Windows Programming
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Screenshot Showcase 1
Volume 125 June, 2017 VirtualBox: Going Retro On PCLinuxOS Inkscape Tutorial: Creating Tiled Clones, Part Three An Un-feh-gettable Image Viewer Game Zone: Sunless Sea PCLinuxOS Family Member Spotlight: arjaybe GOG's Gems: Star Trek 25th Anniversary Tip Top Tips: HDMI Sound On Encrypt VirtualBox Virtual Machines PCLinuxOS Recipe Corner PCLinuxOS Magazine And more inside ... Page 1 In This Issue... 3 From The Chief Editor's Desk... Disclaimer 4 Screenshot Showcase 1. All the contents of The PCLinuxOS Magazine are only for general information and/or use. Such contents do not constitute advice 5 An Un-feh-gettable Image Viewer and should not be relied upon in making (or refraining from making) any decision. Any specific advice or replies to queries in any part of the magazine is/are the person opinion of such 8 Screenshot Showcase experts/consultants/persons and are not subscribed to by The PCLinuxOS Magazine. 9 Inkscape Tutorial: Create Tiled Clones, Part Three 2. The information in The PCLinuxOS Magazine is provided on an "AS IS" basis, and all warranties, expressed or implied of any kind, regarding any matter pertaining to any information, advice 11 ms_meme's Nook: Root By Our Side or replies are disclaimed and excluded. 3. The PCLinuxOS Magazine and its associates shall not be liable, 12 PCLinuxOS Recipe Corner: Skillet Chicken With Orzo & Olives at any time, for damages (including, but not limited to, without limitation, damages of any kind) arising in contract, rot or otherwise, from the use of or inability to use the magazine, or any 13 VirtualBox: Going Retro On PCLinuxOS of its contents, or from any action taken (or refrained from being taken) as a result of using the magazine or any such contents or for any failure of performance, error, omission, interruption, 30 Screenshot Showcase deletion, defect, delay in operation or transmission, computer virus, communications line failure, theft or destruction or unauthorized access to, alteration of, or use of information 31 Tip Top Tips: HDMI Sound On contained on the magazine. -

DOS Virtualized in the Linux Kernel
DOS Virtualized in the Linux Kernel Robert T. Johnson, III Abstract Due to the heavy dominance of Microsoft Windows® in the desktop market, some members of the software industry believe that new operating systems must be able to run Windows® applications to compete in the marketplace. However, running applications not native to the operating system generally causes their performance to degrade significantly. When the application and the operating system were written to run on the same machine architecture, all of the instructions in the application can still be directly executed under the new operating system. Some will only need to be interpreted differently to provide the required functionality. This paper investigates the feasibility and potential to speed up the performance of such applications by including the support needed to run them directly in the kernel. In order to avoid the impact to the kernel when these applications are not running, the needed support was built as a loadable kernel module. 1 Introduction New operating systems face significant challenges in gaining consumer acceptance in the desktop marketplace. One of the first realizations that must be made is that the majority of this market consists of non-technical users who are unlikely to either understand or have the desire to understand various technical details about why the new operating system is “better” than a competitor’s. This means that such details are extremely unlikely to sway a large amount of users towards the operating system by themselves. The incentive for a consumer to continue using their existing operating system or only upgrade to one that is backwards compatible is also very strong due to the importance of application software. -

Open WATCOM Programmer's Guide
this document downloaded from... Use of this document the wings of subject to the terms and conditions as flight in an age stated on the website. of adventure for more downloads visit our other sites Positive Infinity and vulcanhammer.net chet-aero.com Watcom FORTRAN 77 Programmer's Guide Version 1.8 Notice of Copyright Copyright 2002-2008 the Open Watcom Contributors. Portions Copyright 1984-2002 Sybase, Inc. and its subsidiaries. All rights reserved. Any part of this publication may be reproduced, transmitted, or translated in any form or by any means, electronic, mechanical, manual, optical, or otherwise, without the prior written permission of anyone. For more information please visit http://www.openwatcom.org/ Portions of this manual are reprinted with permission from Tenberry Software, Inc. ii Preface The Watcom FORTRAN 77 Programmer's Guide includes the following major components: · DOS Programming Guide · The DOS/4GW DOS Extender · Windows 3.x Programming Guide · Windows NT Programming Guide · OS/2 Programming Guide · Novell NLM Programming Guide · Mixed Language Programming · Common Problems Acknowledgements This book was produced with the Watcom GML electronic publishing system, a software tool developed by WATCOM. In this system, writers use an ASCII text editor to create source files containing text annotated with tags. These tags label the structural elements of the document, such as chapters, sections, paragraphs, and lists. The Watcom GML software, which runs on a variety of operating systems, interprets the tags to format the text into a form such as you see here. Writers can produce output for a variety of printers, including laser printers, using separately specified layout directives for such things as font selection, column width and height, number of columns, etc. -

