HOME of Things the Internet the Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Spimes Not Things: Creating a Design Manifesto for a Sustainable Internet of Things
Running with Scissors, 13th EAD Conference University of Dundee, 10-12 April 2019 Spimes Not Things: Creating A Design Manifesto for A SustainaBle Internet of Things Michael Steada*, Paul CoultonB, Joseph Lindleyc aHighWire CDT, Lancaster University BImaginationLancaster, Lancaster University cImaginationLancaster, Lancaster University *Corresponding author e-mail: [email protected] Abstract: The rhetoric that surrounds the Internet of Things (IoT) contends it will bring about utopian transformative change throughout society, particularly in regards to sustainaBility. Little discourse however, recognises the intrinsically unsustainable nature of IoT devices themselves. Under a façade of innovation, the IoT is a Breeding ground for superfluous, novelty ‘gizmo’ products whose design incorporates environmentally damaging modes of manufacture, consumption and disposal. To Bring attention to this growing unsustainaBle design culture, we have produced a manifesto entitled Spimes Not Things: A Design Manifesto for A Sustainable Internet of Things. It is the synthesis of a practice-led research project which explores Sterling’s spimes concept using Design Fiction methods, as part of a Research through Design approach. This paper outlines the manifesto’s creation, its theoretical foundations and its intentions. The manifesto is the first step towards the reframing of design practices that will contriBute to a more sustainaBle IoT product paradigm. Keywords: Spimes, SustainaBility, Internet of Things, Manifesto, Design Fiction 1. Introduction The rhetoric that surrounds the Internet of Things (IoT) across academia and industry is both persuasive and turgid. Many commentators posit that through its eXpanding array of networked artefacts, sensors and AI capaBilities, the IoT will Bring aBout utopian transformative change to all sectors of society, from healthcare and energy, to transport and finance (Government Office for Science, 2014; Fritsch, Shklovski, & Douglas-Jones, 2018). -

Horizon Digital Economy Research Grant (EP/G065802/1)
ORIZON H INTERGENERATIONAL INTERPRETATION OF THE INTERNET OF THINGS Michael Brown, Tim Coughlan, Glyn Lawson1, Richard Mortier, Rob Houghton and Murray Goulden March 2012 1 Corresponding author: [email protected]; 0115 9514003 v.12 – 27th March 2012 Overview This report investigates how different generations within a household interpret individual members’ data generated by the Internet of Things (IoT). Adopting a mixed methods approach, we are interested in interpretations of the IoT by teenagers, their parents and grandparents, and how they understand and interact with the kinds of data that might be generated by IoT devices. The first part of this document is a technical review that outlines the key existing and envisaged technologies that make up the IoT. It explores the definition and scope of the Internet of Things. Hardware, networking, intelligent objects and Human-Computer Interaction implications are all discussed in detail. The second section focuses on the human perspective, looking at psychological and sociological issues relating to the interpretation of information generated by the IoT. Areas such as privacy, data ambiguity, ageism, and confirmation bias are explored. The third section brings both aspects together, examining how technical and social aspects of the IoT interact in four specific application domains: energy monitoring, groceries and shopping, physical gaming, and sharing experiences. This section also presents three household scenarios developed to communicate and explore the complexities of integrating -

Ubiquitous Computing, Virtual Worlds, and the Displacement of Property Rights
Ubiquitous Computing, Virtual Worlds, and the Displacement of Property Rights M. ScoT BOONE* Abstract: Examining one emerging technology, virtual worlds, may provide us with insight about another emerging technology, ubiquitous computing. The rapid increase in both the popularity and economic value of virtual worlds has resulted in a conflict over whether players in these worlds have any property rights with respect to virtual world objects associated with their avatars. A close examination however reveals that even if such rights exist, they can be overridden through the combined use of contract and technology. This observation may in turn provide an insight about the future of real world property. The emerging technology of ubiquitous computing shares technological characteristics with virtual worlds such that ubiquitous computing would make a displacement of property rights in real world objects possible in the same way that virtual world technology makes such a displacement possible for potential property rights in virtual world objects. "Associate Professor of Law, Appalachian School of Law. I would like to thank Charlie Condon, Judie Barger, David Ritchie and James McGrath for their helpful comments on drafts of this article. I would also like to thank for their comments the participants of the Works-in-Progress Intellectual Property Colloquium, the participants of the Intellectual Property & Communications Law and Policy Scholars Roundtable sponsored by Michigan State University College of Law, and the participants of the annual meeting of Southeastern Association of Laws Schools. The research assistance of Russell Kloosterman and Justin Williams was also immensely helpful. I/S: A JOURNAL OF LAWAND POLICY [VOL. -

