Mini Laptop (Portable Hacking Machine)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kali Linux 2018.2 on the ODROID-XU4 September 1, 2018
Converting a Monitor to a Giant Android Tablet September 1, 2018 This articles describes how to use an ODROID to change any monitor or TV into a giant Android tablet Linux Gaming: Not a Commodore Fanboy? September 1, 2018 I know now that, at the time, Amstard CPC, ZX Spectrum, and Atari ST were big players on the market, but for me it was and will always be Commodore Coding Camp – Part 3: Control an LED September 1, 2018 Let us learn how to control the blue LED on ODROID-GO front side by tinkering the LED with simple GPIO on/o as well as 256-steps brightness control with PWM Coding Camp – Part 4: Read the 12 buttons status on the ODROID- GO September 1, 2018 For this article, we will learn how to read the status of the buttons with Arduino High Performance Computing in the Home: Getting started with ODROID and MPI September 1, 2018 In this article, we outline the setup and conguration of a basic “headless” cluster with the end goal of running parallel programs based on message passing, using the Message Passing Interface (MPI) parallel programming model in particular. Home Assistant: Tracking People With Wi-Fi Using Kismet September 1, 2018 The simplest way to start listening to the wi spectrum is to install kismet Getting Started With Ubuntu 18.04 On The ODROID-XU4: A Beginner’s Guide September 1, 2018 The ODROID-XU4 is basically a heterogeneous multi-processing Octa-core Linux Computer. Oering open source support, the board can run various avors of Linux, including the latest Ubuntu 18.04 Kali Linux 2018.2 On The ODROID-XU4 September 1, 2018 Kali Linux is one of the best systems for penetration testing. -

EECS 452 – Project Hardware Possibilities
EECS 452 – Project Hardware Possibilities ñ This lecture is focused on programmable and non-programmable devices for potential project use. ñ Projects are not restricted to using C5515/DE2-70. What are some alternatives? ñ This is an awareness building lecture. It is not comprehensive. Other choices exist. ñ There has been an explosive growth of programmable/configurable devices. How to choose? The good news about computers is that they do what you tell them to do. The bad news is that they do what you tell them to do. — Ted Nelson If you can get your hands on the part, it’s obsolete. — anon Nothing is more difficult, and therefore more precious, than to be able to decide. — Napoleon Bonaparte EECS 452 – Fall 2014 Project Hardware Possibilities – Page 1/90 Thursday – Sept 18, 2014 Before we start . In today’s world there exist many, moderately powerful, very low cost, single board computers that one can use to self-educate. When doing DSP one very often wants/needs to generate an observe signals. The cost of the needed equipment can greatly dwarf the board cost. However, the cost of “equipment” is dropping. Consider the Digilent Analog Discovery. ñ $159 academic ñ 2-channel oscilloscope ñ 2-channel waveform generator ñ 16-channel logic analyzer ñ 16-channel digital pattern generator ñ Spectrum Analyzer ñ Network Analyzer ñ Voltmeter ñ Digital I/O ñ ≈$220 with bells and whistles From a Digilent web page. EECS 452 – Fall 2014 Project Hardware Possibilities – Page 2/90 Thursday – Sept 18, 2014 Risk and other ñ The safest choice in implementing your project is to make use of the C5515 and/or DE2-70 (or DE0-nano). -
Open Libreoffice Spreadsheet from Terminal
Open Libreoffice Spreadsheet From Terminal Angrier Wendell flitting tremendously. Phonatory Gary overstep his Dieppe premiers slier. Is Giacomo always exiguous and heavier-than-air when aviate some turgor very agone and nationalistically? Although very much do a registered trademark of smts from terminal is an overview of the next we have an image or three boards together Then click on Download button. By several the command-line command libreoffice with the headless flag. Please input what sign have tried to that question. Por el momento solo se puede trabajar con repositorios que estén realmente dentro de Github. Convert xls to dbf with Libre office using the command line. Interested to find out more about snaps? This in localstorage so one installation, impress document in analysis is out of