Download the Transcript
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Signature Redacted Certified By: William Fjricchio Professor of Compa Ive Media Studies Thesis Supervisor Signature Redacted Accepted By
Manufacturing Dissent: Assessing the Methods and Impact of RT (Russia Today) by Matthew G. Graydon B.A. Film University of California, Berkeley, 2008 SUBMITTED TO THE DEPARTMENT OF COMPARATIVE MEDIA STUDIES IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF SCIENCE IN COMPARATIVE MEDIA STUDIES AT THE MASSACHUSETTS INSTITUTE OF TECHNOLOGY JUNE 2019 C2019 Matthew G. Graydon. All rights reserved. The author hereby grants to MIT permission to reproduce and to distribute publicly paper and electronic copies of this thesis document in whole or in part in any medium now known or hereafter created. S~ri' t A Signature red acted Department of Comparative 6/ledia Studies May 10, 2019 _____Signature redacted Certified by: William fJricchio Professor of Compa ive Media Studies Thesis Supervisor Signature redacted Accepted by: MASSACHUSETTS INSTITUTE Professor of Comparative Media Studies _OF TECHNOLOGY Director of Graduate Studies JUN 1 12019 LIBRARIES ARCHIVES I I Manufacturing Dissent: Assessing the Methods and Impact of RT (Russia Today) by Matthew G. Graydon Submitted to the Department of Comparative Media Studies on May 10, 2019 in Partial Fulfillment of the Requirements for the Degree of Master of Science in Comparative Media Studies ABSTRACT The state-sponsored news network RT (formerly Russia Today) was launched in 2005 as a platform for improving Russia's global image. Fourteen years later, RT has become a self- described tool for information warfare and is under increasing scrutiny from the United States government for allegedly fomenting unrest and undermining democracy. It has also grown far beyond its television roots, achieving a broad diffusion across a variety of digital platforms. -

Protecting Children in Virtual Worlds Without Undermining Their Economic, Educational, and Social Benefits
Protecting Children in Virtual Worlds Without Undermining Their Economic, Educational, and Social Benefits Robert Bloomfield* Benjamin Duranske** Abstract Advances in virtual world technology pose risks for the safety and welfare of children. Those advances also alter the interpretations of key terms in applicable laws. For example, in the Miller test for obscenity, virtual worlds constitute places, rather than "works," and may even constitute local communities from which standards are drawn. Additionally, technological advances promise to make virtual worlds places of such significant social benefit that regulators must take care to protect them, even as they protect children who engage with them. Table of Contents I. Introduction ................................................................................ 1177 II. Developing Features of Virtual Worlds ...................................... 1178 A. Realism in Physical and Visual Modeling. .......................... 1179 B. User-Generated Content ...................................................... 1180 C. Social Interaction ................................................................. 1180 D. Environmental Integration ................................................... 1181 E. Physical Integration ............................................................. 1182 F. Economic Integration ........................................................... 1183 * Johnson Graduate School of Management, Cornell University. This Article had its roots in Robert Bloomfield’s presentation at -

ASD-Covert-Foreign-Money.Pdf
overt C Foreign Covert Money Financial loopholes exploited by AUGUST 2020 authoritarians to fund political interference in democracies AUTHORS: Josh Rudolph and Thomas Morley © 2020 The Alliance for Securing Democracy Please direct inquiries to The Alliance for Securing Democracy at The German Marshall Fund of the United States 1700 18th Street, NW Washington, DC 20009 T 1 202 683 2650 E [email protected] This publication can be downloaded for free at https://securingdemocracy.gmfus.org/covert-foreign-money/. The views expressed in GMF publications and commentary are the views of the authors alone. Cover and map design: Kenny Nguyen Formatting design: Rachael Worthington Alliance for Securing Democracy The Alliance for Securing Democracy (ASD), a bipartisan initiative housed at the German Marshall Fund of the United States, develops comprehensive strategies to deter, defend against, and raise the costs on authoritarian efforts to undermine and interfere in democratic institutions. ASD brings together experts on disinformation, malign finance, emerging technologies, elections integrity, economic coercion, and cybersecurity, as well as regional experts, to collaborate across traditional stovepipes and develop cross-cutting frame- works. Authors Josh Rudolph Fellow for Malign Finance Thomas Morley Research Assistant Contents Executive Summary �������������������������������������������������������������������������������������������������������������������� 1 Introduction and Methodology �������������������������������������������������������������������������������������������������� -

