An Investigation of E-Government Adoption in Bahrain and Evaluate the Key Determining Factors for Strategic Advantage Ali Mohame
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Download Being the Number of Sent Packets That Were Acknowledged As Received
Dimming the Internet Detecting Throttling as a Mechanism of Censorship in Iran Collin Anderson? [email protected] Abstract. In the days immediately following the contested June 2009 Presidential election, Iranians attempting to reach news content and so- cial media platforms were subject to unprecedented levels of the degra- dation, blocking and jamming of communications channels. Rather than shut down networks, which would draw attention and controversy, the government was rumored to have slowed connection speeds to rates that would render the Internet nearly unusable, especially for the consump- tion and distribution of multimedia content. Since, political upheavals elsewhere have been associated with headlines such as \High usage slows down Internet in Bahrain" and \Syrian Internet slows during Friday protests once again," with further rumors linking poor connectivity with political instability in Myanmar and Tibet. For governments threatened by public expression, the throttling of Internet connectivity appears to be an increasingly preferred and less detectable method of stifling the free flow of information. In order to assess this perceived trend and begin to create systems of accountability and transparency on such practices, we attempt to outline an initial strategy for utilizing a ubiquitious set of network measurements as a monitoring service, then apply such method- ology to shed light on the recent history of censorship in Iran. Keywords: censorship, national Internet, Iran, throttling, M-Lab 1 Introduction "Prison is like, there's no bandwidth." - Eric Schmidt1 The primary purpose of this paper is to assess the validity of claims that the international connectivity of information networks used by the Iranian public has been subject to substantial throttling based on a historical and correlated set of open measurements of network performance. -

State Power 2.0.Pdf
STATE POWER 2.0 Proof Copy 000 Hussain book.indb 1 9/9/2013 2:02:58 PM This collection is dedicated to the international networks of activists, hactivists, and enthusiasts leading the global movement for Internet freedom. Proof Copy 000 Hussain book.indb 2 9/9/2013 2:02:58 PM State Power 2.0 Authoritarian Entrenchment and Political Engagement Worldwide Edited by MUZAMMIL M. HUSSAIN University of Michigan, USA PHILIP N. HOWARD University of Washington, USA Proof Copy 000 Hussain book.indb 3 9/9/2013 2:02:59 PM © Muzammil M. Hussain and Philip N. Howard 2013 All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise without the prior permission of the publisher. Muzammil M. Hussain and Philip N. Howard have asserted their right under the Copyright, Designs and Patents Act, 1988, to be identified as the editors of this work. Published by Ashgate Publishing Limited Ashgate Publishing Company Wey Court East 110 Cherry Street Union Road Suite 3-1 Farnham Burlington, VT 05401-3818 Surrey, GU9 7PT USA England www.ashgate.com British Library Cataloguing in Publication Data A catalogue record for this book is available from the British Library The Library of Congress has cataloged the printed edition as follows: Howard, Philip N. State Power 2.0 : Authoritarian Entrenchment and Political Engagement Worldwide / by Philip N. Howard and Muzammil M. Hussain. pages cm Includes bibliographical references and index. ISBN 978-1-4094-5469-4 (hardback) -- ISBN 978-1-4094-5470-0 (ebook) -- ISBN 978- 1-4724-0328-5 (epub) 1. -
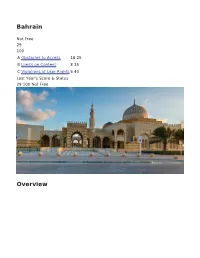
Freedom on the Net 2019
Bahrain Not Free 29 100 A Obstacles to Access 16 25 B Limits on Content 835 C Violations of User Rights 540 Last Year's Score & Status 29 100 Not Free Overview Internet freedom in Bahrain remains restricted. While no internet shutdowns were reported during the coverage period, numerous websites continued to be blocked, social media users were arrested and jailed, and the level of self-censorship and state surveillance remained high. Journalists and activists who work online, including those abroad, continued to face extralegal intimidation, and reports continue of their severe abuse while in custody of Bahraini authorities. The government works to manipulate and control online information. Bahrain was once viewed as a promising model for political reform and democratic transition, but it has become one of the Middle East’s most repressive states. Since violently crushing a popular prodemocracy protest movement in 2011, the Sunni-led monarchy has systematically eliminated a broad range of political rights and civil liberties, dismantled the political opposition, and cracked down harshly on persistent dissent in the Shiite population. Key Developments June 1, 2018 – May 31, 2019 In contrast to past years, no restrictions to connectivity were observed during the reporting period (see A3). In April 2019, authorities announced progress on plans to establish a single national broadband network, which is expected to be completed later in 2019 ( see A4). Video recordings and live-streamed video of government proceedings were censored or removed on several occasions, apparently to prevent users from viewing potentially controversial or embarrassing remarks by officials (see B2). In May 2019, the cybercrime directorate of the Ministry of Interior (MOI) declared the accounts of several Bahraini activists and journalists to be malicious, and a few days later sent SMS messages and tweeted to users to warn them that following “malicious” social media accounts could result in prosecution (see B5, C7). -

