A Survey on BGP Issues and Solutions
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
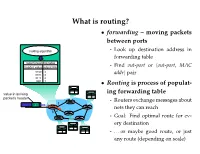
What Is Routing?
What is routing? • forwarding – moving packets between ports - Look up destination address in forwarding table - Find out-port or hout-port, MAC addri pair • Routing is process of populat- ing forwarding table - Routers exchange messages about nets they can reach - Goal: Find optimal route for ev- ery destination - . or maybe good route, or just any route (depending on scale) Routing algorithm properties • Static vs. dynamic - Static: routes change slowly over time - Dynamic: automatically adjust to quickly changing network conditions • Global vs. decentralized - Global: All routers have complete topology - Decentralized: Only know neighbors & what they tell you • Intra-domain vs. Inter-domain routing - Intra-: All routers under same administrative control - Intra-: Scale to ∼100 networks (e.g., campus like Stanford) - Inter-: Decentralized, scale to Internet Optimality A 6 1 3 2 F 1 E B 4 1 9 C D • View network as a graph • Assign cost to each edge - Can be based on latency, b/w, utilization, queue length, . • Problem: Find lowest cost path between two nodes - Must be computed in distributed way Distance Vector • Local routing algorithm • Each node maintains a set of triples - (Destination, Cost, NextHop) • Exchange updates w. directly connected neighbors - periodically (on the order of several seconds to minutes) - whenever table changes (called triggered update) • Each update is a list of pairs: - (Destination, Cost) • Update local table if receive a “better” route - smaller cost - from newly connected/available neighbor • Refresh existing -

The Routing Table V1.12 – Aaron Balchunas 1
The Routing Table v1.12 – Aaron Balchunas 1 - The Routing Table - Routing Table Basics Routing is the process of sending a packet of information from one network to another network. Thus, routes are usually based on the destination network, and not the destination host (host routes can exist, but are used only in rare circumstances). To route, routers build Routing Tables that contain the following: • The destination network and subnet mask • The “next hop” router to get to the destination network • Routing metrics and Administrative Distance The routing table is concerned with two types of protocols: • A routed protocol is a layer 3 protocol that applies logical addresses to devices and routes data between networks. Examples would be IP and IPX. • A routing protocol dynamically builds the network, topology, and next hop information in routing tables. Examples would be RIP, IGRP, OSPF, etc. To determine the best route to a destination, a router considers three elements (in this order): • Prefix-Length • Metric (within a routing protocol) • Administrative Distance (between separate routing protocols) Prefix-length is the number of bits used to identify the network, and is used to determine the most specific route. A longer prefix-length indicates a more specific route. For example, assume we are trying to reach a host address of 10.1.5.2/24. If we had routes to the following networks in the routing table: 10.1.5.0/24 10.0.0.0/8 The router will do a bit-by-bit comparison to find the most specific route (i.e., longest matching prefix). -

P2P Resource Sharing in Wired/Wireless Mixed Networks 1
INT J COMPUT COMMUN, ISSN 1841-9836 Vol.7 (2012), No. 4 (November), pp. 696-708 P2P Resource Sharing in Wired/Wireless Mixed Networks J. Liao Jianwei Liao College of Computer and Information Science Southwest University of China 400715, Beibei, Chongqing, China E-mail: [email protected] Abstract: This paper presents a new routing protocol called Manager-based Routing Protocol (MBRP) for sharing resources in wired/wireless mixed networks. MBRP specifies a manager node for a designated sub-network (called as a group), in which all nodes have the similar connection properties; then all manager nodes are employed to construct the backbone overlay network with ring topology. The manager nodes act as the proxies between the internal nodes in the group and the external world, that is not only for centralized management of all nodes to a certain extent, but also for avoiding the messages flooding in the whole network. The experimental results show that compared with Gnutella2, which uses super-peers to perform similar management work, the proposed MBRP has less lookup overhead including lookup latency and lookup hop count in the most of cases. Besides, the experiments also indicate that MBRP has well configurability and good scaling properties. In a word, MBRP has less transmission cost of the shared file data, and the latency for locating the sharing resources can be reduced to a great extent in the wired/wireless mixed networks. Keywords: wired/wireless mixed network, resource sharing, manager-based routing protocol, backbone overlay network, peer-to-peer. 1 Introduction Peer-to-Peer technology (P2P) is a widely used network technology, the typical P2P network relies on the computing power and bandwidth of all participant nodes, rather than a few gathered and dedicated servers for central coordination [1, 2]. -

