Coordination Avoidance in Distributed Databases
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SCIS Boardman Labs User Manual Version5
SCIS Common Use Labs in Boardman Hall USER MANUAL Note: The instructions in this manual assume students walking into the labs are first-time users of the labs and are complete novices in using the machines. Table of Contents Page I. Access to Boardman Hall SCIS Labs for Computer Science and New Media Students A. Services Provided 2 B. Gaining Access to Lab Rooms and Computers 3 II. SCIS Common Use Lab (Room 138 Boardman) A. Services Provided 3 B. Use of iMacs on Tables 4 C. Use of Large Table Monitor for Sharing Among Table Group 4 D. Use of Overhead Projector 5 E. Use of Laser Printer (8 ½ by 11” Prints) 6 F. Use of Large Format Plotter 7 G. Software Available on Computers in Room 138 7 H. Equipment Available for Checkout from Room 138 Lab Monitors 8 III. Combined Focus Ring and Stillwater Labs (Rooms 127 and 129 Boardman) A. Services Provided 8 B. Use of iMacs on Tables 9 C. Use of Cybertron PC for AI and VR D. Use of … E. Software Available on Computers in Rooms 127 and 129 F. Equipment Checkout Procedure G. Equipment Available for Checkout from Rooms 127 and 129 Lab Monitors IV. SCIS Student Lounge and Project Work Room (Room 137 Boardman) A. Services Provided B. Use of Large Screen by Students APPENDICES Appendix A. Laptop Computer Recommendations for Computer Science Students Appendix B. Laptop Computer Recommendations for New Media Students Appendix C. Convenient Web Resources for Development of Computer Code Note: On SCIS web site all of the above topics will link to anchors at the same topics below. -
Coordination Avoidance in Database Systems
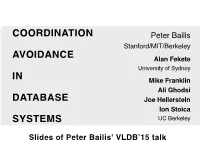
COORDINATION Peter Bailis Stanford/MIT/Berkeley AVOIDANCE Alan Fekete University of Sydney IN Mike Franklin Ali Ghodsi DATABASE Joe Hellerstein Ion Stoica SYSTEMS UC Berkeley Slides of Peter Bailis' VLDB’15 talk VLDB 2014 Default Supported? Serializable Actian Ingres NO YES Aerospike NO NO transactions are Persistit NO NON Clustrix NO NON not as widely Greenplum NO YESN IBM DB2 NO YES deployed as you IBM Informix NO YES MySQL NO YES might think… MemSQL NO NO MS SQL Server NO YESN NuoDB NO NO Oracle 11G NO NON Oracle BDB YES YESN Oracle BDB JE YES YES PostgreSQL NO YES SAP Hana NO NO ScaleDB NO NON VoltDB YES YESN VLDB 2014 Default Supported? Serializable Actian Ingres NO YES Aerospike NO NO transactions are Persistit NO NON Clustrix NO NON not as widely Greenplum NO YESN IBM DB2 NO YES deployed as you IBM Informix NO YES MySQL NO YES might think… MemSQL NO NO MS SQL Server NO YESN NuoDB NO NO Oracle 11G NO NON Oracle BDB YES YESN WHY?Oracle BDB JE YES YES PostgreSQL NO YES SAP Hana NO NO ScaleDB NO NON VoltDB YES YESN serializability: equivalence to some serial execution “post on timeline” “accept friend request” very general! serializability: equivalence to some serial execution r(x) w(y←1) r(y) w(x←1) very general! …but restricts concurrency serializability: equivalence to some serial execution CONCURRENT EXECUTION r(x)=0 r(y)=0 w(y←1) IS NOT w(x←1) SERIALIZABLE! verySerializability general! requires Coordination …buttransactions restricts cannot concurrency make progress independently Serializability requires Coordination transactions cannot make progress independently Two-Phase Locking Multi-Version Concurrency Control Blocking Waiting Optimistic Concurrency Control Pre-Scheduling Aborts Costs of Coordination Between Concurrent Transactions 1. -

