Exploring the Security of Kaios Mobile Applications NCC Group - Third-Party Projects August 24, 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Comparison and Evaluation of Cross Platform Mobile Application Development Tools
International Journal of Applied Mathematics, Electronics and Computers 8(4): 273-281, 2020 INTERNATIONAL JOURNAL OF APPLIED MATHEMATICS International Open Access ELECTRONICS AND COMPUTERS Volume 08 Issue 04 www.dergipark.org.tr/ijamec e-ISSN: 2147-8228 December, 2020 Research Article Comparison and Evaluation of Cross Platform Mobile Application Development Tools Mehmet ISITAN a , Murat KOKLU b a Sakarya University, Faculty of Computer and Information Science, Department of Software Engineering b Selcuk University, Faculty of Technology, Department of Computer Engineering ARTICLE INFO ABSTRACT Article history: In order to develop a mobile application, it is necessary to develop software separately for each Received 28 November 2020 operating system to be outputted. In response to this problem, frameworks that can give application Accepted 6 December 2020 outputs for more than one operating system by developing applications on only one platform have Keywords: been developed. With the recent diversification of these systems, which are called cross platform Cross Platform, mobile application development tools, which one should be preferred has become a problem for Mobile Development, Mobile Frameworks, developers. In this study, the cross-platform mobile application development tools that have come One Code to the fore in recent years will be determined and evaluated separately based on the pros and cons of distinguishing parameters. With the help of the applications to be developed, values such as processor, memory, battery and network usage, rendering time, opening time, installation file size, application size will be measured. It is also aimed to help developers find out which framework is more suitable for their needs by comparing them on topics such as popularity, third party software support, operating systems that can be outputted, development languages and ease of use, speed - performance. -

Download Android Os for Phone Open Source Mobile OS Alternatives to Android
download android os for phone Open Source Mobile OS Alternatives To Android. It’s no exaggeration to say that open source operating systems rule the world of mobile devices. Android is still an open-source project, after all. But, due to the bundle of proprietary software that comes along with Android on consumer devices, many people don’t consider it an open source operating system. So, what are the alternatives to Android? iOS? Maybe, but I am primarily interested in open-source alternatives to Android. I am going to list not one, not two, but several alternatives, Linux-based mobile OSes . Top Open Source alternatives to Android (and iOS) Let’s see what open source mobile operating systems are available. Just to mention, the list is not in any hierarchical or chronological order . 1. Plasma Mobile. A few years back, KDE announced its open source mobile OS, Plasma Mobile. Plasma Mobile is the mobile version of the desktop Plasma user interface, and aims to provide convergence for KDE users. It is being actively developed, and you can even find PinePhone running on Manjaro ARM while using KDE Plasma Mobile UI if you want to get your hands on a smartphone. 2. postmarketOS. PostmarketOS (pmOS for short) is a touch-optimized, pre-configured Alpine Linux with its own packages, which can be installed on smartphones. The idea is to enable a 10-year life cycle for smartphones. You probably already know that, after a few years, Android and iOS stop providing updates for older smartphones. At the same time, you can run Linux on older computers easily. -

Nokia 8110 4G User Guide
Nokia 8110 4G User Guide Issue 2021-09-27 en-AE Nokia 8110 4G User Guide Table of Contents 1 About this user guide 5 2 Get started 6 Keys and parts .......................................... 6 Set up and switch on your phone ................................ 7 Charge your phone ....................................... 11 3 Basics 12 Explore your phone ....................................... 12 Change the volume ....................................... 12 Write text ............................................. 12 4 Connect with your friends and family 14 Calls ................................................ 14 Contacts ............................................. 14 Send messages ......................................... 15 Send mail ............................................. 15 5 Personalize your phone 17 Change the tones ........................................ 17 Change the look of your home screen ............................. 17 6 Camera 18 Photos .............................................. 18 Videos ............................................... 18 7 Internet and connections 20 Browse the web ......................................... 20 Bluetooth® ............................................ 20 Wi-Fi ................................................ 20 © 2021 HMD Global Oy. All rights reserved. 2 Nokia 8110 4G User Guide 8 Music and videos 22 Music player ........................................... 22 Listen to radio .......................................... 22 Video player ........................................... 22 Recorder -