Well-Known TCP Port Numbers Page 1 of 2
Webopedia: Well-Known TCP Port Numbers Page 1 of 2 You are in the: Small Business Channel Jump to Website Enter a keyword... ...or choose a category. Go! choose one... Go! Home Term of the Day Well-Known TCP Port New Terms New Links Quick Reference Numbers Did You Know? Search Tool Tech Support In TCP/IP and UDP networks, a port is an endpoint to a logical connection and the way Webopedia Jobs a client program specifies a specific server program on a computer in a network. Some About Us ports have numbers that are preassigned to them by the IANA, and these are known as Link to Us well-known ports (specified in RFC 1700). Port numbers range from 0 to 65536, but Advertising only ports numbers 0 to 1024 are reserved for privileged services and designated as well-known ports. This list of well-known port numbers specifies the port used by the Compare Prices server process as its contact port. Port Number Description Submit a URL 1 TCP Port Service Multiplexer (TCPMUX) Request a Term Report an Error 5 Remote Job Entry (RJE) 7 ECHO 18 Message Send Protocol (MSP) 20 FTP -- Data 21 FTP -- Control Internet News 22 SSH Remote Login Protocol Internet Investing IT 23 Telnet Windows Technology Linux/Open Source 25 Simple Mail Transfer Protocol (SMTP) Developer Interactive Marketing 29 MSG ICP xSP Resources Small Business 37 Time Wireless Internet Downloads 42 Host Name Server (Nameserv) Internet Resources Internet Lists 43 WhoIs International EarthWeb 49 Login Host Protocol (Login) Career Resources 53 Domain Name System (DNS) Search internet.com Advertising -
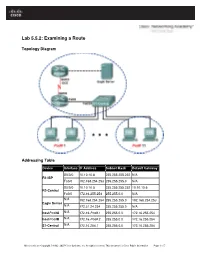
Lab 5.5.2: Examining a Route
Lab 5.5.2: Examining a Route Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S0/0/0 10.10.10.6 255.255.255.252 N/A R1-ISP Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0 10.10.10.5 255.255.255.252 10.10.10.6 R2-Central Fa0/0 172.16.255.254 255.255.0.0 N/A N/A 192.168.254.254 255.255.255.0 192.168.254.253 Eagle Server N/A 172.31.24.254 255.255.255.0 N/A host Pod# A N/A 172.16. Pod#.1 255.255.0.0 172.16.255.254 host Pod# B N/A 172.16. Pod#. 2 255.255.0.0 172.16.255.254 S1-Central N/A 172.16.254.1 255.255.0.0 172.16.255.254 All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 CCNA Exploration Network Fundamentals: OSI Network Layer Lab 5.5.1: Examining a Route Learning Objectives Upon completion of this lab, you will be able to: • Use the route command to modify a Windows computer routing table. • Use a Windows Telnet client command telnet to connect to a Cisco router. • Examine router routes using basic Cisco IOS commands. Background For packets to travel across a network, a device must know the route to the destination network. This lab will compare how routes are used in Windows computers and the Cisco router. -