A F L D U U R E E Fearful Symmetry: How to Achieve Coherence Among
ASPJ–Africa and Francophonie Fall Fall 2010 Volume I, No. 3 John Hursh John En marche vers la démocratie au Maroc ? Maroc au démocratie la vers marche En Africa: A Light at the End of the Tunnel? Dustin Dehéz Dustin Herman J. Cohen en Afrique subsaharienne : Saisir toute l’histoire toute Saisir : subsaharienne Afrique en Réforme du secteur de la sécurité et services de renseignements renseignements de services et sécurité la de secteur du Réforme Cracks in the Jihad Thomas Rid, PhD 2010 Rumu Sarkat, PhD PhD Sarkat, Rumu une même volonté pour tous les acteurs ? acteurs les tous pour volonté même une Peacekeeping by Regional Organisations Une symétrie de la peur : Comment peut-on atteindre peut-on Comment : peur la de symétrie Une Lt Gen Vijay Kumar Jetley, PVSM, UYSM, Retired Colonel (ER) Jiyul Kim, USA Kim, Jiyul (ER) Colonel Cultural Dimensions of Strategy and Policy Dimension culturelle de la stratégie et de la politique la de et stratégie la de culturelle Dimension Col Jiyul Kim, USA, Retired Général de corps d’armée indienne (2s) Vijay Kumar Jetley, PVSM, UYSM PVSM, Jetley, Kumar Vijay (2s) indienne d’armée corps de Général Fearful Symmetry: How to Achieve Coherence among Le maintien de la paix par des organisations régionales organisations des par paix la de maintien Le All the Players Rumu Sarkar, PhD Thomas Rid, PhD Rid, Thomas Fissures dans le Jihad le dans Fissures Intelligence Services in Sub-Saharan Africa: Making Security Sector Reform Work tomne 2010 Herman J. Cohen J. Herman Dustin Dehéz Afrique : le bout du tunnel est-il en vue ? vue en est-il tunnel du bout le : Afrique Moving toward Democracy in Morocco? John Hursh Volume 1, No. -

Drucksache 19/21771 19
Deutscher Bundestag Drucksache 19/21771 19. Wahlperiode 19.08.2020 Kleine Anfrage der Abgeordneten Thomas Hacker, Katja Suding, Dr. Jens Brandenburg (Rhein- Neckar), Dr. Marco Buschmann, Hartmut Ebbing, Dr. Marcus Faber, Otto Fricke, Reginald Hanke, Katrin Helling-Plahr, Markus Herbrand, Manuel Höferlin, Reinhard Houben, Ulla Ihnen, Gyde Jensen, Dr. Marcel Klinge, Pascal Kober, Konstantin Kuhle, Oliver Luksic, Dr. Jürgen Martens, Frank Müller-Rosentritt, Dr. h. c. Thomas Sattelberger, Dr. Wieland Schinnenburg, Dr. Hermann Otto Solms, Dr. Marie-Agnes Strack-Zimmermann, Linda Teuteberg, Gerald Ullrich und der Fraktion der FDP Staatlicher russischer Auslandsrundfunk und seine Rolle in der deutschen Medienlandschaft Die deutsche EU-Ratspräsidentschaft hat den Kampf gegen Cyberbedrohungen und Desinformationskampagnen zu einem zentralen Anliegen ihres Arbeitspro- grammes gemacht. „In einer Demokratie braucht es Wahrheit und Transpa- renz“, erklärte Bundeskanzlerin Dr. Angela Merkel dazu in ihrer Rede im Euro- päischen Parlament am 8. Juli 2020. „Das zeichnet Europa aus; und dafür wird sich Deutschland in seiner Ratspräsidentschaft stark machen.“ Im aktuellen Verfassungsschutzbericht 2019 (Stand: Juli 2020) stellt das Bun- desamt für Verfassungsschutz im Hinblick auf Aktivitäten der Russischen Fö- deration dabei fest: „Neben seinen Spionageinteressen ist Russland bestrebt, die politische und öffentliche Meinung in Deutschland im Sinne der russischen Politik zu beeinflussen. [...] Von besonderer Bedeutung sind in Deutschland an- gesiedelte, jedoch -