Tworzenie Dokumentów, Prawo Autorskie
Zajęcia 7 - tworzenie dokumentów JANUSZ WRÓBEL Typy plików Tekstowe txt – najprostszy plik tekstowy np. z Notatnika doc, docx - dokumenty z WORDA lub WORDPADA odt – dokumenty z programu OPENOFFICE rtf – format tekstowy zawierający podstawowe formatowanie tekstu kompatybilny z wieloma edytorami tekstu Graficzne jpg – najpopularniejszy format plików graficznych png – format głównie wykorzystywany przez Internet gif – format graficzny umożliwiający przechowanie wielu obrazów tworzących np. animację Tiff – format kompresji bezstratnej Dźwiękowe Mp3 – najpopularniejszy, stratny zapis dźwięku Midi - standard dla przechowywania zapisu dźwięku zbliżonego do nutowego Wav – popularny standard dla Windowsa i internetu Wma – gównie pliki w Windowsie Wideo MPEG4 – najpopularniejszy standard kodowania umożliwiający rejestrowanie i przesyłanie na bieżąco wizji i fonii. MOV- kodowanie firmy Apple wymaga specjalnego odtwarzacza QuickTime Player Avi – format zapisu filmów zwykle przeznaczonych do dalszej obróbki WMV – format kompresji filmów firmy Microsoft FLV – format filmów wykorzystywany na stronach www Uruchamialne EXE – popularny dla Windowsa plik programu mogący zawierać różne zasoby np. okna, ikony, dźwięki BAT – program wykonywany przez komputer bez wpływu użytkownika na jego przebieg (tryb wsadowy) COM – dawniej popularny typ programów wykonywalnych w systemie DOS Skompresowane ZIP – format kompresji bezstratnej i archiwizacji na PC (Personal Computer) RAR – format kompresji bezstratnej i archiwizacji JPG, MPEG, MP3 – to -
Audacity® Is Recording and Audio Editing Software That Is Free, Open Sourced, and Generally Easy to Use
How to Use Introduction Audacity® is recording and audio editing software that is free, open sourced, and generally easy to use. Audacity® can be used to record live audio, edit various sound files, convert from tapes and records to digital audio or CDs, and so much more! This software can be used for Windows, Mac OS X, GNU/Linux, and a variety of other operating systems. Audacity® User Interface This is a screenshot of Audacity®. The next section of this How-To guide will introduce you to this user interface. Copyright © 2008 Audacity® How- to 1 Audacity® User Interface: Toolbars The Audacity® Control Toolbar Envelope Tool Skip to Start Stop Button Button Select D r a w Record Tool Tool Button Zoom Multi- Tool Tool Pause Skip to End Timeshift Play Button Button Tool Button The Audacity® Edit Toolbar Zoom Zoom To Copy Cut Paste Undo Redo Out Selection Zoom Zoom To Trim Silence In Entire Project The Audacity® Meter & Mixer Toolbars Input Output Level Level Meter Meter Output Input Volume Volume Input Control Control Source Selector Copyright © 2008 Audacity® How- to 2 Importing Audio with Audacity® 1. Create a New Project This is an important step. Give your project a name & saving location prior to working in Audacity®. Select and choose a file name and location to save your project. *Note when you initially begin Audacity® only the “Save As” function will be available. 2. Check Preferences Click File > Preferences (Ctrl + P) Check to be sure the correct Playback & Recording Devices have been selected. Copyright © 2008 Audacity® How- to 3 Set the sample rate of your choice. -

Command-Line Sound Editing Wednesday, December 7, 2016
21m.380 Music and Technology Recording Techniques & Audio Production Workshop: Command-line sound editing Wednesday, December 7, 2016 1 Student presentation (pa1) • 2 Subject evaluation 3 Group picture 4 Why edit sound on the command line? Figure 1. Graphical representation of sound • We are used to editing sound graphically. • But for many operations, we do not actually need to see the waveform! 4.1 Potential applications • • • • • • • • • • • • • • • • 1 of 11 21m.380 · Workshop: Command-line sound editing · Wed, 12/7/2016 4.2 Advantages • No visual belief system (what you hear is what you hear) • Faster (no need to load guis or waveforms) • Efficient batch-processing (applying editing sequence to multiple files) • Self-documenting (simply save an editing sequence to a script) • Imaginative (might give you different ideas of what’s possible) • Way cooler (let’s face it) © 4.3 Software packages On Debian-based gnu/Linux systems (e.g., Ubuntu), install any of the below packages via apt, e.g., sudo apt-get install mplayer. Program .deb package Function mplayer mplayer Play any media file Table 1. Command-line programs for sndfile-info sndfile-programs playing, converting, and editing me- Metadata retrieval dia files sndfile-convert sndfile-programs Bit depth conversion sndfile-resample samplerate-programs Resampling lame lame Mp3 encoder flac flac Flac encoder oggenc vorbis-tools Ogg Vorbis encoder ffmpeg ffmpeg Media conversion tool mencoder mencoder Media conversion tool sox sox Sound editor ecasound ecasound Sound editor 4.4 Real-world -