Connected Society Mobile Internet Skills Training Toolkit a Guide for Training People in Basic Mobile Internet Skills
Connected Society Mobile Internet Skills Training Toolkit A guide for training people in basic mobile internet skills Copyright © 2017 GSM Association GSMA Connected Society The GSMA represents the interests of mobile operators The Connected Society programme works with the mobile worldwide, uniting more than 750 operators with almost industry, tech companies, the development community and 400 companies in the broader mobile ecosystem, governments to increase access to and adoption of the including handset and device makers, software mobile internet, focusing on underserved population companies, equipment providers and internet companies, groups in developing markets. Key activities include: as well as organisations in adjacent industry sectors. The Generating and disseminating insights and learnings on the GSMA also produces the industry-leading MWC events mobile internet coverage and usage gap. held annually in Barcelona, Los Angeles and Shanghai, as well as the Mobile 360 Series of regional conferences. Supporting mobile operators to extend coverage and drive usage. For more information, please visit the GSMA corporate website at www.gsma.com. Undertaking advocacy and policy work to ensure that mo- bile operators’ efforts to achieve greater digital inclusion are Follow the GSMA on Twitter: @GSMA. being effectively supported by governments, the interna- tional community and other stakeholders. For more information, please visit www.gsma.com/connected-society Or contact us at: [email protected] MOBILE INTERNET SKILLS TRAINING -

Innovation in Fare Collection Systems for Public Transport in African Cities
INNOVATION IN FARE COLLECTION SYSTEMS FOR PUBLIC TRANSPORT IN AFRICAN CITIES Fatima Arroyo-Arroyo // Philip van Ryneveld // Brendan Finn // Chantal Greenwood // Justin Coetzee An international partnership supported by: Innovation in fare collection systems for public transport in African cities // 2 Copyright The SSATP is an international partnership to facilitate policy development and related capacity building in the transport sector in Africa. Sound policies lead to safe, reliable, and cost-effective transport, freeing people to lift themselves out of poverty and helping countries compete internationally. The SSATP is a partnership of 42 African countries: Angola, Benin, Burkina Faso, Burundi, Cameroon, Cape Verde, Central African Republic, Chad, Comoros, Congo, Democratic Republic of the Congo, Côte d’Ivoire, Djibouti, Eswatini, Ethiopia, Gabon, The Gambia, Ghana, Guinea, Guinea-Bissau, Kenya, Lesotho, Liberia, Madagascar, Malawi, Mali, Mauritania, Morocco, Mozambique, Namibia, Niger, Nigeria, Rwanda, Senegal, Sierra Leone, South Sudan, Tanzania, Togo, Tunisia, Uganda, Zambia, Zimbabwe; Eight Regional Economic Communities (RECs); Two African institutions: the African Union Commission (AUC) and the United Nations Economic Commission for Africa (UNECA); Financing partners for the Third Development Plan: European Commission (main donor), Swiss State Secretariat for Economic Affairs (SECO), Agence Française de Développement (AFD), the African Development Bank (AfDB), and the World Bank (host); and many public and private national and regional organizations. The SSATP gratefully acknowledges the contributions and support of member countries and its partners. More publications can be accessed on the SSATP website: www.ssatp.org. The findings, interpretations, and conclusions expressed here are those of the authors and do not necessarily reflect the views of the SSATP or its partners. -

Mobile Coverage and Its Impact on Digital Financial Services Leon Perlman1 and Michael Wechsler2
Mobile Coverage and its Impact on Digital Financial Services Leon Perlman1 and Michael Wechsler2 ABSTRACT3 Digital Financial Services (DFS) is a relatively recent mobile-centric financial inclusion innovation in developing countries. Using ubiquitous mobile phones as the means of service access, DFS provides the unbanked and underserved - many of whom live in rural areas - with access to basic financial services provided by banks and non- banks such as mobile network operators and third party DFS providers (DFSPs). With mobile phones as the primary access mechanism for services, access to DFS is highly dependent upon the degree and quality of mobile coverage offered by mobile network operators (MNOs). User interfaces (UIs) for access to DFS are mostly dependent on the type of mobile coverage available which in many cases in the developing world is via slower (narrowband) second generation (2G) GSM technology. Faster broadband third (3G) and fourth generation (4G) mobile coverage is available in most developing world countries, but is mostly limited to urban and peri-urban areas and along national road corridors. Our study finds that the type of mobile coverage provided has a significant effect on the DFS UI and type of mobile phone that can be used for DFS access. Feature phones and Unstructured Supplementary Service Data (USSD) transactions continue to be the choice for the vast majority of (mobile money) users. Faster mobile broadband technologies are optimal for smartphone use – or hybrid smartphones in feature phone format - which -

