Paper, We Propose the Bigram and Uni- and Semantic Similar
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Semantic Shift, Homonyms, Synonyms and Auto-Antonyms
WALIA journal 31(S3): 81-85, 2015 Available online at www.Waliaj.com ISSN 1026-3861 © 2015 WALIA Semantic shift, homonyms, synonyms and auto-antonyms Fatemeh Rahmati * PhD Student, Department of Arab Literature, Islamic Azad University, Central Tehran Branch; Tehran, Iran Abstract: One of the important topics in linguistics relates to the words and their meanings. Words of each language have specific meanings, which are originally assigned to them by the builder of that language. However, the truth is that such meanings are not fixed, and may evolve over time. Language is like a living being, which evolves and develops over its lifetime. Therefore, there must be conditions which cause the meaning of the words to change, to disappear over time, or to be signified by new signifiers as the time passes. In some cases, a term may have two or more meanings, which meanings can be different from or even opposite to each other. Also, the semantic field of a word may be expanded, so that it becomes synonymous with more words. This paper tried to discuss the diversity of the meanings of the words. Key words: Word; Semantic shift; Homonym; Synonym; Auto-antonym 1. Introduction person who employed had had the intention to express this sentence. When a word is said in *Speaking of the language immediately brings the absence of intent to convey a meaning, it doesn’t words and meanings immediately to mind, because signify any meaning, and is meaningless, as are the they are two essential elements of the language. words uttered by a parrot. -

Automatic Labeling of Troponymy for Chinese Verbs
Automatic labeling of troponymy for Chinese verbs 羅巧Ê Chiao-Shan Lo*+ s!蓉 Yi-Rung Chen+ [email protected] [email protected] 林芝Q Chih-Yu Lin+ 謝舒ñ Shu-Kai Hsieh*+ [email protected] [email protected] *Lab of Linguistic Ontology, Language Processing and e-Humanities, +Graduate School of English/Linguistics, National Taiwan Normal University Abstract 以同©^Æ與^Y語意關¶Ë而成的^Y知X«,如ñ語^² (Wordnet)、P語^ ² (EuroWordnet)I,已有E分的研v,^²的úË_已øv完善。ú¼ø同的目的,- 研b語言@¦已úË'規!K-文^Y²路 (Chinese Wordnet,CWN),è(Ð供完t的 -文YK^©@分。6而,(目MK-文^Y²路ûq-,1¼目M;要/¡(ºº$ 定來標記同©^ÆK間的語意關Â,因d這些標記KxÏ尚*T成可L應(K一定規!。 因d,,Ç文章y%針對動^K間的上下M^Y語意關 (Troponymy),Ðú一.ê動標 記的¹法。我們希望藉1句法上y定的句型 (lexical syntactic pattern),úË一個能 ê 動½取ú動^上下M的ûq。透N^©意$定原G的U0,P果o:,dûqê動½取ú 的動^上M^,cº率將近~分K七A。,研v盼能將,¹法應(¼c(|U-的-文^ ²ê動語意關Â標記,以Ê知X,體Kê動úË,2而能有H率的úË完善的-文^Y知 XÇ源。 關關關uuu^^^:-文^Y²路、語©關Âê動標記、動^^Y語© Abstract Synset and semantic relation based lexical knowledge base such as wordnet, have been well-studied and constructed in English and other European languages (EuroWordnet). The Chinese wordnet (CWN) has been launched by Academia Sinica basing on the similar paradigm. The synset that each word sense locates in CWN are manually labeled, how- ever, the lexical semantic relations among synsets are not fully constructed yet. In this present paper, we try to propose a lexical pattern-based algorithm which can automatically discover the semantic relations among verbs, especially the troponymy relation. There are many ways that the structure of a language can indicate the meaning of lexical items. For Chinese verbs, we identify two sets of lexical syntactic patterns denoting the concept of hypernymy-troponymy relation. -

