Transactions - ACID
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Not ACID, Not BASE, but SALT a Transaction Processing Perspective on Blockchains
Not ACID, not BASE, but SALT A Transaction Processing Perspective on Blockchains Stefan Tai, Jacob Eberhardt and Markus Klems Information Systems Engineering, Technische Universitat¨ Berlin fst, je, [email protected] Keywords: SALT, blockchain, decentralized, ACID, BASE, transaction processing Abstract: Traditional ACID transactions, typically supported by relational database management systems, emphasize database consistency. BASE provides a model that trades some consistency for availability, and is typically favored by cloud systems and NoSQL data stores. With the increasing popularity of blockchain technology, another alternative to both ACID and BASE is introduced: SALT. In this keynote paper, we present SALT as a model to explain blockchains and their use in application architecture. We take both, a transaction and a transaction processing systems perspective on the SALT model. From a transactions perspective, SALT is about Sequential, Agreed-on, Ledgered, and Tamper-resistant transaction processing. From a systems perspec- tive, SALT is about decentralized transaction processing systems being Symmetric, Admin-free, Ledgered and Time-consensual. We discuss the importance of these dual perspectives, both, when comparing SALT with ACID and BASE, and when engineering blockchain-based applications. We expect the next-generation of decentralized transactional applications to leverage combinations of all three transaction models. 1 INTRODUCTION against. Using the admittedly contrived acronym of SALT, we characterize blockchain-based transactions There is a common belief that blockchains have the – from a transactions perspective – as Sequential, potential to fundamentally disrupt entire industries. Agreed, Ledgered, and Tamper-resistant, and – from Whether we are talking about financial services, the a systems perspective – as Symmetric, Admin-free, sharing economy, the Internet of Things, or future en- Ledgered, and Time-consensual. -

Failures in DBMS
Chapter 11 Database Recovery 1 Failures in DBMS Two common kinds of failures StSystem filfailure (t)(e.g. power outage) ‒ affects all transactions currently in progress but does not physically damage the data (soft crash) Media failures (e.g. Head crash on the disk) ‒ damagg()e to the database (hard crash) ‒ need backup data Recoveryyp scheme responsible for handling failures and restoring database to consistent state 2 Recovery Recovering the database itself Recovery algorithm has two parts ‒ Actions taken during normal operation to ensure system can recover from failure (e.g., backup, log file) ‒ Actions taken after a failure to restore database to consistent state We will discuss (briefly) ‒ Transactions/Transaction recovery ‒ System Recovery 3 Transactions A database is updated by processing transactions that result in changes to one or more records. A user’s program may carry out many operations on the data retrieved from the database, but the DBMS is only concerned with data read/written from/to the database. The DBMS’s abstract view of a user program is a sequence of transactions (reads and writes). To understand database recovery, we must first understand the concept of transaction integrity. 4 Transactions A transaction is considered a logical unit of work ‒ START Statement: BEGIN TRANSACTION ‒ END Statement: COMMIT ‒ Execution errors: ROLLBACK Assume we want to transfer $100 from one bank (A) account to another (B): UPDATE Account_A SET Balance= Balance -100; UPDATE Account_B SET Balance= Balance +100; We want these two operations to appear as a single atomic action 5 Transactions We want these two operations to appear as a single atomic action ‒ To avoid inconsistent states of the database in-between the two updates ‒ And obviously we cannot allow the first UPDATE to be executed and the second not or vice versa. -