NBAR2 Standard Protocol Pack 1.0
NBAR2 Standard Protocol Pack 1.0 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 © 2013 Cisco Systems, Inc. All rights reserved. CONTENTS CHAPTER 1 Release Notes for NBAR2 Standard Protocol Pack 1.0 1 CHAPTER 2 BGP 3 BITTORRENT 6 CITRIX 7 DHCP 8 DIRECTCONNECT 9 DNS 10 EDONKEY 11 EGP 12 EIGRP 13 EXCHANGE 14 FASTTRACK 15 FINGER 16 FTP 17 GNUTELLA 18 GOPHER 19 GRE 20 H323 21 HTTP 22 ICMP 23 IMAP 24 IPINIP 25 IPV6-ICMP 26 IRC 27 KAZAA2 28 KERBEROS 29 L2TP 30 NBAR2 Standard Protocol Pack 1.0 iii Contents LDAP 31 MGCP 32 NETBIOS 33 NETSHOW 34 NFS 35 NNTP 36 NOTES 37 NTP 38 OSPF 39 POP3 40 PPTP 41 PRINTER 42 RIP 43 RTCP 44 RTP 45 RTSP 46 SAP 47 SECURE-FTP 48 SECURE-HTTP 49 SECURE-IMAP 50 SECURE-IRC 51 SECURE-LDAP 52 SECURE-NNTP 53 SECURE-POP3 54 SECURE-TELNET 55 SIP 56 SKINNY 57 SKYPE 58 SMTP 59 SNMP 60 SOCKS 61 SQLNET 62 SQLSERVER 63 SSH 64 STREAMWORK 65 NBAR2 Standard Protocol Pack 1.0 iv Contents SUNRPC 66 SYSLOG 67 TELNET 68 TFTP 69 VDOLIVE 70 WINMX 71 NBAR2 Standard Protocol Pack 1.0 v Contents NBAR2 Standard Protocol Pack 1.0 vi CHAPTER 1 Release Notes for NBAR2 Standard Protocol Pack 1.0 NBAR2 Standard Protocol Pack Overview The Network Based Application Recognition (NBAR2) Standard Protocol Pack 1.0 is provided as the base protocol pack with an unlicensed Cisco image on a device. -

Routing Tables
Routing Tables A routing table is a grouping of information stored on a networked computer or network router that includes a list of routes to various network destinations. The data is normally stored in a database table and in more advanced configurations includes performance metrics associated with the routes stored in the table. Additional information stored in the table will include the network topology closest to the router. Although a routing table is routinely updated by network routing protocols, static entries can be made through manual action on the part of a network administrator. How Does a Routing Table Work? Routing tables work similar to how the post office delivers mail. When a network node on the Internet or a local network needs to send information to another node, it first requires a general idea of where to send the information. If the destination node or address is not connected directly to the network node, then the information has to be sent via other network nodes. In order to save resources, most local area network nodes will not maintain a complex routing table. Instead, they will send IP packets of information to a local network gateway. The gateway maintains the primary routing table for the network and will send the data packet to the desired location. In order to maintain a record of how to route information, the gateway will use a routing table that keeps track of the appropriate destination for outgoing data packets. All routing tables maintain routing table lists for the reachable destinations from the router’s location. -

Secure Border Gateway Protocol (S-BGP) — Real World Performance and Deployment Issues
Secure Border Gateway Protocol (S-BGP) — Real World Performance and Deployment Issues Stephen Kent, Charles Lynn, Joanne Mikkelson, and Karen Seo BBN Technologies Abstract configuration information, or routing databases may be The Border Gateway Protocol (BGP), which is used to modified or replaced illicitly via unauthorized access to distribute routing information between autonomous a router, or to a server from which router software is systems, is an important component of the Internet's downloaded, or via a spoofed distribution channel, etc. routing infrastructure. Secure BGP (S-BGP) addresses Such attacks could result in transmission of fictitious critical BGP vulnerabilities by providing a scalable BGP messages, modification or replay of valid means of verifying the authenticity and authorization of messages, or suppression of valid messages. If BGP control traffic. To facilitate widespread adoption, cryptographic keying material is used to secure BGP S-BGP must avoid introducing undue overhead control traffic, that too may be compromised. We have (processing, bandwidth, storage) and must be developed security enhancements to BGP that address incrementally deployable, i.e., interoperable with BGP. most of these vulnerabilities by providing a secure, To provide a proof of concept demonstration, we scalable system: Secure-BGP (S-BGP) [1,3]. Better developed a prototype implementation of S-BGP and physical, procedural and basic communication security deployed it in DARPA’s CAIRN testbed. Real Internet for BGP routers could address some of these attacks. BGP traffic was fed to the testbed routers via replay of a However, such measures would not counter any of the recorded BGP peering session with an ISP’s BGP many forms of attacks that compromise routers router. -