Bruce Sterling
Bruce Sterling: "The future is about people navigating urban Internets" Poptronics: What has Internet of things to do with spimes, a word you invented in your book "Shaping things" composed of space and time ? What’s the difference between these two concepts ? Bruce Sterling: An Internet of Things naturally focusses attention on the Internet, while a "spime" is a "Thing" within an Internet of Things. I used the invented word "spime" in order to approach the subject from the perspective of industrial design. It seemed to me to help a lot to focus on physical objects rather than networking issues -- on the Thing, not the Internet. But there could be many different kinds of "Internets of things." They wouldn't necessarily have the qualities of "spimes." Spimes are things within a comprehensive production system that is clearly focussed on sustainability. I see "spimes" as part of a general struggle with major environmental problems. After a few years of development of the Internet of things, what are the key step(s) in designing and handling spimes ? There are six of them: digital plans for objects, digital identities for objects, digital manufacturing or "fabrication", a tracking system, a searching and datamining system, and a recycling system. But even if these six key technologies all develop and converge at a brisk pace, they will still need interaction design and probably social media in order to work. In "Shaping things", you wrote that 2010 would be the society for gizmos or spimes. How do you feel about it today? In order for "spimes" to come into existence, six technologies would have to converge. -

Ubiquitous Computing
Ubiquitous Computing Gabriela Avram IxDM13 The Trends in Computing Technology 1970s 1990s Late 1990s Now and Tomorrow ? Pervasive Computing Era Computing Evolution Ubiquitous Computing Mark Weiser, Xerox PARC 1988 “Ubiquitous computing enhances computer use by making many computers available throughout the physical environment, but making them effectively invisible to the user.” Source: Weiser, 1993a Pervasive (Ubiquitous) Computing Vision “In the 21st century the technology revolution will move into the everyday, the small and the invisible…” “The most profound technologies are those that disappear. They weave themselves into the fabrics of everyday life until they are indistinguishable from it.” Mark Weiser (1952 –1999), XEROX PARC Small, cheap, mobile processors and sensors " ! in almost all everyday objects " ! on your body (“wearable computing”) " ! embedded in environment (“ambient intelligence”) What is Ubiquitous Computing? ! Ubiquitous computing (ubicomp) integrates computation into the environment, rather than having computers which are distinct objects. ! The idea of ubicomp enable people to interact with information-processing devices more naturally and casually, and in ways that suit whatever location or context they find themselves in. Other terms used to describe this paradigm ! many of them are associated with a particular institution or perspective ! pervasive computing ! ambient intelligence ! everyware ! physical computing ! the "Internet of things" ! haptic computing ! things that think ! "spime"= theoretical object -

Internet of Things and the Metamorphosis of Objects-2.Pdf
The metamorphosis of objects and human subjects in the Internet of Things Sophie Le Pallec, Rick Bouter, Gérald Santucci “All things appear and disappear because of the concurrence of causes and conditions. Nothing ever exists entirely alone; everything is in relation to everything else.” Gautama Siddhartha Introduction Where in prior times technique was referring to: “a method of accomplishing a desired aim”, today we speak more of technology. Technology has long been presented as a set of techniques; today it has become more than a method to accomplish a desired aim. From now on, we live in ‘the age of makers’. In times when there are more people with mobile phone access than toothbrushes, everyone has the ability to start up a million euro business from behind the kitchen table. Technology does not only affect business any longer; it also affects culture, politics, society and every element we value in life. Maybe most important of all, it affects the human race as we know it today. For the reason technology will impact the way we have lived for ages, it is legitimate to ask whether there is an intersection where humans and objects will find a mutually beneficial coexistence, or whether one of these entities will rule over the other, or whether there will be an alliance between the human race and some sort of technology that represents a global connected world brain. Will technology be, like in prior times, a collection of methods to accomplishing a desired aim, or will the human race be enslaved by technology and ruled by the artificial intelligence embedded in it? 1. -

