPhone 8 plus iOS 11.3 Apple iPhone 8 Plus iOS 11.4 iPhone SE iOS 11.3 iPhone X iOS 11.4 Iphone X iOS 12 * * Google Pixel Android 8.0,8.1 LG V35 ThinQ Android 8.0 Entune Plus with Scout Toyota Camry 2018 AT&T Moto G6 Play Android 8.0 Motorola Nexus 6 Android 7.1.1 Galaxy J3 Android 8.0 Galaxy J7 Android 8.0 Galaxy Note 8 Android 7.1.1, 8.0 Galaxy Note 9 Android 8.1 Samsung Galaxy S8 Active Android 7.0 Galaxy S8 plus Android 8.0 Galaxy S8 Android 8.0 Galaxy S9 Android 8.0 Galaxy S9+ Android 8.0 Sonim XP8 Android 7.0 * For iOS 12, Lagging issues are observed while using various functions of the Scout App Last Updated: Oct 2018 This list represents the phones that have been tested for compatibility with Entune App Suite features to date. Test results are valid as of the date noted, using the specified versions of the Head Unit, App Suite and Operating Systems. -

In the United States District Court for the District of Delaware
Case 1:17-cv-01081-UNA Document 1 Filed 08/03/17 Page 1 of 22 PageID #: 1 IN THE UNITED STATES DISTRICT COURT FOR THE DISTRICT OF DELAWARE IMMERSION CORPORATION, Plaintiff, v. Civil Action No. MOTOROLA MOBILITY LLC and DEMAND FOR JURY TRIAL MOTOROLA MOBILITY HOLDINGS LLC, Defendants. COMPLAINT FOR PATENT INFRINGEMENT Immersion Corporation (“Immersion”) brings this action against Motorola Mobility LLC (“Motorola Mobility”) and Motorola Mobility Holdings LLC (“Motorola Holdings”) (collectively, “Motorola”), and alleges as follows: NATURE OF THE ACTION 1. This action is based on Motorola’s infringement of several patents developed and owned by Immersion, sometimes referred to as “basic haptics” patents, covering Motorola’s use of haptic feedback technology (“haptic feedback”) in mobile devices. For many years, Motorola had paid for a license to use Immersion’s patent portfolio. Although Motorola decided not to renew its patent license with Immersion when it expired in November 2015, Motorola did not stop using the haptic feedback technology covered by the patents. Despite its continuing use of Immersion’s patented technology, Motorola has declined to enter into a new license agreement Case 1:17-cv-01081-UNA Document 1 Filed 08/03/17 Page 2 of 22 PageID #: 2 with Immersion. 2. The patents at issue (collectively, the “Asserted Patents”) are U.S. Patent Nos. 6,429,846 (“the ’846 patent”), 7,969,288 (“the ’288 patent”), 7,982,720 (“the ’720 patent”), 8,031,181 (“the ’181 patent”), and 9,323,332 (“the ’332 patent”). All except the ’332 patent were specifically identified in the previous patent license. -

Release Notes UFED Ultimate, UFED Infield, UFED Physical Analyzer
Release Notes UFED Ultimate, UFED InField, UFED Physical Analyzer, UFED Logical Analyzer & Cellebrite Reader February 2019 Now supporting: 27,785 device profiles App versions: 7,596 Forensic methods v. 7.15 Total Logical extraction 135 11,088 Physical extraction* 140 6,757 File system extraction 137 6,709 Extract/disable user lock 232 3,231 Total 644 27,785 *Including GPS devices The number of unique mobile devices with passcode capabilities is 5,216 HIGHLIGHTS App support • Now supporting deleted data from the WeChat application for Android devices. • 149 updated application versions for iOS and Android devices. Release Notes | UFED Ultimate, UFED InField, UFED Physical Analyzer, UFED Logical Analyzer & Cellebrite Reader | February 2019 | www.cellebrite.com Release Notes Industry first: Samsung Exynos physical bypass solution As Cellebrite continues to pioneer the world of mobile device extractions, we are the first vendor in the industry to provide a generic solution to access Samsung devices with the Exynos processor. This new decrypting bootloader capability enables unlock, full file system and physical extractions from a vast range of Samsung devices, popular around the world. Together with the support for Samsung Qualcomm devices, Cellebrite is the only vendor to provide a holistic solution to unlock and extract data from Samsung devices. Supported devices include: SM-G930F Galaxy S7, SM-G935F Galaxy S7 Edge, SM- A520F Galaxy A5 2017 and SM-J730F Galaxy J7 Pro. Get to evidence faster with Selective Extraction When time is of the essence, and decisions need to be made quickly, examiners can use the new Selective Extraction capability to perform fast and focused extractions.