The La Tauronolulu in Na Maalim
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Download the Evo Barcode Recognition Server Brochure Here
eVo Barcode Recognition Server Click arrow to turn turn page to arrow Click Automatic extraction of barcode data turn page to arrow Click What is a barcode? Barcodes are an optical representation of machine readable data – they are now routinely used in all walks of life from identifying products on our supermarket shelves, tracking patients in hospitals, providing links to websites, or classifying documents and application forms. Why use barcodes on a document Scanning documents into a document management system, or workflow process can be a time consuming and repetitive task. To speed this up and provide reliable indexing, barcodes are often used to provide information about the document, or the record it relates to. A barcode on the front page of a document can also be used to split multiple pages in a document pack into discrete documents. Barcode used to identify a record Separator Page Why the need? Scanning software with the capability to a read barcode from an image can be expensive and linked to a restrictive dongle, or yearly document volume. The eVo Barcode Recognition Server simply processes an image and returns the values of the barcode it finds – it can then decide what to do with document and data. There is no limitation on the volume of images it will process, or the number of watch-folders, MFPs, or scanners it will collect output from. Images containing multiple documents can also be split based on the presence of a barcode. The following images types are supported: pdf, bmp, jpg, jpeg, png, tif, tiff, gif, ico. -

ITG Barcode Generator
ITG Barcode Generator Copyright © 2007-2018, IT Genetics. All Rights Reserved. 3 Contents Introduction 5 1 Key Fe.a..t.u..r..e..s......................................................................................................................... 5 2 System.. .R..e..q..u..i.r.e..m...e..n..t.s............................................................................................................ 6 3 Installi.n..g................................................................................................................................ 6 4 What c.a..n.. .y..o..u.. .d..o.................................................................................................................... 6 How to Generate Barcode Labels 7 1 Genera..t.e.. .L..i.s..t........................................................................................................................ 7 2 Forma.t.t.i.n..g.. .B..a..r.c..o..d..e............................................................................................................... 9 Printing Barcodes 9 1 Printin.g.................................................................................................................................. 9 2 Chang..i.n..g.. .P...r.i.n..t.e..r. .S..e..t.t.i.n..g..s.................................................................................................... 11 Selecting Label Type 11 1 Label. .T..y..p..e..s. .S...u..p..p..o..r.t.e..d........................................................................................................ 14 Symbologies -

Barcode Symbology Reference Guide a Guide to Assist with Selecting the Barcode Symbology
omni-id.com Barcode Symbology Reference Guide A guide to assist with selecting the barcode symbology This document Provides background information pertaining to the major barcode symbologies to allow the reader to understand the features of the codes. Barcode Symbology Reference Guide omni-id.com Contents Introduction 3 Code 128 4 Code 39 4 Code 93 5 Codabar (USD-4, NW-7 and 2OF7 Code) 5 Interleaved 2 of 5 (code 25, 12OF5, ITF, 125) 5 Datamatrix 5 Aztec Codd 6 QR Code 6 PDF-417 Standard and Micro 7 2 Barcode Symbology Reference Guide omni-id.com Introduction This reference guide is intended to provide some guidance to assist with selecting the barcode symbology to be applied to the Omni-ID products during Service Bureau tag commissioning. This document Provides background information pertaining to the major barcode symbologies to allow the reader to understand the features of the codes. This guide provides information on the following barcode symbologies; • Code 128 (1-D) • Code 39 (1-D) • Code 93 (1-D) • Codabar (1-D) • Interleave 2of5 (1-D) • Datamatrix (2-D) • Aztec code (2-D) • PDF417-std and micro (2-D) • QR Code (2-D) 3 Barcode Symbology Reference Guide omni-id.com Code 128 Code 128 is one of the most popular barcode selections. Code 128 provides excellent density for all-numeric data and good density for alphanumeric data. It is often selected over Code 39 in new applications because of its density and because it offers a much larger selection of characters. The Code 128 standard is maintained by AIM (Automatic Identification Manufacturers). -

