1. All of the Following Are Examples of Input Devices Except Which One of the Following? A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

END USER COMPUTING - NETWORK ATTACHED PRINTER SUPPORT Effective JULY 1, 2020
END USER COMPUTING - NETWORK ATTACHED PRINTER SUPPORT Effective JULY 1, 2020 SUPPORT OVERVIEW The OTS approach for providing services and support for all State technology is to utilize Lines of Service as a mechanism to adequately and appropriately recover the cost of operations related to each of the services. In order to further standardize EUC support operations as a line of service, network attached printers must be counted as a supported and managed device included in the Enterprise Device Support line of service. The EUC Enterprise Device Support rate of $60 per device per month is being applied to all purchased or legacy out of warranty network attached printers to cover the cost of the initial setup and ongoing operational management and support requirements. The EUC Network Copier and Warrantied Printer Support rate of $30 per device per month is being applied to all network based copiers and printers that are either rented through the Office of State Procurement copier contract or have an active service agreement or warranty with a third party provider. This service is applied to cover the EUC related support costs at a reduced rate to account for services already provided directly through the copier rental vendor or printer warranty vendor. WHAT IS INCLUDED Every network attached printer and copier requires EUC support throughout the lifecycle of the device. The line of service rate provides for the following services: · Initial device setup on the network · Initial device setup on the OTS print server · Installation -

An Isometric Joystick As a Pointing Device for Handheld Information Terminals
An Isometric Joystick as a Pointing Device for Handheld Information Terminals Miika Silfverberg I. Scott MacKenzie Tatu Kauppinen Usability Group Department of Computer Science Usability Group Nokia Research Center, Finland York University, Canada Nokia Research Center, Finland Abstract embedded pointing device that is suitable for handheld Meeting the increasing demand for desktop-like appli- use. This work studies the applicability of the isometric cations on mobile products requires powerful interac- joystick to handheld usage. tion techniques. One candidate is GUI-style point-and- click interaction using an integrated pointing device 1.1 Isometric Joystick that supports handheld use. We tested an isometric joy- A joystick is a good candidate for handheld pointing. stick for this purpose. Two prototypes were built. They Since it is mounted in the device chassis, it cannot be were designed for thumb operation and included a sepa- lost, unlike a stylus. It is small and can be manipulated rate selection button. Twelve participants performed potentially with the same hand that holds the device. point-and-select tasks. We tested both one-handed and two-handed interaction, and selection using the separate The device studied herein is an isometric joystick. The selection button and the joystick’s integrated press-to- pointer is moved by applying force to the stick. The select feature. A notebook configuration served as a stick itself doesn't move, or moves very little – hence reference. Results for the handheld conditions, both the name "isometric". The most common input-output one-handed and two-handed, were just slightly off those mapping is known as “velocity-control”, whereby the for the notebook condition, suggesting that an isometric applied force controls the velocity of the pointer. -

Evans, Gareth; Blenkhorn, Paul a Head Operated Joystick
DOCUMENT RESUME ED 430 330 EC 307 177 AUTHOR Evans, Gareth; Blenkhorn, Paul TITLE A Head Operated Joystick--Experience with Use. PUB DATE 1999-03-00 NOTE 6p. PUB TYPE Reports Descriptive (141) EDRS PRICE MF01/PC01 Plus Postage. DESCRIPTORS *Accessibility (for Disabled); *Assistive Devices (for Disabled); *Input Output Devices; *Severe Disabilities; Use Studies IDENTIFIERS *Joysticks ABSTRACT This paper describes the development and evaluation of a low-cost head-operated joystick for computer users with disabilities that prevent them from using a conventional hand-operated computer mouse and/or keyboard. The paper focuses on three issues: first, the style of head movement required by the device; second, whether a head-operated device should work as an absolute positioning device or as a joystick; and, third, the accuracy required by the device. It finds that the device's "nose following" style of head movement is more accepted by users than alternatives; that users also preferred the joystick relative pointing device over absolute positioning devices; and that users did not notice inaccuracies inherent in the device's design, thus allowing production at a lower cost. (DB) ******************************************************************************** Reproductions supplied by EDRS are the best that can be made from the original document. ******************************************************************************** PERMISSION TO REPRODUCE AND DISSEMINATE THIS MATERIAL HAS ert BEEN GRANTED BY r1) el") EXPERIENCE WITHUSE ans A HEADOPERATEDJOYSTICK - TO THE EDUCATIONAL RESOURCES INFORMATION CENTER (ERIC) Gareth Evans and PaulBlenkhorn 1 Manchester, UK, [email protected] of Computation, UMIST, Technology for DisabledPeople Unit, Department Introduction computer mouse and/orkeyboard, may use a head- Computer users who cannot use aconventional hand-operated computer and, by using anon-screen keyboard, totype operated mouse or joystickin order to control their user's head movements aretranslated into mouse pointer information. -

