Analysis of Human Affect and Bug Patterns to Improve Software Quality and Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Regression Models by Gretl and R Statistical Packages for Data Analysis in Marine Geology Polina Lemenkova
Regression Models by Gretl and R Statistical Packages for Data Analysis in Marine Geology Polina Lemenkova To cite this version: Polina Lemenkova. Regression Models by Gretl and R Statistical Packages for Data Analysis in Marine Geology. International Journal of Environmental Trends (IJENT), 2019, 3 (1), pp.39 - 59. hal-02163671 HAL Id: hal-02163671 https://hal.archives-ouvertes.fr/hal-02163671 Submitted on 3 Jul 2019 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License International Journal of Environmental Trends (IJENT) 2019: 3 (1),39-59 ISSN: 2602-4160 Research Article REGRESSION MODELS BY GRETL AND R STATISTICAL PACKAGES FOR DATA ANALYSIS IN MARINE GEOLOGY Polina Lemenkova 1* 1 ORCID ID number: 0000-0002-5759-1089. Ocean University of China, College of Marine Geo-sciences. 238 Songling Rd., 266100, Qingdao, Shandong, P. R. C. Tel.: +86-1768-554-1605. Abstract Received 3 May 2018 Gretl and R statistical libraries enables to perform data analysis using various algorithms, modules and functions. The case study of this research consists in geospatial analysis of Accepted the Mariana Trench, a hadal trench located in the Pacific Ocean. -

Gretl User's Guide
Gretl User’s Guide Gnu Regression, Econometrics and Time-series Allin Cottrell Department of Economics Wake Forest university Riccardo “Jack” Lucchetti Dipartimento di Economia Università Politecnica delle Marche December, 2008 Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation (see http://www.gnu.org/licenses/fdl.html). Contents 1 Introduction 1 1.1 Features at a glance ......................................... 1 1.2 Acknowledgements ......................................... 1 1.3 Installing the programs ....................................... 2 I Running the program 4 2 Getting started 5 2.1 Let’s run a regression ........................................ 5 2.2 Estimation output .......................................... 7 2.3 The main window menus ...................................... 8 2.4 Keyboard shortcuts ......................................... 11 2.5 The gretl toolbar ........................................... 11 3 Modes of working 13 3.1 Command scripts ........................................... 13 3.2 Saving script objects ......................................... 15 3.3 The gretl console ........................................... 15 3.4 The Session concept ......................................... 16 4 Data files 19 4.1 Native format ............................................. 19 4.2 Other data file formats ....................................... 19 4.3 Binary databases .......................................... -

IASK Conference Nunes&Balsa .Pdf
Teaching Methodologies and Open Source Software: Empirical Application to Econometrics and Mathematics Alcina Nunes and Carlos Balsa Abstract — Nowadays, the software open source represents an important teaching resource. However, it is not sufficiently explored as an higher education teaching methodology. In subjects with a very specific goal, applied contents and attended by a small number of students, the commercial software is still preferred to the open source software. Aware of this reality, this paper presents a reflection about the use of open source software in Applied Econometrics and Mathematics. The adoption of two different software programmes – Gretl and Octave – allows the discussion about a comprehensive set of pedagogical, economical and technical advantages and some observed practical limitations. In practice, the refereed advantages are stressed when the students’ results are analysed. Their academic results benefit from the adoption of software which is executed, distributed and improved freely. Index Terms — Econometrics, Mathematics, Open-Source software , Teaching methodologies. —————————— —————————— 1 INTRODUCTION commercial software with which the teachers seem to have created strong personal and he access to open source software is professional links. Tnowadays a rather unexplored source of In the Escola Superior de Tecnologia e de academic pedagogic tools. Software Gestão do Instituto Politécnico de Bragança tools which are crucial to the promotion of, (ESTiG-IPB ) the use of open source software both theoretic and practical, learning is not uncommon. Indeed, the commercial processes in higher education teaching software is being substituted by open source institutions. software concerning operative systems, Along with commercial labels it is possible internet navigation, e-mail management and to find a large diversity of high quality free word processing programmes. -