Readerware Cuecat Manual
Readerware CueCat Manual This manual will help you install your CueCat(R) barcode reader and get you started scanning your books, music and videos. Important: If you purchased your CueCat from another source, you may have received software with it, do not install this software. You do not need any additional software when using your CueCat with Readerware, and following the demise of Digital Convergence, the CueCat software will no longer work. Table of Contents Installing a PS/2 CueCat on a desktop machine (Windows and Linux)..............................2 Installing a PS/2 CueCat on a laptop (Windows and Linux)..............................................4 Installing a USB CueCat (Windows, Mac OS X and Linux)..............................................5 How to Swipe a Barcode..................................................................................................6 Troubleshooting................................................................................................................7 Readerware CueCat Manual v1.04 Page: 1 Installing a PS/2 CueCat on a desktop machine (Windows and Linux) Note: Before you begin, shut down all programs and turn off your computer. If you are installing the CueCat reader on a laptop computer, proceed to the next section. Disconnect the keyboard cable from your computer. The CueCat reader operates through the keyboard port. Make sure you do not use the mouse port. If the keyboard port on your computer doesn©t match the male connector on the CueCat reader, you can get adapters at any computer store or Radio Shack. Readerware CueCat Manual v1.04 Page: 2 Connect the male connector on the CueCat reader into the computer©s keyboard port. Match up the "notch key" for easy insertion. (Note: the male connector is the one with the protruding pins.) Connect the keyboard cable to the female connector on the CueCat reader. -

CS4070 Scanner Product Reference Guide (En)
CS4070 SCANNER PRODUCT REFERENCE GUIDE CS4070 SCANNER PRODUCT REFERENCE GUIDE MN000762A07 Revision A December 2020 ii CS4070 Scanner Product Reference Guide No part of this publication may be reproduced or used in any form, or by any electrical or mechanical means, without permission in writing. This includes electronic or mechanical means, such as photocopying, recording, or information storage and retrieval systems. The material in this manual is subject to change without notice. The software is provided strictly on an “as is” basis. All software, including firmware, furnished to the user is on a licensed basis. We grant to the user a non-transferable and non-exclusive license to use each software or firmware program delivered hereunder (licensed program). Except as noted below, such license may not be assigned, sublicensed, or otherwise transferred by the user without our prior written consent. No right to copy a licensed program in whole or in part is granted, except as permitted under copyright law. The user shall not modify, merge, or incorporate any form or portion of a licensed program with other program material, create a derivative work from a licensed program, or use a licensed program in a network without written permission. The user agrees to maintain our copyright notice on the licensed programs delivered hereunder, and to include the same on any authorized copies it makes, in whole or in part. The user agrees not to decompile, disassemble, decode, or reverse engineer any licensed program delivered to the user or any portion thereof. Zebra reserves the right to make changes to any product to improve reliability, function, or design. -
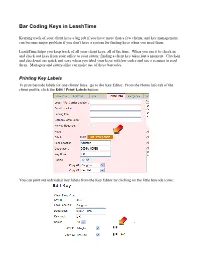
Bar Coding Keys in Leashtime
Bar Coding Keys in LeashTime Keeping track of your client keys a big job if you have more than a few clients, and key management can become major problem if you don't have a system for finding keys when you need them. LeashTime helps you keep track of all your client keys, all of the time. When you use it to check in and check out keys from your office to your sitters, finding a client key takes just a moment. Check-in and check-out are quick and easy when you label your keys with bar codes and use a scanner to read them. Managers and sitters alike can make use of these barcodes. Printing Key Labels To print barcode labels for one clients' keys, go to the Key Editor. From the Home Info tab of the client profile, click the Edit / Print Labels button: You can print out individual key labels from the Key Editor by clicking on the little barcode icons: You can save paper and time by printing out lots of key labels at once from the Key Location Report (KEYS > Key Location Report). Key Tags If you're going to print key labels, you will need key tags to slip the labels into. Search eBay for “key label tags” and you will find plenty of them. A tag that encases the label or protects the label from the elements with a window of plastic is a good idea. The largest size label tag that LeashTime currently prints labels for is sold under the Clik-It brand. -

