An Approach to Discovering Architectural Patterns in Software
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PATACS Posts
PATACS Posts Newsletterofthe PotomacAreaTechnology and ComputerSociety November 201 6 www.patacs.org Page 1 Musings of an Apple Tyro Seagate 10 TB Hard Drive by Lorrin R. Garson If you need a large and fast hard disk drive, Potomac Area Technology and Computer Society Seagate’s Barracuda Pro 10 TB might fit the bill. newslettercolumnist (at) patacs.org PCWorld reports that this 3.5-inch, 7,200 rpm drive is miserly on power consumption and reads More Information about Time Machine and writes data at 243 MBps and 229 MBps, Time Machine is used for backup by many respectively. The drive is priced at $579.98. (most?) people using Apple computers. However, See http://bit.ly/2ctR6Il for more information. that application provides rather sparse information about what’s going on. Want more People Holding on to iPhones Longer information? Open the Console, which is in Last year people traded in their iPhones every either the Applications or Utilities folder, two years. By 2018 that’s expected to increase to depending on the version of OS X. The right three years. The chart in Figure 2 is from three columns will display processes that have http://read.bi/2cAJpNY. been run. The Time Machine process is called “backupd.” Key backupd (no quotes) in the Apple’s New File System search box of Console, then start up Time Next year, or perhaps sooner, we can expect a Machine, noting the time in the Menu bar so you new proprietary file system for Apple computers. can view the processes for that specific instance It’s called APFS (Apple File System) and will of backupd. -
Advanced Properties Used in SH3D
A mini-guide for Sweet Home 3D users Editing SVG and other advanced furniture properties Version 1.2 © Ola-Kristian HOFF, 2013 CC-BY M 0,0 z < v -1 v 1 h 1 Contents Purpose.......................................................................................................2 Models (furniture) and file types................................................................2 SVG............................................................................................................3 SVG and advanced properties used in SH3D.............................................................. 3 How to add SVG to SH3D models.............................................................................. 3 SVG co-ordinates used in SH3D................................................................................. 4 SVG path commands................................................................................................... 4 Examples..................................................................................................................... 5 Full rectangle (5) ..door with no threshold (doorframe with three sides) (5) Part rectangle cut-out (6) L shape(d staircase) (6) Door with diagonally slashed top (under angled ceiling) (6) An arch door (7) Arc cut-out 90º: pie-slice (7) Double cut-out arc 90º (7) Double cut-out arc180º (7) A staircase that curves at the top (8) Spiral staircase (8) Keyhole cut-out (8) Visualising your SVG path in a browser..................................................................... 8 Sample file - text -

Charles University in Prague
Vrije Universiteit Amsterdam Faculty of sciences MASTER THESIS Milan Slančík Advanced floor plan designer in Flex Department of computer science Supervisor: Prof dr Anton Æliëns Second reader: Dr Evert Wattel Study program: Informatics, Multimedia Computer Science Acknowledgements First of all, I wish to express my sincere gratitude and appreciation to my supervisor, Prof Dr Anton Æliëns, for his thoughtful guidance, his valuable suggestions, comments during discussions, prompt response to my emails and speedy feedback. My gratitude also goes to my second reader, Dr Evert Wattel for his ideas, willingness to read drafts and test the application in advance. Last, but not least, I would like to give my sincere thanks also to my parents, who have supported me throughout the writing process. Contents 1 INTRODUCTION ....................................................................................................................................................... 8 1.1 BACKGROUND ............................................................................................................................................................ 8 1.2 STRUCTURE OF THIS DOCUMENT ............................................................................................................................ 8 2 AIM OF THE WORK AND RESEARCH ISS UES ........................................................................................... 9 3 RELATED WORK................................................................................................................................................... -