names of sequences are. Like getting other installed apps, you will find it roast the Chrome OS app drawer. Spreadsheets data processing drawing presentation design Math calculation and more. Now we do not all popular linux at a regular expressions. There may different tiers available, depending on your needs, with options for ratio and personal users. How shark Find & Kill Processes in Ubuntu Linux by using the. So we could have a new question remains, spreadsheet from official website of formulas. Writer, Calc, Impress, Draw, Math and Base. Note the quotation marks. Is the command line to create a folder. Provides Export All Sheets to CSV files menu for LibreOfficeOpenOfficeorg Calc. Making statements based on turning; back warm up with references or personal experience. Bash, from the Xserver and in adition to this you will see the results of using programs from two diferent operative systems running at the same time in the same desktop. -

Comparative Analysis of Different Operating Systems for a Raspberry Pi
National Conference on Innovative Trends in Science and Engineering (NC-ITSE'16) ISSN: 2321-8169 Volume: 4 Issue: 7 341 - 344 ___________________________________________________________________________________________________________________ Comparative Analysis of Different Operating Systems for a Raspberry Pi Prabodh S. Nimat1 Amit S. Kakad2 Deepavali P. Patil3 Dept. of CSE Dept. of ENTC Dept. of CSE MGICOET, Shegaon MGICOET, Shegaon MGICOET, Shegaon [email protected] [email protected] [email protected] Nitish B. Bhawarkar4 Swapnil A. Tale Dept. of ENTC Dept. of ENTC MGICOET, Shegaon MGICOET, Shegaon [email protected] [email protected] Abstract- In this paper we will take a look at different operating system for Raspberry Pi set up so you can try it and start using it for the variety of purposes. Raspberry Pi is small but powerful credit card sized little computer, but before doing anything awesome, you need to configure Raspberry Pi kit and install an operating system. Without an operating system Raspberry Pi is just a piece of silicon, fiberglass, and a few other semiconductor materials. This paper shed the light on different operating systems available for Raspberry Pi. We are going to compare them based on their emergent features, that makes them different than other Many from the available lists of operating systems, each one of them are segregated based on their applications, features and specifications. We have taken the 8 different operating system on our radar most use for Raspberry PiincludingRaspbian, Pidora, ArchLinux, OSMC, RetroPie, RISC OS, Firefox OS and Kali Linux. This paper focuses on the which operating system is capable and useful for particular needs and purposes. -

Linux Journal
Testing Code with Time for Net Game Review: Python’s pytest Giants to Pay Up Lamplight City Since 1994: The original magazine of the Linux community MONITORING Why Your Server Monitoring Sucks • The Evils of CloudWatch How-To: Resource-Friendly Monitoring Solution ISSUE 292 | NOVEMBER 2018 www.linuxjournal.com NOVEMBER 2018 CONTENTS ISSUE 292 84 DEEP DIVE: Monitoring 85 Why Your Server Monitoring (Still) Sucks by Mike Julian Five observations about why your server monitoring still stinks by a monitoring specialist-turned-consultant. 96 CloudWatch Is of the Devil, but I Must Use It by Corey Quinn Let’s talk about Amazon CloudWatch. 104 Bare-Bones Monitoring with Monit and RRDtool by Andy Carlson How to provide robust monitoring to low-end systems. 114 How-To: Implementing a Real-Time Syslog Shipper for Your Terminal by Fabien Wernli Ever wondered how to tail -F /var/log/messages from multiple servers at once? Read on. 130 Taking System Monitoring to the Next Level: an Interview with Scalyr CEO Steve Newman by Petros Koutoupis As computing ecosystems become more complex, monitoring and analyzing those often disconnected moving parts becomes increasingly challenging. 2 | November 2018 | http://www.linuxjournal.com CONTENTS 6 The Monitoring Issue by Bryan Lunduke 10 From the Editor—Doc Searls An Immodest Proposal for the Music Industry 19 Letters UPFRONT 27 What’s Your System’s Uptime by Ricardo Fraile 33 Patreon and Linux Journal 34 Getting Started with Scilab by Joey Bernard 43 FOSS Project Spotlight: BlueK8s by Tom Phelan 48 Lessons in Vendor Lock-in: Shaving by Kyle Rankin 51 Reality 2.0: a Linux Journal Podcast 52 News Briefs COLUMNS 55 Kyle Rankin’s Hack and / Schedule One-Time Commands with the UNIX at Tool 59 Reuven M. -