Xerox® Freeflow® VI Compose User Guide © 2020 Xerox Corporation
Version 16.0.3.0 December 2020 702P08479 Xerox® FreeFlow® VI Compose User Guide © 2020 Xerox Corporation. All rights reserved. XEROX® and XEROX and Design®, FreeFlow®, FreeFlow Makeready®, FreeFlow Output Manager®, FreeFlow Process Manager®, VIPP®, and GlossMark® are trademarks of Xerox Corporation in the United States and/or other countries. Other company trademarks are acknowledged as follows: Adobe PDFL - Adobe PDF Library Copyright © 1987-2020 Adobe Systems Incorporated. Adobe®, the Adobe logo, Acrobat®, the Acrobat logo, Acrobat Reader®, Distiller®, Adobe PDF JobReady™, InDesign®, PostScript®, and the PostScript logo are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. All instances of the name PostScript in the text are references to the PostScript language as defined by Adobe Systems Incorporated unless otherwise stated. The name PostScript is used as a product trademark for Adobe Systems implementation of the PostScript language interpreter, and other Adobe products. Copyright 1987-2020 Adobe Systems Incorporated and its licensors. All rights reserved. Includes Adobe® PDF Libraries and Adobe Normalizer technology. Intel®, Pentium®, Centrino®, and Xeon® are registered trademarks of Intel Corporation. Intel Core™ Duo is a trademark of Intel Corporation. Intelligent Mail® is a registered trademark of the United States Postal Service. Macintosh®, Mac®, and Mac OS® are registered trademarks of Apple, Inc., registered in the United States and other countries. Elements of Apple Technical User Documentation used by permission from Apple, Inc. Novell® and NetWare® are registered trademarks of Novell, Inc. in the United States and other countries. Oracle® is a registered trademark of Oracle Corporation Redwood City, California. -

RP2/RP4* Mobile Printers
RP2/RP4* Mobile Printers User Guide * For China, models RP2B-C, RP2D-C, RP4B, RP4D-C *For Thailand models RP2B, RP2D-T, RP4B, RP4D-T *For India models RP2B, RP2D, RP4B-I, RP4D-I Disclaimer Honeywell International Inc. (“HII”) reserves the right to make changes in specifications and other information contained in this document without prior notice, and the reader should in all cases consult HII to determine whether any such changes have been made. The information in this publication does not represent a commitment on the part of HII. HII shall not be liable for technical or editorial errors or omissions contained herein; nor for incidental or consequential damages resulting from the furnishing, performance, or use of this material. HII disclaims all responsibility for the selection and use of software and/or hardware to achieve intended results. This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this document may be photocopied, reproduced, or translated into another language without the prior written consent of HII. Copyright 2017-2020 Honeywell International Inc. All rights reserved. Web Address: www.honeywellaidc.com. Trademarks Microsoft Windows 7, Windows 8, Windows Mobile, and Windows CE are trademarks or registered trademarks of Microsoft Corporation. Wavelink Avalanche is a registered trademark of Wavelink Corporation. The Bluetooth word mark and logos are owned by Bluetooth SIG, Inc. Android is a trademark of Google Inc. Other product names or marks mentioned in this document may be trademarks or registered trademarks of other companies and are the property of their respective owners. -

Useful Facts About Barcoding
Useful Facts about Barcoding When Did Barcodes Begin? (Part 1) A barcode is an optical machine-readable representation of data relating to the object to which it is attached. Originally barcodes represented data by varying the widths and spacing’s of parallel lines and may be referred to as linear or one-dimensional (1D). Later they evolved into rectangles, dots, hexagons and other geometric patterns in two dimensions (2D). Although 2D systems use a variety of symbols, they are generally referred to as barcodes as well. Barcodes originally were scanned by special optical scanners called barcode readers; later, scanners and interpretive software became available on devices including desktop printers and smartphones. Barcodes are on the leading edge of extraordinary things. They have given humans the ability to enter and extract large amounts of data in relatively small images of code. With some of the latest additions like Quick Response (QR) codes and Radio-frequency identification (RFID), it’s exciting to see how these complex image codes are being used for business and even personal use. The original idea of the barcode was first introduced in 1948 by Bernard Silver and Norman Joseph Woodland after Silver overheard the President of a local food chain talking about their need for a system to automatically read product information during checkout. Silver and Woodland took their inspiration from recognizing this rising need and began development on this product so familiar to the world now. After several attempts to create something usable, Silver and Woodland finally came up with their ”Classifying Apparatus and Method” which was patented on October 07, 1952. -
Gryphon™ I GD44XX General Purpose Corded Handheld Area Imager Bar Code Reader
Gryphon™ I GD44XX General Purpose Corded Handheld Area Imager Bar Code Reader Quick Reference Guide Datalogic Scanning, Inc. 959 Terry Street Eugene, Oregon 97402 USA Telephone: (541) 683-5700 Fax: (541) 345-7140 An Unpublished Work - All rights reserved. No part of the con- tents of this documentation or the procedures described therein may be reproduced or transmitted in any form or by any means without prior written permission of Datalogic Scanning, Inc. or its subsidiaries or affiliates ("Datalogic" or “Datalogic Scanning”). Owners of Datalogic products are hereby granted a non-exclu- sive, revocable license to reproduce and transmit this documen- tation for the purchaser's own internal business purposes. Purchaser shall not remove or alter any proprietary notices, including copyright notices, contained in this documentation and shall ensure that all notices appear on any reproductions of the documentation. Should future revisions of this manual be published, you can acquire printed versions by contacting your Datalogic represen- tative. Electronic versions may either be downloadable from the Datalogic website (www.scanning.datalogic.com) or provided on appropriate media. If you visit our website and would like to make comments or suggestions about this or other Datalogic publications, please let us know via the "Contact Datalogic" page. Disclaimer Datalogic has taken reasonable measures to provide informa- tion in this manual that is complete and accurate, however, Dat- alogic reserves the right to change any specification at any time without prior notice. Datalogic and the Datalogic logo are registered trademarks of Datalogic S.p.A. in many countries, including the U.S.A. -