Internet of Things: Smart Things
International Journal of Future Computer and Communication, Vol. 4, No. 4, August 2015 Internet of Things: Smart Things Somayya Madakam B. Things Abstract—Research study on the Internet of Things and Smart Things has been going on for more than a decade and Thing can be defined as an entity, an idea, a quality reaches back to Mark Weiser’s original dream of ubiquitous perceived, or thought to have its own existence in the world. computing. Bruce Sterling recently popularized the idea of Things are also often interchanged with the word “Objects”. Smart Objects and the IoT. Smart Things is another paradigm When we are talking about things, they could be both Living shift in IT world. Smart Things are the things that are having Things and Non-Living Things. Things, in this context, can be embedding smartness or intelligence, identification, automation, monitoring and controlling calibre. Smart Things are assisting people, animals, plants, birds, servers, applications, shampoo human life a lot, nowadays without their applications life is bottles, cars, steering wheels, coffee machines, electronic becoming cumbersome. This paper exhibits systematically on devices, park benches or just about any other random item Internet, Things, and then explores on Internet of Things and that comes to our mind, even which could be vicinity dust also. finally Smart Things from researchers’, and corporate’s Everyday objects include not only electronic devices we perspective. Moreover, this article focuses on the state of Smart Things and its applications. This in turn would help the new encounter but also use daily, and technologically advanced researchers, who want to do research in this IoT domain. -

SHAPING THINGS by Bruce Sterling
SHAPING THINGS by bruce sterling designer LORRAINE WILD editorial director PETER LUNENFELD mediawork The MIT Press Cambridge, Massachusetts London, England CONTENTS 1. TO WHOM IT OUGHT TO CONCERN 5 2. TOMORROW COMPOSTS TODAY 8 3. OLD WINE IN NEW BOTTLES 15 4. THE PERSONAL IS HISTORICAL 25 5. METAHISTORY 37 6. A SYNCHRONIC SOCIETY 45 7. THE RUBBISH MAKERS 55 8. THE STARK NECESSITY OF GLAMOR 61 9. AN END-USER DRINKS GIZMO WINE 70 10. MEET THE SPIME 76 11. ARPHIDS 85 12. AN INTERNET OF THINGS 92 13. THE MODEL IS THE MESSAGE 95 14. FABBING 102 15. SPIME ECONOMICS 107 16. THE DESIGNER’S QUESTIONS 112 17. TOMORROW’S TOMORROW 133 18. UBLOPIA OR OTIVION 138 entroduction 146 designer’s notes 148 author’s notes 150 1. TO WHOM IT OUGHT TO CONCERN This book is about created objects and the environment, which is to say, it’s a book about everything. Seen from sufficient distance, this is a small topic. The ideal readers for this book are those ambitious young souls (of any age) who want to constructively inter- vene in the process of technosocial transformation. That is to say, this book is for designers and thinkers, engi- neers and scientists, entrepreneurs and financiers, and anyone else who might care to understand why things were once as they were, why things are as they are, and what things seem to be becoming. The world of organized artifice is transforming in ways that are poorly understood and little explored. There are two reasons why this is happening. -

The End of Cyberspace and Other Surprises
Convergence: The International Journal of Research into New Media Technologies Copyright © 2006 Sage Publications London, Thousand Oaks & New Delhi Vol 12(4): 383–391 FEATURE REPORT DOI: 10.1177/1354856506068316 http://cvg.sagepub.com The End of Cyberspace and Other Surprises Sue Thomas De Montfort University, UK Abstract / This article reports on Web 2.0, the end of cyberspace, and the internet of things. It proposes that these concepts have synergies both with the current fashion for modifying physical objects with the features of virtual objects, as evidenced in O’Reilly’s MAKE magazine and similar projects, and with the potential technologies for collective intelligence described by Bruce Sterling, Adam Greenfield, Julian Bleecker and others. It considers Alex Pang’s research on the end of cyber- space and asks whether the ‘new’ of new media writing will have any meaning in a world that is updated by the microsecond every time there is fresh activity in the system. Key Words / blogjects / books / collective intelligence / end of cyberspace / everyware / internet of things / new media writing / spimes / Web 2.0 1 In 2005 O’Reilly Media launched MAKE, ‘the first magazine devoted entirely to DIY tech- nology projects’. Resonant of the much earlier Homebrew Computer Club,1 founded in 1975 and home of many early hobbyist technology inventions, the magazine ‘unites, inspires and informs a growing community of resourceful people who undertake amazing projects in their backyards, basements and garages’ (MAKE Magazine, n.d.). It is a print magazine, although of course it is supported by a website and blog and all the usual paraphernalia. -
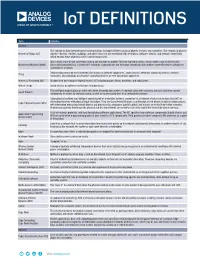
Iot DEFINITIONS
IoT DEFINITIONS Term Definition General The concept to allow Internet-based communications to happen between physical objects, sensors, and controllers. The network of physical Internet of Things (IoT) objects—devices, vehicles, buildings, and other items that are embedded with electronics, software, sensors, and network connectivity, which enables these objects to collect and exchange data. Was initially a one-to-one connection, linking one machine to another. This has evolved to mean a much wider range of devices with Machine-to-Machine (M2M) data easily transmitted via a system of IP networks. Communicate and exchange information with another connected device, without the assistance of a human. Device being measured and connected. Also known as Internet “appliances,” smart devices, netcentric computing devices, network Thing computers, and ubiquitous or pervasive computing devices, or even information appliances. Internet of Everything (IoE) Broader term describing the highest level of IoT, including people, things, machines, and subsystems. Web of Things Solely focuses on software architecture (narrow focus). The intelligent product plays an active role within the production system. It communicates with machines, humans, and other system Smart Product components to control its own processing, as well as its processing time in an independent manner. Cyber physical systems are intelligent objects based on embedded systems, connected to an Internet of data and services (also IoT) as interacting elements with physical input and output. They are characterized through a combination of real (physical) objects and processes Cyber Physical System (CPS) with information processing (virtual) objects and processes by using open, partially global, and always connected information networks. Autonomous systems that merge the physical and the virtual world, connected to each other and to the Internet by wire or wireless. -