Eugine Pavlov
Eugine Pavlov [email protected]; [email protected] +7 (968) 671 34 72 Moscow, Russia Nakhimovsky prospect, 47 Education BA in Economics, honors Belgorod State University, Belgorod, Russia, 2011 Concentration: International economics MA in Economics, honors Higher school of economics, Moscow, Russia, 2013 Concentration: Economics of energy and exhaustible resources MA in Economics New economic school, Moscow, Russia, expected 2014 Scholarships Potanin Charity Fund scholarship (2009-2011) Oxford Russia Fund scholarship (2011-2012) Higher school of economics scholarship for academic progress (2012-2013) Publications V. Kryukov, E. Pavlov (2012), “An approach to social and economic assessment of resource regime in an oil and gas sector (the case of the USA)”, Voprosy economiki, Vol.10, 105-116 p. Conferences, II Russian Congress for economic science (2013, Suzdal) summer schools Presentation: “An approach to social and economic assessment of resource regime in an oil and gas sector” E.ON Ruhrgas AG cycle of lectures on energy economics (2012, Moscow) Russian summer school on institutional analysis (2010, Moscow) Presentation: “A straw for a bubble: contract approach to irrational trading” XXXIX Week of science in Saint Petersburg polytechnic university Presentation: “Global financial transaction tax – effects of implementation” (2010, Saint Petersburg) I Russian Congress for economic science (2009, Moscow) Presentation: “Innovation effects under poor institutions” School on EU-Russia relations (2009, Voronezh) Research RA, topic concerning -

They Have Very Good Docs At
Intro to the Julia programming language Brendan O’Connor CMU, Dec 2013 They have very good docs at: http://julialang.org/ I’m borrowing some slides from: http://julialang.org/blog/2013/03/julia-tutorial-MIT/ 1 Tuesday, December 17, 13 Julia • A relatively new, open-source numeric programming language that’s both convenient and fast • Version 0.2. Still in flux, especially libraries. But the basics are very usable. • Lots of development momentum 2 Tuesday, December 17, 13 Why Julia? Dynamic languages are extremely popular for numerical work: ‣ Matlab, R, NumPy/SciPy, Mathematica, etc. ‣ very simple to learn and easy to do research in However, all have a “split language” approach: ‣ high-level dynamic language for scripting low-level operations ‣ C/C++/Fortran for implementing fast low-level operations Libraries in C — no productivity boost for library writers Forces vectorization — sometimes a scalar loop is just better slide from ?? 2012 3 Bezanson, Karpinski, Shah, Edelman Tuesday, December 17, 13 “Gang of Forty” Matlab Maple Mathematica SciPy SciLab IDL R Octave S-PLUS SAS J APL Maxima Mathcad Axiom Sage Lush Ch LabView O-Matrix PV-WAVE Igor Pro OriginLab FreeMat Yorick GAUSS MuPad Genius SciRuby Ox Stata JLab Magma Euler Rlab Speakeasy GDL Nickle gretl ana Torch7 slide from March 2013 4 Bezanson, Karpinski, Shah, Edelman Tuesday, December 17, 13 Numeric programming environments Core properties Dynamic Fast? and math-y? C/C++/ Fortran/Java − + Matlab + − Num/SciPy + − R + − Older table: http://brenocon.com/blog/2009/02/comparison-of-data-analysis-packages-r-matlab-scipy-excel-sas-spss-stata/ Tuesday, December 17, 13 - Dynamic vs Fast: the usual tradeof - PL quality: more subjective. -

Using the MIDAS Matlab Toolbox Via GNU Octave
Using the MIDAS Matlab Toolbox via GNU Octave Allin Cottrell∗ August 30, 2016 1 Introduction Eric Ghysels' MIDAS Matlab Toolbox is the benchmark implementation of MIDAS (Mixed Data Sampling) methods in econometrics, written by the economist who pioneered these methods.1 Octave is a free, open-source clone of Matlab, albeit|not surprisingly|not quite 100% compat- ible with the latter. It's often the case that for complex programs, some tweaks are required to get Matlab code to run on Octave, and the MIDAS Toolbox is a case in point. This note explains how to get the MIDAS Toolbox running on Octave. However, parts of the following may be of interest to Matlab users too, since some of the tweaks described below are also required to run Ghysels' code on Matlab R2016a for Linux.2 I begin by stating what's needed on the Octave side, then describe my modifications to the MIDAS Toolbox files. An annotated listing of these modifications is given in section 4. Section 5 provides instructions for installing the modified version of the Toolbox, and section 6 goes into some technicalities, for anyone who's interested. 2 On the Octave side First, you will need the io, optim and statistics packages installed; and optim requires struct. If you don't already have these, it's simply a matter of executing the following commands at the Octave prompt (when online, of course):3 pkg install -forge io pkg install -forge struct pkg install -forge optim pkg install -forge statistics Second, the MIDAS code calls the Matlab function addParameter, which is not supported in Octave (or not in Octave version ≤ 4.0.3 anyway). -

Gretl Manual
Gretl Manual Gnu Regression, Econometrics and Time-series Library Allin Cottrell Department of Economics Wake Forest University August, 2005 Gretl Manual: Gnu Regression, Econometrics and Time-series Library by Allin Cottrell Copyright © 2001–2005 Allin Cottrell Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation (see http://www.gnu.org/licenses/fdl.html). iii Table of Contents 1. Introduction........................................................................................................................................... 1 Features at a glance ......................................................................................................................... 1 Acknowledgements .......................................................................................................................... 1 Installing the programs................................................................................................................... 2 2. Getting started ...................................................................................................................................... 4 Let’s run a regression ...................................................................................................................... 4 Estimation output............................................................................................................................. 6 The -

