Lessons in Grid Computing : the System Is a Mirror / Stuart Robbins
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

COMIC BOOKS AS AMERICAN PROPAGANDA DURING WORLD WAR II a Master's Thesis Presented to College of Arts & Sciences Departmen
COMIC BOOKS AS AMERICAN PROPAGANDA DURING WORLD WAR II A Master’s Thesis Presented To College of Arts & Sciences Department of Communications and Humanities _______________________________ In Partial Fulfillment of the Requirements for the Master of Science Degree _______________________________ SUNY Polytechnic Institute By David Dellecese May 2018 © 2018 David Dellecese Approval Page SUNY Polytechnic Institute DEPARTMENT OF COMMUNICATIONS AND HUMANITIES INFORMATION DESIGN AND TECHNOLOGY MS PROGRAM Approved and recommended for acceptance as a thesis in partial fulfillment of the requirements for the degree of Master of Science in Information Design + Technology. _________________________ DATE ________________________________________ Kathryn Stam Thesis Advisor ________________________________________ Ryan Lizardi Second Reader ________________________________________ Russell Kahn Instructor 1 ABSTRACT American comic books were a relatively, but quite popular form of media during the years of World War II. Amid a limited media landscape that otherwise consisted of radio, film, newspaper, and magazines, comics served as a useful tool in engaging readers of all ages to get behind the war effort. The aims of this research was to examine a sampling of messages put forth by comic book publishers before and after American involvement in World War II in the form of fictional comic book stories. In this research, it is found that comic book storytelling/messaging reflected a theme of American isolation prior to U.S. involvement in the war, but changed its tone to become a strong proponent for American involvement post-the bombing of Pearl Harbor. This came in numerous forms, from vilification of America’s enemies in the stories of super heroics, the use of scrap, rubber, paper, or bond drives back on the homefront to provide resources on the frontlines, to a general sense of patriotism. -
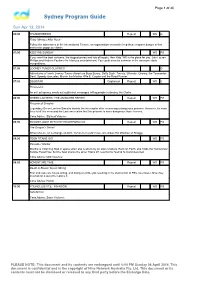
Sydney Program Guide
Page 1 of 40 Sydney Program Guide Sun Apr 13, 2014 06:00 THUNDERBIRDS Repeat WS G Thirty Minutes After Noon Follow the adventures of the International Rescue, an organisation created to help those in grave danger in this marionette puppetry classic. 07:00 KIDS' WB SUNDAY WS PG If you want the best cartoons, the biggest prizes and lots of laughs, then Kids’ WB is the place for you. Join Lauren Phillips and Andrew Faulkner for hilarious entertainment. You could even be a winner in the awesome daily competitions. 07:05 LOONEY TUNES CLASSICS G Adventures of iconic Looney Tunes characters Bugs Bunny, Daffy Duck, Tweety, Silvester, Granny, the Tasmanian Devil, Speedy Gonzales, Marvin the Martian Wile E. Coyote and the Road Runner. 07:30 DOGSTAR Captioned Repeat WS C Persuasion An evil ad agency sends out subliminal messages telling people to destroy the Clarks. 08:00 GREEN LANTERN: THE ANIMATED SERIES Repeat WS PG Prisoner of Sinestro Legendary Green Lantern Sinestro boards the interceptor after recovering a dangerous prisoner. However, he soon tries to kill the crew and the Lanterns realize that the prisoner is more dangerous than it seems. Cons.Advice: Stylised Violence 08:30 SCOOBY-DOO! MYSTERY INCORPORATED Repeat WS PG The Dragon's Secret When Mi-Lee, an exchange student, comes to Crystal Cove, she draws the affection of Shaggy. 09:00 TEEN TITANS GO! WS PG Parasite / Starliar Starfire is collecting food in space when she is struck by an alien creature. Back on Earth, she holds the Tamaranian holiday Feast Day, but the food scares the other Titans off, leaving her feeling hurt and dejected Cons.Advice: Mild Violence 09:30 ADVENTURE TIME Repeat WS PG Death in Bloom/ Susan Strong Finn and Jake are house sitting, and doing a terrible job resulting in the destruction of PB's rare flower. -