Appendix A: Compiler Porting Tools
Appendix A: Compiler Porting Tools Vector Pascal is an open-source project. It aims to create a productive and efficient program development environment for SIMD programming. In order to validate the concepts it has been developed initially for the Intel family of processors running Linux and Microsoft Windows. However, it has been intended from the outset that the technology should be portable to other families of CPUs. This Appendix addresses some of the issues involved in porting the compiler to new systems. A.1 Dependencies The Vector Pascal compiler tool-set can be divided along two axes as shown in Figure A.l. 1. Tools can be divided into (a) those provided as part of the release and (b) those provided as part of the operating environment. (a) These are mainly written in Java, the exceptions being a small run-time library in C, a Pascal System unit and several machine descriptions. (b) These are all available as standard under Linux, and Windows versions are freely downloadable from the web. 2. Tools can further be divided into (a) those required for program prepara tion and documentation, (b) those for code translation tools and (c) those for code generator preparation. (a) The program preparation tools are the VIPER IDE described in Chapter 16, along with the standard IM_EX document preparation system, DVI viewers and the TTH tool to prepare web-enabled versions of Vector Pascal program descriptions. (b) The program translation tools are: i. The i l c g . p a s c a l Java package which contains the Pascal compiler itself and classes to support Pascal-type declarations. -

A Comparison of C++, C#, Java, and PHP in the Context of E-Learning
A Comparison of C++, C#, Java, and PHP in the context of e-learning MIKAEL OLSSON KTH Information and Communication Technology Master of Science Thesis Stockholm, Sweden 2009 TRITA-ICT-EX-2009:8 A Comparison of C++, C#, Java, and PHP in the context of e‐learning Mikael Olsson April 30, 2009 Master’s Thesis in Computer Science Royal Institute of Technology Examiner: Prof. Gerald Q. Maguire Jr. ‐ i ‐ Abstract The first part of this master thesis presents an effective method for producing video tutorials. This method was used during this thesis project to create tutorials on the e- learning site PVT (http://www.programmingvideotutorials.com). Part one also discloses how the production method was developed and how tutorials produced using this method compare to professional video tutorials. Finally, it evaluates the result of this thesis work and the efficiency of the production method. The second part of this thesis compares the syntactical similarities and differences between four of the languages taught via video tutorials for PVT. These languages are: C++, C#, Java, and PHP. The purpose of this comparison is to provide a bridge for programmers knowing one of these languages to rapidly learn one or more of the other languages. The reason why this would be necessary is because there is no single language suited for every area of software development. Knowing a multitude of languages gives a programmer a wider range of job opportunities and more choices in how to solve their problems. Part two of the thesis also includes a comparison of Java and C# in the context of a video tutorial series that shows how to build a basic text editor. -

Comparative Studies of 10 Programming Languages Within 10 Diverse Criteria
Department of Computer Science and Software Engineering Comparative Studies of 10 Programming Languages within 10 Diverse Criteria Jiang Li Sleiman Rabah Concordia University Concordia University Montreal, Quebec, Concordia Montreal, Quebec, Concordia [email protected] [email protected] Mingzhi Liu Yuanwei Lai Concordia University Concordia University Montreal, Quebec, Concordia Montreal, Quebec, Concordia [email protected] [email protected] COMP 6411 - A Comparative studies of programming languages 1/139 Sleiman Rabah, Jiang Li, Mingzhi Liu, Yuanwei Lai This page was intentionally left blank COMP 6411 - A Comparative studies of programming languages 2/139 Sleiman Rabah, Jiang Li, Mingzhi Liu, Yuanwei Lai Abstract There are many programming languages in the world today.Each language has their advantage and disavantage. In this paper, we will discuss ten programming languages: C++, C#, Java, Groovy, JavaScript, PHP, Schalar, Scheme, Haskell and AspectJ. We summarize and compare these ten languages on ten different criterion. For example, Default more secure programming practices, Web applications development, OO-based abstraction and etc. At the end, we will give our conclusion that which languages are suitable and which are not for using in some cases. We will also provide evidence and our analysis on why some language are better than other or have advantages over the other on some criterion. 1 Introduction Since there are hundreds of programming languages existing nowadays, it is impossible and inefficient -