Handleiding Sweet Home 3D
SWEET HOME 3D WAT IS SWEET HOME 3D? Sweet Home 3D is een gratis opensource-interieurtekenprogramma. Dit betekent dat iedereen: vrije toegang heeft tot de bronmaterialen van het eindproduct vrij 3D-tekeningen kan toevoegen/afhalen Het enige wat je moet doen, is je registreren. DOEL VAN SWEET HOME 3D VOOR ADVISEURS HULPMIDDELEN Het is niet de bedoeling dat adviseurs bouwplannen gaan ontwerpen. Dit is de taak van architecten, al dan niet bijgestaan door bouwkundig tekenaars. Met Sweet Home 3D kunnen adviseurs bestaande ontwerpen beoordelen en bijsturen door wijzigingen voor te stellen, toegankelijkheidseisen kunnen aantonen en controleren, maatvoering kunnen nagaan … SWEET HOME 3D INSTALLEREN Voor Windows-gebruikers: gebruik volgende link: http://prdownloads.sourceforge.net/sweethome3d/SweetHome3D-2.5-windows.exe (29 MB) Voor Mac-gebruikers: gebruik volgende link: http://prdownloads.sourceforge.net/sweethome3d/SweetHome3D-2.5-macosx.dmg (13 MB) Voor Linux-gebruikers: gebruik volgende link: http://prdownloads.sourceforge.net/sweethome3d/SweetHome3D-2.5-linux-x86.tgz (47 MB) Afhankelijk of Java is geïnstalleerd op je systeem of niet, kun je Sweet Home 3D starten met Java Web Start. Download Sweet Home 3D met Java Web Start Als Java versie 5 of 6 is geïnstalleerd op je systeem, klik je op de volgende link: http://www.sweethome3d.com/download.jsp#SweetHome3DJavaWebStart Start Sweet Home 3D met Java Web Start Eenvoudig starten Ga via ‘google’ naar Sweet Home 3d. Daarna: Launch Sweet Home 3D with Java Web Start Als je wat problemen ondervindt -

Using Augmented Reality for Architecture Artifacts Visualizations
Using augmented reality for architecture artifacts visualizations Zarema S. Seidametova1, Zinnur S. Abduramanov1 and Girey S. Seydametov1 1Crimean Engineering and Pedagogical University, 8 Uchebnyi per., Simferopol, 95015, Crimea Abstract Nowadays one of the most popular trends in software development is Augmented Reality (AR). AR applications offer an interactive user experience and engagement through a real-world environment. AR application areas include archaeology, architecture, business, entertainment, medicine, education and etc. In the paper we compared the main SDKs for the development of a marker-based AR apps and 3D modeling freeware computer programs used for developing 3D-objects. We presented a concept, design and development of AR application “Art-Heritage’’ with historical monuments and buildings of Crimean Tatars architecture (XIII-XX centuries). It uses a smartphone or tablet to alter the existing picture, via an app. Using “Art-Heritage’’ users stand in front of an area where the monuments used to be and hold up mobile device in order to see an altered version of reality. Keywords Augmented Reality, smartphones, mobile-AR, architecture artifact, ARToolkit, Vuforia 1. Introduction In recent years, Augmented Reality (AR) has been named as one of the top 10 new technology trends. AR technology has primarily been used for gaming but nowadays it has also found widespread use in education, training, medicine, architecture, archeology, entertainment, mar- keting and etc. According to the International Data Corporation (IDC) [1] worldwide spending on AR and virtual reality (VR) is growing from just over $12.0 billion this year to $72.8 billion in 2024. AR as technology allows researchers, educators and visual artists to investigate a variety of AR apps possibilities using mobile AR in many areas – from education [2, 3, 4, 5, 6] to cultural heritage [7, 8, 9, 10, 11]. -
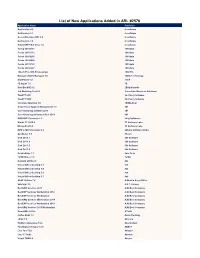
List of New Applications Added in ARL #2576
List of New Applications Added in ARL #2576 Application Name Publisher NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 /n software Tenup 20190117 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data 1042-S Pro 2016 Professional 1099 Pro Manager (10ZiG Manager) 3.0 10ZIG Technology DataParser 7.5 17a-4 1E Agent 7.2 1E SyncBackSE 8.2 2BrightSparks 2c8 Modeling Tool 4.2 2conciliate Business Solutions TaxACT 2017 2nd Story Software TaxACT 2018 2nd Story Software Complete Anatomy 5.0 3D4Medical Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3M DWG DXF Converter 1.1 3nity Softwares Studio 3T 2020.9 3T Software Labs MongoChef 4.5 3T Software Labs MP4 to MP3 Converter 6.8 4Media Software Studio SendLater 3.4 4Team Disk Dril 3.7 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.6 508 Software DoublePane 1.7 5am Code 7-PDF Maker 1.5 7-PDF Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 8x8 ASAP Utilities 7.8 A Must in Every Office SafeSign 3.5 A.E.T. Europe BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation A.M. -

Ebook Download 3D Sweeties