Whatsapp White Paper
WHITE PAPER Research on how end-to-end encrypted WhatsApp data can be recovered and decrypted by MD-RED. Contents WhatsApp Overview Major features of WhatsApp and data analysis by MD-RED I. Messaging features II. Chat history III. Backup Setting IV. Share live location V. Privacy VI. Network Background This white paper provides a technical explanation of WhatsApp’s encryption system, major features of WhatsApp that needs advanced research and how those data can be recovered/decrypted and viewed. Summary MD-RED will support forensic investigators to analyze various features of the latest WhatsApp installed in any version of Android and iOS. And through our regular product updates, phone models over 80 manufacturers are supported and deleted and encrypted data such as Message/Multimedia/Contacts/File and etc. can be recovered and decrypted by MD-RED. We Empower Your Investigation! WhatsApp Overview Supports various platforms I. Supported OS: Android, iOS, KaiOS, Windows, MacOS, Blackberry II. Supports KaiOS version from v2.5.(Nov. 2017) Figure 1. Account Accounts I. Allows one accounts for one mobile phone number. II. If mobile phone number is changed, user needs to request for an account information modification. III. It takes certain period of time after the requests for account deletion is submitted. IV. End-to-end Encryption WhatsApp's End-to-end encryption ensures only you and the person you're communicating with can read what is sent, and nobody in between, not even WhatsApp. For added protection, every message being sent has its own unique lock and key. All of this happens automatically: no need to turn on settings or set up special secret chats to secure the messages. -

A Survey on Android Security: Development and Deployment Hindrance and Best Practices
TELKOMNIKA Telecommunication, Computing, Electronics and Control Vol. 18, No. 1, February 2020, pp. 485∼499 ISSN: 1693-6930, accredited First Grade by Kemenristekdikti, No: 21/E/KPT/2018 DOI: 10.12928/TELKOMNIKA.v18i1.13288 r 485 A survey on android security: development and deployment hindrance and best practices Ratul Sikder1, Md Shohel Khan2, Md Shohrab Hossain3, Wazir Zada Khan4 1,2,3Department of CSE, BUET, Dhaka, Bangladesh 4Department of CS and IT, Jazan University, Jazan, Saudi Arabia Article Info ABSTRACT Article history: Android OS is the most popular mobile OS for the past few years. Vulnerabilities arise Received Jun 10, 2019 with respect to the increasing functionality of Android OS, impolitic app development practices of developers, end-user incautious and interestingly remediation for the Revised Dec 21, 2019 vulnerabilities has been introduced frequently as well. To mitigate security risk factor Accepted Dec 31, 2019 Google has been updated, deprecated and restricted many system level APIs for 3rd Keywords: party developers. Considering the consequences, this paper provides a wide overview of Android’s system level app development, privacy issues, and guideline for the Android security developers about what measure they should consider while developing apps. We also Developers guideline discussed the historical development of Android OS and the end-users role to maintain System permission privacy and to minimize security risks. User privacy Vulnerability This is an open access article under the CC BY-SA license. Corresponding Author: Ratul Sikder, Department of CSE, BUET, Dhaka, Bangladesh. Email: [email protected] 1. INTRODUCTION Current age is considered as the age of mobility. -
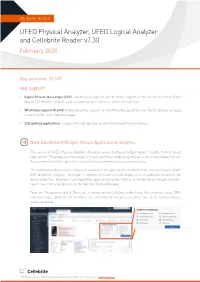
UFED Physical Analyzer, UFED Logical Analyzer and Cellebrite Reader V7.30 February 2020
RELEASE NOTES UFED Physical Analyzer, UFED Logical Analyzer and Cellebrite Reader v7.30 February 2020 App versions: 10,443 App support • Signal Private Messenger (iOS) – Updated decryption and decoding support for the latest version of Signal app on iOS devices surfaces user account details, contacts, chats and call logs. • WhatsApp support (KaiOS) – New decoding support for the WhatsApp application on KaiOS devices surfaces contact details and chat messages. • 225 updated applications – Support for 225 new app versions for iOS and Android devices. New Dashboard Widget Shows Application Insights This version of UFED Physical Analyzer introduces a new dashboard widget named “Insights from Installed Applications.” The purpose of the widget is to help examiners make insightful decisions around where to focus their examination efforts upfront, to optimize their examination process downstream. The dashboard widget shows a high-level overview of the applications installed on the extracted device, under their respective category. The widget is dynamic in nature and will display a list of categories based on the device extraction. Examiners can expand the application view by clicking on the dashboard widget, and later select one or more applications for further drill-down and review. There are 30 categories listed. These are a combination of Cellebrite defined; hide files or pictures, fake GPS, Fake messages, Spoofing, Clean mobile etc, and industry accepted categories like social, finance, music, games and more. UFED Physical Analyzer, UFED Logical Analyzer and Cellebrite Reader v7.30 | February 2020 | www.cellebrite.com This is the first step towards implementing a more intuitive design, with improved navigation, visuals and tools to optimize your use of UFED Physical Analyzer and to help you save valuable time. -