Dennis Wesselbaum Contact Information Personal Data Appointments Professional Activities
Dennis Wesselbaum Contact Information University of Otago Department of Economics P.O. Box 56 Dunedin 9054 New Zealand Email: [email protected] Personal Webpage Personal Data Born: November 2, 1985 Citizenship: Germany, New Zealand Resident Appointments Lecturer, University of Otago, Department of Economics, 01/2016 - present. Researcher, University of Hamburg, Chair of Economics, Methods in Economics, 09/2012 - 09/2015. Research Assistant, Department of Money and Macroeconomics, Chair in Monetary and Fiscal Policy, Professor Ester Faia, 10/2011 - 09/2012. Researcher, The Kiel Institute for the World Economy, Research areas "Monetary Policy under Market Imperfections" and "Reforming the Welfare Society", 03/2010 - 07/2011. Professional Activities Research Visit, Johann-Wolfgang Goethe University, Frankfurt am Main, Germany, August - September 2014. Research Visit, Federal Reserve Bank of Chicago, United States, September - November 2010. Visit, Faculty of Economics, University of Pavia, Italy, December 2009 and July 2010. Visit, Department of Economics, University of Louvain la Neuve, Belgium, January 2010. Fellow, Euro Area Business Cycle Network (EABCN), since 2009. Fellow, German Physical Society (DPG), 2005 - 2015. Education Doctor rerum politicarum – University of Hamburg, 09/2012 - 11/2015. – Dissertation on "Fiscal Policy in General Equilibrium." Diploma in Economics (M.Sc. equivalent) – University of Kiel, GPA 1.3 (3.8 U.S. scale), 10/2005 - 03/2010. – Specialization: Macro Labor Economics and Monetary Policy. Abitur – Friedrich-List-Gymnasium, Lübeck, GPA 1.5. Research Interests Macroeconomics, Monetary and Fiscal Policy, Labor Economics, Time Series Econometrics, Game The- ory. Research Publications "Sectoral Labor Market E¤ects of Fiscal Spending", Structural Change and Economic Dynamics, 34: 19-35, 2015. -

MIDAS in Gretl
MIDAS in gretl Allin Cottrell Wake Forest University Gretl conference, Athens 2017 Subject matter “Mixed Data Sampling” in gretl See http://gretl.sourceforge.net/midas/, in particular ñ midas gretl.pdf : newly revised guide ñ midas-supp.pdf : supplement with forecasting experiments, etc. I will talk about some of the points in each of these documents. Mixed frequency data How to combine frequencies in a single data file/dataset? “Spread” the higher-frequency data. Here’s a slice of MIDAS data. gdpc96 indpro_m3 indpro_m2 indpro_m1 1947:1 1934.47 14.3650 14.2811 14.1973 1947:2 1932.28 14.3091 14.3091 14.2532 1947:3 1930.31 14.4209 14.3091 14.2253 1947:4 1960.70 14.8121 14.7562 14.5606 1948:1 1989.54 14.7563 14.9240 14.8960 1948:2 2021.85 15.2313 15.0357 14.7842 Creating a MIDAS dataset Importation from a database is easy (script): clear open fedstl.bin data gdpc96 data indpro --compact=spread store gdp_indpro.gdt Other methods: ñ Create two datasets, compact the high-frequency one, then use append. ñ Use matrices. ñ Use join. Creating a MIDAS dataset Importation from a database is easy (script): clear open fedstl.bin data gdpc96 data indpro --compact=spread store gdp_indpro.gdt Other methods: ñ Create two datasets, compact the high-frequency one, then use append. ñ Use matrices. ñ Use join. MIDAS lists A MIDAS list is a list of m series holding per-period values of a single high-frequency series, arranged in the order of most recent first. -
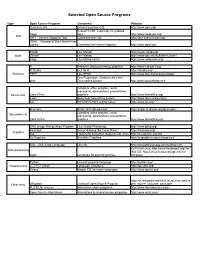
Selected Open Source Programs
Selected Open Source Programs Type Open Source Program Comments Website Quantum GIS General purpose GIS http://www.qgis.org/ Research GIS, especially for gridded Saga data http://www.saga-gis.org/ GIS GMT - Generic Mapping Tool Command line GIS http://gmt.soest.hawaii.edu/ GDAL - Geospatial Data Abstraction Library Command line raster mapping http://www.gdal.org Scilab Like Matlab http://www.scilab.org/ Math Octave Like Matlab http://www.gnu.org/software/octave/ Sage Like Mathematica http://www.sagemath.org/ R Statistics, data processing, graphics http://www.r-project.org/ R Studio GUI for R http://rstudio.org/ Statistics PSPP Like SPSS http://www.gnu.org/software/pspp/ Gnu Regression, Econometrics and gretl Time-series Library http://gretl.sourceforge.net/ Complete office program: word processing, spreadsheet, presentation, Documents Libre Office graphics http://www.libreoffice.org/ Latex Document typesetting system http://www.latex-project.org/ Lyx WYSIWYG front end for Latex http://www.lyx.org/ gnumeric Small, fast spreadsheet http://projects.gnome.org/gnumeric/ Complete office program: word Spreadsheets processing, spreadsheet, presentation, Libre Office graphics http://www.libreoffice.org/ GNU Image Manipulation Program Like Adobe Photoshop http://www.gimp.org/ Inkscape Vector drawing like Corel Draw http://inkscape.org/ Graphics Dia Flowcharts and other diagrams like Visio http://live.gnome.org/Dia SciGraphica Scientific Graphing http://scigraphica.sourceforge.net/ GDL - GNU Data Language Like IDL http://gnudatalanguage.sourceforge.net/ -

