Ideaexchange@Uakron
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Route Chart Gurgaon for 2019-20 Route - G-01 Route Stop S
PROPOSED AC BUS ROUTE CHART GURGAON FOR 2019-20 ROUTE - G-01 ROUTE STOP S. N. BOARDING AREA STOP NAME STOP CODE CODE TIME 1 BADSHAHPUR OPP. MAMTA RESTAURANT G-002 G-01 6:25 AM 2 SOHNA ROAD VATIKA G-103 G-01 6:35 AM 3 SHEESHPAL VIHAR BEFORE T-POINT G-005 G-01 6:37 AM 4 SHEESHPAL VIHAR GATE NO.-2 G-105 G-01 6:39 AM 5 SOHNA ROAD VIPUL GREEN G-004 G-01 6:41 AM SOUTH CITY-II, BEFORE TRAFFIC LIGHT ON 6 G-003 G-01 6:43 AM SOHNA ROAD TURN TO OMAX PLAZA 7 SOHNA ROAD PARK HOSPITAL G-103 G-01 6:45 AM 8 SOHNA ROAD SOUTH CITY - B-II G-104 G-01 6:47 AM 9 SOUTH CITY-2 BLOCK-A (BUS STOP) G-106 G-01 6:49 AM 10 SOUTH CITY-2 BLOCK-B (T-POINT) G-094 G-01 6:51 AM 11 SECTOR-51 RED LIGHT (BEFORE MRIS) G-009 G-01 6:47 AM 12 SECTOR-46 NEAR HUDA MARKET G-107 G-01 6:50 AM 13 SECTOR-46 NEAR MATA MANDIR G-096 G-01 6:55 AM 14 SUBHASH CHOWK AIRFORCE SOCIETY G-102 G-03 6:58 AM BAKTAWAR GOL CHAKKAR 15 SECTOR-47 G-010 G-01 6:59 AM BUS STAND 16 SECTOR-47 CYBER PARK G-097 G-01 7:00 AM 17 SECTOR-47 OPP. D P S MAIN GATE G-011 G-01 7:02 AM AUTHORITY/ HOSPITAL / 18 SECTOR-52 SPG0043 G-01 7:05 AM BEFORE TRAFFIC LIGHT 19 SECTOR-52 AARDEE CITY-OPP. -
GURGAON - MANESAR on the Website for All Practical Purposes
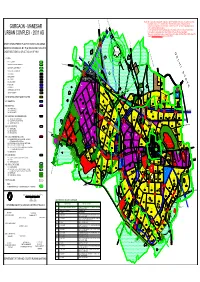
FROM FARUKHNAGAR FROM FARUKHNAGAR NOTE: This copy is a digitised copy of the original Development Plan notified in the Gazette.Though precaution has been taken to make it error free, however minor errors in the same cannot be completely ruled out. Users are accordingly advised to cross-check the scanned copies of the notified Development plans hosted GURGAON - MANESAR on the website for all practical purposes. Director Town and Country Planning, Haryana and / or its employees will not be liable under any condition TO KUNDLI for any legal action/damages direct or indirect arising from the use of this development plan. URBAN COMPLEX - 2031 AD The user is requested to convey any discrepancy observed in the data to Sh. Dharm Rana, GIS Developer (IT), SULTANPUR e-mail id- [email protected], mob. no. 98728-77583. SAIDPUR-MOHAMADPUR DRAFT DEVELOPMENT PLAN FOR CONTOLLED AREAS V-2(b) 300m 1 Km 800 500m TO BADLI BADLI TO DENOTED ON DRG.NO.-D.T.P.(G)1936 DATED 16.04.2010 5Km DELHI - HARYANA BOUNDARY PATLI HAZIPUR SULTANPUR TOURIST COMPLEX UNDER SECTION 5 (4) OF ACT NO. 41 OF 1963 AND BIRDS SANTURY D E L H I S T A T E FROM REWARI KHAINTAWAS LEGEND:- H6 BUDEDA BABRA BAKIPUR 100M. WIDE K M P EXPRESSWAY V-2(b) STATE BOUNDARY WITH 100M.GREEN BELT ON BOTH SIDE SADHRANA MAMRIPUR MUNICIPAL CORPORATION BOUNDARY FROM PATAUDI V-2(b) 30 M GREEN BELT V-2(b) H5 OLD MUNICIPAL COMMITTEE LIMIT 800 CHANDU 510 CONTROLLED AREA BOUNDARY 97 H7 400 RS-2 HAMIRPUR 30 M GREEN BELT DHANAWAS VILLAGE ABADI 800 N A J A F G A R H D R A I N METALLED ROAD V-2(b) V2 GWS CHANNEL -