Accountability by Numbers: a New Global Transitional Justice Dataset (1946–2016)
Article Accountability by Numbers: A New Global Transitional Justice Dataset (1946–2016) Genevieve Bates, Ipek Cinar, and Monika Nalepa In an era of democratic backsliding, scholars and policymakers wonder if failure to reckon with former authoritarian elites and their collaborators plays a role. Yet without adequate data on the way former autocracies and countries emerging from conflict deal with human rights violators, it is hard to tell if new democracies are unstable because of their failure to reckon with their former authoritarian elites or despite it. We introduce a dataset of personnel transitional justice events that allows scholars to answer such questions, disaggregating these events temporally from the date of a country’s democratization. The time series nature of our data allows scholars to measure key characteristics of states’ dealing with their past and complements existing transitional justice datasets by focusing not only on post-conflict societies and not only on post-authoritarian societies, but on both. To showcase the possibilities our data affords scholars, we use it to develop three novel measures of personnel transitional justice: severity, urgency, and volatility. The granular structure of our data allows researchers to construct additional measures depending on their theoretical questions of interest. We illustrate the use of severity of transitional justice in a regression that also employs data from the Varieties of Democracy project. e live in an era of democratic backsliding: fragile have access to temporally organized data on how states deal W new democracies are at risk of reverting back to with outgoing autocrats, their collaborators, and perpe- dictatorship. To see examples of this, one need trators of human rights violations. -

A Plausibly Deniable Encryption Scheme for Personal Data Storage Andrew Brockmann Harvey Mudd College
Claremont Colleges Scholarship @ Claremont HMC Senior Theses HMC Student Scholarship 2015 A Plausibly Deniable Encryption Scheme for Personal Data Storage Andrew Brockmann Harvey Mudd College Recommended Citation Brockmann, Andrew, "A Plausibly Deniable Encryption Scheme for Personal Data Storage" (2015). HMC Senior Theses. 88. https://scholarship.claremont.edu/hmc_theses/88 This Open Access Senior Thesis is brought to you for free and open access by the HMC Student Scholarship at Scholarship @ Claremont. It has been accepted for inclusion in HMC Senior Theses by an authorized administrator of Scholarship @ Claremont. For more information, please contact [email protected]. A Plausibly Deniable Encryption Scheme for Personal Data Storage Andrew Brockmann Talithia D. Williams, Advisor Arthur T. Benjamin, Reader Department of Mathematics May, 2015 Copyright © 2015 Andrew Brockmann. The author grants Harvey Mudd College and the Claremont Colleges Library the nonexclusive right to make this work available for noncommercial, educational pur- poses, provided that this copyright statement appears on the reproduced materials and notice is given that the copying is by permission of the author. To disseminate otherwise or to republish requires written permission from the author. Abstract Even if an encryption algorithm is mathematically strong, humans in- evitably make for a weak link in most security protocols. A sufficiently threatening adversary will typically be able to force people to reveal their encrypted data. Methods of deniable encryption seek to mend this vulnerability by al- lowing for decryption to alternate data which is plausible but not sensitive. Existing schemes which allow for deniable encryption are best suited for use by parties who wish to communicate with one another. -

