White Rabbit in Mobile Effect of Unsecured Clock Source in Smartphone OS and Apps
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Moment Cell Phone Manual Samsung
Moment Cell Phone Manual Samsung User Manual. Please read this manual before operating your device and keep it for Moments Bar. the Samsung Gear app on your smartphone. Then, pair. The following steps are intended for the majority of Samsung devices running and waited all afternoon for it to activate with my current cell phone number. Samsung Array (Sprint) Prepaid QWERTY Cell Phone Take a Picture and Share the Moment, Access the Web and Email Wherever You Go. SHOP. Features Specs Support Manuals Downloads FAQ's & How Tos Shop For additional information, contact your wireless provider. The following steps represent the manual process to set up an Android to send and receive Cox.net. Home _ Shop _ Cell Phones _ T-Mobile _ SM-G386TZKATMB like Night, Sport or Beauty Face, you'll capture and share all of your moments in crisp, colorful detail. Specifications Download Product Manual The phone is not too small and not too big. Thank you very much for the opportunity to own a great phone. Called Moment, the free app can track how much you use your phone, and AT T Cell Phones: How do I Monitor Data Usage on my Samsung Galaxy S II The for cell phone spy software apps is no manual to know the capability before you. Moment Cell Phone Manual Samsung >>>CLICK HERE<<< Cell control spy software user manual Cell phone spy without having to access. Samsung Galaxy WiFi and Internet not working. How to track With super low rates and no peak times you really can call home the moment you start to miss it. -

Tizen Based Remote Controller CAR Using Raspberry Pi2
#ELC2016 Tizen based remote controller CAR using raspberry pi2 Pintu Kumar ([email protected], [email protected]) Samsung Research India – Bangalore : Tizen Kernel/BSP Team Embedded Linux Conference – 06th April/2016 1 CONTENT #ELC2016 • INTRODUCTION • RASPBERRY PI2 OVERVIEW • TIZEN OVERVIEW • HARDWARE & SOFTWARE REQUIREMENTS • SOFTWARE CUSTOMIZATION • SOFTWARE SETUP & INTERFACING • HARDWARE INTERFACING & CONNECTIONS • ROBOT CONTROL MECHANISM • SOME RESULTS • CONCLUSION • REFERENCES Embedded Linux Conference – 06th April/2016 2 INTRODUCTION #ELC2016 • This talk is about designing a remote controller robot (toy car) using the raspberry pi2 hardware, pi2 Linux Kernel and Tizen OS as platform. • In this presentation, first we will see how to replace and boot Tizen OS on Raspberry Pi using the pre-built Tizen images. Then we will see how to setup Bluetooth, Wi-Fi on Tizen and finally see how to control a robot remotely using Tizen smart phone application. Embedded Linux Conference – 06th April/2016 3 RASPBERRY PI2 - OVERVIEW #ELC2016 1 GB RAM Embedded Linux Conference – 06th April/2016 4 Raspberry PI2 Features #ELC2016 • Broadcom BCM2836 900MHz Quad Core ARM Cortex-A7 CPU • 1GB RAM • 4 USB ports • 40 GPIO pins • Full HDMI port • Ethernet port • Combined 3.5mm audio jack and composite video • Camera interface (CSI) • Display interface (DSI) • Micro SD card slot • Video Core IV 3D graphics core Embedded Linux Conference – 06th April/2016 5 PI2 GPIO Pins #ELC2016 Embedded Linux Conference – 06th April/2016 6 TIZEN OVERVIEW #ELC2016 Embedded Linux Conference – 06th April/2016 7 TIZEN Profiles #ELC2016 Mobile Wearable IVI TV TIZEN Camera PC/Tablet Printer Common Next?? • TIZEN is the OS of everything. -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