La Metodología TRIZ E Integración De Software De Licencia Libre Con Módulos Multifuncionales Como Estrategia De
10º Congreso de Innovación y Desarrollo de Productos Monterrey, N.L., del 18 al 22 de Noviembre del 2015 Instituto Tecnológico de Estudios Superiores de Monterrey, Campus Monterrey. 1 10º Congreso de Innovación y Desarrollo de Productos Monterrey, N.L., del 18 al 22 de Noviembre del 2015 Instituto Tecnológico de Estudios Superiores de Monterrey, Campus Monterrey. La metodología TRIZ e Integración de software de licencia libre con módulos multifuncionales: como estrategia de fortalecimiento y competitividad en empresas emergentes de México. Guillermo Flores Téllez Jaime Garnica González Joselito Medina Marín Elisa Arisbé Millán Rivera José Carlos Cortés Garzón Resumen El sistema productivo de México se constituye en gran proporción, por empresas emergentes que funcionan como negocios familiares, surgidos a través de una idea creativa, para emprender una actividad económica específica, ya sea de la producción de un bien o prestación de servicio. El funcionamiento de este tipo de empresas es limitado, son compañías surgidas del emprendimiento con contribuciones positivas hacia la práctica de la innovación, desarrollo de procesos y generación de empleos principalmente. Sin embargo, estas empresas se encuentran en desventaja para afrontar el entorno tecnológico global, porque no disponen de los recursos económicos, infraestructura, maquinaria o equipo que les brinde la posibilidad de operación estable y competencia internacional. El presente artículo exhibe alternativas viables y sus medios de implementación; como lo son la sinergia de operación de la metodología TRIZ y los módulos de software de gestión de negocios, para apoyar el proceso de innovación y el monitoreo de nuevas ideas llevadas al mercado, por parte de una empresa emergente. -

Audacity Manual.Pdf
A Free, Open Source, Cross-Platform Audio Editor Version 1.2.4 This is the online help for Audacity. It is meant to be a quick reference, not a complete manual. There is also a complete user's manual available online: http://audacity.sourceforge.net/help/documentation Table of Contents Table of Contents............................................................................................................................ 1 Toolbars .......................................................................................................................................... 3 Control Toolbar........................................................................................................................... 3 Editing Tools........................................................................................................................... 3 Audio Control Buttons............................................................................................................ 3 Mixer Toolbar ............................................................................................................................. 4 Edit Toolbar ................................................................................................................................4 Meter Toolbar ............................................................................................................................. 5 Menu Bar ....................................................................................................................................... -

Audacity: Record, Import & Export on Windows & Macintosh Platforms
IMC Innovate Make Create https://library.albany.edu/imc/ 518 442-3607 Audacity: record, import & export on Windows & Macintosh platforms Audacity is an open-source application to edit sound files and convert them to various formats. It is freely available to the public for download. The copyright law of the United States (Title 17, United States Code) governs the reproduction of copyrighted material. The person using this equipment and software is liable for any infringement. To install Audacity, download from https://www.audacityteam.org/. To work with many audio file types (i.e. OGG, ac3, and audio from video) download the FFmpeg plug-in [NOTE: versions previous to 2.3.2 also require the MP3 lame encoder to work with MP3 files]. After installing Audacity, open the application. From the top line menu select Edit > Preferences on Windows and Audacity > Preferences on Mac. Select Libraries from the menu on the left. Select Download for FFmpeg. Follow the instructions for adding this export/import Library. NOTES when working in Audacity If you are using multiple tracks, they should all be the same format. Use the [keyboard] space bar to play and stop the audio track If Pause or Play is selected you cannot execute commands. IMPORTING A SOUND FILE NOTES: Audio files from a CD must first be “ripped” or extracted using CD extraction software and then imported into Audacity. Audio may be extracted from video. From the top line menu select File > Import > Audio... Page 1 of 4 Make a copy of the file before editing to ensure that the original audio is untouched and that the file imported into Audacity will always be associated with the project. -

