The Future of Fiber-Optic Computer Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Long-Range Free-Space Optical Communication Research Challenges Dr
Long-Range Free-Space Optical Communication Research Challenges Dr. Scott A. Hamilton, MIT Lincoln Laboratory and Prof. Joseph M. Khan, Stanford University The substantial benefits of free-space optical (FSO) or laser communications (lasercom) have been well known to system designers for quite some time, c.f. [1]. The free-space channel, similar to the fiber channel, provides many benefits at optical frequencies compared to radio frequencies (RF) including extremely wide unregulated bandwidth and tightly confined beams (i.e. narrow beam divergence), both of which enable low size, weight and power (SWaP) terminals. However, significant challenges are still perceived: stochastic intensity fluctuations in a received optical signal after propagating through the atmosphere, power-starved link mode of operation, and narrow transmit beams that must be precisely pointed and tracked. Since the late 1970’s the United States [2], Europe [3] and Japan [4] have actively been developing FSO technology motivated primarily for long-haul spaceborne communication systems. While early efforts were focused on maturing FSO technology, the past decade has seen significant progress toward demonstrating the practicality of FSO for multiple applications. The first high-rate demonstration of FSO between a satellite in Geosynchronous (GEO) orbit and the ground was achieved by the US during the GeoLITE experiment in 2001. A short time later, the European Space Agency (ESA) demonstrated a 50- Mbps FSO link operating at 800-nm wavelengths between their Artemis GEO satellite and: i) another ESA spacecraft in Low-Earth orbit (LEO) in 2001 [5]; ii) a ground station located in Tenerife, Spain in 2001 [6]; and iii) an airplane flying at altitudes as low as 6,000 meters outfitted with an FSO terminal developed by France’s Astrium EADS in 2006 [7]. -

Optical Communications and Networks - Review and Evolution (OPTI 500)
Optical Communications and Networks - Review and Evolution (OPTI 500) Massoud Karbassian [email protected] Contents Optical Communications: Review Optical Communications and Photonics Why Photonics? Basic Knowledge Optical Communications Characteristics How Fibre-Optic Works? Applications of Photonics Optical Communications: System Approach Optical Sources Optical Modulators Optical Receivers Modulations Optical Networking: Review Core Networks: SONET, PON Access Networks Optical Networking: Evolution Summary 2 Optical Communications and Photonics Photonics is the science of generating, controlling, processing photons. Optical Communications is the way of interacting with photons to deliver the information. The term ‘Photonics’ first appeared in late 60’s 3 Why Photonics? Lowest Attenuation Attenuation in the optical fibre is much smaller than electrical attenuation in any cable at useful modulation frequencies Much greater distances are possible without repeaters This attenuation is independent of bit-rate Highest Bandwidth (broadband) High-speed The higher bandwidth The richer contents Upgradability Optical communication systems can be upgraded to higher bandwidth, more wavelengths by replacing only the transmitters and receivers Low Cost For fibres and maintenance 4 Fibre-Optic as a Medium Core and Cladding are glass with appropriate optical properties!!! Buffer is plastic for mechanical protection 5 How Fibre-Optic Works? Snell’s Law: n1 Sin Φ1 = n2 Sin Φ2 6 Fibre-Optics Fibre-optic cable functions -

