Data Loss Prevention Administration Guide R75.40 | 8
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
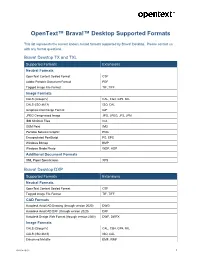
Opentext Brava! Desktop Supported Formats By
OpenText™ Brava!™ Desktop Supported Formats This list represents the current known, tested formats supported by Brava! Desktop. Please contact us with any format questions. Brava! Desktop TX and TXL Supported Formats Extensions Neutral Formats OpenText Content Sealed Format CSF Adobe Portable Document Format PDF Tagged Image File Format TIF, TIFF Image Formats CALS (Group IV) CAL, CG4, GP4, MIL CALS (ISO 8613) ISO, CAL Graphics Interchange Format GIF JPEG Compressed Image JPG, JPEG, JP2, JPM IBM MODCA Files ICA GEM Paint IMG Portable Network Graphic PNG Encapsulated PostScript PS, EPS Windows Bitmap BMP Windows Media Photo WDP, HDP Additional Document Formats XML Paper Specification XPS Brava! Desktop DXP Supported Formats Extensions Neutral Formats OpenText Content Sealed Format CSF Tagged Image File Format TIF, TIFF CAD Formats Autodesk AutoCAD Drawing (through version 2020) DWG Autodesk AutoCAD DXF (through version 2020) DXF Autodesk Design Web Format (through version 2020) DWF, DWFX Image Formats CALS (Group IV) CAL, CG4, GP4, MIL CALS (ISO 8613) ISO, CAL Enhanced Metafile EMF, WMF 2020-04 16.6.2 1 Supported Formats Extensions Graphics Interchange Format GIF JPEG Compressed Image JPG, JPEG, JP2, JPM IBM MODCA Files ICA GEM Paint IMG Portable Network Graphic PNG Windows Bitmap BMP Windows Media Photo WDP, HDP Additional Document Formats XML Paper Specification XPS Brava! Desktop CXL Supported Formats Extensions Neutral Formats OpenText Content Sealed Format CSF Adobe Portable Document Format PDF Tagged Image File Format TIF, TIFF CAD -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata -

IBM Production Imaging Edition V5.0 Add-Ons Provide Flexibility and Productivity
IBM Asia Pacific Software Announcement AP11-0062, dated February 22, 2011 IBM Production Imaging Edition V5.0 add-ons provide flexibility and productivity Table of contents 1 Overview 5 Publications 1 Key prerequisites 5 Technical information 2 Planned availability date 6 Ordering information 2 Description 12 Terms and conditions 4 Product positioning 15 Prices 5 Program number At a glance IBM® Production Imaging Edition V5.0 is available as an add-on to: • IBM FileNet® Content Manager V4.5.1 • IBM FileNet Content Manager V5.0 • IBM FileNet Business Process Manager V4.5.1 • IBM FileNet Business Process Manager V5.0 • IBM Case Manager V5.0 Overview IBM Production Imaging Edition V5.0 is available as an add-on to: • IBM FileNet Content Manager V4.5.1 • IBM FileNet Content Manager V5.0 • IBM FileNet Business Process Manager V4.5.1 • IBM FileNet Business Process Manager V5.0 • IBM Case Manager V5.0 As an add-on, IBM Production Imaging Edition delivers tools enabling users to conduct document capture, control, management, and distribution of document images, as well as image viewing, annotation, and redaction. • The IBM Production Imaging Edition Add-on for IBM FileNet Content Manager includes IBM Datacap Taskmaster, IBM FileNet Process Engine, IBM FileNet Business Process Designer, IBM FileNet Process Analyzer, IBM FileNet Business Process Simulator, IBM FileNet Business Process Tracker, IBM FileNet Business Process Connector for Microsoft® Visio, and Daeja ViewONE Pro. • The IBM Production Imaging Edition Add-on for IBM FileNet Business Process Manager includes IBM Datacap Taskmaster and Daeja ViewONE Pro. • The IBM Production Imaging Edition Add-on for IBM Case Manager includes IBM Datacap Taskmaster and Daeja ViewONE Pro. -