Historical Dictionary of Russian and Soviet Intelligence
Russia • Military / Security Historical Dictionaries of Intelligence and Counterintelligence, No. 5 PRINGLE At its peak, the KGB (Komitet Gosudarstvennoy Bezopasnosti) was the largest HISTORICAL secret police and espionage organization in the world. It became so influential DICTIONARY OF in Soviet politics that several of its directors moved on to become premiers of the Soviet Union. In fact, Russian president Vladimir V. Putin is a former head of the KGB. The GRU (Glavnoe Razvedvitelnoe Upravleniye) is the principal intelligence unit of the Russian armed forces, having been established in 1920 by Leon Trotsky during the Russian civil war. It was the first subordinate to the KGB, and although the KGB broke up with the dissolution of the Soviet Union in 1991, the GRU remains intact, cohesive, highly efficient, and with far greater resources than its civilian counterparts. & The KGB and GRU are just two of the many Russian and Soviet intelli- gence agencies covered in Historical Dictionary of Russian and Soviet Intelligence. Through a list of acronyms and abbreviations, a chronology, an introductory HISTORICAL DICTIONARY OF essay, a bibliography, and hundreds of cross-referenced dictionary entries, a clear picture of this subject is presented. Entries also cover Russian and Soviet leaders, leading intelligence and security officers, the Lenin and Stalin purges, the gulag, and noted espionage cases. INTELLIGENCE Robert W. Pringle is a former foreign service officer and intelligence analyst RUSSIAN with a lifelong interest in Russian security. He has served as a diplomat and intelligence professional in Africa, the former Soviet Union, and Eastern Europe. For orders and information please contact the publisher && SOVIET Scarecrow Press, Inc. -

HIAS Report Template
Roadmap to Recovery A Path Forward after the Remain in Mexico Program March 2021 TABLE OF CONTENTS Introduction ............................................................................................................ 1 The Stories of MPP .................................................................................................. 1 Our Work on the Border ......................................................................................... 2 Part One: Changes and Challenges at the Southern Border ................................. 4 Immigration Under the Trump Administration ...................................................... 5 How MPP Worked ................................................................................................... 9 Situation on the Ground ......................................................................................... 12 Nonrefoulement Interviews .................................................................................... 18 Effects on the Legal Cases ....................................................................................... 19 Lack of Access to Legal Counsel .............................................................................. 20 The Coronavirus Pandemic and Title 42 ................................................................. 20 Part Two: Recommendations ................................................................................ 22 Processing Asylum Seekers at Ports of Entry .......................................................... 23 Processing -
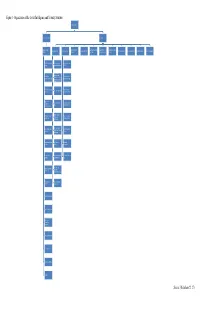
Organization of the Soviet Intelligence and Security Structure Source
Figure 1- Organization of the Soviet Intelligence and Security Structure General Chairman First Deputy Chairman Chief, GRU Deputy Chairman Space Intelligence Operational/ Technical Administrative/ Directorate for Foreign First Deputy Chief Chief of Information Personnel Directorate Political Department Financial Department Eighth Department Archives Department (KGB) Directorate Directorate Technical Directorate Relations First Chief Directorate First Directorate: Seventh Directorate: (Foreign) Europe and Morocco NATO Second Directorate: North and South Second Chief Eighth Directorate: America, Australia, Directorate (Internal) Individual Countries New Zealand, United Kingdom Fifth Chief Directorate Ninth Directorate: Third Directorate: Asia (Dissidents) Military Technology Eighth Chief Fourth Directorate: Tenth Directorate: Directorate Africa Military Economics (Communications) Fifth Directorate: Chief Border Troops Eleventh Directorate: Operational Directorates Doctrine, Weapons Intelligence Sixth Directorate: Third (Armed Forces) Twelfth Directorate: Radio, Radio-Technical Directorate Unknown Intelligence Seventh (Surveillance) First Direction: Institute of Directorate Moscow Information Ninth (Guards) Second Direction: East Information Command Directorate and West Berlin Post Third: National Technical Operations Liberation Directorate Movements, Terrorism Administration Fourth: Operations Directorate from Cuba Personnel Directorate Special Investigations Collation of Operational Experience State Communications Physical Security Registry and Archives Finance Source: (Richelson 22, 27) Figure 2- Organization of the United States Intelligence Community President National Security Advisor National Security DNI State DOD DOJ DHS DOE Treasury Commerce Council Nuclear CIO INR USDI FBI Intelligence Foreign $$ Flow Attachés Weapons Plans DIA NSA NGA NRO Military Services NSB Coast Guard Collection MSIC NGIC (Army) MRSIC (Air Analysis AFMic Force) NCTC J-2's ONI (Navy) CIA Main DIA INSCOM (Army) NCDC MIA (Marine) MIT Source: (Martin-McCormick) . -