Applied Linguistics Unit III
Applied Linguistics Unit III D ISCOURSE AND VOCABUL ARY We cannot deny the fact that vocabulary is one of the most important components of any language to be learnt. The place we give vocabulary in a class can still be discourse-oriented. Most of us will agree that vocabulary should be taught in context, the challenge we may encounter with this way of approaching teaching is that the word ‘context’ is a rather catch-all term and what we need to do at this point is to look at some of the specific relationships between vocabulary choice, context (in the sense of the situation in which the discourse is produced) and co-text (the actual text surrounding any given lexical item). Lexical cohesion As we have seen in Discourse Analysis, related vocabulary items occur across clause and sentence boundaries in written texts and across act, move, and turn boundaries in speech and are a major characteristic of coherent discourse. Do you remember which were those relationships in texts we studied last Semester? We call them Formal links or cohesive devices and they are: verb form, parallelism, referring expressions, repetition and lexical chains, substitution and ellipsis. Some of these are grammatical cohesive devices, like Reference, Substitution and Ellipsis; some others are Lexical Cohesive devices, like Repetition, and lexical chains (such us Synonymy, Antonymy, Meronymy etc.) Why should we study all this? Well, we are not suggesting exploiting them just because they are there, but only because we can give our learners meaningful, controlled practice and the hope of improving them with more varied contexts for using and practicing vocabulary. -

Lexical Semantics
Lexical Semantics COMP-599 Oct 20, 2015 Outline Semantics Lexical semantics Lexical semantic relations WordNet Word Sense Disambiguation • Lesk algorithm • Yarowsky’s algorithm 2 Semantics The study of meaning in language What does meaning mean? • Relationship of linguistic expression to the real world • Relationship of linguistic expressions to each other Let’s start by focusing on the meaning of words— lexical semantics. Later on: • meaning of phrases and sentences • how to construct that from meanings of words 3 From Language to the World What does telephone mean? • Picks out all of the objects in the world that are telephones (its referents) Its extensional definition not telephones telephones 4 Relationship of Linguistic Expressions How would you define telephone? e.g, to a three-year- old, or to a friendly Martian. 5 Dictionary Definition http://dictionary.reference.com/browse/telephone Its intensional definition • The necessary and sufficient conditions to be a telephone This presupposes you know what “apparatus”, “sound”, “speech”, etc. mean. 6 Sense and Reference (Frege, 1892) Frege was one of the first to distinguish between the sense of a term, and its reference. Same referent, different senses: Venus the morning star the evening star 7 Lexical Semantic Relations How specifically do terms relate to each other? Here are some ways: Hypernymy/hyponymy Synonymy Antonymy Homonymy Polysemy Metonymy Synecdoche Holonymy/meronymy 8 Hypernymy/Hyponymy ISA relationship Hyponym Hypernym monkey mammal Montreal city red wine beverage 9 Synonymy and Antonymy Synonymy (Roughly) same meaning offspring descendent spawn happy joyful merry Antonymy (Roughly) opposite meaning synonym antonym happy sad descendant ancestor 10 Homonymy Same form, different (and unrelated) meaning Homophone – same sound • e.g., son vs. -

Classification of Entailment Relations in PPDB
Classification of Entailment Relations in PPDB CHAPTER 5. ENTAILMENT RELATIONS 71 CHAPTER 5. ENTAILMENT RELATIONS 71 R0000 R0001 R0010 R0011 CHAPTER 5. ENTAILMENT RELATIONS CHAPTER 5. ENTAILMENT71 RELATIONS 71 1 Overview equivalence synonym negation antonym R0100 R0101 R0110 R0000R0111 R0001 R0010 R0011 couch able un- This document outlines our protocol for labeling sofa able R0000 R0001 R0010 R0000R0011 R0001 R0010 R0011 R R R R R R R R noun pairs according to the entailment relations pro- 1000 1001 1010 01001011 0101 0110 0111 R R R R R R R R posed by Bill MacCartney in his 2009 thesis on Nat- 0100 0101 0110 01000111 0101 0110 0111 R1100 R1101 R1110 R1000R1111 R1001 R1010 R1011 CHAPTER 5. ENTAILMENT RELATIONS 71 ural Language Inference. Our purpose of doing this forward entailment hyponymy alternation shared hypernym Figure 5.2: The 16 elementary set relations, represented by Johnston diagrams. Each box represents the universe U, and the two circles within the box represent the sets R1000 R1001 R1010 R1000R1011 R1001 R1010 R1011 x and y. A region is white if it is empty, and shaded if it is non-empty. Thus in the carni is to build a labelled data set with which to train a R1100 R1101 R1110 R1111 bird vore CHAPTER 5. ENTAILMENT RELATIONSdiagram labeled R1101,onlytheregionx y is empty,71 indicating that x y U. \ ;⇢ ⇢ ⇢ Figure 5.2: The 16 elementary set relations, represented by Johnston diagrams. Each classifier for differentiating between these relations. R0000 R0001 R0010 R0011 feline box represents the universe U, and the two circles within the box represent the setscanine equivalence classR1100 in which onlyR partition1101 10 is empty.)R1110 These equivalenceR1100R1111 classes areR1101 R1110 R1111 x and y. -

