Can Fingerprint Be Used As a Reliable DNA Source?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Dental DNA Fingerprinting in Identification of Human Remains
REVIEW ARTICLE Dental DNA fingerprinting in identification of human remains Girish KL, Farzan S Rahman, Shoaib R Tippu1 Departments of Oral Pathology & Microbiology and 1Oral & Abstract Maxillofacial Surgery, Jaipur Dental College, Jaipur, Rajasthan, The recent advances in molecular biology have revolutionized all aspects of dentistry. India DNA, the language of life yields information beyond our imagination, both in health or disease. DNA fingerprinting is a tool used to unravel all the mysteries associated with the oral cavity and its manifestations during diseased conditions. It is being increasingly used in analyzing various scenarios related to forensic science. The technical advances in molecular biology have propelled the analysis of the DNA into routine usage in crime laboratories for rapid and early diagnosis. DNA is an excellent means for identification Address for correspondence: of unidentified human remains. As dental pulp is surrounded by dentin and enamel, Dr. Girish KL, which forms dental armor, it offers the best source of DNA for reliable genetic type in Department of Oral Pathology & forensic science. This paper summarizes the recent literature on use of this technique Microbiology, Jaipur Dental College, Dhand, Thesil-Amer, in identification of unidentified human remains. NH. 8, Jaipur-302 101, Rajasthan, India. Key words: DNA analysis, DNA profiling, forensic odontology E-mail: [email protected] Introduction DNA since it is a sealed box preserving DNA from extreme environmental conditions, except its apical entrance. This he realization that DNA lies behind all the cell’s has prompted the investigation of various human tissues Tactivities led to the development of molecular biology. as potential source of genetic evidentiary material. -

Making a Place for Touch DNA in Post-Conviction DNA Testing Statutes, 62 Cath
Catholic University Law Review Volume 62 Issue 3 Spring 2013 Article 7 2013 Can’t Touch This? Making a Place for Touch DNA in Post- Conviction DNA Testing Statutes Victoria Kawecki Follow this and additional works at: https://scholarship.law.edu/lawreview Part of the Criminal Procedure Commons, and the Evidence Commons Recommended Citation Victoria Kawecki, Can’t Touch This? Making a Place for Touch DNA in Post-Conviction DNA Testing Statutes, 62 Cath. U. L. Rev. 821 (2013). Available at: https://scholarship.law.edu/lawreview/vol62/iss3/7 This Comments is brought to you for free and open access by CUA Law Scholarship Repository. It has been accepted for inclusion in Catholic University Law Review by an authorized editor of CUA Law Scholarship Repository. For more information, please contact [email protected]. Can’t Touch This? Making a Place for Touch DNA in Post-Conviction DNA Testing Statutes Cover Page Footnote J.D. Candidate, May 2014, The Catholic University of America, Columbus School of Law; B.A., 2011, Gettysburg College. The author wishes to thank John Sharifi for his exceptional and invaluable insight, guidance, dedication, tenacity, and inspiration throughout this process. She would also like to thank her colleagues on the Catholic University Law Review for their work on this Comment, and her legal writing professors, who taught her to question what she thinks she may know and to always lead with her conclusion. This comments is available in Catholic University Law Review: https://scholarship.law.edu/lawreview/vol62/iss3/7 CAN’T TOUCH THIS? MAKING A PLACE FOR TOUCH DNA IN POST-CONVICTION DNA TESTING STATUTES Victoria Kawecki+ DNA testing is to justice what the telescope is for the stars: not a lesson in biochemistry, not a display of the wonders of magnifying optical glass, but a way to see things as they really are. -