Damage Management in Database Management Systems
The Pennsylvania State University The Graduate School Department of Information Sciences and Technology Damage Management in Database Management Systems A Dissertation in Information Sciences and Technology by Kun Bai °c 2010 Kun Bai Submitted in Partial Ful¯llment of the Requirements for the Degree of Doctor of Philosophy May 2010 The dissertation of Kun Bai was reviewed and approved1 by the following: Peng Liu Associate Professor of Information Sciences and Technology Dissertation Adviser Chair of Committee Chao-Hsien Chu Professor of Information Sciences and Technology Thomas La Porta Distinguished Professor of Computer Science and Engineering Sencun Zhu Assistant Professor of Computer Science and Engineering Frederico Fonseca Associate Professor of Information Sciences and Technology Associate Dean, College of Information Sciences and Technology 1Signatures on ¯le in the Graduate School. iii Abstract In the past two decades there have been many advances in the ¯eld of computer security. However, since vulnerabilities cannot be completely removed from a system, successful attacks often occur and cause damage to the system. Despite numerous tech- nological advances in both security software and hardware, there are many challenging problems that still limit e®ectiveness and practicality of existing security measures. As Web applications gain popularity in today's world, surviving Database Man- agement System (DBMS) from an attack is becoming even more crucial than before because of the increasingly critical role that DBMS is playing in business/life/mission- critical applications. Although signi¯cant progress has been achieved to protect the DBMS, such as the existing database security techniques (e.g., access control, integrity constraint and failure recovery, etc.,), the buniness/life/mission-critical applications still can be hit due to some new threats towards the back-end DBMS. -

ACID, Transactions
ECE 650 Systems Programming & Engineering Spring 2018 Database Transaction Processing Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) Transaction Processing Systems • Systems with large DB’s; many concurrent users – As a result, many concurrent database transactions – E.g. Reservation systems, banking, credit card processing, stock markets, supermarket checkout • Need high availability and fast response time • Concepts – Concurrency control and recovery – Transactions and transaction processing – ACID properties (desirable for transactions) – Schedules of transactions and recoverability – Serializability – Transactions in SQL 2 Single-User vs. Multi-User • DBMS can be single-user or multi-user – How many users can use the system concurrently? – Most DBMSs are multi-user (e.g. airline reservation system) • Recall our concurrency lectures (similar issues here) – Multiprogramming – Interleaved execution of multiple processes – Parallel processing (if multiple processor cores or HW threads) A A B B C CPU1 D CPU2 t1 t2 t3 t4 time Interleaved concurrency is model we will assume 3 Transactions • Transaction is logical unit of database processing – Contains ≥ 1 access operation – Operations: insertion, deletion, modification, retrieval • E.g. things that happen as part of the queries we’ve learned • Specifying database operations of a transaction: – Can be embedded in an application program – Can be specified interactively via a query language like SQL – May mark transaction boundaries by enclosing operations with: • “begin transaction” and “end transaction” • Read-only transaction: – No database update operations; only retrieval operations 4 Database Model for Transactions • Database represented as collection of named data items – Size of data item is its “granularity” – E.g. May be field of a record (row) in a database – E.g. -

SQL Vs Nosql: a Performance Comparison
SQL vs NoSQL: A Performance Comparison Ruihan Wang Zongyan Yang University of Rochester University of Rochester [email protected] [email protected] Abstract 2. ACID Properties and CAP Theorem We always hear some statements like ‘SQL is outdated’, 2.1. ACID Properties ‘This is the world of NoSQL’, ‘SQL is still used a lot by We need to refer the ACID properties[12]: most of companies.’ Which one is accurate? Has NoSQL completely replace SQL? Or is NoSQL just a hype? SQL Atomicity (Structured Query Language) is a standard query language A transaction is an atomic unit of processing; it should for relational database management system. The most popu- either be performed in its entirety or not performed at lar types of RDBMS(Relational Database Management Sys- all. tems) like Oracle, MySQL, SQL Server, uses SQL as their Consistency preservation standard database query language.[3] NoSQL means Not A transaction should be consistency preserving, meaning Only SQL, which is a collection of non-relational data stor- that if it is completely executed from beginning to end age systems. The important character of NoSQL is that it re- without interference from other transactions, it should laxes one or more of the ACID properties for a better perfor- take the database from one consistent state to another. mance in desired fields. Some of the NOSQL databases most Isolation companies using are Cassandra, CouchDB, Hadoop Hbase, A transaction should appear as though it is being exe- MongoDB. In this paper, we’ll outline the general differences cuted in iso- lation from other transactions, even though between the SQL and NoSQL, discuss if Relational Database many transactions are execut- ing concurrently. -