Automatic Text Simplification Via Synonym Replacement
LIU-IDA/KOGVET-A{12/014{SE Linkoping¨ University Master Thesis Automatic Text Simplification via Synonym Replacement by Robin Keskis¨arkk¨a Supervisor: Arne J¨onsson Dept. of Computer and Information Science at Link¨oping University Examinor: Sture H¨agglund Dept. of Computer and Information Science at Link¨oping University Abstract In this study automatic lexical simplification via synonym replacement in Swedish was investigated using three different strategies for choosing alternative synonyms: based on word frequency, based on word length, and based on level of synonymy. These strategies were evaluated in terms of standardized readability metrics for Swedish, average word length, pro- portion of long words, and in relation to the ratio of errors (type A) and number of replacements. The effect of replacements on different genres of texts was also examined. The results show that replacement based on word frequency and word length can improve readability in terms of established metrics for Swedish texts for all genres but that the risk of introducing errors is high. Attempts were made at identifying criteria thresholds that would decrease the ratio of errors but no general thresh- olds could be identified. In a final experiment word frequency and level of synonymy were combined using predefined thresholds. When more than one word passed the thresholds word frequency or level of synonymy was prioritized. The strategy was significantly better than word frequency alone when looking at all texts and prioritizing level of synonymy. Both prioritizing frequency and level of synonymy were significantly better for the newspaper texts. The results indicate that synonym replacement on a one-to-one word level is very likely to produce errors. -

COMPARATIVE FUNCTIONAL ANALYSIS of SYNONYMS in the ENGLISH and UZBEK LANGUAGE Nazokat Rustamova Master Student of Uzbekistan
ACADEMIC RESEARCH IN EDUCATIONAL SCIENCES VOLUME 2 | ISSUE 6 | 2021 ISSN: 2181-1385 Scientific Journal Impact Factor (SJIF) 2021: 5.723 DOI: 10.24412/2181-1385-2021-6-528-533 COMPARATIVE FUNCTIONAL ANALYSIS OF SYNONYMS IN THE ENGLISH AND UZBEK LANGUAGE Nazokat Rustamova Master student of Uzbekistan State University of World Languages (Supervisor: Munavvar Kayumova) ABSTRACT This article is devoted to the meaningfulness of lexical-semantic relationships. Polysemic lexemes were studied in the synonymy seme and synonyms of sememe which are derived from the meaning of grammar and polysememic lexemes. Synonymic sememes and synonyms are from lexical synonyms. The grammatical synonyms, context synonyms, complete synonyms, the spiritual synonyms, methodological synonyms as well as grammar and lexical units within polysememic lexemes have been studied. Keywords: Synonymic affixes, Lexical synonyms, Meaningful (semantic) synonyms, Contextual synonymy, Full synonymy, Traditional synonyms, Stylistic synonyms. INTRODUCTION With the help of this article we pay a great attention in order to examine the meaningfulness of lexical-semantic relationships. Polysemic lexemes were studied in the synonymy seme and synonyms of sememe which are derived from the meaning of grammar and polysememic lexemes. Synonymic sememes and synonyms are from lexical synonyms. The grammatical synonyms, context synonyms, complete synonyms, the spiritual synonyms, methodological synonyms as well as grammar and lexical units within polysememic lexemes have been studied. There are examples of meaningful words and meaningful additions, to grammatical synonyms. Lexical synonyms and affixes synonyms are derived from linguistics unit. Syntactic synonyms have been studied in terms of the combinations of words, fixed connections and phrases.[1] The synonym semes are divided into several types depending on the lexical, meaning the morpheme composition the grammatical meaning of the semantic space, the syntactic relationship and the synonym syllabus based on this classification. -