Experiment: Latent Fingerprinting
EXPERIMENT: DUSTED! Operating Guide Dusted! Visitors press their fingertips onto a clean Plexiglas sheet. Their fingerprints are then revealed as visitors dust over the print with fingerprint powder. OBJECTIVES: Visitors will learn that every person has a unique set of fingerprints. Visitors will understand how fingerprints are revealed on surfaces. SCIENCE TOPICS PROCESS SKILLS VOCABULARY Properties of Matter Observing Fingerprint Properties of Electrons Comparing/Contrasting Latent UNIT 7 CRIME SCENE CHEMISTRY U7.1 EXPERIENCING CHEMISTRY ©2006 OMSI EXPERIMENT: DUSTED!! Operating Guide Dusted! Procedure: 1. Always wear safety goggles. 2. Use the towel to clean and dry the plastic Plexiglas. 3. Firmly press one of your fingertips, fingerprint side down, anywhere on the Plexiglas. Try not to smudge your print. Can you see your print? 4. Take the same finger and dab it gently onto the oil sponge, then press firmly onto the Plexiglas near your other print. Can you see your print? 5. Pull the brush out of the powder container. 6. Carefully brush over where you left your fingerprints until you see clear prints. What do you see? Is one print more visible than the other? 7. Push the brush back into the powder container. 8. Take a piece of tape and press it down onto one of your prints and rub firmly. 9. Lift the tape off and place it onto a square of the black paper. U7.2 UNIT 7 CRIME SCENE CHEMISTRY EXPERIENCING CHEMISTRY ©2006 OMSI EXPERIMENT: DUSTED! Operating Guide Does all the powder lift with the tape? How does your lifted print compare to the original? Why do we leave fingerprints behind? How can we collect them? A Closer Look: In this experiment, you left your fingerprint on a Plexiglas surface. -

Discovery for Complex DNA Cases Carrie Wood, Appellate Attorney, Hamilton County, Public Defender's Office
Discovery for complex DNA cases Carrie Wood, Appellate Attorney, Hamilton County, Public Defender’s Office (Cincinnati, OH) Crossing the State’s Expert in Complex DNA cases (mixtures, drop out and inconclusive results) Carrie Wood (Cincinnati, OH) and Nathan Adams (Fairborn, OH) Pre-trial Litigation: Discovery, Admissibility Challenges, and Practice Tips Carrie Wood NACDL Pennsylvania Training Conference, February 23, 2018 – 90 Minutes This presentation will address how a lawyer obtains and identifies the appropriate discovery for each of the areas outlined by Nathan Adams in his talk. This talk will assist attendees to use discovery to identify potential unfounded statements and/or unreliable technology, as well as flag areas are where an expert for the State may oversimplify, misapply, or mischaracterize based on the discovery materials and investigation. Finally, for each identified area of concern, the talk will present pre-trial litigation strategy, law, and motions as well as practice points for cross- examination. 1. Exam/inspection for samples of interest (including serology) 2. Extraction 3. Quantification/quantitation 4. Amplification (PCR) 5. CE injection (genetic analyzer) 6. Analysis by human 7. Analysis by probabilistic genotyping software (maybe) Getting Started • Discovery: One of the most critical steps in successfully challenging scientific evidence and in particular DNA evidence is obtaining the necessary discovery. It is impossible to evaluate the DNA evidence or assess the strength of it without obtaining discovery. -

Nature Flaunts Her Glory
Volume 34, Number 1 ■ January, 2019 Center for the Study of the First Americans Department of Anthropology Texas A&M University 4352 TAMU College Station, TX 77843-4352 www.centerfirstamericans.com - Nature flaunts her glory Near Vik, Iceland, a geologic formation known as a columnar basalt rose spectacularly showcases University of Oregon anthropologist Jon Erlandson, who takes time off from his research on the California Channel Islands to explore Viking-age sites (and engage his Nordic roots). His principal goal is to marshal convincing evidence for the coastal-entry route, one of several competing hypotheses that explain how the First Americans entered North America. See part 1 of our series on how the First Americans got here on page 13. To learn more about Erlandson’s work and career, see his profile on page 17. Photo by Erik Erlandson he Center for the Study of the First Americans fosters research and public T interest in the Peopling of the Americas. The Center, an integral part of the Department of Anthropology at Texas A&M University, pro motes inter disciplinary scholarly dialogue among physical, geological, biological and social scientists. The Mammoth Trumpet, news magazine of the Center, seeks to involve you in the peopling of the Americas by report- ing on developments in all pertinent areas of knowledge. JoinJoin inin thethe SearchSearch for the First Americans! Become a member of the Center for the Study of the First Americans on Center publications plus additional benefits according to the level of and explore the origin, lifeways, artifacts, and other aspects of the membership support you choose. -