File No.EIC II-221001/3/2019-O/O (SE)Sewerage System(Oandm) 647 I/3206/2021
File No.EIC II-221001/3/2019-O/o (SE)Sewerage System(OandM) 647 I/3206/2021 GURUGRAM METROPOLITAN DEVELOPMENT AUTHORITY, GURUGRAM File No. E-214/20/2018-O/o SE-Infra-II/74 Dated: 09.02.2021 To Registrar General, National Green Tribunal New Delhi Subject: Action Taken Report in the case of O.A. No.523/2019 title Vaishali Rana Chandra vs UOI Reference: This is in continuation to this office letter no. E-214/20/2018-O/o SE- Infra-II/65 dated 05.02.2021 with reference to order dt 07.09.2020 in the case of OA 523/2019 Vaishali Rana & Ors. Vs UOI & Ors and letter dated 14.10.2020 received from Sh. Anil Grover, Sr. Additional Advocate, Haryana with request to provide response to Hon’ble NGT on points mentioned as under: 1. Preparation of proper Action Plan with timelines to mitigate the effect of “reduction in recharge capacity” due to concretization of Badshahpur Drain, dealing with estimated loss of recharge capacity and contents of OA No. 523/2019 in coordination with MCG & HSVP. 2. Report in compliance of the same is attached herewith and be perused instead of report sent earlier vide office letter no. E-214/20/2018-O/o SE-Infra-II/65 dt 5.2.2021 Report submitted for kind consideration and further necessary action please. Superintending Engineer, Infra-II Gurugram Metropolitan Development Authority Gurugram CC to 1. Chief Executive Officer, GMDA, Gurugram 2. Commissioner, Municipal Corporation Gurugram 3. Chairman, HSPCB, Panchkula 4. Chief Engineer, Infra-II, GMDA, Gurugram 5. -

Integrated Mobility Plan for Gurgaon Manesar Urban Complex
December 2010 Department of Town and Country Planning (DTCP), Government of Haryana Integrated Mobility Plan for Gurgaon Manesar Urban Complex Support Document 5th Floor ‘A’ Wing, IFCI Tower Nehru Place New Delhi 110019 www.umtc.co.in Integrated Mobility Plan for Gurgaon- Manesar Urban Complex TABLE OF CONTENTS 1 PRIMARY DATA COLLECTED ............................................................................. 2 1.1 Traffic Surveys Conducted .............................................................................. 2 1.2 Survey Schedule .......................................................................................... 2 1.3 Road Network Inventory ................................................................................. 6 1.4 Screen - line Volume Counts ............................................................................ 7 1.5 Cordon Volume Counts & RSI Surveys .................................................................. 9 1.6 Road Side Interview Surveys ........................................................................... 13 1.7 Occupancy ................................................................................................ 15 1.8 Intersection Classified Volume Counts ............................................................... 17 1.9 Speed and Delay Surveys ............................................................................... 31 1.10 On- street Parking Surveys ............................................................................. 34 1.11 Off - Street Parking Surveys -

Gurgaon-Manesar Urban Complex
Trans.Inst.Indian Geographers ISSN 0970-9851 Gurgaon-Manesar Urban Complex Sheetal Sharma and Anjan Sen, Delhi Abstract Central National Capital Region/Central NCR is one of the four policy zones of National Capital Region (NCR) as per its Regional Plan 2021. Central NCR is an ‘inter-state functional region’ pivoted upon the National Capital Territory of Delhi (NCT of Delhi), and is successor to the Delhi Metropolitan Area (DMA). It comprises six urban complexes or zones, four in Haryana (Sonipat-Kundli, Bahadurgarh, Gurgaon-Manesar, and Faridabad- Ballabhgarh) and two in Uttar Pradesh (NOIDA and Ghaziabad-Loni). The study presents the levels of development in terms of urban influence on settlements, and functional hierarchy of settlements, in the Gurgaon-Manesar urban complex of Central NCR. The present study is a micro-level study, where all 120 settlements (both urban and rural) comprising Gurgaon- Manesar urban complex of Central NCR, form part of the study. The study is based upon secondary data sources, available from Census of India; at settlement level (both town and village) for the decennial years 1981, 1991 and 2001. The paper determines the level of urban influence and functional hierarchy in each settlement, at these three points of time, and analyses the changes occurring among them. The study reveals the occurrence of intra- regional differentials in demographic characteristics and infrastructural facilities. The study also emphasis on issues of development in rural settlements and growth centers, in the emerging urban complex within Central NCR. The work evaluates the role of Haryana Urban Development Authority in the current planning processes of development and formulates suitable indicators for development. -