Writing with a Joystick: a Comparison of Date Stamp, Selection Keyboard, and Edgewrite Jacob O
Writing with a Joystick: A Comparison of Date Stamp, Selection Keyboard, and EdgeWrite Jacob O. Wobbrock, Brad A. Myers and Htet Htet Aung Human-Computer Interaction Institute School of Computer Science Carnegie Mellon University Pittsburgh, Pennsylvania, USA {jrock, bam, hha}@cs.cmu.edu http://www.cs.cmu.edu/~edgewrite/ Abstract A joystick text entry method for game controllers and mobile phones would be valuable, since these devices often have joysticks but no conventional keyboards. But prevalent joystick text entry methods are slow because they are selection-based. EdgeWrite, a new joystick text entry method, is not based on selection but on gestures from a unistroke alphabet. Our experiment shows that this new method is faster, leaves fewer errors, and is more satisfying than date stamp and selection keyboard (two prevalent Figure 1. The Saitek P2500 Rumble Force Pad. Our experiment selection-based methods) for novices after minimal used the two thumbsticks and one of the silver buttons. practice. For more practiced users, our results show that EdgeWrite is at least 1.5 times faster than selection messenger-style text. With only selection-based text entry keyboard, and 2.4 times faster than date stamp. methods for game controllers, this can be awkward. Keywords: Text entry, text input, joystick, game controller, Mobile devices have also placed high demands on text game console, physical edges, corners, gestures, unistrokes. entry development. Numerous text entry methods have been investigated, including those driven by buttons, character 1 Introduction – Why Joystick Text Entry? recognition, virtual keyboards, thumbwheels, and voice. Joysticks have served as input devices since the earliest Many new handheld devices, such as the Ericsson T68i computers [7]. -

Android Based Area Web Monitoring
EPJ Web of Conferences 68, 00002 (2014) DOI: 10.1051/epjconf/20146800002 C Owned by the authors, published by EDP Sciences, 2014 Android Based Area Web Monitoring Bayu Kanigoro, Afan Galih Salman, Jurike V Moniaga, Eric Chandra, and Zein Rezky Chandra Computer Science Program, School of Computer Science, Bina Nusantara University, Indonesia Abstract. The research objective is to develop an application that can be used in the monitoring of an area by using a webcam. It aims to create a sense of security on the user's application because it can monitor an area using mobile phone anywhere. The results obtained in this study is to create an area with a webcam monitoring application that can be accessed anywhere as long as the monitoring results have internet access and can also be accessed through Android Based Mobile Phone. 1 Introduction 2 Recent Works In the era of globalization, developments in information There are some discussions about web monitoring. technology plays an important role in various sectors of Details of the development of a simple webcam joystick, human life and mobile phone is a main actor in this era. a wireless, or rather cable less, and contactless pointing When it was becomes popular around 1990, it was only device by using a webcam and a simple flexible non- be used for voice communication between persons but electronic joystick for recording patient movement has now it has a very sophisticated ability which formerly been described in [1]. could only be done by computers which can be done by An efficient Omni directional surveillance system for mobile phone today which is known by the wider digital home security was proposed in [5]. -