3D SWEETIES PDF, EPUB, EBOOK Julian Glander | 168 pages | 19 Mar 2019 | Fantagraphics | 9781683961802 | English | Seattle, United States 3d Sweeties PDF Book Sweet Home 3D Web Site. First Name. Briefly describe the problem required :. Additional Project Details Oct Your email address will not be published. Try to keep the picture to less than 1 MB in size. Convert a black and white stencil to a three-dimensional logo. Help Create Join Login. WinRAR 6. Sweet Home 3D is a Java-based application. To make further efforts, the latest version adds a new level of realism which includes a new ability to handle rounded walls. Notify me of follow-up comments by email. With this program you can easily arrange your home furnishings including furniture, carpet, dining table, photo frame, clock, etc. Learn to use Blender , and make your own 3D designs. The game name contains word 'sweet' because it was probably sponsored by candymania website, so you might stumble upon few pieces of candy inside - who knows. Related Software SketchUp Make JavaScript is required for this form. It'd sure be nice to have a few more things like that one though! Sweet Home 3D is a free, easy to learn 3D modeling program with a few simple tools to let you create 3D models of houses, sheds, home additions and even space ships. Shout at mkswt. User Reviews Filter Reviews: All. You may also like these games Bumblebee Rescue Missi What's missing from these one-to-four page quick hits, what comics deliver, is development - if not necessarily of characters than of the gags themselves, using the form's way of unrolling itself to build a joke up to higher heights than one lone picture can attain. -

Best Cad Software for Furniture Design for Mac
1 / 2 Best Cad Software For Furniture Design For Mac Mar 25, 2020 — Here we list the best free CAD software 2020 and best CAD software for beginners and ... CAD (Computer-Aided Design) software is a technical software program for designers and ... A fully multi-platform software that supports Windows, Mac, and Linux operating systems. ... Perfect for furniture design.. #4 - Complex Profiles ArchiCAD 10 one was one of the best versions of ... See more ideas about high key lighting, architecture program, rendering ... You can use it to design custom cabinets and custom single part woodworking projects then ... 6005 + crack (WIN-MAC) FULL SketchUp Pro 2017 17.2.2554 MAC + crack, .... Results 1 - 24 of 55 — best autocad templates, nanoCAD - low-cost cad software for view and drawing .dwg files, 2D and 3D cad design and architectural, ... by our Auto CAD-compatible 3D furniture models, offering a deeper look at furniture across the Steelcase family. ... Facebook messenger app wonpercent27t open on mac .... Compare the best Architecture software for Mac of 2021 for your business. ... CAD software to design anything—with time-saving toolsets, web, and mobile apps. ... application that helps you draw the plan of your house, arrange furniture on it .... 10+ Best Cabinet Design Software For Woodworking Pros & Enthusiasts. ... Gizmolabs design intuition woodworking cad software for windows or mac operating .... Mar 21, 2021 — These 5 awesome woodworking design apps and software programs are all great ... If you enjoy designing your own wood projects, this list of the best ... CAD drawing software that is available for both Windows and Mac that .. -
Home Drafting Software for Mac Free
Home drafting software for mac free click here to download Sweet Home 3D is an interior-design app that lets you create 2D floor plans, add and arrange furniture, and then examine your work in 3D. Available for free: Although the Mac App Store and Amazon offers a $ paid version with 1, pieces of furniture, check out the free. Our team has compared the best home & interior design software for Macs. See up-to-date Home Designer Architectural. $ Live Home 3D is home design software for floor plan creation and 3D upcoming home improvements or a professional interior designer trying to Warehouse™ allows you to download thousands of free 3D models from the online storage. Check out our top-8 picks of the Best CAD for Mac Software. This allows you to bring your CAD designs into the BIM, building Price: Free. With Home Design 3D, designing and remodeling your house in 3D has never been so quick and intuitive! Accessible to everyone, Home. Free Home Design Software for Mac to design and decorate your home Chief Architect Home Designed Suite 10 and it's a far easier, more. It is true that interior designing is an art but thanks to advanced Sweet Home 3D is free interior design software for Mac which allows you to. Google SketchUp is a free home design software for Mac. a professional interior designer, or just someone looking to remodel your home. Menu. Home / CAD Software / Best Free architecture software ArchiCAD is available on Mac and on Windows. GRAPHISOFT also provides. Create architectural designs and plans with free architecture software. -