Mobilizing Through Online Media
REPORT ARAB POLITICS BEYOND THE UPRISINGS Mobilizing through Online Media Why the Internet Still Matters for Change in the Middle East MAY 9, 2017 — MARC LYNCH PAGE 1 Social media had a starring role in the Arab uprisings of 2011. But since then, authoritarians have cracked down on online activists, and even on casual dissent on platforms such as Facebook and Twitter. Meanwhile, numerous reactionaries have shown they can use the web just as effectively as the liberals who were its first adopters in the region. Together, these events have unraveled the once-popular narrative that the Internet has an inherent bent toward democracy. Still, state control of communications has been forever disrupted, and online platforms continue to provide the region’s most resilient sites for political and social engagement. Usually, they do not directly lead to mass action. However, such a metric underestimates social media’s significance. The Internet’s churn often occurs beneath the surface: ideas ferment, identities evolve, and coordination happens across geographical and social divides. Authorities may infiltrate and imprison, but online media will certainly be central to the next wave of change, whatever form it takes. As autocratic regimes have regained their grip on power following the extraordinary moments of early 2011, many politically engaged Arabs have retreated into online spaces to rethink, reshape, and recreate forms of contentious political action. The severe increase in state surveillance and repression of the Internet over the last five years has shaped the way online media is used in Arab countries. But such repressive measures cannot erase the generational impact of the massive increase in the availability and use of social media. -

University of Bradford Ethesis
Factors affecting the adoption of internet banking in the Kingdom of Bahrain Item Type Thesis Authors Janahi, Yusuf M.A.M. Rights <a rel="license" href="http://creativecommons.org/licenses/ by-nc-nd/3.0/"><img alt="Creative Commons License" style="border-width:0" src="http://i.creativecommons.org/l/by- nc-nd/3.0/88x31.png" /></a><br />The University of Bradford theses are licenced under a <a rel="license" href="http:// creativecommons.org/licenses/by-nc-nd/3.0/">Creative Commons Licence</a>. Download date 03/10/2021 18:09:32 Link to Item http://hdl.handle.net/10454/15884 University of Bradford eThesis This thesis is hosted in Bradford Scholars – The University of Bradford Open Access repository. Visit the repository for full metadata or to contact the repository team © University of Bradford. This work is licenced for reuse under a Creative Commons Licence. FACTORS AFFECTING THE ADOPTION OF INTERNET BANKING IN THE KINGDOM OF BAHRAIN Overcoming Barriers to Adoption Through the Use of Biometrics YUSUF MOHAMED ABDULLA MOHAMED JANAHI Submitted for the Degree of Doctor of Philosophy FACULTY OF ENGINEERING AND INFORMATICS UNIVERSITY OF BRADFORD 2016 Janahi, Yusuf Mohamed Abdulla M. “FACTORS AFFECTING THE ADOPTION OF INTERNET BANKING IN THE KINGDOM OF BAHRAIN” Abstract The emergence of the Internet in business as a marketing tool and as a communication medium is one of the existing challenges for the banking industry. Because of this evolution, the banking industry has adopted Internet banking both for financial transactions and for the provision -

FINAL Completed Thesis
The Localisation of International News Agency Reports in English Newspapers in the Middle East Author Mohamed, Ali Published 2014 Thesis Type Thesis (PhD Doctorate) School School of Languages and Linguistics DOI https://doi.org/10.25904/1912/1462 Copyright Statement The author owns the copyright in this thesis, unless stated otherwise. Downloaded from http://hdl.handle.net/10072/367979 Griffith Research Online https://research-repository.griffith.edu.au The Localisation of International News Agency Reports in English Newspapers in the Middle East Ali Mohamed BA, English Language and Literature, University of Bahrain 2003 MA, Applied English Language Studies, University of Bahrain 2007 School of Languages and Linguistics Arts, Education and Law Griffith University Submitted in fulfilment of the requirements of the degree of Doctor of Philosophy August 2013 Statement of Originality This work has not previously been submitted for a degree or diploma in any university. To the best of my knowledge and belief, the thesis contains no material previously published or written by another person except where due reference is made in the thesis itself. _____________________________ Ali Mohamed Abstract This thesis investigates the process of producing localised news reports by English newspapers in the Middle East instead of them using the actual news articles that they obtain from the international news agencies. The production of English news in the Middle East is a subject that has hardly been studied so far and this study is an attempt to shed light into how English news is produced and received in this part of the world. Since most news articles about international events reach the Middle East through the various international news agencies, news editors in the English newspapers in the region are faced with the task of fending off the ideologies that contradict with the local interest. -