Planner Grafton Says Department Behind the Times
Holiday gift guide inside this week's NewArk Post Chrysler may lay off 1,700 /2a · State playoffs open /lh Vol. 76, No. 73 November 11, 1987 Newark, Del. COVER STORY Planner Grafton says department behind the times by Cathy Thomas '' We're not . ~Nture New Castle County is boom ing. Houses are springing up at enough as an · ~ every turn, business construc tion is running apace and silhouetted against the skyline to be a role-model are nearly as many cranes as trees. II Trying to cope with this un paralleled growth is a planning to get in vogue with contem department still in its infancy. porary planning programs. That is the assessment of "I don't mean we need to be on Wayne Grafton, New Castle the cutting edge. We need to County's planning director, who have codes and ordinances that readily admits to a reputation are at least cognizant of contem for causing a ripple. porary planning principles." ·· · rom where 1 sit, we've Grafton stepped into the rQle made marvelous strides," says of New Castle county's planning Grafton, "and, yet, it's not director three years ago. enough." "Administratively, this place Grafton doesn't expect the was a mess." According to Graf county to "pull itself out of the ton, employees in the depart- woods" for another three or four Salem Woods is just one of many new developments being constructed in New Castle County. years. He would like the county See GRAFTON/12a Purzycki: Plan Comprehen~ive· plan must he specific out by year's end If the new comprehensive plan for New Castle Coun The much-awaited com posals now before the Delaware ty refers to lofty, sentimental goals, then it's not doing prehensive plan for New Castle legislature. -

GREEN LANTERN (Alan Scott)
GREEN LANTERN (Alan Scott) Serie dedicata alla 1° Lanterna Verde nata nel Settembre del 1941 e proseguita per 38 numeri, fino a Ottobre del 1949. 1) Masquerading Mare! (Finger/Nodell) (11/41- Protagonista Lanterna Verde [Alan Scott]) Disease!! (Finger/Nodell) (Protagonista Lanterna Verde [Alan Scott]) Arson in the Slums (Finger/Nodell) (Protagonista Lanterna Verde [Alan Scott]) Green Lantern in South America (Finger/Nodell) (Protagonista Lanterna Verde [Alan Scott]) 2) The Tycoon's Legacy (Finger/Nodell) (12/41- Protagonista Lanterna Verde [Alan Scott]) 3) The Living Graveyard of the Sea (Finger/Nodell) (03/42- Protagonista Lanterna Verde [Alan Scott]) 4) Green Lantern and Doiby Join the Army part I-II-III-IV (Finger/Nodell) (06/42- Protagonista Lanterna Verde [Alan Scott]) 5) The Legion of the Lantern (Finger/Nodell) (09/42- Protagonista Lanterna Verde [Alan Scott]) 6) Empire of Exiles (Greene/Nodell) (12/42- Protagonista Lanterna Verde [Alan Scott]) 7) The Wizard of Odds (Greene/Nodell) (03/43- Protagonista Lanterna Verde [Alan Scott]) 8) The Lady and Her Jewels (Greene/Nodell) (09/43- Protagonista Lanterna Verde [Alan Scott]) A Lease On Life (Finger/Nodell) (Protagonista Lanterna Verde [Alan Scott]) Company General Use 9) The School for Vandals (Bester/Nodell) (10/43- Protagonista Lanterna Verde [Alan Scott]) 10) The Man Who Wanted the World (Bester/Nodell) (12/43- Protagonista Lanterna Verde [Alan Scott]) Doiby Dickles' Dismal Discovery (Bester/Nodell) (Protagonista Lanterna Verde [Alan Scott]) 11) The Dastardly Designs of Doiby Dickles -