A Survey on Optical Technologies for Iot, Smart Industry, and Smart Infrastructures
Journal of Sensor and Actuator Networks Review A Survey on Optical Technologies for IoT, Smart Industry, and Smart Infrastructures Slavisa Aleksic Institute of Communications Engineering, Leipzig University of Telecommunications (HfTL), 04277 Leipzig, Germany; [email protected]; Tel.: +49-341-3062-212 Received: 1 July 2019; Accepted: 7 September 2019; Published: 17 September 2019 Abstract: In the Internet of Things (IoT), a huge number of sensors, actuators and other equipment for data acquisition and processing will be interconnected by means of an omnipresent communication network able to efficiently support heterogeneous transmission technologies and applications. On the one hand, advanced optical communication systems, which already play a significant role in modern networks, are currently evolving to meet very high requirements of modern applications. On the other hand, there are already many ways to utilize optical components and effects for building precise, efficient, and reliable sensors. Thus, optical technologies have the potential to greatly help in realizing future smart infrastructures and systems. This paper gives an overview of currently available and emerging optical technologies for sensing and communication applications and reviews their possible application in the context of the IoT for realizing smart systems and infrastructures. Keywords: optical technology; Internet of Things (IoT); optical sensors; optical communication systems and networks 1. Introduction The main prerequisite for implementing future smart city applications and systems is the existence of an efficient and reliable smart infrastructure. Such an infrastructure integrates in an efficient and reliable manner various basic infrastructures such as (i) water distribution systems, (ii) electricity grids, and (iii) transport infrastructure (roads, railways, trams, and metro) together with information technologies, distributed smart sensing systems, and communication networks. -

Design and Optimization of Free Space Optical Networks
Design and Optimization of Free Space Optical Networks by In Keun Son A dissertation submitted to the Graduate Faculty of Auburn University in partial fulfillment of the requirements for the Degree of Doctor of Philosophy Auburn, Alabama December 13, 2010 Keywords: Free space optics, FSO, Network design, Network optimization Copyright 2010 by In Keun Son Approved by Shiwen Mao, Chair, Assistant Professor of Electrical and Computer Engineering Prathima Agrawal, Professor of Electrical and Computer Engineering Chwan–Hwa “John” Wu, Professor of Electrical and Computer Engineering Abstract Recent advances in wireless communication technologies and the explosive growth of the number and variety of mobile devices and multimedia applications motivate the development of next generation wireless networks, i.e., beyond 4G mobile systems. Indeed, the compelling demand for extensive coverage and high capacity has brought about a challenging problem to design adaptive and scalable network architectures. Some broadband wireless technologies, such as WiMAX, millimeter-wave, and free space optics (FSO), have been developed to meet this demand. Free space optics have emerged as a promising technology for next generation wireless broadband networks [1] [2]. FSO is a wireless telecommunication system that uses free space as transmission medium to transmit optical data at high bit rates. Compared with traditional wireless technologies, such optical wireless links have many advantages, including cost effectiveness, long transmission distance, license-free operation, interference immunity, high bandwidth, and so on. In this dissertation, we propose to design and optimize broadband wireless networks based on the FSO technology. We first provide a comprehensive survey of prior work. We classify prospective global FSO networks into three categories, and present current state of the art in the field and discuss the challenging issues and open problems. -
Passive Optical Networking
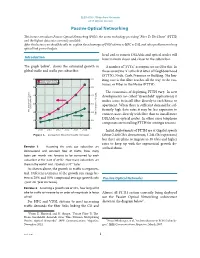
ELEX 4550 : Wide Area Networks 2014 Winter Session Passive Optical Networking is lecture introduces Passive Optical Networking (PON), the access technology providing “Fibre To e Home” (FTTH) and the highest data rates currently available. Aer this lecture you should be able to: explain the advantages of PON relative to HFC or DSL and solve problems involving optical link power budgets. head end to remote DSLAMs and optical nodes will Introduction have to move closer and closer to the subscriber. e graph below1, shows the estimated growth in A number of “FTTx” acronyms are used for this. In global traffic and traffic per subscriber. these acronyms ‘x’ is the first letter of Neighbourhood (FTTN), Node, Curb, Premises or Building. e lim- 60 600 Total global traffic iting case is that fibre reaches all the way to the cus- Traffic per subscriber tomer, or Fiber to the Home (FTTH). 50 500 ) T o r e economics of deploying FTTH vary. In new c a s f i ) f C 40 400 i h c ( t n p c developments (so-called “Greenfield” applications) it i o e f f r m a / s r s u t makes sense to install fiber directly to each house or e b l t a s y 30 300 c b b r o i a l b apartment. When there is sufficient demand for suf- x g e e l ( r a ( t k ficiently high data rates it may be less expensive to o b T 20 200 / s ) connect users directly with fibre than to install more 10 100 DSLAMs or optical nodes. -