Fingerprint Capture Challenges and Opportunities
Fingerprint Capture Challenges and Opportunities Dr. Rama Krishnan IDENT - Biometrics Quality Lead Presentation Overview □ Importance of Fingerprint Quality • Impacts on identification system □ Fingerprint Capture Challenges • Factors that will affect/impact fingerprint capture process □ Fingerprint Capture Opportunities • Possible approaches/solutions to enhance fingerprint capture quality Importance of Fingerprint Quality in an AFIS System □ Fingerprint Quality Impact on AFIS •NIST studies have shown that image quality has a direct impact on identification match accuracy □ Poor Fingerprint Image Quality Can Have the Following Negative Impacts in an AFIS System such as US-VISIT •Potential missed identification/verification of a subject •Additional secondary workload process •Additional fingerprint examiner workload Factors of Poor Fingerprint Quality Physiological • Dry fingers due to natural aging process • Worn ridge structure due to occupation • Finer ridge structure specific to a demographic group Behavioral • Uncooperative subject • Nervous Subject Environmental • Humidity / Temperature • Seasonal Change • Ambient Light Operational • High Throughput/ Reduced Capture Time • Unclean Scanner Platen Technological • Application Graphical User Interface (GUI) • Ease of Scanner Use / Interaction Poor Quality Image Illustrations Dry Finger Moist Finger Light Print Dark Print Poor Finger Worn Ridge Placement Structure Image Quality – User Demographics □ Male – Female • Female subjects have worse image quality □ Right Hand – Left Hand 41,000 Subjects • Left hand fingerprint quality is worse than right 24,000 Males hand 17,000 Females □ By Age of Subject • Image Quality worsens as subject age increases Image Quality Assurance Monitoring/Reporting 1 Application Identifies if there is an application-specific image quality issue - scanner, fingerprint capture GUI etc. 2 Site/Terminal Identifies if there is a site/terminal/operator-specific image quality issue within the application. -

Government Institute of Forensic Science, Aurangabad M.Sc
DR. BABASAHEB AMBEDKAR MARATHWADA UNIVERSITY, AURANGABAD SYLLABUS Of M.Sc. II (Semester III and IV) (Forensic Science) Effective from Academic Year 2013-2014 onwards 1 Government Institute Of Forensic Science, Aurangabad M.Sc. II Year (Finger print and Questioned Document) Preamble M.Sc.-II (Sem-III & IV) (Forensic Science) Ordinance ------------:- Title of the Program: - M.Sc.-II (Sem-III & IV) (Forensic Science) Ordinance ------------:-- Eligibility: - M.Sc.-I (Forensic Science) Regulation no. ----------- : Specializations :- Four Specializations viz. Finger print and Questioned Document, Forensic Chemistry and Toxicology, Forensic Biology, Serology and DNA Finger Printing, Cyber Space, IT Security and Cyber Forensic may be offered subject to the availability of students as mentioned in the preceding Para/ regulation. Regulation no. -----------:- Minimum intake capacity for each specialization: - There shall be minimum 25% of the intake capacity of the students for each specialization. Regulation no. ----------- :-Allotment of specialization :- The specialization to the students will be allotted on the basis of choice and merit (M.Sc.-I) of the students. However, if the criterion of minimum intake capacity for a particular specialization as mentioned above is not full filled, in such case the students will be diverted to other specialization strictly based on the marks obtained by him/her at M.Sc.-I examination. In such situation the decision of the Head of the concerned Institution shall be final. Regulation no.-------------- :- Course structure Each semester will have four theory papers and two theory based practical papers. In the fourth semester students will carry out Dissertation instead of one practical paper. Each paper shall be of 75 marks. -