Collection Titles
Direct e-Learning Solutions for Today’s Careers CBT Direct’s IT Pro Collection Available: 7476 Collection Titles Coming Soon: 557 .NET 2.0 for Delphi Programmers Architecture Tivoli OMEGAMON XE for DB2 Performance .NET 3.5 CD Audio Player: Create a CD Audio 3D Computer Graphics: A Mathematical Expert on z/OS Player in .NET 3.5 Using WPF and DirectSound Introduction with OpenGL A Field Guide to Digital Color .NET Development for Java Programmers "3D for the Web: Interactive 3D animation using A First Look at Solution Installation for .NET Development Security Solutions 3ds max; Flash and Director " Autonomic Computing .NET Domain-Driven Design with C#: Problem - 3D Game Programming All in One A Guide to Global E-Commerce: Issues to Design - Solution 3D Graphics ReferencePoint Suite Consider When Selling Internationally Over the .NET E-Commerce Programming 3D Modeling in AutoCAD: Creating and Using Internet .NET Enterprise Development in C#: From 3D Models in AutoCAD 2000; 2000i; 2002; A Guide to MATLAB Object-Oriented Design to Deployment Second Edition Programming .NET Enterprise Development in VB.NET: From 3D Programming for Windows: Three- A Guide to Software Configuration Design to Deployment Dimensional Graphics Programming for the Management .NET for Visual FoxPro Developers Windows Presentation Foundation A Guide to Software Package Evaluation and .NET Framework ReferencePoint Suite 3ds max 5 Bible Selection .NET Framework Solutions: In Search of the 3ds max 5 For Dummies A Guide to the Project Management Body of Lost Win32 API -

Circle Rates
g.r.p....) Year 2oL8-2or9 w.e.f. -Q-T:Q. Year of 2OL7-2OL8 Rates for the Year of 2OL8-2OL9 Rates for the year 2OL6-2OL7 Rates for the Rates of Land upto 2 Acre depth from NH-48, l\lDD lirraroam-(ahare .rveeAazA 1\oAl Mainr .rt rr, vur u6. -"vt '!!erv. District Road 10% Residentiol Commercial Agriculture Residentiol Commercial Sr. Name of Village Agriculture Residentiol Commercidl Agriculture Major District Road / Land (Rs. Per (Rs. Per Sq. Rs. Per Sq. NH-48, NPR, Gurugram No. Land (Rs. Per (Rs. Per Sq. Land (Rs. Per (Rs" Per 5q. State Highway Sohna Road Acre) Yards.) Acre) Yards.) Acrel Yards.) Yards.l 14800 3130C 18139000 27000 4200c 25% NPR 22673750 NA NA 1 Gurgaon Village 1870000c 15300 32300 18139000 2040000c 15300 32300 20400000 15300 3230C 2 lnayatpur 20400000 17000 4200c NA NA NA NA na na na 17000 42000 NA NA NA NA 3 Hidavatpur Chawani na na na na 31300 4 Sarhaul 22950000 15300 3230C 2226L500 14800 2226150C 18000 44000 25% NH-48 27826875 10% STHW 24487650 18100 3460C 5 Dundahera 22950000 18700 3570C 22261500 2226L50C 19800 4r'}OOO 25% NH-48 27826875 10% STHW 24487650 212nn 6 Moalhera 22950000 15300 32300 2226L504 14900 2226L50C i7000 4ZUUU NA NA NA NA 26400 7 Nathupur 22950000 14450 27200 2226150C 14100 2226L50C 4500c 60000 NA NA NA NA 36700 8 Sikanderpur Ghosi 20400000 15300 37400 1999200C 15000 19992000 s000c 78000 NA NA NA NA 1500c 3170C 9 Shahpur 2295000C 15300 32300 2249LOOC 2249LOOO 1800c 44000 25% NH-48 28LL3750 NA NA t796C 10 Bajghera 16150000 8s0c 18700C 15504000 820C 15504000 1500c 3s000 NA NA NA NA 12200 22000 11 SaraiAlawardi -