Free Space Optics for Next-Generation Satellite Networks
1 Free Space Optics for Next-Generation Satellite Networks Aizaz U. Chaudhry and Halim Yanikomeroglu Department of Systems and Computer Engineering, Carleton University, Ottawa, Canada – K1S 5B6 Abstract–Free space optics (FSO) refers to optical wireless communications in outdoor environments. The aim of this paper is to analyze the role that FSO is envisaged to play in the creation of next-generation satellite networks. To begin with, the reader is introduced to the types of FSO links and functionalities of a basic FSO system. Next, a comparison of FSO and radio frequency (RF) technologies for inter-satellite links (ISLs) is provided, including a comparison between FSO and RF links when employed between low Earth orbit satellites. After that, the types of FSO or laser ISLs are considered, and the challenges in establishing laser ISLs, the properties of laser ISLs, and the capabilities of terminals for laser ISLs are discussed. Then, the parameters of a satellite constellation are highlighted, and different aspects of SpaceX’s upcoming mega- constellation Starlink are explored. In addition, the optical wireless satellite network that is created by utilizing laser ISLs is examined. Finally, a use case is investigated for next-generation optical wireless satellite networks that are envisioned by the mid to late 2020s. WHAT IS FREE SPACE OPTICS? foundation for today’s FSO came with the discovery of the first working laser in 1960. The first optical In optical wireless communications (OWC), an or laser ISL was demonstrated in 2008 between two optical carrier is employed to send information over low Earth orbit (LEO) satellites, Terra SAR-X and an unguided channel. -

The Key Benefits of OTN Networks Introduction Optical Transport Networks Have Been Migrating from SONET Technology to WDM Architectures Over the Past 5–10 Years
The Key Benefits of OTN Networks Introduction Optical transport networks have been migrating from SONET technology to WDM architectures over the past 5–10 years. Deploying WDM systems has allowed carriers to tap enormous capacity by carrying multiple wavelengths over a single fiber. For carriers, this means significant cost savings compared to the cost of deploying single-channel networks, or of overlaying multiple networks for each service offering. As this transition to WDM architectures occurred, it became painfully obvious that early WDM implementations lacked many key features required to properly operate and maintain these optical networks. With early WDM platforms many features, such as performance monitoring, fault detection and isolation, a standard multiplexing hierarchy and standard communication channels, were either missing or implemented in a proprietary fashion by each WDM equipment vendor. The Optical Transport Network (OTN) standards, defined by the ITU-T G.709 standards committee, were developed to add SONET-like performance monitoring, fault detection, communication channels, and multiplexing hierarchy to WDM wavelengths. The primary benefits of OTN include: • Enhanced OAM for wavelengths • Universal container supporting any service type • Standard multiplexing hierarchy • End-to-end optical transport transparency of customer traffic • Multi-level path OAM WDM Issues – The Need for OTN Standards The benefits that made SONET a robust optical transport technology, including a standardized mapping of client signals, enhanced performance monitoring at multiple layers, comprehensive fault detection and isolation, and embedded communications channels, were all missing from early WDM networks. Each vendor implemented their own proprietary methods of mapping client traffic, of detecting/isolating alarm faults, and of providing optical performance monitoring. -