Samena Trends Exclusively for Samena Telecommunications Council's Members Building Digital Economies
Volume 08, December, 2017 A SAMENA Telecommunications Council Newsletter www.samenacouncil.org SAMENA TRENDS EXCLUSIVELY FOR SAMENA TELECOMMUNICATIONS COUNCIL'S MEMBERS BUILDING DIGITAL ECONOMIES THIS MONTH PROMOTING 5G INVESTMENT AND BUSINESS MODELS Upgrade your Business with Batelco the leading Digital Solutions Provider From Business connectivity, cloud services to security solutions. We provide you with everything So that your idea doesn’t just change the world, it transforms yours too. Work better with Batelco’s Digital Business Solutions batelco.com/business VOLUME 08, DECEMBER, 2017 Contributing Editors Publisher Izhar Ahmad SAMENA Telecommunications Council SAMENA Javaid Akhtar Malik Subscriptions TRENDS Contributing Members [email protected] Alfa Editor-in-Chief A.D. Little Advertising Bocar A. BA Cisco [email protected] du Huawei SAMENA TRENDS Oman Broadband [email protected] Tel: +971.4.364.2700 CONTENTS 04 EDITORIAL 05 REGULATOR ACHIEVEMENTS 26 REGIONAL & MEMBERS UPDATES Members News Regional News 61 SATELLITE UPDATES Satellite News 71 WHOLESALE UPDATES The SAMENA TRENDS newsletter is Wholesale News wholly owned and operated by The SAMENA Telecommunications Council 78 (SAMENA Council). Information in the TECHNOLOGY UPDATES newsletter is not intended as professional Technology News services advice, and SAMENA Council disclaims any liability for use of specific 87 REGULATORY & POLICY 21 SAMENA COUNCIL information or results thereof. Articles ACTIVITY and information contained in this UPDATES publication -

Empirical Study with Relevance to Bahrain an Ical Study with Bahrain
Global Journal of Enterprise Information System January 2010 -June 2010 Volume-2 Issue -1 ABSTRACT Online Shopping is growing globally. However, there may be notable differences in the way people engage the online marketplace based on such factors as age, gender, and educational background (among others). This research focuses Insight of Online on the expanding trend of electronic retail (e -tail) in Bahrain. It examines various factors such as Trend : availability, knowledge, awareness, security and Shopping Trend : An customer service which are expected to have an impact on online shopping popularity among different age groups an d their educational Empirical Study with background. The study challenges the growth of e - tail in Bahrain’s heterogeneous market and relevance to Bahrain highlights that the main dependencies that affect it can be either related to technology availability or lifestyle perspective of Internet users . The study hypothesizes that the highest online shopping activity is not sustained within a specific age group. Dr. Akram Jalal The research also discusses the advancement of Chair of MIS Department, College of Business and online shopping in a country like Bahrain and how Finance, Ahlia University, Kingdom of Bahrain the business trend can be transforming from r etail to e-tail. In conclusion it attempts to forecast the [email protected] move towards e-tail and highlights the underlying factors such as product variety, cost, security and customer service. Another area that is moderately Mazen AlAl----MaskatiMaskati explored is online banking usage which is an area that is closely related to e-tail as it requires similar College of Business and Finance, Ahlia University, mechanisms. -

Empowerment Approach to Gender Equality in the Information Society
Volume 2 December 2008 An Empowerment Approach to Gender Equality in the Information Society Regional Analyses from Asia Information Society for the South Series Volume 2 An Empowerment Approach to Gender Equality in the Information Society Regional Analyses from Asia IT for Change Information Society for the South Series Volume 2 An Empowerment Approach to Gender Equality in the Information Society: Regional Analyses from Asia Editors Anita Gurumurthy Parminder Jeet Singh Anja Kovacs Editorial and Production Assistance Adithi N Rao Design Krupa Thimmaiah December 2008 Creative Commons Attribution-NonCommercial-share Alike 2.5 India Licence Published by: IT for Change Bangalore, India www.ITforChange.net Printed at National Printing Press, Bangalore Table of Contents Introduction 5 1. An Empowerment Approach to Gender Equality in the Information Society: Perspectives from East Asia Angela M. Kuga Thas 11 2. What Women Want from IT: Views from Western Asia Deborah L. Wheeler 51 3. ICTs and Women’s Empowerment: Findings from South Asia Mridula Swamy 79 Author and Editor Profiles 111 An Empowerment Approach to Gender Equality in the Information Society 4 Introduction About This Collection This document is the second in the series of publications from IT for Change under the ‘Information Society for the South’ research umbrella. The series is an attempt to build a body of critical work that offers analytical and conceptual tools to understand and engage with the structural changes that information and communication technologies (ICTs) are bringing about in society. This collection of papers comes out of a project undertaken as part of the regional activities of the Gender Caucus1 of the World Summit on the Information Society (WSIS). -