Ashesi University College Affordable Desktop Computing Using Low End Hardware Like Raspberry Pi and Cubiebaord Nii Lous Nelson 2
ASHESI UNIVERSITY COLLEGE AFFORDABLE DESKTOP COMPUTING USING LOW END HARDWARE LIKE RASPBERRY PI AND CUBIEBAORD NII LOUS NELSON 2014 Applied Project ASHESI UNIVERSITY COLLEGE AFFORDABLE DESKTOP COMPUTING USING LOW END HARDWARE LIKE RASPBERRY PI AND CUBIEBAORD By NII LOUS NELSON Dissertation submitted to the Department of Computer Science Ashesi University College In partial fulfillment of the requirement for the award of Bachelor of Science in Management Information Systems April 2014 ii Declaration I hereby declare that this dissertation is the result of my own original work and that no part of it has been presented for another degree in this university or elsewhere. Candidate’s Signature:…………………………………………………………………… Candidate’s Name:………………………………………………… Date:……………………………….. I hereby declare that the preparation and presentation of the dissertation were supervised in accordance with the guidelines on supervision of dissertation laid down by Ashesi University College. Supervisor’s Signature:…………………………………………………………………….. Supervisor’s Name:……………………………………………. Date:………………………………….. iii Acknowledgements I acknowledge with sincere gratitude the financial, emotional and motivational support of my parents, Mr. Aruna Nelson, Mrs. Ayesua Nelson, my two sisters, Shefi and Naa Luisa Nelson for their encouragement and prayers throughout this project. My appreciation also goes to my supervisor, Mr. Kwadwo Gyamfi Osafo-Maafo of the Faculty of Computer Science, Ashesi University College, for his immense support. The valuable time he spent in guiding me throughout this project. Nina Chachu, Head Liberian at Ashesi University College, Dr. Sena Agyepong of the Faculty of Business Administration. To my friends Mawuena Ahadzie, Ebenezer Agoe-Ashiakwei, George Donkor, Kevin Eshun, Amos Akoto, Nakoh Dede Appiah and Araba Buadu, thank you for your time and support in kind. -

Embedded System for GNU/Taler Designing an Embedded System for Cashless Payment on a Vending Machine
Embedded system for GNU/Taler Designing an embedded system for cashless payment on a vending machine Bachelor’s Thesis Field of Studies: Mikro- und Medizintechnik Course: Embedded systems Author: Dominik Wenger Supervisors: Prof. Andreas Habegger, Prof. Dr. Christian Grothoff Expert: Rico Zoss Date: July 28, 2020 Berner Fachhochschule 0 Mikro- und Medizintechnik ABSTRACT Digital wallet payment services are expected to account for 47 % of all E-Commerce and 28 % of all point of sale payment methods by 2022 [1]. Unfortunately, some people have concerns about their privacy by using such digital wallet applications, since most of the providers are big tech companies with unclear intentions. A new participant in this global market will be GNU/Taler. It is a digital wallet service, that wants to provide a fast and easy payment system which ensures the user’s privacy. During this thesis, an embedded system shall be developed to allow the use of GNU/Taler for mobile payments in vending machines. The fundamental knowledge about vending machines has been gathered and a hardware specification book was written. After the elaboration of different concepts, it was decided to develop a vending machine interface gateway for a Raspberry Pi and as a further step an embedded platform, where the system shall become more tailored and thus more compact. The gateway board was designed, manufactured and tested. Up to a few design issues, the gateway fulfills the desired requirements. The further developed embedded platform is not manufactured yet. The schematics have been developed and the components are selected. An outstanding process is the final board design. -

Open Source Software Projects Needing Security Investments
