Cryptographic Hashing Functions - MD5
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Intro to Cryptography 1 Introduction 2 Secure Password Manager
Programming Assignment 1 Winter 2021 CS 255: Intro to Cryptography Prof. Dan Boneh Due Monday, Feb. 8, 11:59pm 1 Introduction In many software systems today, the primary weakness often lies in the user’s password. This is especially apparent in light of recent security breaches that have highlighted some of the weak passwords people commonly use (e.g., 123456 or password). It is very important, then, that users choose strong passwords (or “passphrases”) to secure their accounts, but strong passwords can be long and unwieldy. Even more problematic, the user generally has many different services that use password authentication, and as a result, the user has to recall many different passwords. One way for users to address this problem is to use a password manager, such as LastPass and KeePass. Password managers make it very convenient for users to use a unique, strong password for each service that requires password authentication. However, given the sensitivity of the data contained in the password manager, it takes considerable care to store the information securely. In this assignment, you will be writing a secure and efficient password manager. In your implemen- tation, you will make use of various cryptographic primitives we have discussed in class—notably, authenticated encryption and collision-resistant hash functions. Because it is ill-advised to imple- ment your own primitives in cryptography, you should use an established library: in this case, the Stanford Javascript Crypto Library (SJCL). We will provide starter code that contains a basic tem- plate, which you will be able to fill in to satisfy the functionality and security properties described below. -

Fast Hashing and Stream Encryption with Panama
Fast Hashing and Stream Encryption with Panama Joan Daemen1 and Craig Clapp2 1 Banksys, Haachtesteenweg 1442, B-1130 Brussel, Belgium [email protected] 2 PictureTel Corporation, 100 Minuteman Rd., Andover, MA 01810, USA [email protected] Abstract. We present a cryptographic module that can be used both as a cryptographic hash function and as a stream cipher. High performance is achieved through a combination of low work-factor and a high degree of parallelism. Throughputs of 5.1 bits/cycle for the hashing mode and 4.7 bits/cycle for the stream cipher mode are demonstrated on a com- mercially available VLIW micro-processor. 1 Introduction Panama is a cryptographic module that can be used both as a cryptographic hash function and a stream cipher. It is designed to be very efficient in software implementations on 32-bit architectures. Its basic operations are on 32-bit words. The hashing state is updated by a parallel nonlinear transformation, the buffer operates as a linear feedback shift register, similar to that applied in the compression function of SHA [6]. Panama is largely based on the StepRightUp stream/hash module that was described in [4]. Panama has a low per-byte work factor while still claiming very high security. The price paid for this is a relatively high fixed computational overhead for every execution of the hash function. This makes the Panama hash function less suited for the hashing of messages shorter than the equivalent of a typewritten page. For the stream cipher it results in a relatively long initialization procedure. Hence, in applications where speed is critical, too frequent resynchronization should be avoided. -

User Authentication and Cryptographic Primitives
User Authentication and Cryptographic Primitives Brad Karp UCL Computer Science CS GZ03 / M030 16th November 2016 Outline • Authenticating users – Local users: hashed passwords – Remote users: s/key – Unexpected covert channel: the Tenex password- guessing attack • Symmetric-key-cryptography • Public-key cryptography usage model • RSA algorithm for public-key cryptography – Number theory background – Algorithm definition 2 Dictionary Attack on Hashed Password Databases • Suppose hacker obtains copy of password file (until recently, world-readable on UNIX) • Compute H(x) for 50K common words • String compare resulting hashed words against passwords in file • Learn all users’ passwords that are common English words after only 50K computations of H(x)! • Same hashed dictionary works on all password files in world! 3 Salted Password Hashes • Generate a random string of bytes, r • For user password x, store [H(r,x), r] in password file • Result: same password produces different result on every machine – So must see password file before can hash dictionary – …and single hashed dictionary won’t work for multiple hosts • Modern UNIX: password hashes salted; hashed password database readable only by root 4 Salted Password Hashes • Generate a random string of bytes, r Dictionary• For user password attack still x, store possible [H(r,x after), r] in attacker seespassword password file file! Users• Result: should same pick password passwords produces that different aren’t result close to ondictionary every machine words. – So must see password file -