What Women Want from IT: Views from Western Asia
What Women Want from IT: Views from West Asia Deborah L. Wheeler December 2006 Bangalore, India IT for Change Research supported by WSIS-GC IDRC IT for Change, Bangalore Research supported by WSIS-GC and IDRC Table of Contents Introduction................................................................................................... 2 Gender and IT Access .................................................................................. 2 Qualifying Women’s IT Access.................................................................... 3 Regional Realities Challenge and Shape Women’s IT Practices.............. 4 Signs that IT Leads to Empowerment ......................................................... 6 The Macro-Picture of the Information Society in Western Asia....................................................... 7 Contextualising the Information Society in Western Asia: Voices of Empowerment ............................................................................................. 10 Kuwait .................................................................................................................................................. 10 Saudi Arabia ........................................................................................................................................ 13 Bahrain................................................................................................................................................. 16 Jordan.................................................................................................................................................. -

Arab Uprisings: Bahrain's Turn
Arab Uprisings: Bahrain’s Turn February 18, 2011 POMEPS Briefings 2 Contents Fifth columns in the Gulf? . 3. Bahrain’s torture problem . 4. The Internet in Bahrain: breaking the monopoly of information . 6. Ahead of elections what do Bahraini Shias really want? . 8 Why the Bahrain elections matter . 1. 0 The siege of Bahrain . 1. 2 Crackdown in Bahrain . 1. 4 The Project on Middle East Political Science The Project on Middle East Political Science (POMEPS) is a collaborative network which aims to increase the impact of political scientists specializing in the study of the Middle East in the public sphere and in the academic community . POMEPS, directed by Marc Lynch, is based at the Institute for Middle East Studies at the George Washington University and is supported by the Carnegie Corporation and the Social Science Research Council . It is a co-sponsor of the Middle East Channel (http://mideast foreignpolicy. com). For more information, see http://www .pomeps .org . Online Article Index Fifth columns in the Gulf? http://mideast .foreignpolicy .com/posts/2010/05/24/fifth_columns_in_the_gulf Bahrain’s torture problem http://mideast .foreignpolicy .com/posts/2010/03/29/bahrain_s_torture_problem The Internet in Bahrain: breaking the monopoly of information http://mideast .foreignpolicy .com/posts/2010/09/21/bahrain_government_vs_the_internet Ahead of elections what do Bahraini Shias really want? http://mideast .foreignpolicy .com/posts/2010/10/22/ahead_of_elections_what_do_bahraini_shias_really_want Why the Bahrain elections matter http://mideast .foreignpolicy .com/posts/2010/12/01/bahrain_elections The siege of Bahrain http://mideast .foreignpolicy .com/posts/2011/02/18/the_siege_of_bahrain Crackdown in Bahrain http://www .foreignpolicy .com/articles/2011/02/17/crackdown_in_bahrain 2 Arab Uprisings: Bahrain’s Turn Fifth columns in the Gulf? Posted By Frederic M. -

Kingdom of Bahrain State of the Nation Review of Internet Safety
Kingdom of Bahrain State of the Nation Review of Internet Safety July 2010 Prof. Julia Davidson, Kingston University and Dr Elena Martellozzo, Middlesex University on behalf of The Telecommunications Regulatory Authority, Kingdom of Bahrain 1 1. Acknowledgements We would like to thank the Telecommunications Regulatory Authority (TRA) staff who contributed to the planning and organization of the research. We are particularly grateful to the chairman Dr. Mohamed Al Amer for his support. We are grateful to Nick Truman, Internet Security Advisor for his assistance and invaluable support throughout this project; to Robert Middlehurst, Deputy General Director, for his support and constant encouragement; to Mohammed Mahmood, director of technical and operations, and Basil Al Arrayed, Director of Communications and Consumer Affairs for their help. We are also grateful to Ghada Ebrahim Alqassab, Reem Al Alawi, Rana Majed Sultan, Abdulelah Abdulla and Adel Darwish. We would like to thank Dr Khalid Al-Mutawah for managing and conducting the qualitative focus groups in the public schools and his colleagues Doctor Athraa Al Mosawi, Doctor Mohamed Baqer and Ghazwa B. Sulaibeekh from Bahrain University for their invaluable help with the data collection. We would also like to thank Mazen Khamis, Samuel, VK and Sundeep Mathias from Nielsen for their help and assistance with the survey data. The authors would also like to acknowledge the contribution of Internet Service Providers (Lightspeed, Zain, Mena and Batelco), Ministry Representatives (Education, Health and Social Development), The Sura Council, Bahrain Internet Society, Bahraini Society for Child Development NGOs, Child Protection Centre, all the schools that participated in the research and the invaluable support of the British Embassy in Bahrain.