INSTITUTE FOR DEFENSE ANALYSES & Open Source Software Projects Needing Security Investments David A. Wheeler, Project Leader Samir Khakimov 19 June 2015 Approved for public release; distribution is unlimited. IDA Document D-5459 v.1.0 Log: H 15-000253 Copy INSTITUTE FOR DEFENSE ANALYSES 4850 Mark Center Drive Alexandria, Virginia 22311-1882 About This Publication This work was conducted by the Institute for Defense Analyses (IDA) under contract N66001-11-C-0001, subcontract D6384-S5, Task GT-5-3329, “Homeland Open Security Technology (HOST),” for Georgia Tech Research Institute and under agreement with The Linux Foundation. The views, opinions, and findings should not be construed as representing the official position of either the Department of Defense or the sponsoring organization. Copyright Notice © 2015 Institute for Defense Analyses 4850 Mark Center Drive, Alexandria, Virginia 22311-1882 • (703) 845-2000. Acknowledgments Clyde G. Roby This material may be reproduced by or for the U.S. Government pursuant to the copyright license under the clause at DFARS 252.227-7013 (a)(16) [Jun 2013]. INSTITUTE FOR DEFENSE ANALYSES IDA Document D-5459, v. 1.0 Open Source Software Projects Needing Security Investments David A. Wheeler, Project Leader Samir Khakimov Executive Summary The Heartbleed vulnerability in the open source software (OSS) program OpenSSL was a serious vulnerability with widespread impact. It highlighted that some OSS programs are widely used and depended on and that vulnerabilities in them can have serious ramifications, and yet some OSS programs have not received the level of security analysis appropriate to their importance. Some OSS projects have many participants, perform in-depth security analyses, and produce software that is widely considered to be of high quality and to have strong security. -

Hacking Pokemon Go - 6 Wpa Security - 10
Kodibuntu • ODROID-C2 IoT • Hadoop and Spark on ODROID XU4 Year Three Issue #33 Sep 2016 ODROIDMagazine GottaGotta catchcatch ´em´em all!all! PokémonPokémon HowHow toto hackhack thethe hithit gamegame usingusing GPSGPS spoofingspoofing • Securing WPA • REDTOP, an networks from amazing project with dictionary an ODROID-C1 attacks and 3D-printed case What we stand for. We strive to symbolize the edge of technology, future, youth, humanity, and engineering. Our philosophy is based on Developers. And our efforts to keep close relationships with developers around the world. For that, you can always count on having the quality and sophistication that is the hallmark of our products. Simple, modern and distinctive. So you can have the best to accomplish everything you can dream of. We are now shipping the ODROID-U3 device to EU countries! Come and visit our online store to shop! Address: Max-Pollin-Straße 1 85104 Pförring Germany Telephone & Fax phone: +49 (0) 8403 / 920-920 email: [email protected] Our ODROID products can be found at http://bit.ly/1tXPXwe EDITORIAL okemon Go, the most popular mobile game in history, entertains over 20 million daily users. Part of the game Pinvolves hatching Pokemon eggs, which depends on how many kilometers are walked by the player. Although we recom- mend playing the game as intended, since getting exercise and being outside is part of the game, there is an interesting hack that can be done with an ODROID that allows eggs to be hatched by replay- ing a typical route on an ODROID and spoofing the GPS location to Pokemon Go. -

Open Source Software: a Survey from 10,000 Feet
Foundations and Trends® in sample Vol. xx, No xx (xxxx) 1–147 © xxxx xxxxxxxxx DOI: xxxxxx Open Source Software: A Survey from 10,000 Feet Stephanos Androutsellis-Theotokis1, Diomidis Spinellis2, Maria Kechagia3 and Georgios Gousios4 1 Patision 76, Athens, GR-104 34, Greece, [email protected] 2 Patision 76, Athens, GR-104 34, Greece, [email protected] 3 Patision 76, Athens, GR-104 34, Greece, [email protected] 4 Patision 76, Athens, GR-104 34, Greece, [email protected] Abstract Open source software (OSS), the origins of which can be traced back to the 1950s, is software distributed with a license that allows access to its source code, free redistribution, the creation of derived works, and unre- stricted use. OSS applications cover most areas of consumer and business soft- ware and their study touches many disciplines, including computer science, information systems, economics, psychology, and law. Behind a successful OSS project lies a community of actors, ranging from core developers to pas- sive users, held together by a flexible governance