Programming Guide 1400 10Th Street Plano, TX 75074 0308 US CCD LR Programming Guide Wasp Barcode Technologies
Barcode Scanning Made Easy Wasp Barcode Technologies Programming Guide 1400 10th Street Plano, TX 75074 www.waspbarcode.com 0308 US CCD LR Programming Guide Wasp Barcode Technologies Please Read Note: The Wasp® WLR8900 Series Scanners are ready to scan the most popular barcodes out of the box. This manual should only be used to make changes in the configuration of the scanner for specific applications. These scanners do not require software or drivers to operate. The scanner enters data as keyboard data. Please review this manual before scanning any of the programming barcodes in this manual. Tech Tip If you are unsure of the scanner configuration or have scanned the incorrect codes, please scan the default barcode on page 7. This will reset the scanner to its factory settings. Check Version Productivity Solutions for Small Business that Increases Productivity & Profitability • Barcode, data colection solutions • Small business focus • Profitable growth since 1986 • Over 200,000 customers • Business unit of Datalogic SPA © Copyright Wasp Barcode Technologies 2008 No part of this publication may be reproduced or transmitted in any form or by any Wasp® Barcode Technologies means without the written permission of Wasp Barcode Technologies. The information 1400 10th Street contained in this document is subject to change without notice. Plano, TX 75074 Wasp and the Wasp logo are registered trademarks of Wasp Barcode Technologies. All other Phone: 214-547-4100 • Fax: 214-547-4101 trademarks or registered trademarks are the property of their respective owners. www.waspbarcode.com WLR8900_8905Manual0308_sm.A0 6/25/08 3:38 PM Page 1 Table of Contents Chapter 1. -

CR5000 Retail Data Sheet Specifications Subject to Change Without Notice
® www.codecorp.com Performance Characteristics Physical Characteristics Focal Point Approximately 100 mm CR5000 Dimensions 5.95” H x 2.80” L x 3.55” W (151.14 mm H x 71.23 mm L x 90.30 mm W) Target Beam Single, blue targeting bar CR5000 Weight 11.2 oz (318 g) Field of View High Density Field: 30° horizontal by 20° vertical Wide Field: 50° horizontal by 33.5° vertical IP Rating 52 Optical Resolution High Density Field: 960 x 640, Wide Field: 960 x 640 Shock Withstands multiple drops of 6’ (1.8 Meters to concrete) User Environment Communication Interfaces RS232, USB 2.0 (Generic HID, HID Keyboard, Virtual Com Port) Memory Capacity 128MB Flash ROM, 32MB RAM Decode Capability 1D: Codabar, Code 11, Code 32, Code 39, Code 93, Code 128, Warranty 3 years Interleaved 2 of 5, GS1 DataBar (RSS), Hong Kong 2 of 5, Maxtrix 2 of 5, MSI Plessey, Pharmacode, Plessey, Straight 2 of 5, Telepen, Trioptic, UPC/EAN/JAN Stacked 1D: GS1 Composite (CC-A/CC-B/CC-C), MicroPDF, PDF417 2D: Aztec Code, Data Matrix, Micro QR Code, QR Code, Han Xin Accessories Proprietary 2D: GoCode® (Additional License Required) Postal Codes: Australian Post, Intelligent Mail, Japan Post, KIX • Various Cable Options Available. Visit Code, PLANET, POSTNET, UK Royal Mail www.codecorp.com/cables.php for a list of compatible cables Field Selection High Density or Wide Field Data Editing JavaScript ® * Warranty period is specific to North America and EMEA CR5000 Retail Data Sheet Specifications subject to change without notice. Copyright © 2015 Code Corporation.