HP Engage One Serial USB Thermal Printer
QuickSpecs HP Engage One Serial USB Thermal Printer Overview HP Engage One Serial USB Thermal Printer Model HP Engage One Serial USB Thermal Printer (Black) 1RL96AA HP Engage One Serial USB Thermal Printer (White) 3GS19AA Introduction Redefine your perception of retail printing with the HP Engage One Serial USB Thermal Printer, an eye-catching, compact, cubist printer designed to dazzle alongside your HP Engage One AiO System at the point of sale. Key Features and Benefits • Print quickly with 114 mm per second print speed and 8 MB of integrated memory. Add your logo, special offers or coupons to receipts with 203 DPI and fonts that include Unicode, Arabic, and Asian. • Connect to your retail system with an optional USB, PUSB or Serial cable kit (sold separately), and drive up to two optional cash drawers through connections on the printer. • Place the ultra-compact printer where you need it with the assurance that the internal steel frame can withstand the everyday wear and tear of retail environments. Compatibility The HP Engage One Serial USB Thermal Printer is compatible with the HP Engage One AiO Systems. NOTE: Not all Point of Sale system models are available in all regions. Not all HP Cash Drawer models are available in all regions. This printer does not comply with fiscalization requirements that may be required in certain countries. Service and Support Three (3) year limited warranty with advance exchange when purchased from HP. c05573122 —16010 Worldwide — Version 6 — October 2, 2019 Page 1 QuickSpecs HP Engage One Serial USB -

Mobile Print/Scan Guide for Brother Iprint&Scan
Mobile Print/Scan Guide for Brother iPrint&Scan Version D ENG Definitions of notes We use the following icon throughout this user’s guide: Notes tell you how you should respond to a situation that may arise or give Note tips about how the operation works with other features. Trademarks The Brother logo is a registered trademark of Brother Industries, Ltd. Android is a trademark of Google Inc. Apple, Macintosh, Mac OS, iCloud, iPhone, iPod touch, iPad and Safari are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft and Windows are registered trademarks of Microsoft Corporation in the United States and/or other countries. Each company whose software title is mentioned in this manual has a Software License Agreement specific to its proprietary programs. Any trade names and product names of companies appearing on Brother products, related documents and any other materials are all trademarks or registered trademarks of those respective companies. ©2011 Brother Industries, Ltd. All rights reserved. i Table of Contents Section I For Android™ Devices 1 Introduction 2 Overview....................................................................................................................................................2 Hardware requirement...............................................................................................................................3 Supported operating systems..............................................................................................................3 Network settings..................................................................................................................................3 -
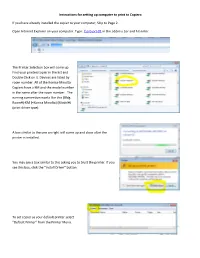
Instructions for Setting up Computer to Print to Copiers
Instructions for setting up computer to print to Copiers: If you have already installed the copier to your computer, Skip to Page 2. Open Internet Explorer on your computer. Type: \\csb-prt-01 in the address bar and hit enter. The Printer Selection box will come up. Find your printer/copier in the list and Double Click on it. Devices are listed by room number. All of the Konica-Minolta Copiers have a KM and the model number in the name after the room number. The naming convention works like this (Bldg. Room#)-KM (=Konica Minolta) (Model#) (print driver type). A box similar to the one on right will come up and close after the printer is installed. You may see a box similar to this asking you to trust the printer. If you see this box, click the “Install Driver” button. To set copier as your default printer select “Default Printer” from the Printer Menu. Changing Copier to Use Account Code From the Printer control panel right click your printer and choose Printing Preferences. You can find this in the Control Panel>Printers. Or you can open Word >Print> Printer Properties. You should see the box to the right. Click on “Basic” Tab In the “Printing Preferences” Click on the “Authentication/Account Track” button. Type your Employee ID in the Password box. Put Your Name in the Department Name box. (If this box is grayed out, the copier is not configured to use “Account Track”) Click the “Verify” button this will check to see if your account number works Click OK. -

Chapter 9. Input Devices
Table of contents 9 Input devices .................................................................................................................9-1 9.1 Keyboards ............................................................................................................. 9-4 9.2 Fixed-function keys .............................................................................................. 9-6 9.3 Pointing devices.................................................................................................... 9-7 9.3.1 General........................................................................................................... 9-7 9.3.2 Mouse ............................................................................................................ 9-9 9.3.3 Joystick and trackball .................................................................................. 9-10 9.3.3.1 General..................................................................................................9-10 9.3.3.2 Hand-operated displacement joysticks .................................................9-10 9.3.3.3 Finger-operated displacement joysticks................................................9-11 9.3.3.4 Thumb tip and fingertip-operated displacement joysticks....................9-13 9.3.3.5 Hand-operated isometric joysticks........................................................9-13 9.3.3.6 Thumb tip and fingertip-operated isometric joysticks..........................9-14 9.3.3.7 Ball controls..........................................................................................9-14 -