Dec. 2012 $10.95
D e c . 2 0 1 2 No.61 $10.95 Legion of Super-Heroes TM & © DC Comics. All Rights Reserved. Rights All Comics. DC © & TM Super-Heroes of Legion Volume 1, Number 61 December 2012 EDITOR-IN- CHIEF Michael Eury Comics’ Bronze Age and Beyond! PUBLISHER John Morrow DESIGNER Rich Fowlks COVER ARTIST Alex Ross COVER DESIGNER Michael Kronenberg PROOFREADER FLASHBACK: The Perils of the DC/Marvel Tabloid Era . .1 Rob Smentek Pitfalls of the super-size format, plus tantalizing tabloid trivia SPECIAL THANKS BEYOND CAPES: You Know Dasher and Dancer: Rudolph the Red-Nosed Rein- Jack Abramowitz Dan Jurgens deer . .7 Neal Adams Rob Kelly and The comics comeback of Santa and the most famous reindeer of all Erin Andrews TreasuryComics.com FLASHBACK: The Amazing World of Superman Tabloids . .11 Mark Arnold Joe Kubert A planned amusement park, two movie specials, and your key to the Fortress Terry Austin Paul Levitz Jerry Boyd Andy Mangels BEYOND CAPES: DC Comics’ The Bible . .17 Rich Bryant Jon Mankuta Kubert and Infantino recall DC’s adaptation of the most spectacular tales ever told Glen Cadigan Chris Marshall FLASHBACK: The Kids in the Hall (of Justice): Super Friends . .24 Leslie Carbaga Steven Morger A whirlwind tour of the Super Friends tabloid, with Alex Toth art Comic Book Artist John Morrow Gerry Conway Thomas Powers BEYOND CAPES: The Secrets of Oz Revealed . .29 DC Comics Alex Ross The first Marvel/DC co-publishing project and its magical Marvel follow-up Paul Dini Bob Rozakis FLASHBACK: Tabloid Team-Ups . .33 Mark Evanier Zack Smith The giant-size DC/Marvel crossovers and their legacy Jim Ford Bob Soron Chris Franklin Roy Thomas INDEX: Bronze Age Tabloids Checklist . -

No.61 2 1 0 2
D e c . 2 0 1 2 No.61 $10.95 Legion of Super-Heroes TM & © DC Comics. All Rights Reserved. Rights All Comics. DC © & TM Super-Heroes of Legion Volume 1, Number 61 December 2012 EDITOR-IN- CHIEF Michael Eury Comics’ Bronze Age and Beyond! PUBLISHER John Morrow DESIGNER Rich Fowlks COVER ARTIST Alex Ross COVER DESIGNER Michael Kronenberg PROOFREADER FLASHBACK: The Perils of the DC/Marvel Tabloid Era . .1 Rob Smentek Pitfalls of the super-size format, plus tantalizing tabloid trivia SPECIAL THANKS BEYOND CAPES: You Know Dasher and Dancer: Rudolph the Red-Nosed Rein- Jack Abramowitz Dan Jurgens deer . .7 Neal Adams Rob Kelly and The comics comeback of Santa and the most famous reindeer of all Erin Andrews TreasuryComics.com FLASHBACK: The Amazing World of Superman Tabloids . .11 Mark Arnold Joe Kubert A planned amusement park, two movie specials, and your key to the Fortress Terry Austin Paul Levitz Jerry Boyd Andy Mangels BEYOND CAPES: DC Comics’ The Bible . .17 Rich Bryant Jon Mankuta Kubert and Infantino recall DC’s adaptation of the most spectacular tales ever told Glen Cadigan Chris Marshall FLASHBACK: The Kids in the Hall (of Justice): Super Friends . .24 Leslie Carbaga Steven Morger A whirlwind tour of the Super Friends tabloid, with Alex Toth art Comic Book Artist John Morrow Gerry Conway Thomas Powers BEYOND CAPES: The Secrets of Oz Revealed . .29 DC Comics Alex Ross The first Marvel/DC co-publishing project and its magical Marvel follow-up Paul Dini Bob Rozakis FLASHBACK: Tabloid Team-Ups . .33 Mark Evanier Zack Smith The giant-size DC/Marvel crossovers and their legacy Jim Ford Bob Soron Chris Franklin Roy Thomas INDEX: Bronze Age Tabloids Checklist . -