Designing for the End of Life of Iot Objects
Edinburgh Research Explorer Designing for the End of Life of IoT Objects Citation for published version: Lechelt, S, Gorkovenko, K, Speed, C, Soares, L, Stead, M & Thorp, JK 2020, Designing for the End of Life of IoT Objects. in DIS' 20 Companion: Companion Publication of the 2020 ACM Designing Interactive Systems Conference. ACM, pp. 417-420, ACM Designing Interactive Systems 2020, Eindhoven, Netherlands, 6/07/20. https://doi.org/10.1145/3393914.3395918 Digital Object Identifier (DOI): https://doi.org/10.1145/3393914.3395918 Link: Link to publication record in Edinburgh Research Explorer Document Version: Peer reviewed version Published In: DIS' 20 Companion: Companion Publication of the 2020 ACM Designing Interactive Systems Conference General rights Copyright for the publications made accessible via the Edinburgh Research Explorer is retained by the author(s) and / or other copyright owners and it is a condition of accessing these publications that users recognise and abide by the legal requirements associated with these rights. Take down policy The University of Edinburgh has made every reasonable effort to ensure that Edinburgh Research Explorer content complies with UK legislation. If you believe that the public display of this file breaches copyright please contact [email protected] providing details, and we will remove access to the work immediately and investigate your claim. Download date: 31. Jul. 2020 Designing for the End of Life of IoT Objects Susan Lechelt James K. Thorp Abstract Katerina Gorkovenko Michael Stead The Internet of Things (IoT) and ubiquitous computing are Luis Lourenço Soares Lancaster University leading to an increase in objects with a short lifespan - ei- Chris Speed Lancaster, United Kingdom ther through breakage, “bricking” by the manufacturer, or University of Edinburgh [email protected] discontinued use by the owner. -

The Internet of Things: a Survey
Computer Networks 54 (2010) 2787–2805 Contents lists available at ScienceDirect Computer Networks journal homepage: www.elsevier.com/locate/comnet The Internet of Things: A survey Luigi Atzori a, Antonio Iera b, Giacomo Morabito c,* a DIEE, University of Cagliari, Italy b University ‘‘Mediterranea” of Reggio Calabria, Italy c University of Catania, Italy article info abstract Article history: This paper addresses the Internet of Things. Main enabling factor of this promising para- Received 10 December 2009 digm is the integration of several technologies and communications solutions. Identifica- Received in revised form 27 April 2010 tion and tracking technologies, wired and wireless sensor and actuator networks, Accepted 14 May 2010 enhanced communication protocols (shared with the Next Generation Internet), and dis- Available online 1 June 2010 tributed intelligence for smart objects are just the most relevant. As one can easily imagine, Responsible Editor: E. Ekici any serious contribution to the advance of the Internet of Things must necessarily be the result of synergetic activities conducted in different fields of knowledge, such as telecom- Keywords: munications, informatics, electronics and social science. In such a complex scenario, this Internet of Things Pervasive computing survey is directed to those who want to approach this complex discipline and contribute RFID systems to its development. Different visions of this Internet of Things paradigm are reported and enabling technologies reviewed. What emerges is that still major issues shall be faced by the research community. The most relevant among them are addressed in details. Ó 2010 Elsevier B.V. All rights reserved. 1. Introduction cation scenarios in which the new paradigm will play a leading role in the near future.