Network Working Group Internet Architecture Board Request for Comments: 1720 J
Network Working Group Internet Architecture Board Request for Comments: 1720 J. Postel, Editor Obsoletes: RFCs 1610, 1600, 1540, 1500, November 1994 1410, 1360, 1280, 1250, 1100, 1083, 1130, 1140, 1200 STD: 1 Category: Standards Track INTERNET OFFICIAL PROTOCOL STANDARDS Status of this Memo This memo describes the state of standardization of protocols used in the Internet as determined by the Internet Architecture Board (IAB). This memo is an Internet Standard. Distribution of this memo is unlimited. Table of Contents Introduction . 2 1. The Standardization Process . 3 2. The Request for Comments Documents . 5 3. Other Reference Documents . 6 3.1. Assigned Numbers . 6 3.2. Gateway Requirements . 6 3.3. Host Requirements . 6 3.4. The MIL-STD Documents . 6 4. Explanation of Terms . 7 4.1. Definitions of Protocol State (Maturity Level) . 8 4.1.1. Standard Protocol . 8 4.1.2. Draft Standard Protocol . 9 4.1.3. Proposed Standard Protocol . 9 4.1.4. Experimental Protocol . 9 4.1.5. Informational Protocol . 9 4.1.6. Historic Protocol . 9 4.2. Definitions of Protocol Status (Requirement Level) . 9 4.2.1. Required Protocol . 10 4.2.2. Recommended Protocol . 10 4.2.3. Elective Protocol . 10 4.2.4. Limited Use Protocol . 10 4.2.5. Not Recommended Protocol . 10 5. The Standards Track . 10 5.1. The RFC Processing Decision Table . 10 5.2. The Standards Track Diagram . 12 6. The Protocols . 14 6.1. Recent Changes . 14 Internet Architecture Board [Page 1] RFC 1720 Internet Standards November 1994 6.1.1. New RFCs . 14 6.1.2. -

Protecting the Integrity of Internet Routing: Border Gateway Protocol (BGP) Route Origin Validation
NIST SPECIAL PUBLICATION 1800-14C Protecting the Integrity of Internet Routing: Border Gateway Protocol (BGP) Route Origin Validation Volume C: How-To Guides William Haag Applied Cybersecurity Division Information Technology Laboratory Doug Montgomery Advanced Network Technologies Division Information Technology Laboratory Allen Tan The MITRE Corporation McLean, VA William C. Barker Dakota Consulting Silver Spring, MD June 2019 This publication is available free of charge from: https://doi.org/10.6028/NIST.SP.1800-14 The first draft of this publication is available free of charge from: https://www.nccoe.nist.gov/sites/default/files/library/sp1800/sidr-piir-nist-sp1800-14-draft.pdf This publication DISCLAIMER is available Certain commercial entities, equipment, products, or materials may be identified by name or company logo or other insignia in order to acknowledge their participation in this collaboration or to describe an free experimental procedure or concept adequately. Such identification is not intended to imply special of status or relationship with NIST or recommendation or endorsement by NIST or NCCoE; neither is it charge intended to imply that the entities, equipment, products, or materials are necessarily the best available for the purpose. from: http://doi.org/10.6028/NIST.SP.1800-14. National Institute of Standards and Technology Special Publication 1800-14C, Natl. Inst. Stand. Technol. Spec. Publ. 1800-14C, 61 pages, (June 2019), CODEN: NSPUE2 FEEDBACK As a private-public partnership, we are always seeking feedback on our Practice Guides. We are particularly interested in seeing how businesses apply NCCoE reference designs in the real world. If you have implemented the reference design, or have questions about applying it in your environment, please email us at [email protected]. -