Khodayari and Giancarlo Pellegrino, CISPA Helmholtz Center for Information Security
JAW: Studying Client-side CSRF with Hybrid Property Graphs and Declarative Traversals Soheil Khodayari and Giancarlo Pellegrino, CISPA Helmholtz Center for Information Security https://www.usenix.org/conference/usenixsecurity21/presentation/khodayari This paper is included in the Proceedings of the 30th USENIX Security Symposium. August 11–13, 2021 978-1-939133-24-3 Open access to the Proceedings of the 30th USENIX Security Symposium is sponsored by USENIX. JAW: Studying Client-side CSRF with Hybrid Property Graphs and Declarative Traversals Soheil Khodayari Giancarlo Pellegrino CISPA Helmholtz Center CISPA Helmholtz Center for Information Security for Information Security Abstract ior and avoiding the inclusion of HTTP cookies in cross-site Client-side CSRF is a new type of CSRF vulnerability requests (see, e.g., [28, 29]). In the client-side CSRF, the vul- where the adversary can trick the client-side JavaScript pro- nerable component is the JavaScript program instead, which gram to send a forged HTTP request to a vulnerable target site allows an attacker to generate arbitrary requests by modifying by modifying the program’s input parameters. We have little- the input parameters of the JavaScript program. As opposed to-no knowledge of this new vulnerability, and exploratory to the traditional CSRF, existing anti-CSRF countermeasures security evaluations of JavaScript-based web applications are (see, e.g., [28, 29, 34]) are not sufficient to protect web appli- impeded by the scarcity of reliable and scalable testing tech- cations from client-side CSRF attacks. niques. This paper presents JAW, a framework that enables the Client-side CSRF is very new—with the first instance af- analysis of modern web applications against client-side CSRF fecting Facebook in 2018 [24]—and we have little-to-no leveraging declarative traversals on hybrid property graphs, a knowledge of the vulnerable behaviors, the severity of this canonical, hybrid model for JavaScript programs. -

Osvのご紹介 in Iijlab セミナー
OSvのご紹介 in iijlab セミナー Takuya ASADA <syuu@cloudius-systems> Cloudius Systems 自己紹介 • Software Engineer at Cloudius Systems • FreeBSD developer (bhyve, network stack..) Cloudius Systemsについて • OSvの開発母体(フルタイムデベロッパで開発) • Office:Herzliya, Israel • CTO : Avi Kivity → Linux KVMのパパ • 他の開発者:元RedHat(KVM), Parallels(Virtuozzo, OpenVZ) etc.. • イスラエルの主な人物は元Qumranet(RedHatに買収) • 半数の開発者がイスラエル以外の国からリモート開発で参加 • 18名・9ヶ国(イスラエル在住は9名) OSvの概要 OSvとは? • OSvは単一のアプリケーションをハイパーバイザ・IaaSでLinuxOSな しに実行するための新しい仕組み • より効率よく高い性能で実行 • よりシンプルに管理しやすく • オープンソース(BSDライセンス)、コミュニティでの開発 • http://osv.io/ • https://github.com/cloudius-systems/osv 標準的なIaaSスタック • 単一のアプリケーションを実行するワークロードでは フルサイズのゲストOS+フル仮想化はオーバヘッド コンテナ技術 • 実行環境をシンプルにする事が可能 • パフォーマンスも高い ライブラリOS=OSv • コンテナと比較してisolationが高い 標準的なIaaSスタック: 機能の重複、オーバヘッド • ハイパーバイザ・OSの双方が ハードウェア抽象化、メモリ Your App 保護、リソース管理、セキュ リティ、Isolationなどの機能 Application Server を提供 JVM • OS・ランタイムの双方がメモ Operating System リ保護、セキュリティなどの 機能を提供 Hypervisor • 機能が重複しており無駄が多 Hardware い OSv: 重複部分の削除 • 重複していた多くの機能を排 Your App 除 Application Server • ハイパーバイザに従来のOSの JVM 役割を負ってもらい、OSvは Core その上でプロセスのように単 Hypervisor 一のアプリケーションを実行 Hardware OSvのコンセプト • 1アプリ=1インスタンス→シングルプロセス • メモリ保護や特権モードによるプロテクションは 行わない • 単一メモリ空間、単一モード(カーネルモード • Linux互換 libc APIを提供、バイナリ互換(一部) • REST APIによりネットワーク経由で制御 動作環境 • ハイパーバイザ • IaaS • KVM • Amazon EC2 • Xen • Google Compute • VMware Engine • VirtualBox 対応アーキテクチャ • x86_64(32bit非サポート) • aarch64 対応アプリ (Java) • JRuby(Ruby on Railsなど) • OpenJDK7,8 • Ringo.JS • Tomcat • Jython • Cassandra • Erjang • Jetty • Scala • Solr • Quercus(PHPエンジン、 -