Cohesity Dataplatform Protecting Individual MS SQL Databases Solution Guide
Cohesity DataPlatform Protecting Individual MS SQL Databases Solution Guide Abstract This solution guide outlines the workflow for creating backups with Microsoft SQL Server databases and Cohesity Data Platform. Table of Contents About this Guide..................................................................................................................................................................2 Intended Audience..............................................................................................................................................2 Configuration Overview.....................................................................................................................................................2 Feature Overview.................................................................................................................................................................2 Installing Cohesity Windows Agent..............................................................................................................................2 Downloading Cohesity Agent.........................................................................................................................2 Select Coheisty Windows Agent Type.........................................................................................................3 Install the Cohesity Agent.................................................................................................................................3 Cohesity Agent Setup........................................................................................................................................4 -
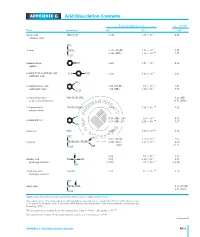
APPENDIX G Acid Dissociation Constants
harxxxxx_App-G.qxd 3/8/10 1:34 PM Page AP11 APPENDIX G Acid Dissociation Constants § ϭ 0.1 M 0 ؍ (Ionic strength ( † ‡ † Name Structure* pKa Ka pKa ϫ Ϫ5 Acetic acid CH3CO2H 4.756 1.75 10 4.56 (ethanoic acid) N ϩ H3 ϫ Ϫ3 Alanine CHCH3 2.344 (CO2H) 4.53 10 2.33 ϫ Ϫ10 9.868 (NH3) 1.36 10 9.71 CO2H ϩ Ϫ5 Aminobenzene NH3 4.601 2.51 ϫ 10 4.64 (aniline) ϪO SNϩ Ϫ4 4-Aminobenzenesulfonic acid 3 H3 3.232 5.86 ϫ 10 3.01 (sulfanilic acid) ϩ NH3 ϫ Ϫ3 2-Aminobenzoic acid 2.08 (CO2H) 8.3 10 2.01 ϫ Ϫ5 (anthranilic acid) 4.96 (NH3) 1.10 10 4.78 CO2H ϩ 2-Aminoethanethiol HSCH2CH2NH3 —— 8.21 (SH) (2-mercaptoethylamine) —— 10.73 (NH3) ϩ ϫ Ϫ10 2-Aminoethanol HOCH2CH2NH3 9.498 3.18 10 9.52 (ethanolamine) O H ϫ Ϫ5 4.70 (NH3) (20°) 2.0 10 4.74 2-Aminophenol Ϫ 9.97 (OH) (20°) 1.05 ϫ 10 10 9.87 ϩ NH3 ϩ ϫ Ϫ10 Ammonia NH4 9.245 5.69 10 9.26 N ϩ H3 N ϩ H2 ϫ Ϫ2 1.823 (CO2H) 1.50 10 2.03 CHCH CH CH NHC ϫ Ϫ9 Arginine 2 2 2 8.991 (NH3) 1.02 10 9.00 NH —— (NH2) —— (12.1) CO2H 2 O Ϫ 2.24 5.8 ϫ 10 3 2.15 Ϫ Arsenic acid HO As OH 6.96 1.10 ϫ 10 7 6.65 Ϫ (hydrogen arsenate) (11.50) 3.2 ϫ 10 12 (11.18) OH ϫ Ϫ10 Arsenious acid As(OH)3 9.29 5.1 10 9.14 (hydrogen arsenite) N ϩ O H3 Asparagine CHCH2CNH2 —— —— 2.16 (CO2H) —— —— 8.73 (NH3) CO2H *Each acid is written in its protonated form. -