Wise Water Use in Gurgaon
Wise Water Use in Gurgaon An action plan for HUDA, MCG and residents Centre for Science and Environment Four Steps to Water Security Recycle and reuse sewage: Badshahpur drain Maximise large-scale rainwater harvesting Create reserved areas for water conservation aka water sanctuaries Maximise protection of Ghata Jheel Water summary • Sewage recycling can save 55 million litres per day • Restored Ghata Jheel can have a spread of around 12 hectares and water storage potential of 12 billion litres if catchment is treated and encroachments are prevented • Rainwater harvesting potential in village ponds identified is about 90 million litres • Water sanctuary can harness 21.6 billion litres Gurgaon can meet about 50% of its current water needs from these measures In-situ sewage treatment Badshahpur Drain Badshahpur Drain Objective To treat waste water from Badshahpur drain for reuse and to mitigate pollution in Najafgarh Drain. Rationale The groundwater levels in Gurgaon are dropping at an alarming rate of 2 m a year Reusing water from the drain lessens the need to extract groundwater, particularly for horticulture and construction purposes. Using natural groundwater recharge keeps water within Gurgaon’s watershed. Potentially reduces disease and offensive smells derived from the drain while maintaining wetlands improve biodiversity. Current Situation The Badshahpur Drain runs from southeastern Gurgaon toward the northwest, flowing into the Najafgarh Drain. Exposed areas of the drain from beginning to end emit offensive odors and contain floating globules of sludge, along with solid waste (plastics). Current Situation: STPs HUDA’s Sewage Treatment Plants (STPs) Between the 2 STPs, approximately 35 million gallons per month of treated sewage water is supplied through tankers to construction and other uses Behrampur STP effluent discharges directly into the drain. -

Haryana State Council for Child Welfare 2010-11
HARYANA STATE COUNCIL FOR CHILD WELFARE 2010-11 Complete Postal Address of Crèche Units Friends Colony, Model Town, Ambala City 095518321 Prem Nagar, Near Gurudwara, A/City0171-2552425 Behind Bus Stop, Village Mallour 09896173951 Panchyat Dharamshalla, Vill. Jalbhera Panchyat Building, Vill. Mastpur 0171-2858910 Ram Nagar, A.City 09315859942 Moti Nagar, A/City09466506334 Kaith Majri, Near Sheesh Ganj Gurudwara Village Bhurangpur 0171-2857530 Baldev Nagar, A/City 09896439414 Creche Baldev Nagar, A/City 0171-2556537 ® Panchyat Dharamshalla, Near Gurudwara, Vill. Brara 09315666453 Panchyat Dharamshalla, Vill. Ugala 09896809586 Community Centre, Housing Board Colony, A/Cantt. 09729486678 Dina ki Mandi, Dharamshalla, Kumhar Mandi, A/Cantt. Community Centre, Village Mandhour.0171-2540124-R Dharamshalla, Village Sultanpur Barrier 0171-2542003 Public Library, Water Tanki, Mahesh Nagar, A/Cantt.09466596553 Dharamshalla, Near Govt. S.S. School, Vill. Babyal 0171-2663904 -R Bal Bhawan, A/City 0171-2556751 (B.B) Bal Bhawan, A/Cantt. 09466662477 Gujoani, Bhiwani Ward No. 10, Bhwani Khera, Bank Colony Bank Colony, Bhiwani M.C. Colony, Guwar Factory, Bhiwani Near Nand Trust Puccawala, Ward No. 4, Tosham, Bhiwani Near Sanatan Dharm MandirPanchyati Dharmshalla Tosham-II B.R.C.M School Kaunt Road, Bhiwani Bhootoka Mandir,Ward No. 2, Panchyati Dharmshall, Bhiwani Near Bal Udhyan Public School, Vidhya Nagar, Bhiwani Khatio Ki Dharmshall, Chang, Bhiwani Room No. 13, B.T.M Chowk, Labour Colony,, Bhiwani Near Oil Mill, Gali No. 4,Brijwasi Colony, Bhiwani # 25/50,Telewara, Bhiwani Jeetu Patit, Pawan School, Shanti Nagar, Bhiwani B.T.M Chowk, Room No. 14,Labour Colony, Bhiwani Balmiki Basti Dharmshalla, Ward No. 14, Dadri, Bhiwani Near B.T.M Mill, Main Gate, Bhiwani Indira Lane, T.I.T. -
Project Report Template
MAHINDRA - TERI CENTRE OF EXCELLENCE FOR SUSTAINABLE HABITATS Water Sustainability Assessment Of Gurugram City Water Sustainability Assessment of Gurugram City © The Energy and Resources Institute 2021 Suggested format for citation T E R I. 2021 Water Sustainability Assessment of Gurugram City New Delhi: The Energy and Resources Institute. 82 pp. THE TEAM Technical Team Mr Akash Deep, Senior Manager, GRIHA Council Ms Tarishi Kaushik, Research Associate, TERI Support Team Mr Dharmender Kumar, Administrative Officer, TERI Technical Reviewer Prof. Arun Kansal, Dean (Research and Relationships), TERI School of Advanced Studies, New Delhi For more information Project Monitoring Cell T E R I Tel. 2468 2100 or 2468 2111 Darbari Seth Block E-mail [email protected] IHC Complex, Lodhi Road Fax 2468 2144 or 2468 2145 New Delhi – 110 003 Web www.teriin.org India India +91 • Delhi (0)11 Preface Literature describes urban areas as open systems with porous boundaries and highlights the importance of a systems perspective for understanding ecological sustainability of human settlement. Similarly, a socio-ecological framework helps us to understand the nexus between social equity, environmental sustainability, and economic efficiency. India is urbanizing rapidly with characteristic inequality and conflicts across the social, economic, and locational axes. Following the global pattern, Indian cities use social and natural resources of the rural hinterland and their own resources for survival and growth and, in the process, generate large amount of waste. Water is the most important ‘resource flow’ in an urban area, driven by a complex set of intersecting socio-economic, political, infrastructural, hydrological, and other factors. These drivers vary a great deal within a city and has a significant impact on the water flow and management and requires both micro and macro level study in order to address it. -