Dégooglelisons ! Un Smartphone Android Sans Google Avec /E/ !
DéGooglelisons ! Un Smartphone Android sans Google avec /e/ ! 24/01/2021 Bonsoir le Monde ! Google tout-puissant, que ton nom soit sanctifié, que ta volonté soit … Heu non, qu’est-ce que je raconte moi ? Le marché des Smartphones Android est le terrain de chasse de Google mais il y a des tentatives de plus en plus répétées pour essayer d’en sortir et d’offrir un choix un tout petit peu plus varié et surtout plus respectueux de votre vie privée ! Les pionniers de ce mouvement libertaire commencent en général par supporter quelques modèles d’anciens Smartphones reconditionnés mais aussi des modèles neufs de constructeurs de Smartphone non-liés à Google pour Android comme FairPhone ou Pinefone… Fairphone (lien Wikipédia) est une entreprise hollandaise proposant des Smartphones réparables et donc nettement plus respectueux de l’environnement. Android est une variante de Linux et est donc libre mais Google l’a profondément modifié et complété par plein de modules de codes qui eux ne sont pas libres (Open Source) comme des applications et des services spécifiques à Google. En plus de cela, les différents constructeurs de Smartphone rajoutent leur interface graphique propre et quelques autres applications de leur cru. La plupart du temps, toutes ces applications et services ne sont pas désinstallables et ne vous permettent donc pas de revenir à l’Android libre seul. Je rappelle qu’un programme en Open Source ou « Libre » n’est pas obligatoirement gratuit mais permet à tout organisme ou individu de vérifier le code source du programme et donc entre autres de voir si la vie privée est effectivement respectée. -

Security Analysis of the Kaios Feature Phone Platform for DFS Applications
SECURITY, INFRASTRUCTURE AND TRUST WORKING GROUP Security analysis of the KaiOS feature phone platform for DFS applications REPORT OF THE SECURITY WORKSTREAM Methodology for measurement of Quality of Service (QoS) Key Performance Indicators (KPIs) for Digital Financial Services • b b • Technical report on SS7 vulnerabilities and mitigation measures for digital fi nancial services transactions Security, Infrastructure and Trust Working Group Security analysis of the KaiOS feature phone platform for DFS applications DISCLAIMER The Financial Inclusion Global Initiative (FIGI) is a three-year program implemented in partnership by the World Bank Group (WBG), the Committee on Payments and Market Infrastructures (CPMI), and the International Telecommunica- tion Union (ITU), funded by the Bill & Melinda Gates Foundation (BMGF) to facilitate the implementation of country-led reforms to attain national financial inclusion targets, and ultimately the global 'Universal Financial Access 2020' goal. FIGI funds initiatives in three countries-China, Egypt and Mexico; supports working groups to address three distinct chal- lenges for reaching universal financial access: (1) the Electronic Payment Acceptance Working Group (led by the WBG), (2) The Digital ID for Financial Services Working Group (led by the WBG), and (3) The Security, Infrastructure and Trust Working Group (led by the ITU). FIGI hosts three annual symposia to assemble national authorities, the private sector, and other relevant stakeholders to share emerging insights from the Working Groups -
DDPR Applications
Note: The following list will be valid from 1st April to 30th April Application Home Page URl Adobe Acrobat https://www.adobe.com Airmail https://airmailapp.com Airmail iOS http://airmailapp.com Allstate Digital Footprint https://www.infoarmor.com/digital-footprint Amazon https://www.amazon.com https://www.amazon.com/gp/help/customer/display.html/?nod Amazon Alexa eId=202126980 Apollo https://www.apollo.io App in the Air https://www.appintheair.mobi/ AquaMail http://www.aqua-mail.com/ Bark for Gmail https://www.bark.us BlackBerry Hub+ Services https://us.blackberry.com/smartphones/blackberry-hub-plus BlueMail https://bluemail.me/ Boomerang for Gmail https://www.boomeranggmail.com Brother iPrint&Scan for Android http://www.brother.com/apps/android CallApp https://www.callapp.com Checker Plus for Gmail™ https://jasonsavard.com/Checker-Plus-for-Gmail Chuck https://chuck.email/ Clean Email https://clean.email cloudHQ https://www.cloudhq.net/g_suite ColorOS_Mail https://mailvip.coloros.com/homePage.html Copper CRM https://www.copper.com/ CosmoSia https://cosmosia.net/ CRED https://www.cred.club/ DocHub - PDF Sign & Edit https://dochub.com Earny https://www.earny.co EasyMail - easy & fast email https://hbsolution.site/ eM Client https://www.emclient.com Email - Edison Mail http://www.edison.tech Email Home - Full Screen Email Widget and Launcher https://www.emailhomeapp.com/ Email Notifications for Forms https://digitalinspiration.com/product/google-forms-notification s Eメール http://www.sharp.co.jp/k-tai/ Fetch Rewards https://www.fetchrewards.com