Automatic Synonym Discovery with Knowledge Bases
Automatic Synonym Discovery with Knowledge Bases Meng Xiang Ren Jiawei Han University of Illinois University of Illinois University of Illinois at Urbana-Champaign at Urbana-Champaign at Urbana-Champaign [email protected] [email protected] [email protected] ABSTRACT Text Corpus Synonym Seeds Recognizing entity synonyms from text has become a crucial task in ID Sentence Cancer 1 Washington is a state in the Pacific Northwest region. Cancer, Cancers many entity-leveraging applications. However, discovering entity 2 Washington served as the first President of the US. e.g. Washington State synonyms from domain-specic text corpora ( , news articles, 3 The exact cause of leukemia is unknown. Washington State, State of Washington scientic papers) is rather challenging. Current systems take an 4 Cancer involves abnormal cell growth. entity name string as input to nd out other names that are syn- onymous, ignoring the fact that oen times a name string can refer to multiple entities (e.g., “apple” could refer to both Apple Inc and Cancer George Washington Washington State Leukemia the fruit apple). Moreover, most existing methods require training data manually created by domain experts to construct supervised- learning systems. In this paper, we study the problem of automatic Entities Knowledge Bases synonym discovery with knowledge bases, that is, identifying syn- Figure 1: Distant supervision for synonym discovery. We onyms for knowledge base entities in a given domain-specic corpus. link entity mentions in text corpus to knowledge base enti- e manually-curated synonyms for each entity stored in a knowl- ties, and collect training seeds from knowledge bases. edge base not only form a set of name strings to disambiguate the meaning for each other, but also can serve as “distant” supervision to help determine important features for the task. -
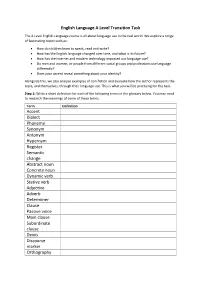
English Language a Level Transition Task Accent Dialect Phoneme
English Language A Level Transition Task The A Level English Language course is all about language use in the real world. We explore a range of fascinating topics such as: • How do children learn to speak, read and write? • How has the English language changed over time, and what is its future? • How has the internet and modern technology impacted our language use? • Do men and women, or people from different social groups and professions use language differently? • Does your accent reveal something about your identity? Alongside this, we also analyse examples of non-fiction and evaluate how the author represents the topic, and themselves, through their language use. This is what you will be practising for this task. Step 1: Write a short definition for each of the following terms in the glossary below. You may need to research the meanings of some of these terms. Term Definition Accent Dialect Phoneme Synonym Antonym Hypernym Register Semantic change Abstract noun Concrete noun Dynamic verb Stative verb Adjective Adverb Determiner Clause Passive voice Main clause Subordinate clause Deixis Discourse marker Orthography Step 2: For part of the examination, you will be asked to analyse a text, thinking about how the language and layout presents the author and the topic of the text. Read through the example annotations below. Step 3: Read the article below from The Washington Post, January 7th 2021, then annotate it with anything you notice about how the language presents the event. You can use the tips in the box below: Think about how Tips: -