Free Space Optical Communication
A SEMINAR REPORT ON Free Space optic Submitted in Partial fulfillment of the requirements for the Degree of BACHELOR OF TECHNOLOGY Affiliated to RTU, Kota IN ELECTRONICS & COMMUNICATION ENGINEERING Session: 2009 -10 SUBMITTED TO: SUBMITTED BY: H.O.D. (Electronics & Comm..) (VIII Sem.) ECE DEPARTMENT OF ELECTRONICS & COMMUNICATION ENGG. P REFACE Technology has rapidly grown in past two-three decades. An engineer without practical knowledge and skills cannot survive in this technical era. Theoretical knowledge does matter but it is the practical knowledge that is the difference between the best and the better. Organizations also prefer experienced engineers than fresher ones due to practical knowledge and industrial exposure of the former. So it can be said the industrial exposure has to be very much mandatory for engineers nowadays. The practical training is highly conductive for solid foundation for: Solid foundation of knowledge and personality. Exposure to industrial environment. Confidence building. Enhancement of creativity A CKNOWLEDGEMENT I express my sincere thanks to my seminar guide Prof. R.L.Dua (Electronics Department) for guiding me right from the inception till the successful completion of the seminar . I sincerely acknowledge him for extending their valuable guidance , support for literature , critical reviews of seminar and the report and above all the oral support he had provide to me with all stages of this seminar. C ONTENT • Introduction • History • Theory • Optical Communication • Free Space Optical Communication • Optical fiber communication • How FSO Works???? • Benefits of FSO • Comparison with FSO • Optical Access Communication • Challenges • Usage and technologies • Applications • Advantages • Conclusion I NTRODUCTION Free space optics (FSO) is an optical communication technology that uses light propagating in free space to transmit data between two points.The technology is useful where the physical connections by the means of fibre optic cable are impractical due to high costs or other considerations. -

Passive Optical Networks
ESPOO 2006 VTT PUBLICATIONS 597 VTT PUBLICATIONS 597 VTT PUBLICATIONS 581 Urala, Nina. Functional foods in Finland. Consumers' views, attitudes and willingness to use. 2005. 79 p. + app. 109 p. 582 Human practice in the life cycle of complex systems. Challenges and methods. Edited by Maaria Nuutinen & Juha Luoma. 2005. 147 p. Passive Optical Networks. Transport concepts 583 Turunen, Erja. Diagnostic tools for HVOF process optimization. 2005. 66 p. + app. 92 p. 584 Measures for improving quality and shape stability of sawn softwood timber during drying and under service conditions. Best Practice Manual to improve straightness of sawn timber. Edited by Veikko Tarvainen. 2005. 149 p. 585 Hyötyläinen, Raimo. Practical interests in theoretical consideration. Constructive methods in the study of the implementation of information systems. 2005. 159 p. 586 Koivisto, Tapio. Developing strategic innovation capability of enterprises. Theoretical and methodological outlines of intervention. 2005. 120 p. 587 Ajanko, Sirke, Moilanen, Antero & Juvonen, Juhani. Kierrätyspolttoaineiden laadun- valvonta. 2005. 59 s. 588 Ebersberger, Bernd. The Impact of Public R&D Funding. 2005. 199 p. + app. 12 p. 589 Kutinlahti, Pirjo. Universities approaching market. Intertwining scientific and entrepre- neurial goals. 2005. 187 p. + app. 4 p. 590 Jantunen, Erkki. Indirect multisignal monitoring and diagnosis of drill wear. 2005. 80 p. + app. 110 p. 591 Rauste, Yrjö. Techniques for wide-area mapping of forest biomass using radar data. 2005. 103 p. + app. 77 p. 592 Safety and reliability. Technology theme – Final report. Ed. by Veikko Rouhiainen. 2006. Sami Lallukka & Pertti Raatikainen 142 p. + app. 27 p. 593 Oedewald, Pia & Reiman, Teemu. Turvallisuuskriittisten organisaatioiden toiminnan eri- tyispiirteet. -