Image and Video Compression Coding Theory Contents
Image and Video Compression Coding Theory Contents 1 JPEG 1 1.1 The JPEG standard .......................................... 1 1.2 Typical usage ............................................. 1 1.3 JPEG compression ........................................... 2 1.3.1 Lossless editing ........................................ 2 1.4 JPEG files ............................................... 3 1.4.1 JPEG filename extensions ................................... 3 1.4.2 Color profile .......................................... 3 1.5 Syntax and structure .......................................... 3 1.6 JPEG codec example ......................................... 4 1.6.1 Encoding ........................................... 4 1.6.2 Compression ratio and artifacts ................................ 8 1.6.3 Decoding ........................................... 10 1.6.4 Required precision ...................................... 11 1.7 Effects of JPEG compression ..................................... 11 1.7.1 Sample photographs ...................................... 11 1.8 Lossless further compression ..................................... 11 1.9 Derived formats for stereoscopic 3D ................................. 12 1.9.1 JPEG Stereoscopic ...................................... 12 1.9.2 JPEG Multi-Picture Format .................................. 12 1.10 Patent issues .............................................. 12 1.11 Implementations ............................................ 13 1.12 See also ................................................ 13 1.13 References -

Digital Imaging of Biological Type Specimens a Manual of Best Practice
Digital Imaging of Biological Type Specimens A Manual of Best Practice Results from a study of the European Network for Biodiversity Information Editors: Christoph L. Häuser, Axel Steiner, Joachim Holstein & Malcolm J. Scoble Stuttgart 2005 Editors: Christoph L. Häuser, Axel Steiner, Joachim Holstein (Stuttgart) & Malcolm J. Scoble (London) Staatliches Museum für Naturkunde, Stuttgart Rosenstein 1, D-70191 Stuttgart, Germany The Natural History Museum, London Cromwell Road, London SW7 5BD, UK This publication should be cited as: HÄUSER, C.L., STEINER, A., HOLSTEIN, J. & SCOBLE, M. J. (eds.) (2005): Digital Imaging of Biological Type Specimens. A Manual of Best Practice. Results from a study of the European Network for Biodiversity Information. Stuttgart. viii + 309 pp. Contributions in this publication should be cited as: CRICK, M. (2005): Image File Management. In: HÄUSER et al. (eds.): Digital Imaging of Biological Type Specimens. A Manual of Best Practice. Results from a study of the European Network for Biodiversity Information: 41-55. Stuttgart. The European Network for Biodiversity Information (ENBI) is solely responsible for the contents of this ENBI Digital Imaging Manual, it does not represent the opinion of the European Commission and the European Commission is not responsible for any use that might be made of data from this ENBI Digital Imaging Manual. ENBI is a thematic network supported by the European Commission under the 5th Framework Programme. Contract number: EVK2-CT-2002-20020. http://www.enbi.info Any commercial products and protected brand names mentioned or recommended in this volume reflect solely the personal views of the respective authors. Individual chapters of this publication may be reproduced in any form without prior permission, provided that the source is acknowledged by citation of the author(s) and editors as indicated above. -

Data Loss Prevention. Руководство Администратора
Data Loss Prevention R75.40VS Руководство администратора 10 июля 2012г © 2012 Check Point Software Technologies Ltd. Все права защищены. Данный продукт и соответствующие документы защищены авторским правом, и распространяются по лицензированию, ограничивающему их использование, копирование, распространение и декомпиляцию. Никакая часть настоящего продукта или соответствующей документации не может воспроизводиться ни в какой форме, никакими средствами без предварительного письменного разрешения со стороны Check Point. Несмотря на все меры предосторожности, принятые при подготовке данной книги, Check Point не берет на себя ответственность за ошибки или упущения. Данное издание и описанные в нем функциональные возможности могут быть изменены без предупреждения. ИНФОРМАЦИЯ ОБ ОГРАНИЧЕНИИ ПРАВ: На использование, копирование и предоставление информации правительством действуют ограничения, установленные в подпункте (c)(1)(ii) пункта о Правах в Положении о технических данных и программном обеспечении в DFARS 252.227-7013 и FAR 52.227-19. ТОВАРНЫЕ ЗНАКИ: Список товарных знаков представлен на странице об авторском праве (http://www.checkpoint.com/copyright.html). Список соответствующих авторских прав и лицензий третьих сторон представлен в уведомлениях об авторском праве третьих сторон (http://www.checkpoint.com/3rd_party_copyright.html). Важная информация Последняя версия программного обеспечения Мы рекомендуем установить самую последнюю версию программного обеспечения, чтобы пользоваться новейшими функциональными улучшениями, исправлениями стабильности, доработками безопасности и защитой от новых угроз. Последняя версия документации Последняя версия данного документа находится по адресу: http://supportcontent.checkpoint.com/documentation_download?ID=16242 Для получения дополнительной технической информации посетите Центр технической поддержки Check Point (http://supportcenter.checkpoint.com). Больше об этой версии можно узнать на домашней странице R75.40VS (http://supportcontent.checkpoint.com/solutions?id=sk76540). История изменений Дата Описание 10 июля 2012 г. -