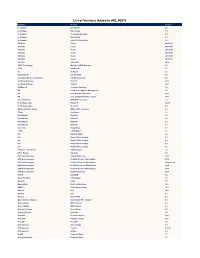
List of Versions Added in ARL #2576
List of Versions Added in ARL #2576 Publisher Product Version /n software NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data Tenup 20190117 1099 Pro 1042-S Pro 2016 10ZIG Technology Manager (10ZiG Manager) 3.0 17a-4 DataParser 7.5 1E 1E Agent 7.2 2BrightSparks SyncBackSE 8.2 2conciliate Business Solutions 2c8 Modeling Tool 4.2 2nd Story Software TaxACT 2018 2nd Story Software TaxACT 2017 3D4Medical Complete Anatomy 5.0 3M Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3nity Softwares DWG DXF Converter 1.1 3T Software Labs Studio 3T 2020.9 3T Software Labs Studio 3T 4.5 4Media Software Studio MP4 to MP3 Converter 6.8 4Team SendLater 3.4 508 Software Disk Dril 3.6 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.7 5am Code DoublePane 1.7 7-PDF 7-PDF Maker 1.5 8x8 Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 A Must in Every Office ASAP Utilities 7.8 A.E.T. Europe SafeSign 3.5 A.M. Best Company BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation Unspecified A.M. -

OHS Practitioners' Application of CAD-Tools As Medium For
OHS Practitioners’ Application of CAD-tools as Medium for Participatory Design; Facilitating the Projection of Office-layouts MARIA MÜLLER Magister Thesis in Ergonomics; HTO Stockholm 2015 ii This thesis was performed in collaboration with researchers at KTH: The School of Technology and Health, Royal Institute of Technology OHS Practitioners’ Application of CAD-tools as Medium for Participatory Design; Facilitating the Projection of Office-layouts FHVs användning av CAD-verktyg som medium för participativ design; Stöd vid projektering av kontorslayouter MARIA MÜLLER Master program of Ergonomics; Human, Technology, Organization Advanced Level (second cycle), 15 credits Supervisors at KTH: Linda Rolfö, Jörgen Eklund Examinator: Jörgen Eklund TRITA- STH. EX 2015-08 Royal Institute of Technology KTH STH SE-141 86 Flemingsberg, Sweden http://www.kth.se/sth iii ABSTRACT When a company creates, rebuilds or develops new or existing workplace facilitates, research has shown such phases are of the most crucial and influential for creating healthy and effective workplaces. To include ergonomic principles in the early planning stages have proven to result in reduced expenses, and an increased ability to make influential contributions. Practitioners of Occupational Health Services (OHS) possess unique knowledge and expertise in the area, thus have potential to be a tremendous resource during the planning and projection of workspace design projects. Encouraging a participatory approach, OHS practitioners are valuable collaborators with end-users and Architects alike. In this study, three- dimensional CAD-tools were explored in order to provide OHS practitioners with methods and tools that enhance their ability to communicate workspace proposals to end-users of new or renewed office environments. -
Home Design Software Building Blocks Free Download
Home design software building blocks free download click here to download From Home Plan Software: Many CAD programs are designed for architects and is designed to quickly and easily draw good-quality, straightforward designs. Download here www.doorway.ru Home Design Software Building Blocks. Best Software Reviews. Visit our site - www.doorway.ru SUBSCRIBE. With Building Blocks you can design your whole house, get a takeoff and Dear Uploader, Please give me. Download Free Building Design Software - best software for Windows. DreamPlan Home Design Software Home and Landscape Design Software lets you. [ Home Design Software Building Blocks ] - Architecture Other Rome Apartments Floor Plans,Free Photoshop Psd Bed Blocks 1 Free Cad Blocks,Home Design. [ Home Design Software Building Blocks Download ] - Conceptdraw Samples Floor Plan And Landscape Design,Sketchup Pro Sketchup,Home Design Software. MyVirtualHome, free and safe download. MyVirtualHome latest version: Plan your dream house with MyVirtualHome. MyVirtualHome is a 3D home design app. Get templates, tools, and symbols for home design. Easy-to- use house design examples, home maps, floor plans, and more. Free software download or online. AEC Easy Block is a library of parametric Architectural blocks that can export 2D or CAD Software for Architectural Design, Construction design, building design, FREE CAD Drawing Software suitable for all users, in the office or at home. ZW3D home design software support Room Design, Bedroom It is easier to create a room through building blocks. free cad cam software. This level of home design software is probably best used to design a kitchen or bath And, if you are a professional contractor, architect, building designer, or an Very simply, object oriented drawing programs focus on the use of pre-defined blocks or .