The Metacomics of Alan Moore, Neil Gaiman, and Warren Ellis
University of Alberta Telling Stories About Storytelling: The Metacomics of Alan Moore, Neil Gaiman, and Warren Ellis by Orion Ussner Kidder A thesis submitted to the Faculty of Graduate Studies and Research in partial fulfilment of the requirements for the degree of Doctor of Philosophy in English Department of English and Film Studies ©Orion Ussner Kidder Spring 2010 Edmonton, Alberta Permission is hereby granted to the University of Alberta Libraries to reproduce single copies of this thesis and to lend or sell such copies for private, scholarly or scientific research purposes only. Where the thesis is converted to, or otherwise made available in digital form, the University of Alberta will advise potential users of the thesis of these terms. The author reserves all other publication and other rights in association with the copyright in the thesis and, except as herein before provided, neither the thesis nor any substantial portion thereof may be printed or otherwise reproduced in any material form whatsoever without the author's prior written permission. Library and Archives Bibliothèque et Canada Archives Canada Published Heritage Direction du Branch Patrimoine de l’édition 395 Wellington Street 395, rue Wellington Ottawa ON K1A 0N4 Ottawa ON K1A 0N4 Canada Canada Your file Votre référence ISBN: 978-0-494-60022-1 Our file Notre référence ISBN: 978-0-494-60022-1 NOTICE: AVIS: The author has granted a non- L’auteur a accordé une licence non exclusive exclusive license allowing Library and permettant à la Bibliothèque et Archives Archives Canada to reproduce, Canada de reproduire, publier, archiver, publish, archive, preserve, conserve, sauvegarder, conserver, transmettre au public communicate to the public by par télécommunication ou par l’Internet, prêter, telecommunication or on the Internet, distribuer et vendre des thèses partout dans le loan, distribute and sell theses monde, à des fins commerciales ou autres, sur worldwide, for commercial or non- support microforme, papier, électronique et/ou commercial purposes, in microform, autres formats. -
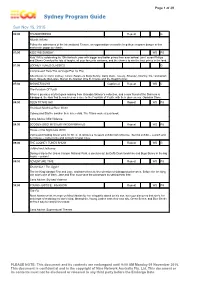
Sydney Program Guide
Page 1 of 39 Sydney Program Guide Sun Nov 15, 2015 06:00 THUNDERBIRDS Repeat G Atlantic Inferno Follow the adventures of the International Rescue, an organisation created to help those in grave danger in this marionette puppetry classic. 07:00 KIDS' WB SUNDAY WS PG Kids’ WB is celebrating its 10th fantastic year with bigger and better prizes than ever before! Join Lauren Phillips and Shane Crawford for lots of laughs, all your favourite cartoons, and the chance to win the best prizes in the land. 07:05 LOONEY TUNES CLASSICS G Compressed Hare/The Jet Cage/Pop 'im Pop Adventures of iconic Looney Tunes characters Bugs Bunny, Daffy Duck, Tweety, Silvester, Granny, the Tasmanian Devil, Speedy Gonzales, Marvin the Martian Wile E. Coyote and the Road Runner. 07:30 SKINNER BOYS Captioned Repeat WS C The Fountain Of Youth When a precious artefact goes missing from Grandpa Skinner’s collection, and a new friend of the Skinners is kidnapped, the kids find themselves on a race to the Fountain of Youth, with their uber-enemy, Obsidian Stone. 