Drugs and Acid Dissociation Constants Ionisation of Drug Molecules Most Drugs Ionise in Aqueous Solution.1 They Are Weak Acids Or Weak Bases
Drugs and acid dissociation constants Ionisation of drug molecules Most drugs ionise in aqueous solution.1 They are weak acids or weak bases. Those that are weak acids ionise in water to give acidic solutions while those that are weak bases ionise to give basic solutions. Drug molecules that are weak acids Drug molecules that are weak bases where, HA = acid (the drug molecule) where, B = base (the drug molecule) H2O = base H2O = acid A− = conjugate base (the drug anion) OH− = conjugate base (the drug anion) + + H3O = conjugate acid BH = conjugate acid Acid dissociation constant, Ka For a drug molecule that is a weak acid The equilibrium constant for this ionisation is given by the equation + − where [H3O ], [A ], [HA] and [H2O] are the concentrations at equilibrium. In a dilute solution the concentration of water is to all intents and purposes constant. So the equation is simplified to: where Ka is the acid dissociation constant for the weak acid + + Also, H3O is often written simply as H and the equation for Ka is usually written as: Values for Ka are extremely small and, therefore, pKa values are given (similar to the reason pH is used rather than [H+]. The relationship between pKa and pH is given by the Henderson–Hasselbalch equation: or This relationship is important when determining pKa values from pH measurements. Base dissociation constant, Kb For a drug molecule that is a weak base: 1 Ionisation of drug molecules. 1 Following the same logic as for deriving Ka, base dissociation constant, Kb, is given by: and Ionisation of water Water ionises very slightly. -

Django-Transaction-Hooks Documentation Release 0.2.1.Dev1
django-transaction-hooks Documentation Release 0.2.1.dev1 Carl Meyer December 12, 2016 Contents 1 Prerequisites 3 2 Installation 5 3 Setup 7 3.1 Using the mixin.............................................7 4 Usage 9 4.1 Notes...................................................9 5 Contributing 13 i ii django-transaction-hooks Documentation, Release 0.2.1.dev1 A better alternative to the transaction signals Django will never have. Sometimes you need to fire off an action related to the current database transaction, but only if the transaction success- fully commits. Examples: a Celery task, an email notification, or a cache invalidation. Doing this correctly while accounting for savepoints that might be individually rolled back, closed/dropped connec- tions, and idiosyncrasies of various databases, is non-trivial. Transaction signals just make it easier to do it wrong. django-transaction-hooks does the heavy lifting so you don’t have to. Contents 1 django-transaction-hooks Documentation, Release 0.2.1.dev1 2 Contents CHAPTER 1 Prerequisites django-transaction-hooks supports Django 1.6.x through 1.8.x on Python 2.6, 2.7, 3.2, 3.3 and 3.4. django-transaction-hooks has been merged into Django 1.9 and is now a built-in feature, so this third-party library should not be used with Django 1.9+. SQLite3, PostgreSQL (+ PostGIS), and MySQL are currently the only databases with built-in support; you can exper- iment with whether it works for your favorite database backend with just a few lines of code. 3 django-transaction-hooks Documentation, Release 0.2.1.dev1 4 Chapter 1. -

Transactions.Pdf
BIT 4514: Database Technology for Business Fall 2019 Database transactions 1 1 Database transactions • A database transaction is any (possibly multi-step) action that reads from and/or writes to a database – It may consist of a single SQL statement or a collection of related SQL statements ex: Adding a new lunch to the class database – requires two related INSERT statements 2 2 Transactions (cont.) • A successful transaction is one in which all of the SQL statements are completed successfully – A consistent database state is one in which all data integrity constraints are satisfied – A successful transaction changes the database from one consistent state to another 3 3 1 Transaction management • Improper or incomplete transactions can have a devastating effect on database integrity Ex: INSERT only items into the Lunch_item table • If a DBMS supports transaction management, it will roll back an inconsistent database (i.e., the result of an unsuccessful transaction) to a previous consistent state. 4 4 Properties of a transaction • Atomicity • Consistency • Isolation • Durability • Every transaction MUST exhibit these four properties 5 5 Properties of a transaction • Atomicity – The "all or nothing" property – All transaction operations must be completed i.e. a transaction is treated as a single, indivisible, logical unit of work • Consistency – When a transaction is completed, the database must be in a consistent state 6 6 2 Properties of a transaction • Isolation – Data used during the execution of a transaction cannot be used by a second -