Autocad Driver and Peripheral Guide
Pointing Devices You can use as your pointing device a mouse, a digitizing puck, or a stylus, and it may have more than two buttons. Topics in this section Pointing Device Buttons The first 10 pointing device buttons are automatically assigned; you can reassign all except button 1, the pick button. Digitizing Tablets You can use the puck or stylus of a digitizing tablet as a pointing device, or you can trace a paper drawing into a file. Please send us your comment about this page Pointing Devices > Pointing Device Buttons > Pointing Device Buttons Concept Procedure Quick Reference Commands OPTIONS Customizes the program settings PAN Moves the view in the current viewport ZOOM Increases or decreases the apparent size of objects in the current viewport System Variables MBUTTONPAN Controls the behavior of the third button or wheel on the pointing device SHORTCUTMENU Controls whether Default, Edit, and Command mode shortcut menus are available in the drawing area ZOOMFACTOR Controls how much the magnification changes when the mouse wheel moves forward or backward Utilities No entries Command Modifiers No entries Please send us your comment about this page Pointing Devices > Digitizing Tablets > Digitizing Tablets Concept Quick Reference Commands OPTIONS Customizes the program settings REINIT Reinitializes the digitizer, digitizer input/output port, and program parameters file TABLET Calibrates, configures, and turns on and off an attached digitizing tablet System Variables TABMODE Controls the use of the tablet Utilities No entries Command Modifiers No entries Please send us your comment about this page Graphics System You can configure the graphics system to use either software or hardware acceleration. -

Role of Forensic Toolkit
i ii AccessData FTK2 User Guide AccessData Forensic Toolkit LEGAL INFORMATION AccessData Corp. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, AccessData Corp. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, AccessData Corp. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, AccessData Corp. reserves the right to make changes to any and all parts of AccessData software, at any time, without any obligation to notify any person or entity of such changes. You may not export or re-export this product in violation of any applicable laws or regulations including, without limitation, U.S. export regulations or the laws of the country in which you reside. © 2008 AccessData Corp. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted without the express written consent of the publisher. AccessData Corp. 384 South 400 West Suite 200 Lindon, Utah 84042 U.S.A. www.accessdata.com AccessData Forensic Toolkit i ACCESSDATA TRADEMARKS • AccessData is a registered trademark of AccessData Corp. • AccessData Certified Examiner is a registered trademark of AccessData Corp. • ACE is a registered trademark of AccessData Corp. • Distributed Network Attack is a registered trademark of AccessData Corp. -
Riksarkivets Föreskrifter Och Allmänna Råd (RA-FS 2009:2)
Riksarkivets författningssamling ISSN 0283-2941 Riksarkivets föreskrifter och allmänna råd om RA-FS 2009:2 tekniska krav för elektroniska handlingar Utkom från trycket (upptagningar för automatiserad behandling); den 1 juli 2009 beslutade den 30 april 2009. Riksarkivet föreskriver med stöd av 2 och 11 §§ arkivförordningen (1991:446) följande föreskrifter och allmänna råd om tekniska krav för elektroniska handlingar. 1 kap. Omfattning och tillämpning Omfattning 1§ Denna författning avser tekniska krav för elektroniska handlingar som ska tillämpas vid framställning, bevarande hos myndighet och överlämnan- de till arkivmyndighet. 2 § Författningen specificerar bestämmelserna i Riksarkivets föreskrifter och allmänna råd (RA-FS 2009:1) om elektroniska handlingar (upptagning- ar för automatiserad behandling). 3 § Myndigheten ska i tillämpliga delar använda de standarder som anges i författningen för att säkerställa ett bevarande av elektroniska handlingar. 4 § Myndigheten ska i enlighet med 4 kap. 2 § Riksarkivets föreskrifter och allmänna råd (RA-FS 2009:1) om elektroniska handlingar (upptagning- ar för automatiserad behandling) framställa elektroniska handlingar i enlig- het med kraven i denna författning. Om detta inte är möjligt ska handlingar- na senast vid överföring till bevarande uppfylla kraven i denna författning. Överföringen ska ske så snart det är möjligt. 5 § Riksarkivet kan, om särskilda skäl föreligger, föreskriva om undantag från bestämmelser i denna författning. Sådant undantag kan vara förenat med krav på kompenserande åtgärder. I vissa fall kan undantag ges för en bestämd tid. Tillämpningsområde 6 § Författningen gäller för statliga myndigheter med undantag för riksda- gens myndigheter, regeringen, Regeringskansliet och utrikesrepresentatio- nen. Med statliga myndigheter jämställs i denna författning sådana organ som avses i 2 kap. 4 § offentlighets- och sekretesslag (2009:400) när det gäller 1 RA-FS 2009:2 allmänna handlingar i den verksamhet som avses i bilagan i offentlighets- och sekretesslagen. -