Haryana Government, Transport Department, Notification No
HARYANA GOVERNMENT TRANSPORT DEPARTMENT Notification The 11th March, 2010. No.S.O. 46/C.A.59/1988/S.99/2010.- Whereas, the Haryana Roadways, a Haryana State Transport Undertaking is providing transport services on all the inter-state and inter-state routes except certain routes on link roads in Haryana allotted to the unemployed youth through their co-operative transport societies under the Scheme 1993 and Scheme 2001, and that the need for passenger transportation has been increasing constantly which is resulting into proliferation of unauthorized operation of traffic in the State; therefore, in order to bridge the gap between demand and supply of transport services, the Governor of Haryana is of the opinion that for the purpose of providing an efficient, adequate, economical and properly co-ordinated road transport service, it is necessary and in the public interest that passenger roads transport services in general should continue to be run and operated by the State Transport Undertaking, namely Haryana Roadways to the complete exclusion of other persons except on routes specified under this scheme and those routes situated on link roads and allotted to private Transport Co-operative Societies of unemployed youth under the Scheme 1993 and Scheme 2001. Now, therefore, in exercise of the powers conferred by sub section (i) of section 99 of the Motor Vehicles Act, 1988 (Central Act 59 of 1988), and in supersession of Haryana Government, Transport Department, notification No. S.O. 90/C.A. 59 /88/S.100/93, dated the 3rd November, 1993 and notification No. SO 422/AT1/CA 59/1988/S (3)/100, dated the 19th January, 2001, the Governor of Haryana hereby formulates a proposal regarding the following policy and publishes it in the Official Gazette for information of persons likely to be affected thereby. -

Introduction to Ajax
IInnttrroodduuccttiioonn ttoo AAjjaaxx SSaanngg SShhiinn JJaavvaa TTeecchhnonollogogyy AArrcchhiitteecctt SSunun MMiiccrroossyysstteemmss,, IIncnc.. ssaanng.g.sshhiinn@@ssuunn..ccoomm wwwwww..jjaavvaapapassssiioonn..ccoomm Agenda 1.What is Rich User Experience? 2.Rich Internet Application (RIA) Technologies 3.AJAX: Real-life examples & Usage cases 4.What is and Why AJAX? 5.Technologies used in AJAX 6.Anatomy of AJAX operation 7.XMLHttpRequest Methods & Properties 8.DOM APIs & InnerHTML 9.AJAX Security 10.JavaScript debugging tools 2 Topics Covered in Other Presentations • AJAX Toolkits & Frameworks • JSON (JavaScript Object Notation) • Dojo Toolkit • DWR (Direct Web Remoting) • AJAX-enabled JSF Components • Google Web Toolkit (GWT) • jMaki • Phobos (MVC-based server-side scripting) • Ajax and Portlet/Portal • Wicket and Shale (as AJAX-aware Web applicaion frameworks) • JavaScript Programming Best Practices 3 11.. RRiicchh UUsseerr EExxppeerriieennccee ffoorr WWeebb AApppplliiccaattiioonn Rich User Experience • Take a look at a typical desktop application (Spreadsheet app, etc.) • The program responses intuitively and quickly • The program gives a user meaningful feedback's instantly > A cell in a spreadsheet changes color when you hover your mouse over it > Icons light up as mouse hovers them • Things happen naturally > No need to click a button or a link to trigger an event 5 Characteristics of Conventional Web Applications (Apps without Ajax) • “Click, wait, and refresh” user interaction > Any communication with the server forces a