Rebecca Menssen Sites.Northwestern.Edu/Rebeccamenssen [email protected] | 612.998.4125
Last Updated on 15th April 2017 Rebecca Menssen sites.northwestern.edu/rebeccamenssen [email protected] | 612.998.4125 EDUCATION RESEARCH NORTHWESTERN UNIVERSITY MANI GROUP | GRADUATE RESEARCHER PHD IN ENGINEERING SCIENCES AND March 2015 – Present | Evanston, IL APPLIED MATHEMATICS Worked with Madhav Mani and in collaboration with the experimental group of Expected June 2019 | Evanston, IL Thomas Gregor to research the dynamics of chromatin in the early Drosophila GPA: 4.0/4.0 embryo. Projects include developing a mathematical model to explain the motion of Advisor: Madhav Mani single gene loci (paper in-progress), applying the model to experimental data, and later working on inferring transcription rates. Presenting work at the Chicago Area MS IN APPLIED MATHEMATICS SIAM Student Conference on April 15, 2017. June 2015 | Evanston, IL CENTER FOR GEOPHYSICAL STUDIES OF ICE AND CLIMATE ST. OLAF COLLEGE UNDERGRADUATE RESEARCHER BA IN MATHEMATICS, PHYSICS, June 2011 – August 2012 | Northfield, MN ECONOMICS Worked on WISSARD, an NSF funded project researching subglacial lakes in West June 2014 | Northfield, Minnesota Antarctica, in the lab of Dr. Robert Jacobel. Examined properties of ice and its layers GPA: 3.98/4.0 from radar data through data analysis and modeling. Work resulted in a poster at the summa cum laude Geological Society of America 2011 Conference and a publication in Annals of Distinction in Physics and Economics Glaciology. Phi Beta Kappa • Pi Mu Epsilon Sigma Pi Sigma • Omicron Delta Epsilon EXPERIENCE COURSEWORK KEMPS LLC | ST. OLAF MATHEMATICS PRACTICUM INTERN January 2014 | St. Paul/Northfield, MN Machine Learning • High Performance Created a model for milk sales volume, and presented findings and the model to the Computing • Numerical Methods for company, including the CFO. -

Download (1MB)
Developing Policy Inputs for Efficient Trade and Sustainable Development Using Data Analysis Mini.K.G Senior Scientist, Fisheries Resources Assessment Division Central Marine Fisheries Research Institute, Kochi Email: [email protected] Introduction Trade forms a vital part of the world economy. The analysis of data on trade and related parameters plays a pivotal role in developing policy inputs for efficient trade and sustainable development. It is evident that the success of any type of analysis depends on the availability of the suitable type of data. In general, time series, cross sectional and pooled data are the three types of data available for trade analysis. Time series data are characterized by observations collected at regular intervals over a period of time while cross-sectional data are data on one or more variables collected at the same point of time. The pooled data is a combination of time series and cross-sectional data. For example, panel data, which is a special type of pooled data is used to study the relationship between trade flows and trade barriers over time. In recent years, the quantitative and qualitative analysis of trade and the effects of policies have grown sharply. This was due to the advances in the theoretical and analytical techniques as well as increased computational and data processing power of computers. A multitude of analysis tools are available in today’s world for a thorough and scientifically valid analysis of data. There are several choices available for the user to choose from – ranging from the general public license packages, analysis packages with statistical add-ons, general purpose languages with statistics libraries to the advanced proprietary packages.