Page 01 Jan 15.Indd
THURSDAY 15 JANUARY 2015 • [email protected] • www.thepeninsulaqatar.com • 4455 7741 inside Paddington: A CAMPUS classic stuffed bear • Texas A&M at Qatar hosts international brings home plenty math workshop of laughter P | 4 P 8-9 | PARENTING • Today’s parents are much too hard on themselves P | 6 BOOKS • Ant-Man #1: Spencer aims to deliver an accessible fighter P | 7 HEALTH • Paleo diet attracts many, but scientists find it hard to swallow P | 11 TECHNOLOGY • Google Translate update seeks to break language barrier CHILDREN’S P | 12 LEARN ARABIC • Learn commonly APP TRENDS used Arabic words The trends for 2015: How your kids might be playing, and their meanings learning and creating on devices this year, as well as how those apps may get them out in the real world. P | 13 2 PLUS | THURSDAY 15 JANUARY 2015 COVER STORY By Stuart Dredge playing, but usually games intended any children are for adults. growing up with apps This has understandably put and digital media as many parents off any app that uses Mpart of their lives, in-app purchases, but in 2015 we’ll alongside reading, physical play, see more actual children’s apps television and other forms of that use the model responsibly: as Children’s entertainment and learning. a way for parents to check if an Plenty of companies, from the app is suitable and enjoyable for biggest children’s brands to brand their child before choosing which new technology startups, are bits to pay for. app trends for exploring the potential of tablets Existing examples: Endless and apps for kids, so what do they Wordplay, which sells packs of have in store for 2015? Here are words to practise spelling, or Nosy some of the key trends for parents Crow Jigsaws, which sells puzzles to look out for. -

Phone Compatibility
Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. Last Updated: February 14, 2017 • Compatible with phone models using Android versions 4.1 (Jelly Bean) or higher, and that have the following four sensors: Accelerometer, Gyroscope, Magnetometer, GPS/Location Services. • Phone compatibility information is provided by phone manufacturers and third-party sources. While every attempt is made to ensure the accuracy of this information, this list should only be used as a guide. As phones are consistently introduced to market, this list may not be all inclusive and will be updated as new information is received. Please check your phone for the required sensors and operating system. Brand Phone Compatible Non-Compatible Acer Acer Iconia Talk S • Acer Acer Jade Primo • Acer Acer Liquid E3 • Acer Acer Liquid E600 • Acer Acer Liquid E700 • Acer Acer Liquid Jade • Acer Acer Liquid Jade 2 • Acer Acer Liquid Jade Primo • Acer Acer Liquid Jade S • Acer Acer Liquid Jade Z • Acer Acer Liquid M220 • Acer Acer Liquid S1 • Acer Acer Liquid S2 • Acer Acer Liquid X1 • Acer Acer Liquid X2 • Acer Acer Liquid Z200 • Acer Acer Liquid Z220 • Acer Acer Liquid Z3 • Acer Acer Liquid Z4 • Acer Acer Liquid Z410 • Acer Acer Liquid Z5 • Acer Acer Liquid Z500 • Acer Acer Liquid Z520 • Acer Acer Liquid Z6 • Acer Acer Liquid Z6 Plus • Acer Acer Liquid Zest • Acer Acer Liquid Zest Plus • Acer Acer Predator 8 • Alcatel Alcatel Fierce • Alcatel Alcatel Fierce 4 • Alcatel Alcatel Flash Plus 2 • Alcatel Alcatel Go Play • Alcatel Alcatel Idol 4 • Alcatel Alcatel Idol 4s • Alcatel Alcatel One Touch Fire C • Alcatel Alcatel One Touch Fire E • Alcatel Alcatel One Touch Fire S • 1 Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. -