Class -IV Super Computer Year- 2020-21
s Class -IV Super Computer Year- 2020-21 1 1. Input and Output devices • Focus of the Chapter 1. Input devices 2. Output devices • Introduction The computer will be of no use unless it is able to communicate with the outside world. Input/output devices are required for users to communicate with the computer. An input device sends information to a computer system for processing. An input device tor a computer allows you to enter information. An output device can receive data from another device, but it cannot send data to another device. There are different devices of the computer that help it to do work. Input Devices The devices which are used to input the data and the program in the computer are known as "Input Devices". For the text input, keyboard are used, microphone is used for audio or sound input. 2 Keyboard The keyboard is the most common input device. A 'keyboard' is a human interface device which is "-presented as a layout of buttons. It is a text-based input device that allows the user to interact with the computer through a set of keys mounted on a board. Mouse After the keyboard, the mouse is the most common type of input device. A mouse makes the process of navigating the screen much easier than trying to use just a keyboard. A mouse usually uses a ball, light or a laser to track movement. Joystick A joystick is an input device consisting of a large pointed stick and input buttons on it. We can use this for playing games on the computer. -

The Trackball Controller: Improving the Analog Stick
The Trackball Controller: Improving the Analog Stick Daniel Natapov I. Scott MacKenzie Department of Computer Science and Engineering York University, Toronto, Canada {dnatapov, mack}@cse.yorku.ca ABSTRACT number of inputs was sufficient. Despite many future additions Two groups of participants (novice and advanced) completed a and improvements, the D-Pad persists on all standard controllers study comparing a prototype game controller to a standard game for all consoles introduced after the NES. controller for point-select tasks. The prototype game controller Shortcomings of the D-Pad became apparent with the introduction replaces the right analog stick of a standard game controller (used of 3D games. The Sony PlayStation and the Sega Saturn, for pointing and camera control) with a trackball. We used Fitts’ introduced in 1995, supported 3D environments and third-person law as per ISO 9241-9 to evaluate the pointing performance of perspectives. The controllers for those consoles, which used D- both controllers. In the novice group, the trackball controller’s Pads, were not well suited for 3D, since navigation was difficult. throughput was 2.69 bps – 60.1% higher than the 1.68 bps The main issue was that game characters could only move in eight observed for the standard controller. In the advanced group the directions using the D-Pad. To overcome this, some games, such trackball controller’s throughput was 3.19 bps – 58.7% higher than the 2.01 bps observed for the standard controller. Although as Resident Evil, used the forward and back directions of the D- the trackball controller performed better in terms of throughput, Pad to move the character, and the left and right directions for pointer path was more direct with the standard controller. -

Peripheral Guidance and How to Connect a Home Printer
Peripheral Guidance and How to Connect a Home Printer In the current COVID-19 telework environment, you may have the need to use your personal printer, monitor or mouse, or even use a headset for a meeting from a NASA computer. In accordance with NASA Policy Directive NPD 2540.1I Acceptable Use of Government Office Property Including Information Technology section 5, clause (6), “Users shall not connect unauthorized non-NASA devices to GFP (Government Furnished Property) via Universal Serial Bus (USB), Bluetooth, or other connection methods.” This policy is currently being updated, and the following guidelines should be adhered to: • Allowed non-NASA device categories for wired and wireless connectivity to a GFP computer include a personally owned: monitor, keyboard, mouse, scanner, printer, home network router, headset and headphone. • Disallowed non-NASA device categories for connection to a GFP computer: USB or “thumb drive” external storage device, external hard drive, smart phone/tablet and any device that provides/offers data storage. • No software shall be installed, or peripheral equipment connected by wired or wireless (including Bluetooth) or device/system used to process NASA data from the following companies or any subsidiary or affiliate of such entities: . Kaspersky Lab . Hikvision Digital Technology Company . Huawei Technologies . Dahua Technology Company . ZTE Corp. Hytera Communications Corp. To Install a New Printer Follow the instructions below to install a new printer. Detailed instructions with screen shots are available in Knowledge Article KB0018594. Due to a recent policy change, elevated privilege (EP) is not needed for printer installation. Important: If the printer is a networked printer at your home location, you will need to disconnect from NASA's VPN before performing the steps below.