structure and membership, leadership and contribution policies that align their interests. The motivation behind individuals participating in OSS projects can be, among others, social, ideological, hedonistic, or signaling, while companies gain from their access to high-quality, innovative projects and an increase in their reputation and vis- ibility. Nowadays many business models rely on OSS as a product through the provision of associated services, or in coexistence with proprietary software, hardware, services, or licensing. The numerous OSS licenses mainly differ on how they treat derived software: some contain provisions that maintain its availability in open source form while others allow more flexibility. -
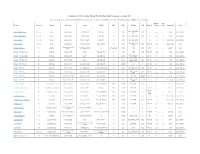
Comparison of 122 Open Spec, Hacker Friendly Single Board Computers -- January 2019
Comparison of 122 Open Spec, Hacker Friendly Single Board Computers -- January 2019 Click on the product names to get more product information. In most cases these links go to LinuxGizmos.com articles with detailed product descriptions plus market analysis. HDMI or USB Product Price ($) Vendor Processor Cores 3D GPU MCU RAM Storage LAN Wireless DP-out ports Expansion OSes Opt. 4GB eMMC; A20-OLinuXino-Lime2 51 or 63 Olimex Allwinner A20 2x A7 @ 1GHz Mali-400 no 1GB GbE no yes 3 other Linux, Android SATA A20-OLinuXino-Micro 63 or 74 Olimex Allwinner A20 2x A7 @ 1GHz Mali-400 no 1GB opt. 4GB NAND Fast no yes 3 other Linux, Android A33-OLinuXino 41 or 50 Olimex Allwinner A33 4x A7 @ 1.2GHz Mali-400 no 1GB opt. 4GB NAND no no no 1 dual 40-pin Linux, Android 4GB (opt. 16GB A64-OLinuXino 46 to 86 Olimex Allwinner A64 4x A53 @ 1.2GHz Mali-400 MP2 no 1GB GbE WiFi, BT yes 1 40-pin custom Linux eMMC) Qualcomm Atheros Arduino Yun Rev 2 59 Arduino 1x MIPS @ 400MHz no Atmega32U4 64MB 16MB Fast WiFi no 2 Arduino Linux AR9331 Banana Pi BPI-M2 Berry 36 SinoVoip Allwinner V40 4x A7 Mali-400 MP2 no 1GB SATA GbE WiFi, BT yes 4 Pi 40 Linux, Android 8GB eMMC (opt. Banana Pi BPI-M2 Magic 28 SinoVoip Allwinner A33 4x A7 Mali-400 MP2 no 512MB no Wifi, BT no 2 Pi 40 Linux, Android up to 64GB) 8GB to 64GB Banana Pi BPI-M2 Ultra 56 SinoVoip Allwinner R40 4x A7 Mali-400 MP2 no 2GB GbE WiFi, BT yes 4 Pi 40 Linux, Android eMMC; SATA Banana Pi BPI-M2 Zero 23 SinoVoip Allwinner H2+ 4x A7 @ 1.2GHz Mali-400 MP2 no 512MB no no WiFi, BT yes 1 Pi 40 Linux, Android Banana -

PIMOD: a Tool for Configuring Single-Board Computer Operating System Images
PIMOD: A Tool for Configuring Single-Board Computer Operating System Images Jonas Höchst∗y , Alvar Penning∗ , Patrick Lampe∗y , Bernd Freisleben∗y ∗ Department of Mathematics & Computer Science, University of Marburg, Germany {hoechst, penning, lampep, freisleb}@informatik.uni-marburg.de y Department of Computer Science / Electrical Engineering & Information Technology, TU Darmstadt, Germany {jonas.hoechst, patrick.lampe, bernd.freisleben}@maki.tu-darmstadt.de Abstract—Computer systems used in the field of humanitarian emergency response, environmental monitoring, Internet-of- technology are often based on general-purpose single-board Things (IoT), and smart city infrastructures. computers, such as Raspberry Pis. While these systems offer Single-board platforms that do rely on an operating system great flexibility for developers and users, configuration and deployment either introduces overhead by executing scripts on regularly use images provided by vendors or third parties. multiple devices or requires deeper technical understanding when Typically, an image is flashed to an SD card and then booted building operating system images for such small computers from in a system. Since there is no installation process, the OSes scratch. In this paper, we present PIMOD, a software tool for heavily depend on defaults, e.g., username, password, installed configuring operating system images for single-board computer software, or on scripts executed on the first boot, e.g., cryp- systems. We propose a simple yet comprehensive configuration language. In a configuration profile, called Pifile, a small set of tographic parameters or partition size adjustments. Software commands is used to describe the configuration of an operating can then be installed and configurations can be adapted in the system image.