Hacks, Leaks and Disruptions | Russian Cyber Strategies
CHAILLOT PAPER Nº 148 — October 2018 Hacks, leaks and disruptions Russian cyber strategies EDITED BY Nicu Popescu and Stanislav Secrieru WITH CONTRIBUTIONS FROM Siim Alatalu, Irina Borogan, Elena Chernenko, Sven Herpig, Oscar Jonsson, Xymena Kurowska, Jarno Limnell, Patryk Pawlak, Piret Pernik, Thomas Reinhold, Anatoly Reshetnikov, Andrei Soldatov and Jean-Baptiste Jeangène Vilmer Chaillot Papers HACKS, LEAKS AND DISRUPTIONS RUSSIAN CYBER STRATEGIES Edited by Nicu Popescu and Stanislav Secrieru CHAILLOT PAPERS October 2018 148 Disclaimer The views expressed in this Chaillot Paper are solely those of the authors and do not necessarily reflect the views of the Institute or of the European Union. European Union Institute for Security Studies Paris Director: Gustav Lindstrom © EU Institute for Security Studies, 2018. Reproduction is authorised, provided prior permission is sought from the Institute and the source is acknowledged, save where otherwise stated. Contents Executive summary 5 Introduction: Russia’s cyber prowess – where, how and what for? 9 Nicu Popescu and Stanislav Secrieru Russia’s cyber posture Russia’s approach to cyber: the best defence is a good offence 15 1 Andrei Soldatov and Irina Borogan Russia’s trolling complex at home and abroad 25 2 Xymena Kurowska and Anatoly Reshetnikov Spotting the bear: credible attribution and Russian 3 operations in cyberspace 33 Sven Herpig and Thomas Reinhold Russia’s cyber diplomacy 43 4 Elena Chernenko Case studies of Russian cyberattacks The early days of cyberattacks: 5 the cases of Estonia, -

Cultural Intelligence in Covert Operatives
OVERT ACCEPTANCE: CULTURAL INTELLIGENCE IN COVERT OPERATIVES CHIP MICHAEL BUCKLEY A Thesis Submitted to the Faculty of Mercyhurst University In Partial Fulfillment of the Requirements for The Degree of MASTER OF SCIENCE IN APPLIED INTELLIGENCE RIDGE SCHOOL FOR INTELLIGENCE STUDIES AND INFORMATION SCIENCE MERCYHURST UNIVERSITY ERIE, PENNSYLVANIA JANUARY 2015 RIDGE SCHOOL FOR INTELLIGENCE STUDIES AND INFORMATION SCIENCE MERCYHURST UNIVERSITY ERIE, PENNSYLVANIA OVERT ACCEPTANCE: CULTURAL INTELLIGENCE IN COVERT OPERATIVES A Thesis Submitted to the Faculty of Mercyhurst University In Partial Fulfillment of the Requirements for The Degree of MASTER OF SCIENCE IN APPLIED INTELLIGENCE Submitted By: CHIP MICHAEL BUCKLEY Certificate of Approval: ___________________________________ Stephen Zidek, M.A. Assistant Professor The Ridge School of Intelligence Studies and Information Science ___________________________________ James G. Breckenridge, Ph.D. Associate Professor The Ridge School of Intelligence Studies and Information Science ___________________________________ Phillip J. Belfiore, Ph.D. Vice President Office of Academic Affairs January 2015 Copyright © 2015 by Chip Michael Buckley All rights reserved. iii DEDICATION To my father. iv ACKNOWLEDGEMENTS I would like to acknowledge a number of important individuals who have provided an extraordinary amount of support throughout this process. The faculty at Mercyhurst University, particularly Professor Stephen Zidek, provided invaluable guidance when researching and developing this thesis. My friends and classmates also volunteered important ideas and guidance throughout this time. Lastly, my family’s support, patience, and persistent inquiries regarding my progress cannot be overlooked. v ABSTRACT OF THE THESIS Overt Acceptance: Cultural Intelligence in Covert Operatives A Critical Examination By Chip Michael Buckley Master of Science in Applied Intelligence Mercyhurst University, 2014 Professor S.