Cygwin Information.Pages
The Cygwin distribution Caia under Windows For those of you, who don’t want to install Linux on your computer, it is possible to install and use Cygwin. Cygwin emulates Linux and starts up with the bash terminal shell. This makes it possible to compile and link GNU sources in the same way as under Linux. You can use the same makefiles and it produces, of course, Windows executables. Some knowledge about Linux is necessary! For more information and downloads, please see: www.cygwin.com. What is Cygwin needed for? Well, for the players, referee and manager it actually doesn’t matter. They can be compiled and linked in the normal way: C source can be build with DJGPP or DEV C++, Pascal source with Freepascal. However, the caiaio must be created with Cygwin in order to let things work properly. Which version of Cygwin do I need? We have precompiled and linked our executables with cygwin1.dll file version 1005.25.0.0. That one was included in the distribution of 29 December 2007. Make sure you use an update of Cygwin which is the same or newer. How to install Caia? In exactly the same way as in the Linux distribution: • tar –xzf caia_<namegame>_cygwin.tar.gz • caia_install_<namegame>/install_game.sh <namegame> Differences The Cygwin distribution is almost the same as the Linux distribution. The differences are: • The executables are compiled and linked for Windows. • The names of the executables need to have .exe as a suffix • The time measurements are less accurate under Cygwin. Whereas under Linux time is measured in microseconds, under Cygwin it is accurate up to 55 milliseconds. -

Link IDE : a Real Time Collaborative Development Environment
San Jose State University SJSU ScholarWorks Master's Projects Master's Theses and Graduate Research Spring 2012 Link IDE : A Real Time Collaborative Development Environment Kevin Grant San Jose State University Follow this and additional works at: https://scholarworks.sjsu.edu/etd_projects Part of the Computer Sciences Commons Recommended Citation Grant, Kevin, "Link IDE : A Real Time Collaborative Development Environment" (2012). Master's Projects. 227. DOI: https://doi.org/10.31979/etd.rqpj-pj3k https://scholarworks.sjsu.edu/etd_projects/227 This Master's Project is brought to you for free and open access by the Master's Theses and Graduate Research at SJSU ScholarWorks. It has been accepted for inclusion in Master's Projects by an authorized administrator of SJSU ScholarWorks. For more information, please contact [email protected]. Link IDE : A Real Time Collaborative Development Environment A Project Report Presented to The Faculty of the Department of Computer Science San José State University In Partial Fulfillment of the Requirements for the Degree Master of Science in Computer Science by Kevin Grant May 2012 1 © 2012 Kevin Grant ALL RIGHTS RESERVED 2 SAN JOSE STATE UNIVERSITY The Undersigned Project Committee Approves the Project Titled Link : A Real Time Collaborative Development Environment by Kevin Grant APPROVED FOR THE DEPARTMENT OF COMPUTER SCIENCE SAN JOSÉ STATE UNIVERSITY May 2012 ------------------------------------------------------------------------------------------------------------ Dr. Soon Tee Teoh, Department -
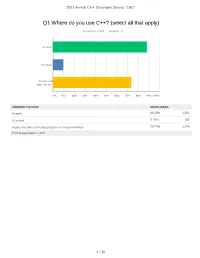
Q1 Where Do You Use C++? (Select All That Apply)
2021 Annual C++ Developer Survey "Lite" Q1 Where do you use C++? (select all that apply) Answered: 1,870 Skipped: 3 At work At school In personal time, for ho... 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES At work 88.29% 1,651 At school 9.79% 183 In personal time, for hobby projects or to try new things 73.74% 1,379 Total Respondents: 1,870 1 / 35 2021 Annual C++ Developer Survey "Lite" Q2 How many years of programming experience do you have in C++ specifically? Answered: 1,869 Skipped: 4 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 7.60% 142 3-5 years 20.60% 385 6-10 years 20.71% 387 10-20 years 30.02% 561 >20 years 21.08% 394 TOTAL 1,869 2 / 35 2021 Annual C++ Developer Survey "Lite" Q3 How many years of programming experience do you have overall (all languages)? Answered: 1,865 Skipped: 8 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 1.02% 19 3-5 years 12.17% 227 6-10 years 22.68% 423 10-20 years 29.71% 554 >20 years 34.42% 642 TOTAL 1,865 3 / 35 2021 Annual C++ Developer Survey "Lite" Q4 What types of projects do you work on? (select all that apply) Answered: 1,861 Skipped: 12 Gaming (e.g., console and.. -