The Future of Optical Networking
Revista Científica Periódica – Telecomunicações ISSN 1516-2338 The Future of Optical Networking Sando Anoff When Alexander Graham Bell, the inventor of the THE FORCES SHAPING BANDWIDTH telephone, made the world’s first phone call in 1876, the transmission rate was the equivalent of about 2,000 No matter what application it is that is generating bits per second. He would be very astounded and digital traffic, most of this traffic will be carried by the proud to see how far things have come since then. In unifying optical layer (see Figure One). For this early 1998, a team of researchers in laboratories reason, the growth of various applications such as named in his honor demonstrated the world’s first telephony (whether cellular or fixed), Internet, video long-distance error-free transmission of one million transmission, computer communication and database million bits (one terabit) per second over a single access leads directly to an increase in the demand optical fiber. But this is just the beginning. In the placed on the optical network. At the same time, future, each wispy fiber may transmit close to an advances such as dense wavelength division incredible 200 terabits per second. That’s the multiplexing technology (DWDM) – which enables equivalent of more than 3,000 million phone calls. systems to transmit different wavelengths, or colors of This is truly astounding. light, on the same fiber strand -- as well as market liberalization, are making bandwidth cheaper, and this is in turn encouraging the development of applications which require even more bandwidth. For example, it is quite likely that the optical network will be increasingly used to convey high-quality video. -

OTN (G.709) Reference Guide Your Insight Into the Optical Transport Network
OTN (G.709) Reference Guide Your insight into the optical transport network th 4 Edition About EXFO EXFO is among the leading providers of next-generation test and service assurance solutions for wireless and wireline network operators and equipment manufacturers in the global telecommunications industry. The company offers innovative solutions for the development, installation, management and maintenance of converged, IP fixed and mobile networks — from the core to the edge. Key technologies supported include 3G, 4G/LTE, IMS, Ethernet, OTN, FTTx, and various optical technologies (accounting for an estimated 35% of the portable fiber-optic test market). EXFO has a staff of approxim ately 1600 people in 25 countries, supporting more than 2000 telecom customers worldwide. About the Author Mai Abou-Shaban, Product Specialist, Transport and Datacom Business Unit, brings to EXFO her extensive experience in optical transport networks on addition to working with major telecom accounts in Americas, EMEA and Asia. She holds a Bachelor degree in Electrical Engineering from Concordia University, Montreal, QC. Mai has eleven years of experience working for public and privately held companies in the areas of systems engineering, product marketing as well as in sales support. Table of Contents 1. Introduction ..............................................................................3 6. Overclocked Optical Transport Network .................37 2. Optical Transport Network (OTN) Layers ..................5 6.1 OTU2e—10GBASE-R Signal Mapping into OPU2e............38 -

Everything You Always Wanted to Know About Optical Networking – but Were Afraid to Ask
Everything You Always Wanted to Know About Optical Networking – But Were Afraid to Ask Richard A Steenbergen <[email protected]> NANOG 57 February 2013 1 Purpose of This Tutorial • Why talk about optical networking? • The Internet as an industry is largely based around fiber. • Yet many router jockeys don’t get enough exposure to it. • This leads to a wide variety of confusion, misconceptions, and errors when working with fiber optic networks. • Will this presentation make me an optical engineer? • Probably not. • The purpose of this tutorial to to touch on a little bit of every topic, from the theoretical to the practical. • But it helps to have a basic understanding of these concepts, even if you aren’t designing optical networks. 2 The Basics 3 How does Optical Fiber Work? • Optical fiber is a very thin strand of pure glass, which acts as a waveguide for light over long distances. • Uses a principal known as “Total Internal Reflection”. • When light tries to pass between two different media: 4 Total Internal Reflection • Fiber is actually composed of two layers of glass. • The “core”, which carries the actual light signal. • The “cladding”, a layer of glass surrounding the core. • The cladding has a lower refractive index than the core. • This causes Total Internal Reflection within the core. 5 Gratuitous Pretty Picture From Wikipedia 6 Inside a Single-Mode Fiber Cable Jacket (400 µm) Buffer (250 µm) Cladding (125 µm) Core (9µm) 7 What We Transmit Over Fiber • Digital signals are encoded in analog pulses of light. • Today, primarily via a method known a Non-Return to Zero (NRZ) modulation.