L-1 Identity Solutions Fingerprint Reader
L-1 Identity Solutions Fingerprint Reader Savance Phone: 248-478-2555 | Fax: 248-478-3270 www.eioboard.com | [email protected] | www.savance.com © 2014 L-1 Identity Solutions Fingerprint Reader Table of Contents Fingerprint Reader Hardware Installation (4G V-Flex) 3 Fingerprint Reader Hardware Installation (4G V-Flex Lite) 5 Kiosk/Punch RS-232 Wiring Installation (Option 1) 9 Kiosk/Punch RS-485 Wiring Installation (Option 2) 13 Infinias Door Module Wiegand Wiring Installation (Option 3) 14 SecureAdmin Software Installation 19 SecureAdmin Software Configuration 30 EIOBoard Kiosk Software Configuration 37 Savance EIOBoard • www.eioboard.com • Phone: 248-478-2555 • Fax: 248-478-3270 2 1111 W. Oakley Park Rd., Ste 103 Commerce Township, MI 48390 L-1 Identity Solutions Fingerprint Reader Fingerprint Reader Hardware Installation (4G V-Flex) Here are the instructions for setting up the fingerprint reader to the computer. This applies to the 4G V-Flex model only. 1. Unbox your L-1 Identity Solutions Fingerprint Reader. 2. Connect the power adapter into the back of the unit in the round connector. Plug the other end into the wall. The unit’s lights should turn on. Savance EIOBoard • www.eioboard.com • Phone: 248-478-2555 • Fax: 248-478-3270 3 1111 W. Oakley Park Rd., Ste 103 Commerce Township, MI 48390 L-1 Identity Solutions Fingerprint Reader 3. One option for communicating between the fingerprint reader and the SecureAdmin fingerprint software is to use an Ethernet cable. You would plug one end of the Ethernet cable into the back of the unit, and the other end into a router or switch on your network. -

An Investigation Into the Foundational Principles of Forensic Science
Department of Chemistry An Investigation into the Foundational Principles of Forensic Science Max Michael Houck This thesis is presented for the Degree of Doctor of Philosophy Of Curtin University of Technology February, 2010 i Declaration: To the best of my knowledge and belief this thesis contains no material previously published by any other person except where due acknowledgment has been made. This thesis contains no material which has been accepted for the award of any other degree or diploma in any university. Signature: __________________________________ Date: _________________ ii Abstract This thesis lays the groundwork for a philosophy of forensic science. Forensic science is a historical science, much like archaeology and geology, which operates by the analysis and understanding of the physical remnants of past criminal activity. Native and non-native principles guide forensic science’s operation, application, and interpretations. The production history of mass-produced goods is embedded in the finished product, called the supply chain. The supply chain solidifies much of the specificity and resolution of the evidentiary significance of that product. Forensic science has not had an over-arching view of this production history integrated into its methods or instruction. This thesis offers provenance as the dominant factor for much of the inherent significance of mass-produced goods that become evidence. iii Presentations and Publications Some ideas and concepts in this thesis appeared in the following presentations and publications: “Forensic Science is History,” 2004 Combined Meeting of the Southern, Midwestern, Mid Atlantic Associations of Forensic Scientists and the Canadian Society of Forensic Scientists, Orlando, FL, September. “Crime Scene Investigation,” NASA Goddard Engineering Colloquium, Goddard Space Flight Center, Greenbelt, MD, November 2005 “A supply chain approach to evidentiary significance,” 2008 Australia New Zealand Forensic Science Society, Melbourne. -