Дополнения IBM Production Imaging Edition 5.0 Обеспечивают Гибкость И Эффективность Работы
Информационное письмо о программном продукте IBM Europe, Middle East and Africa № ZP11-0084 от 22 февраля 2011 г. Дополнения IBM Production Imaging Edition 5.0 обеспечивают гибкость и эффективность работы Содержание 1 Обзор 2 Описание 1 Основные условия 4 Позиционирование продукта 2 Дата выпуска Краткое описание IBM® Production Imaging Edition V5.0 доступен в виде дополнения для: • IBM FileNet® Content Manager 4.5.1 • IBM FileNet Content Manager 5.0 • IBM FileNet Business Process Manager 4.5.1 • IBM FileNet Business Process Manager 5.0 • IBM Case Manager 5.0 Обзор Продукт IBM Production Imaging Edition V5.0 доступен в виде дополнения для: • IBM FileNet Content Manager 4.5.1 • IBM FileNet Content Manager 5.0 • IBM FileNet Business Process Manager 4.5.1 • IBM FileNet Business Process Manager 5.0 • IBM Case Manager 5.0 В качестве дополнения, IBM Production Imaging Edition предоставляет инструменты для сбора документов, контроля, управления и распространения образов документов, а также просмотра образов, редактирования и добавления комментариев. • IBM Production Imaging Edition Add-on for IBM FileNet Content Manager включает IBM Datacap Taskmaster, IBM FileNet Process Engine, IBM FileNet Business Process Designer, IBM FileNet Process Analyzer, IBM FileNet Business Process Simulator, IBM FileNet Business Process Tracker, IBM FileNet Business Process Connector for Microsoft® Visio и Daeja ViewONE Pro. • IBM Production Imaging Edition Add-on for IBM FileNet Business Process Manager включает IBM Datacap Taskmaster и Daeja ViewONE Pro. • IBM Production Imaging Edition Add-on for IBM Case Manager включает IBM Datacap Taskmaster и Daeja ViewONE Pro. Основные условия Сведения о требованиях к аппаратному и программному обеспечению описаны в разделе . -

FTK Recognized File Types Document File Types
AccessData Corp. Legal Notices AccessData Corp. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, AccessData Corp. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, AccessData Corp. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, AccessData Corp. reserves the right to make changes to any and all parts of AccessData software, at any time, without any obligation to notify any person or entity of such changes. You may not export or re-export this product in violation of any applicable laws or regulations including, without limitation, U.S. export regulations or the laws of the country in which you reside. © 2007 AccessData Corp. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted without the express written consent of the publisher. AccessData Corp. 384 South 400 West Lindon, Utah 84042 U.S.A. www.accessdata.com ii Forensic Toolkit User Guide AccessData Corp. AccessData Trademarks AccessData is a registered trademark of AccessData Corp. Distributed Network Attack is a registered trademark of AccessData Corp. DNA is a registered trademark of AccessData Corp. Forensic Toolkit is a registered trademark of AccessData Corp. FTK is a trademark of AccessData Corp. -

Tektronix: Glossary Video Terms and Acronyms
Glossaryvideo terms and acronyms This Glossary of Video Terms and Acronyms is a compilation of material gathered over time from numer- ous sources. It is provided "as-is" and in good faith, without any warranty as to the accuracy or currency of any definition or other information contained herein. Please contact Tektronix if you believe that any of the included material violates any proprietary rights of other parties. Video Terms and Acronyms Glossary 1-9 0H – The reference point of horizontal sync. Synchronization at a video 0.5 interface is achieved by associating a line sync datum, 0H, with every 1 scan line. In analog video, sync is conveyed by voltage levels “blacker- LUMINANCE D COMPONENT E A than-black”. 0H is defined by the 50% point of the leading (or falling) D HAD D A 1.56 µs edge of sync. In component digital video, sync is conveyed using digital 0 S codes 0 and 255 outside the range of the picture information. 0.5 T N E 0V – The reference point of vertical (field) sync. In both NTSC and PAL CHROMINANCE N COMPONENT O systems the normal sync pulse for a horizontal line is 4.7 µs. Vertical sync P M is identified by broad pulses, which are serrated in order for a receiver to O 0 0 C maintain horizontal sync even during the vertical sync interval. The start H T 3.12 µs of the first broad pulse identifies the field sync datum, 0 . O V B MOD 12.5T PULSE 1/4” Phone – A connector used in audio production that is characterized -0.5 by its single shaft with locking tip.