08:00 TEEN TITANS GO! Repeat WS PG Yearbook Madness/Hose Water Cyborg and Starfire awaken their inner child. The Titans make a year book. Cons.Advice: Mild Violence 08:30 SCOOBY-DOO! MYSTERY INCORPORATED Repeat WS PG House of the Nightmare Witch Velma and Hotdog Water work for Mr. E. to retrieve a museum exhibit from Moscow. But the exhibit -- a witch and her house -- come to life and torment Crystal Cove. 09:00 THE LOONEY TUNES SHOW Repeat WS G Jailbird and Jailbunny During a trip to the Grand Canyon National Park, a careless act by Daffy Duck lands him and Bugs Bunny in the big house -- prison! 09:30 ADVENTURE TIME Repeat WS PG Enchiridion / The Jiggler The Ice King kidnaps Finn and Jake, and takes them to his collection of kidnapped princesses. -

Extensions of Remarks E687 EXTENSIONS of REMARKS
May 3, 2002 CONGRESSIONAL RECORD — Extensions of Remarks E687 EXTENSIONS OF REMARKS HONORING GENERAL THOMAS A. leader at every level with prior experience in David March. Our thoughts and prayers are SCHWARTZ ON HIS RETIREMENT Korea that will serve both our nations well.’’ with his family as we remember his heroic General Shelton’s faith in General Schwartz service to our community and our nation. HON. DAVID L. HOBSON was well placed, as his command history has f demonstrated. OF OHIO NAFTA IN THE HOUSE OF REPRESENTATIVES No truly effective leader can ever make it to a position of prominence without assistance. Wednesday, May 1, 2002 General Schwartz has been aided every step HON. NICK J. RAHALL II Mr. HOBSON. Mr. Speaker, I rise today to of the way by his wife Sandy. Together, the OF WEST VIRGINIA honor General Thomas A. Schwartz, the out- Schwartz’ have made a formidable team in IN THE HOUSE OF REPRESENTATIVES going Commander of United States Forces in their efforts to quality of military life in Korea. Wednesday, May 1, 2002 Korea, and to share my hearty congratulations On behalf of all of the soldiers who have on his well-deserved retirement after 35 years served under his command and the United Mr. RAHALL. Mr. Speaker, I want to submit of distinguished service to our country in the States Congress, I thank General Schwartz for for the record an editorial from ‘‘The Logan United States Army. all he has done. We are going to miss the ex- Banner’’ about another West Virginia company A native of St. -

The Eternal Green Lantern
Roy Tho mas ’ Mean & Green Comics Fan zine GREEN GROW THE LANTTEERRNNSS $7.95 NODELL, KANE, In the USA & THE CREATION OF A No.102 LEGEND— TIMES TWO! June 2011 06 1 82658 27763 5 Green Lantern art TM & ©2011 DC Comics Vol. 3, No. 102 / June 2011 Editor Roy Thomas Associate Editors Bill Schelly Jim Amash Design & Layout Christopher Day Consulting Editor John Morrow FCA Editor P.C. Hamerlinck Comic Crypt Editor TH Michael T. Gilbert NOW WI Editorial Honor Roll 16 PAGES Jerry G. Bails (founder) R! Ronn Foss, Biljo White OF COLO Mike Friedrich Proofreader Rob Smentek Cover Artists Mart Nodell, Gil Kane, & Terry Austin Contents Cover Colorists Writer/Editorial – “Caught In The Creative Act” . 2 Mart Nodell & Tom Ziuko The Eternal Green Lantern . 3 With Special Thanks to: Will Murray’s overview of the Emerald Gladiators of two comic book Ages. Heidi Amash Bob Hughes Henry Andrews Sean Howe “Marty Created ‘The Green Lantern’!” . 15 Finn Andreen Betty Tokar Jankovich Ger Apeldoorn Robert Kennedy Mart & Carrie Nodell interviewed about GL and other wonders by Shel Dorf. Terry Austin David Anthony Kraft Bob Bailey R. Gary Land “Life’s Not Over Yet!” . 31 Mike W. Barr Jim Ludwig Jim Beard Monroe Mayer Jack Mendelsohn on his comics and animation work (part 2), with Jim Amash. John Benson Jack Mendelsohn Jared Bond Raymond Miller Bob & Betty—& Archie & Betty . 44 Dominic Bongo Ken Moldoff An interview with the woman who probably inspired Betty Cooper—conducted by Shaun Clancy. Wendy Gaines Bucci Shelly Moldoff Mike Burkey Lynn Montana Glen Cadigan Brian K. -