The Fingerprint Sourcebook
CHAPTER HISTORY Jeffery G. Barnes CONTENTS 3 1.1 Introduction 11 1.6 20th Century 3 1.2 Ancient History 17 1.7 Conclusion 4 1.3 221 B.C. to A.D. 1637 17 1.8 Reviewers 5 1.4 17th and 18th Centuries 17 1.9 References 6 1.5 19th Century 18 1.10 Additional Information 1–5 History C H A P T E R 1 CHAPTER 1 HISTORY 1.1 Introduction The long story of that inescapable mark of identity has Jeffery G. Barnes been told and retold for many years and in many ways. On the palm side of each person’s hands and on the soles of each person’s feet are prominent skin features that single him or her out from everyone else in the world. These fea- tures are present in friction ridge skin which leaves behind impressions of its shapes when it comes into contact with an object. The impressions from the last finger joints are known as fingerprints. Using fingerprints to identify indi- viduals has become commonplace, and that identification role is an invaluable tool worldwide. What some people do not know is that the use of friction ridge skin impressions as a means of identification has been around for thousands of years and has been used in several cultures. Friction ridge skin impressions were used as proof of a person’s identity in China perhaps as early as 300 B.C., in Japan as early as A.D. 702, and in the United States since 1902. 1.2 Ancient History Earthenware estimated to be 6000 years old was discov- ered at an archaeological site in northwest China and found to bear clearly discernible friction ridge impressions. -

BPA Guidelines for Report Writing in Bloodstain Pattern Analysis
This document has been accepted by the Academy Standards Board (ASB) for development as an American National Standard (ANS). For information about ASB and their process please refer to asb.aafs.org. This document is being made available at this stage of the process so that the forensic science community and interested stakeholders can be more fully aware of the efforts and work products of the Organization of Scientific Area Committees for Forensic Science (OSAC). The documents were prepared with input from OSAC Legal Resource Committee, Quality Infrastructure Committee, and Human Factors Committees, as well as the relevant Scientific Area Committee. The content of the documents listed below is subject to change during the standards development process within ASB, and may not represent the contents of the final published standard. All stakeholder groups or individuals, are strongly encouraged to submit technical comments on this draft document during the ASB’s open comment period. Technical comments will not be accepted if submitted to the OSAC Scientific Area Committee or Subcommittees. Guidelines for Report Writing in Bloodstain Pattern Analysis DRAFT DRAFT DOCUMENT ASB Numerical Designation Guidelines for Report Writing in Bloodstain Pattern Analysis Keywords: Report, case information, methods, limitations, assumptions, observations, analysis, conclusions, review The purpose of this document is to provide a guide for the report content and issuance of Bloodstain Pattern Analysis (BPA) reports. It is not intended to set forth a specific format for report writing. DRAFT 1 Foreword This document provides guidelines for report writing in Bloodstain Pattern Analysis (BPA). In addition, it provides guidance regarding statements to be avoided in the report. -
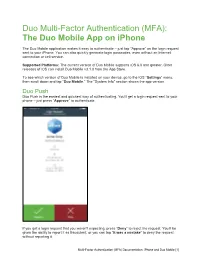
(MFA): the Duo Mobile App on Iphone
Duo Multi-Factor Authentication (MFA): The Duo Mobile App on iPhone The Duo Mobile application makes it easy to authenticate – just tap “Approve” on the login request sent to your iPhone. You can also quickly generate login passcodes, even without an Internet connection or cell service. Supported Platforms: The current version of Duo Mobile supports iOS 6.0 and greater. Older releases of iOS can install Duo Mobile v3.1.0 from the App Store. To see which version of Duo Mobile is installed on your device, go to the iOS “Settings” menu, then scroll down and tap “Duo Mobile.” The "System Info" section shows the app version. Duo Push Duo Push is the easiest and quickest way of authenticating. You'll get a login request sent to your phone – just press “Approve” to authenticate. If you get a login request that you weren't expecting, press “Deny” to reject the request. You’ll be given the ability to report it as fraudulent, or you can tap “It was a mistake” to deny the request without reporting it. Multi-Factor Authentication (MFA) Documentation: iPhone and Duo Mobile [1] Touch ID Duo Mobile for iOS also supports Touch ID for Duo Push-based logins; an additional layer of security to verify your users’ identities. If you're using a Touch ID capable iOS device, you'll see a Touch ID prompt each time you authenticate via Duo Mobile (if required by your administrator). If you're not able to scan your fingerprint using the TouchID sensor you can also approve the Duo authentication request using the device's passcode (the same one you use on the iOS lock screen).