MD5 Collisions the Effect on Computer Forensics April 2006
Paper MD5 Collisions The Effect on Computer Forensics April 2006 ACCESS DATA , ON YOUR RADAR MD5 Collisions: The Impact on Computer Forensics Hash functions are one of the basic building blocks of modern cryptography. They are used for everything from password verification to digital signatures. A hash function has three fundamental properties: • It must be able to easily convert digital information (i.e. a message) into a fixed length hash value. • It must be computationally impossible to derive any information about the input message from just the hash. • It must be computationally impossible to find two files to have the same hash. A collision is when you find two files to have the same hash. The research published by Wang, Feng, Lai and Yu demonstrated that MD5 fails this third requirement since they were able to generate two different messages that have the same hash. In computer forensics hash functions are important because they provide a means of identifying and classifying electronic evidence. Because hash functions play a critical role in evidence authentication, a judge and jury must be able trust the hash values to uniquely identify electronic evidence. A hash function is unreliable when you can find any two messages that have the same hash. Birthday Paradox The easiest method explaining a hash collision is through what is frequently referred to as the Birthday Paradox. How many people one the street would you have to ask before there is greater than 50% probability that one of those people will share your birthday (same day not the same year)? The answer is 183 (i.e. -

To Change Your Ud Password(S)
TO CHANGE YOUR UD PASSWORD(S) The MyCampus portal allows the user a single-signon for campus applications. IMPORTANT NOTICE AT BOTTOM OF THESE INSTRUCTIONS !! INITIAL PROCEDURE TO ALLOW YOU TO CHANGE YOUR PASSWORD ON THE UD NETWORK : 1. In your web browser, enter http://mycampus.dbq.edu . If you are logging in for the first time, you will be directed to answer (3) security questions. Also, be sure to answer one of the recovery methods. 2. Once the questions are answered, you will click on SUBMIT and then CONTINUE and then YES. 3. In one location, you will now find MyUD, Campus Portal, Email and UDOnline (Moodle). 4. You can now click on any of these apps and you will be logged in already. The email link will prompt you for the password a second time until we get all accounts set up properly. YOU MUST BE SURE TO LOGOUT OF EACH APPLICATION AFTER YOU’RE DONE USING IT !! TO CHANGE YOUR PASSWORD: 1. After you have logged into the MyCampus.dbq.edu website, you will see your username in the upper- right corner of the screen. 2. Click on your name and then go into My Account. 3. At the bottom, you will click on Change Password and then proceed as directed. 4. You can now logout. You will need to use your new password on your next login. Password must be a minimum of 6 characters and contain 3 of the following 4 categories: - Uppercase character - Lowercase character - Number - Special character You cannot use the previous password You’ll be required to change your password every 180 days. -
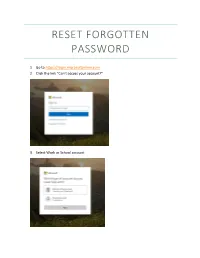
Reset Forgotten Password with Office365
RESET FORGOTTEN PASSWORD 1. Go to https://login.microsoftonline.com 2. Click the link “Can’t access your account?” 3. Select Work or School account 4. Enter in your User ID with the @uamont.edu at the end and then enter the characters as seen in the picture. You can click the refresh button for a different set of letters. 5. You will have 3 options to verify your account and reset your password. This information was set up when you registered with self-service password reset. If you have not registered, please go to https://aka.ms/ssprsetup and enter in your information. A step by step guide on how to do this can be found here. a. Text your mobile phone b. Call your mobile phone c. Answer Security Questions 6. Choose one option and enter the information requested 7. Click Text for text my mobile phone, Call for call my mobile phone, or click Next when you’ve answered all security questions. a. If you have selected Text my mobile phone you will be required to enter in a verification code and click Next b. If you have select Call my mobile phone you will receive a call and will need to enter # to verify. 8. Enter in your new password and click Finish a. Note: If you receive the message, “Unfortunately, your password contains a word, phrase, or pattern that makes it easily guessable. Please try again with a different password.” Please try to create a password that does not use any dictionary words. b. Passwords must meet 3 of the 4 following requirements i. -