Gothic Genesis 6.5 MB
Mythos #3 Winter, 2019 In the beginning…Bob created the Batman. But, Batman was battle against the evil forces of society…his identity remains un- unformed and unfinished. And so, Bob brought his new creation known.” 2 This was a basic detective murder mystery thriller, in to his writer-friend Bill, who looked upon Batman and pondered which Batman tracked down a corporate criminal named Alfred the potential and possibilities of what could be. Bill suggested Stryker, who schemed to murder his two partners in the Apex Majestic and grandiose are the two terms by which I would Batman truly was. Like the Dark Knight, his influential and some adjustments and alterations inspired by the bat motif, Chemical Corporation before he would have to buy them out. personally describe the remarkable talent of maestro scribe, inspiring work has been mantled in the mists of mystery and which Bob incorporated into Batman’s unique and uncanny In the climatic scene, Batman punched Stryker so powerfully Gardner Francis Fox. For the most part, his life, his vast myth since the genesis of the character. For Gardner was image. Bob and Bill looked upon their collaborative effort and that the blow caused him to break through the protective railing mind-boggling body of work, and perhaps most importantly right there, front and center from nearly the very beginning, behold, Batman was very good! Bob presented Batman to and fall into a tank of acid. Finger’s second effort in Detec- of all, his immeasurable influence upon the wild and wacky taking over the script writing duties from Bill Finger as early as DC Comics’ senior editor Vincent A. -

Justice Society America!
Roy Thomas’ Star-Bedecked $ Comics Fanzine JUST WHEN YOU THOUGHT 8.95 YOU KNEW EVERYTHING THERE In the USA WAS TO KNOW ABOUT THE No.109 May JUSTICE 2012 SOCIETY ofAMERICA!™ 5 0 5 3 6 7 7 2 8 5 Art © DC Comics; Justice Society of America TM & © 2012 DC Comics. 6 Plus: SPECTRE & HOUR-MAN 2 8 Co-Creator 1 BERNARD BAILY Vol. 3, No. 109 / April 2012 Editor Roy Thomas Associate Editors Bill Schelly Jim Amash Design & Layout Jon B. Cooke Consulting Editor John Morrow FCA Editor AST! P.C. Hamerlinck AT L Comic Crypt Editor ALL IN Michael T. Gilbert FOR Editorial Honor Roll COLOR $8.95! Jerry G. Bails (founder) Ronn Foss, Biljo White Mike Friedrich Proofreader Rob Smentek Cover Artist Contents George Pérez Writer/Editorial: An All-Star Cast—Of Mind . 2 Cover Colorist Bernard Baily: The Early Years . 3 Tom Ziuko With Special Thanks to: Ken Quattro examines the career of the artist who co-created The Spectre and Hour-Man. “Fairytales Can Come True…” . 17 Rob Allen Roger Hill The Roy Thomas/Michael Bair 1980s JSA retro-series that didn’t quite happen! Heidi Amash Allan Holtz Dave Armstrong Carmine Infantino What If All-Star Comics Had Sported A Variant Line-up? . 25 Amy Baily William B. Jones, Jr. Eugene Baily Jim Kealy Hurricane Heeran imagines different 1940s JSA memberships—and rivals! Jill Baily Kirk Kimball “Will” Power . 33 Regina Baily Paul Levitz Stephen Baily Mark Lewis Pages from that legendary “lost” Golden Age JSA epic—in color for the first time ever! Michael Bair Bob Lubbers “I Absolutely Love What I’m Doing!” .