Database Systems 09 Transaction Processing
1 SCIENCE PASSION TECHNOLOGY Database Systems 09 Transaction Processing Matthias Boehm Graz University of Technology, Austria Computer Science and Biomedical Engineering Institute of Interactive Systems and Data Science BMVIT endowed chair for Data Management Last update: May 13, 2019 2 Announcements/Org . #1 Video Recording . Since lecture 03, video/audio recording . Link in TeachCenter & TUbe . #2 Exercises . Exercise 1 graded, feedback in TC in next days 77.4% . Exercise 2 still open until May 14 11.50pm (incl. 7 late days, no submission is a mistake) 53.7% . Exercise 3 published and introduced today . #3 CS Talks x4 (Jun 17 2019, 5pm, Aula Alte Technik) . Claudia Wagner (University Koblenz‐Landau, Leibnitz Institute for the Social Sciences) . Title: Minorities in Social and Information Networks . Dinner opportunity for interested female students! INF.01014UF Databases / 706.004 Databases 1 – 09 Transaction Processing Matthias Boehm, Graz University of Technology, SS 2019 3 Announcements/Org, cont. #4 Infineon Summer School 2019 Sensor Systems . Where: Infineon Technologies Austria, Villach Carinthia, Austria . Who: BSc, MSc, PhD students from different fields including business informatics, computer science, and electrical engineering . When: Aug 26 through 30, 2019 . Application deadline: Jun 16, 2019 . #5 Poll: Date of Final Exam . We’ll move Exercise 4 to Jun 25 . Current date: Jun 24, 6pm . Alternatives: Jun 27, 4pm / 7.30pm, or week starting Jul 8 (Erasmus?) INF.01014UF Databases / 706.004 Databases 1 – 09 Transaction Processing Matthias Boehm, Graz University of Technology, SS 2019 4 Transaction (TX) Processing User 2 User 1 User 3 read/write TXs #1 Multiple users Correctness? DBS DBMS #2 Various failures Deadlocks (TX, system, media) Constraint Reliability? violations DBs Network Crash/power failure Disk failure failure . -
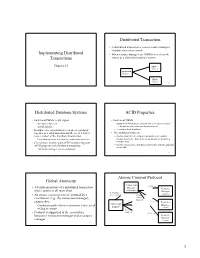
Implementing Distributed Transactions Distributed Transaction Distributed Database Systems ACID Properties Global Atomicity Atom
Distributed Transaction • A distributed transaction accesses resource managers distributed across a network Implementing Distributed • When resource managers are DBMSs we refer to the Transactions system as a distributed database system Chapter 24 DBMS at Site 1 Application Program DBMS 1 at Site 2 2 Distributed Database Systems ACID Properties • Each local DBMS might export • Each local DBMS – stored procedures, or – supports ACID properties locally for each subtransaction – an SQL interface. • Just like any other transaction that executes there • In either case, operations at each site are grouped – eliminates local deadlocks together as a subtransaction and the site is referred • The additional issues are: to as a cohort of the distributed transaction – Global atomicity: all cohorts must abort or all commit – Each subtransaction is treated as a transaction at its site – Global deadlocks: there must be no deadlocks involving • Coordinator module (part of TP monitor) supports multiple sites ACID properties of distributed transaction – Global serialization: distributed transaction must be globally serializable – Transaction manager acts as coordinator 3 4 Atomic Commit Protocol Global Atomicity Transaction (3) xa_reg • All subtransactions of a distributed transaction Manager Resource must commit or all must abort (coordinator) Manager (1) tx_begin (cohort) • An atomic commit protocol, initiated by a (4) tx_commit (5) atomic coordinator (e.g., the transaction manager), commit protocol ensures this. (3) xa_reg Resource Application – Coordinator