FIPS 140-2 Non-Proprietary Security Policy Oracle Linux 7 NSS
FIPS 140-2 Non-Proprietary Security Policy Oracle Linux 7 NSS Cryptographic Module FIPS 140-2 Level 1 Validation Software Version: R7-4.0.0 Date: January 22nd, 2020 Document Version 2.3 © Oracle Corporation This document may be reproduced whole and intact including the Copyright notice. Title: Oracle Linux 7 NSS Cryptographic Module Security Policy Date: January 22nd, 2020 Author: Oracle Security Evaluations – Global Product Security Contributing Authors: Oracle Linux Engineering Oracle Corporation World Headquarters 500 Oracle Parkway Redwood Shores, CA 94065 U.S.A. Worldwide Inquiries: Phone: +1.650.506.7000 Fax: +1.650.506.7200 oracle.com Copyright © 2020, Oracle and/or its affiliates. All rights reserved. This document is provided for information purposes only and the contents hereof are subject to change without notice. This document is not warranted to be error-free, nor subject to any other warranties or conditions, whether expressed orally or implied in law, including implied warranties and conditions of merchantability or fitness for a particular purpose. Oracle specifically disclaim any liability with respect to this document and no contractual obligations are formed either directly or indirectly by this document. This document may reproduced or distributed whole and intact including this copyright notice. Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. Oracle Linux 7 NSS Cryptographic Module Security Policy i TABLE OF CONTENTS Section Title -

BLAKE2: Simpler, Smaller, Fast As MD5
BLAKE2: simpler, smaller, fast as MD5 Jean-Philippe Aumasson1, Samuel Neves2, Zooko Wilcox-O'Hearn3, and Christian Winnerlein4 1 Kudelski Security, Switzerland [email protected] 2 University of Coimbra, Portugal [email protected] 3 Least Authority Enterprises, USA [email protected] 4 Ludwig Maximilian University of Munich, Germany [email protected] Abstract. We present the hash function BLAKE2, an improved version of the SHA-3 finalist BLAKE optimized for speed in software. Target applications include cloud storage, intrusion detection, or version control systems. BLAKE2 comes in two main flavors: BLAKE2b is optimized for 64-bit platforms, and BLAKE2s for smaller architectures. On 64- bit platforms, BLAKE2 is often faster than MD5, yet provides security similar to that of SHA-3: up to 256-bit collision resistance, immunity to length extension, indifferentiability from a random oracle, etc. We specify parallel versions BLAKE2bp and BLAKE2sp that are up to 4 and 8 times faster, by taking advantage of SIMD and/or multiple cores. BLAKE2 reduces the RAM requirements of BLAKE down to 168 bytes, making it smaller than any of the five SHA-3 finalists, and 32% smaller than BLAKE. Finally, BLAKE2 provides a comprehensive support for tree-hashing as well as keyed hashing (be it in sequential or tree mode). 1 Introduction The SHA-3 Competition succeeded in selecting a hash function that comple- ments SHA-2 and is much faster than SHA-2 in hardware [1]. There is nev- ertheless a demand for fast software hashing for applications such as integrity checking and deduplication in filesystems and cloud storage, host-based intrusion detection, version control systems, or secure boot schemes. -

Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption
S S symmetry Article Optimizing a Password Hashing Function with Hardware-Accelerated Symmetric Encryption Rafael Álvarez 1,* , Alicia Andrade 2 and Antonio Zamora 3 1 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain 2 Fac. Ingeniería, Ciencias Físicas y Matemática, Universidad Central, Quito 170129, Ecuador; [email protected] 3 Departamento de Ciencia de la Computación e Inteligencia Artificial (DCCIA), Universidad de Alicante, 03690 Alicante, Spain; [email protected] * Correspondence: [email protected] Received: 2 November 2018; Accepted: 22 November 2018; Published: 3 December 2018 Abstract: Password-based key derivation functions (PBKDFs) are commonly used to transform user passwords into keys for symmetric encryption, as well as for user authentication, password hashing, and preventing attacks based on custom hardware. We propose two optimized alternatives that enhance the performance of a previously published PBKDF. This design is based on (1) employing a symmetric cipher, the Advanced Encryption Standard (AES), as a pseudo-random generator and (2) taking advantage of the support for the hardware acceleration for AES that is available on many common platforms in order to mitigate common attacks to password-based user authentication systems. We also analyze their security characteristics, establishing that they are equivalent to the security of the core primitive (AES), and we compare their performance with well-known PBKDF algorithms, such as Scrypt and Argon2, with favorable results. Keywords: symmetric; encryption; password; hash; cryptography; PBKDF 1. Introduction Key derivation functions are employed to obtain one or more keys from a master secret. This is especially useful in the case of user passwords, which can be of arbitrary length and are unsuitable to be used directly as fixed-size cipher keys, so, there must be a process for converting passwords into secret keys. -