Programming with Windows Forms
A P P E N D I X A ■ ■ ■ Programming with Windows Forms Since the release of the .NET platform (circa 2001), the base class libraries have included a particular API named Windows Forms, represented primarily by the System.Windows.Forms.dll assembly. The Windows Forms toolkit provides the types necessary to build desktop graphical user interfaces (GUIs), create custom controls, manage resources (e.g., string tables and icons), and perform other desktop- centric programming tasks. In addition, a separate API named GDI+ (represented by the System.Drawing.dll assembly) provides additional types that allow programmers to generate 2D graphics, interact with networked printers, and manipulate image data. The Windows Forms (and GDI+) APIs remain alive and well within the .NET 4.0 platform, and they will exist within the base class library for quite some time (arguably forever). However, Microsoft has shipped a brand new GUI toolkit called Windows Presentation Foundation (WPF) since the release of .NET 3.0. As you saw in Chapters 27-31, WPF provides a massive amount of horsepower that you can use to build bleeding-edge user interfaces, and it has become the preferred desktop API for today’s .NET graphical user interfaces. The point of this appendix, however, is to provide a tour of the traditional Windows Forms API. One reason it is helpful to understand the original programming model: you can find many existing Windows Forms applications out there that will need to be maintained for some time to come. Also, many desktop GUIs simply might not require the horsepower offered by WPF. -

Pdftk Server Redistribution Agreement Version
SOFTWARE LICENSE AND DISTRIBUTION AGREEMENT Steward and Lee, LLC PDFtk Server Redistribution License VERSION 2.0 Only by delivering a valid PDFtk Server Redistribution License serial number (ªLicense Serial Numberº) to Licensee does PDF Labs accept the terms and conditions of this Agreement with Licensee. By making the payment in paragraph 2.2.2 or by utilizing a License Serial Number, Licensee acknowledges that Licensee has read, understood and accepted the terms and conditions of this Agreement with PDF Labs. THIS SOFTWARE LICENSE AGREEMENT ("Agreement") is made by and between the individual, company or legal entity that is licensing the Licensed Software ("Licensee"), and Steward and Lee, LLC ("PDF Labs"), a company with primary offices located in McKinney, Texas, USA. 1 DEFINITIONS. 1.1 "PDF Labs Website" shall mean http://www.pdflabs.com. 1.2 "Combined Product" shall mean the product created by Licensee by incorporating or embedding the Licensed Software into third party software. 1.3 "Effective Date" shall mean the date on which this Agreement is accepted by Licensee. 1.4 "Licensed Software" shall mean PDFtk Server in machine executable form and source code, its documentation, and any bug fixes or other changes provided to Licensee as available on the PDF Labs Website. 1.5 "Specifications" shall mean the Licensed Software API specifications and help documentation, available from the PDF Labs Website. 1.6 "Sub-license Agreement" shall mean any agreement entered into by and between Licensee and any other individual or entity under which such individual or entity is granted a sub-license to the Combined Product. -

8 C# Development Tools
Object Oriented Programming using C# C# Development Tools 8 C# Development Tools Introduction This chapter will introduce the reader to several development tools that support the development of large scale C# systems. We will also consider the importance of documentation and show tools can be used to generate documentation for systems you create (almost automatically). Objectives By the end of this chapter you will be able to…. • Find details of several professional and free interactive development environments • Understand the importance of the software documentation tools and the value of embedding XML comments within your code. • Write XML comments and generate automatic documentation for your programs. This chapter consists of eight sections :- 1) Tools for Writing C# Programs…. 2) Microsoft Visual Studio 3) SharpDevelop 4) Automatic Documentation 5) Sandcastle Help File Builder 6) GhostDoc 7) Adding Namespace Comments 8) Summary 8.1 Tools for Writing C# Programs Whatever mode of execution is employed (see section 1.7), programmers can work with a variety of tools to create source code. It is possible to write C# programs using simple discrete tools such as a plain text editor (e.g. Notepad) and a separate compiler invoked manually as required. However virtually all programmers would use a powerful Integrated Development Environment (IDE) which use compilers and other standard tools behind a seamless interface. Even more sophisticated tools Computer Aided Software Engineering (CASE) tools exist which integrate the implementation process with other phases of the software development lifecycle. CASE tools could take UML class diagrams, generated as part of the software analysis and design phase, and generate classes and method stubs automatically saving some of the effort required to write the C# code (ie.