Sample Morpheme Walls
Sample Morpheme Walls Wall with Basic Morphemes Word + Word = Compound Word house sun light dog time where houseboat sunlight moonlight lapdog sometime somewhere townhouse sunset lighthouse dogcatcher timekeeper nowhere housemate sunrise flashlight dogsled timepiece anywhere doghouse sunglasses lightweight watchdog lifetime whereabouts Word + Word – Letter(s) + Apostrophe = Contraction -n’t -‘re -‘s -‘ve -‘ll -‘d (not) (are) (is or has) (have) (will) (would or had) isn’t you’re it's I’ve I’ll I’d haven’t they’re that’s you’ve you’ll you’d won’t we’re he’s they’ve she’ll he’d shouldn’t who’re what’s would’ve we’ll they’d Inflectional Endings -s -es -ed -ing -er -est (plural) (plural) (past tense) (present tense) (more) (most) bags foxes wanted sending greater greatest trees benches added running hotter hottest friends bushes walked making riper ripest choices buses yelled flying sunnier sunniest Prefixes un- re- pre- dis- over- mis- (not) (again) (before) (not, opposite of) (too much) (wrongly) unhappy redo preview dislike overheat mistake unsure replay preheat disagree overeat misunderstand unfair remake prefix dishonest overdo misread unable reopen preset disappear overwork misbehave Suffixes -ful -less -ly -er -able -ness (adj., full of) (adj., (adv., how an (noun, one who (adj., capable (noun, quality) without) action is done) does something) of) hopeful hopeless quickly teacher teachable kindness fearful fearless sadly worker readable fairness effortful effortless suddenly runner agreeable sadness successful homeless perfectly faker -

Synonymy and Its Features
4th Global Congress on Contemporary Sciences & Advancements 30th April, 2021 Hosted online from Rome, Italy econferecegloble.com SYNONYMY AND ITS FEATURES Safoyeva Sadokat Nasilloyevna Teacher of the Department of ESP for Humanitarian Sciences, Foreign Languages Faculty, Bukhara State University ABSTARCT The grouping of language units based on the same meaning is called synonymy. Firstly, synonymy is born on the basis of the semantic relationship of two or more language units. The number of units involved in such an approach cannot be limited. Secondly, these language units form a regular system within themselves. Given these properties, the units of language that form a synonymous relationship are called synonymous with one another. Synonyms are collectively referred to as a series of synonyms. Synonymy exists in both lexical units and grammatical units. Accordingly, there are two types of synonyms: 1. Lexical synonymy is the mutual synonymy of lexical units: for example, Heaven, future state, eternal blessedness, eternity, Paradise, Eden, promised land, Golden Age, Utopia, Millennium. 2. Grammatical synonymy is the synonym of grammatical units Lexical synonymy is manifested in three ways: 1. Lexical synonymy is the mutual synonymy of lexical units: cunning, crafty, deceitful, underhand, roguish, mischievous… .. 2. Phraseological synonymy - the mutual synonym of phraseological units: Between a rock and a hard place. Between the devil and the deep Blue Sea, in a bind. 3. Lexical phraseological synonymy - the interaction of a phraseological unit with a lecture unit The grouping of lexemes based on the same meaning is called lexical synonymy. For example, ridiculous, ridiculous, proposterous lexemes have the same meaning. It is not to be understood that lexical units have the same meaning as equivalents in meaning. -

Foundational Literacy Glossary of Terms
Foundational Literacy Glossary of Terms Accuracy The ability to recognize words correctly Advanced Phonics Strategies for decoding multisyllabic words that include morphology and information about the meaning, pronunciation, and parts of speech of words gained from knowledge of prefixes, roots, and suffixes Affixes Affixes are word parts that are "fixed to" either the beginnings of words (prefixes) or the endings of words (suffixes). The word disrespectful has two affixes, a prefix (dis-) and a suffix (-ful) Alphabetic Awareness Knowledge of letters of the alphabet coupled with the understanding that the alphabet represents the sounds of spoken language and the correspondence of spoken sounds to written language Alphabetic Code Sound-symbol relationships to recognize words Alphabetic Principle The concept that letters and letter combinations represent individual phonemes in written words Alphabetic Understanding Understanding that the left-to-right spellings of printed words represent their phonemes from first to last Automaticity The ability to translate letters-to-sounds-to-words fluently, effortlessly Base Word A unit of meaning that can stand alone as a whole word (e.g., friend, pig). Also called a free morpheme. Also called a free morpheme Blend A blend is a consonant sequence before or after a vowel within a syllable, such as cl, br, or st; it is the written language equivalent of consonant cluster Blending The task of combining sounds rapidly to accurately represent the word Chunking A decoding strategy for separating words into