Cryptanalysis of MD4
Cryptanalysis of MD4 Hans Dobbertin German Information Security Agency P. O. Box 20 03 63 D-53133 Bonn e-maih dobbert inQskom, rhein .de Abstract. In 1990 Rivest introduced the hash function MD4. Two years later RIPEMD, a European proposal, was designed as a stronger mode of MD4. Recently wc have found an attack against two of three rounds of RIPEMD. As we shall show in the present note, the methods developed to attack RIPEMD can be modified and supplemented such that it is possible to break the full MD4, while previously only partial attacks were known. An implementation of our attack allows to find collisions for MD4 in a few seconds on a PC. An example of a collision is given demonstrating that our attack is of practical relevance. 1 Introduction Rivest [7] introduced the hash function MD4 in 1990. The MD4 algorithm is defined as an iterative application of a three-round compress function. After an unpublished attack on the first two rounds of MD4 due to Merkle and an attack against the last two rounds by den Boer and Bosselaers [2], Rivest introduced the strengthened version MD5 [8]. The most important difference to MD4 is the adding of a fourth round. On the other hand the stronger mode RIPEMD [1] of MD4 was designed as a European proposal in 1992. The compress function of RIPEMD consists of two parallel lines of a modified version of the MD4 compress function. In [4] we have shown that if the first or the last round of its compress function is omitted, then RIPEMD is not collision-free. -

Extending NIST's CAVP Testing of Cryptographic Hash Function
Extending NIST’s CAVP Testing of Cryptographic Hash Function Implementations Nicky Mouha and Christopher Celi National Institute of Standards and Technology, Gaithersburg, MD, USA [email protected],[email protected] Abstract. This paper describes a vulnerability in Apple’s CoreCrypto library, which affects 11 out of the 12 implemented hash functions: every implemented hash function except MD2 (Message Digest 2), as well as several higher-level operations such as the Hash-based Message Authen- tication Code (HMAC) and the Ed25519 signature scheme. The vulnera- bility is present in each of Apple’s CoreCrypto libraries that are currently validated under FIPS 140-2 (Federal Information Processing Standard). For inputs of about 232 bytes (4 GiB) or more, the implementations do not produce the correct output, but instead enter into an infinite loop. The vulnerability shows a limitation in the Cryptographic Algorithm Validation Program (CAVP) of the National Institute of Standards and Technology (NIST), which currently does not perform tests on hash func- tions for inputs larger than 65 535 bits. To overcome this limitation of NIST’s CAVP, we introduce a new test type called the Large Data Test (LDT). The LDT detects vulnerabilities similar to that in CoreCrypto in implementations submitted for validation under FIPS 140-2. Keywords: CVE-2019-8741, FIPS, CAVP, ACVP, Apple, CoreCrypto, hash function, vulnerability. 1 Introduction The security of cryptography in practice relies not only on the resistance of the algorithms against cryptanalytical attacks, but also on the correctness and robustness of their implementations. Software implementations are vulnerable to software faults, also known as bugs. -

A (Second) Preimage Attack on the GOST Hash Function
A (Second) Preimage Attack on the GOST Hash Function Florian Mendel, Norbert Pramstaller, and Christian Rechberger Institute for Applied Information Processing and Communications (IAIK), Graz University of Technology, Inffeldgasse 16a, A-8010 Graz, Austria [email protected] Abstract. In this article, we analyze the security of the GOST hash function with respect to (second) preimage resistance. The GOST hash function, defined in the Russian standard GOST-R 34.11-94, is an iter- ated hash function producing a 256-bit hash value. As opposed to most commonly used hash functions such as MD5 and SHA-1, the GOST hash function defines, in addition to the common iterated structure, a check- sum computed over all input message blocks. This checksum is then part of the final hash value computation. For this hash function, we show how to construct second preimages and preimages with a complexity of about 2225 compression function evaluations and a memory requirement of about 238 bytes. First, we show how to construct a pseudo-preimage for the compression function of GOST based on its structural properties. Second, this pseudo- preimage attack on the compression function is extended to a (second) preimage attack on the GOST hash function. The extension is possible by combining a multicollision attack and a meet-in-the-middle attack on the checksum. Keywords: cryptanalysis, hash functions, preimage attack 1 Introduction A cryptographic hash function H maps a message M of arbitrary length to a fixed-length hash value h. A cryptographic hash function has to fulfill the following security requirements: – Collision resistance: it is practically infeasible to find two messages M and M ∗, with M ∗ 6= M, such that H(M) = H(M ∗).