Appendix a Protocol Filters
APPENDIX A Protocol Filters The tables in this appendix list some of the protocols that you can filter on the access point. In each table, the Protocol column lists the protocol name, the Additional Identifier column lists other names for the same protocol, and the ISO Designator column lists the numeric designator for each protocol. Cisco IOS Software Configuration Guide for Cisco Aironet Access Points A-1 Appendix A Protocol Filters Table A-1 EtherType Protocols Protocol Additional Identifier ISO Designator ARP — 0x0806 RARP — 0x8035 IP — 0x0800 Berkeley Trailer Negotiation — 0x1000 LAN Test — 0x0708 X.25 Level3 X.25 0x0805 Banyan — 0x0BAD CDP — 0x2000 DEC XNS XNS 0x6000 DEC MOP Dump/Load — 0x6001 DEC MOP MOP 0x6002 DEC LAT LAT 0x6004 Ethertalk — 0x809B Appletalk ARP Appletalk 0x80F3 AARP IPX 802.2 — 0x00E0 IPX 802.3 — 0x00FF Novell IPX (old) — 0x8137 Novell IPX (new) IPX 0x8138 EAPOL (old) — 0x8180 EAPOL (new) — 0x888E Telxon TXP TXP 0x8729 Aironet DDP DDP 0x872D Enet Config Test — 0x9000 NetBUI — 0xF0F0 Cisco IOS Software Configuration Guide for Cisco Aironet Access Points A-2 Appendix A Protocol Filters Table A-2 IP Protocols Protocol Additional Identifier ISO Designator dummy — 0 Internet Control Message Protocol ICMP 1 Internet Group Management Protocol IGMP 2 Transmission Control Protocol TCP 6 Exterior Gateway Protocol EGP 8 PUP — 12 CHAOS — 16 User Datagram Protocol UDP 17 XNS-IDP IDP 22 ISO-TP4 TP4 29 ISO-CNLP CNLP 80 Banyan VINES VINES 83 Encapsulation Header encap_hdr 98 Spectralink Voice Protocol SVP 119 Spectralink raw -

Introduction to the Border Gateway Protocol – Case Study Using GNS3
Introduction to The Border Gateway Protocol – Case Study using GNS3 Sreenivasan Narasimhan1, Haniph Latchman2 Department of Electrical and Computer Engineering University of Florida, Gainesville, USA [email protected], [email protected] Abstract – As the internet evolves to become a vital resource for many organizations, configuring The Border Gateway protocol (BGP) as an exterior gateway protocol in order to connect to the Internet Service Providers (ISP) is crucial. The BGP system exchanges network reachability information with other BGP peers from which Autonomous System-level policy decisions can be made. Hence, BGP can also be described as Inter-Domain Routing (Inter-Autonomous System) Protocol. It guarantees loop-free exchange of information between BGP peers. Enterprises need to connect to two or more ISPs in order to provide redundancy as well as to improve efficiency. This is called Multihoming and is an important feature provided by BGP. In this way, organizations do not have to be constrained by the routing policy decisions of a particular ISP. BGP, unlike many of the other routing protocols is not used to learn about routes but to provide greater flow control between competitive Autonomous Systems. In this paper, we present a study on BGP, use a network simulator to configure BGP and implement its route-manipulation techniques. Index Terms – Border Gateway Protocol (BGP), Internet Service Provider (ISP), Autonomous System, Multihoming, GNS3. 1. INTRODUCTION Figure 1. Internet using BGP [2]. Routing protocols are broadly classified into two types – Link State In the figure, AS 65500 learns about the route 172.18.0.0/16 through routing (LSR) protocol and Distance Vector (DV) routing protocol.