Le Capitole Du Libre
Capitole du Libre 2016 Communiqué de Presse 8 novembre 2016 Benh Lieu Song – CC-BY-SA 3.0 Association Toulibre http://toulibre.org http://capitoledulibre.org [email protected] Le Capitole du Libre Le Capitole du Libre est un évènement tout public de promotion des logiciels libres, organisé par l’association Toulibre. Il se déroule à Toulouse, chaque année depuis 2009, sur un weekend du mois de novembre. Grâce à une programmation variée et de qualité, le Capitole du Libre est aujourd’hui une référence parmi les manifestations consacrées aux logiciels libres. Le public et les orateurs y viennent plus nombreux — et de plusieurs pays voisins — chaque année. Tout au long du weekend, des conférences et des ateliers pratiques sur des sujets variés, aussi bien techniques que grand public, se déroulent en parallèle. Le Capitole du Libre est également l’occasion de réunir des communautés du libre pour des conférences, lightning talks, coding sprints… Le Capitole du Libre a accueilli plusieurs évènements depuis 2011 tels que : • DrupalCamp en 2011 ; • DjangoCon en 2012 ; • FranceJS en 2013 ; • LuaWorkshop en 2013 ; • OpenStack en 2013 ; • Hackfest LibreOffice en 2014 ; • Akademy-FR depuis la première édition ! Un village associatif permet également de présenter les projets des associations du libre : Liberté0, Wikimédia France, OpenStreetMap France, Framasoft ou encore Tetaneutral.net. Amphithéâtre comble pour Stéphane Bortzmayer de l’AFNIC L’évènement est basé uniquement sur le bénévolat. Durant les mois de préparation et pendant tout le weekend, Capitole du Libre 2016 https://2016.capitoledulibre.org Dossier de Presse 2/7 100 bénévoles des associations et des clubs techniques de l’INP-ENSEEIHT se sont mobilisés pour l’élabo- ration du programme, l’accueil du public, la captation des conférences ou encore l’aide à l’installation des logiciels libres. -

Name Synopsis Description
SoX(1) Sound eXchange SoX(1) NAME SoX − Sound eXchange, the Swiss Army knife of audio manipulation SYNOPSIS sox [global-options][format-options] infile1 [[format-options] infile2]... [format-options] outfile [effect [effect-options]] ... play [global-options][format-options] infile1 [[format-options] infile2]... [format-options] [effect [effect-options]] ... rec [global-options][format-options] outfile [effect [effect-options]] ... DESCRIPTION Introduction SoX reads and writes audio files in most popular formats and can optionally apply effects to them. It can combine multiple input sources, synthesise audio, and, on manysystems, act as a general purpose audio player or a multi-track audio recorder.Italso has limited ability to split the input into multiple output files. All SoX functionality is available using just the sox command. Tosimplify playing and recording audio, if SoX is invokedas play,the output file is automatically set to be the default sound device, and if invokedas rec,the default sound device is used as an input source. Additionally,the soxi(1) command provides a con- venient way to just query audio file header information. The heart of SoX is a library called libSoX. Those interested in extending SoX or using it in other pro- grams should refer to the libSoX manual page: libsox(3). SoX is a command-line audio processing tool, particularly suited to making quick, simple edits and to batch processing. If you need an interactive,graphical audio editor,use audacity(1). *** The overall SoX processing chain can be summarised as follows: Input(s) → Combiner → Effects → Output(s) Note however, that on the SoX command line, the positions of the Output(s) and the Effects are swapped w.r.t.