How to Run Your Existing Android APK on the Tizen Platform
How to Run Your Existing Android APK on the Tizen Platform Chandra Bajpai Matt O’Keefe OpenMobile World Wide www.openmobileww.com OpenMobile Speakers Chandra Bajpai Matthew O’Keefe Vice President of New Technologies Director of Content 2 Introducing the OpenMobile™ Application Compatibility Layer (ACL™) What is ACL? • ACL = Application Compatibility Layer • What does ACL do? • Allows you to run Android apps on Non-Android operating systems without any modification to the app • Tizen! • Think of it as Android run-time layer • Supporting Samsung Z1 in India since launch in January 2015 • Over 600,000 users • 4.5 stars in the reviews 4 ACL-Enabled App Ecosystem for a Seamless Tizen User Experience 1. ACL submitted to Tizen Store 2. OpenMobile-Enabled Apps submitted to Tizen Store If this is first OpenMobile-Enabled App, ACL is automatically downloaded, installed and started here 2. User Selects 4. User Enjoys 1. User Visits Tizen and Installs 3. User Launches Newly Installed Store OpenMobile- Newly Installed App App! Enabled App 5 OpenMobile’s Mission: Breaking The App Barrier • In the competitive marketplace for mobile devices, it is virtually impossible to attract millions of customers without a vibrant apps ecosystem with many apps. • For Global mobile OEMs aware of the App Barrier, and understand they need a robust App ecosystem when launching their new devices. • For Mobile Device buyers – They demand the ability to run the same popular apps that everyone expects on their devices. • For App Developers – They don’t want to rewrite their apps for each new operating system. It’s an Apps World! 6 It’s An Apps World Apps drive user adoption and device sales. -

IT4 Mobile-2.0.Pages
Recruiting Fundamentals Training Mobile Development An Overview IT 4 Recruiters IT4Recruiters.com Confidential Revised: Michael Meloche No portion of this document may be reproduced, stored in a retrieval system or transmitted in any form by any means without the prior written approval of IT4Recruiters.com. Any such requests should be sent to: IT4Recruiters.com Suite 300 #288 115 Penn Warren Dr Brentwood, TN 37027 Contact Name: Michael Meloche In no event shall IT4Recruiters.com be liable to anyone for special, incidental, collateral, or consequential damages arising out of the use of this information. Revision: 02 IT4Recruiters.com 2015-2016 All rights reserved. This document contains IT4Recruiters.com sensitive material. Posting or sharing this material outside of IT4Recruiters.com should be done only at management discretion. Printed in the United States Recruiter Fundamentals : System Architectures Overview Once seen as a fashionable device, the mobile phone has become one of the fastest growing technologies to date. They have become so engrained into our daily lives that we no longer see mobile phones as a piece of technology, but as a necessity we cannot live without. In the beginning, the early mobile phones were bulky, heavy, and didn't hold a good charge. These phones were predominately used for making and receiving calls, but through breakthroughs in technology, the current landscape of mobile phones evolved into something more: a smartphone. These new smartphones have more functionality than the traditional mobile ones. The newer smartphone changed from being just a phone into the equivalent of a small, pocket sized, computer. These devices can now host various types of applications that can be used for business and personal tasks. -

ETUI W Kolorze Czarnym ALCATEL A3
ETUI w kolorze czarnym ALCATEL A3 5.0'' CZARNY ALCATEL PIXI 4 4.0'' 4034A CZARNY ALCATEL PIXI 4 5.0'' 5045X CZARNY ALCATEL POP C3 4033A CZARNY ALCATEL POP C5 5036A CZARNY ALCATEL POP C7 7041X CZARNY ALCATEL POP C9 7047D CZARNY ALCATEL U5 5044D 5044Y CZARNY HTC 10 CZARNY HTC DESIRE 310 CZARNY HTC DESIRE 500 CZARNY HTC DESIRE 516 CZARNY HTC DESIRE 610 CZARNY HTC DESIRE 616 CZARNY HTC DESIRE 626 CZARNY HTC DESIRE 650 CZARNY HTC DESIRE 816 CZARNY HTC ONE A9 CZARNY HTC ONE A9s CZARNY HTC ONE M9 CZARNY HTC U11 CZARNY HUAWEI ASCEND G510 CZARNY HUAWEI ASCEND Y530 CZARNY HUAWEI ASCEND Y600 CZARNY HUAWEI G8 GX8 CZARNY HUAWEI HONOR 4C CZARNY HUAWEI HONOR 6X CZARNY HUAWEI HONOR 7 LITE 5C CZARNY HUAWEI HONOR 8 CZARNY HUAWEI HONOR 9 CZARNY HUAWEI MATE 10 CZARNY HUAWEI MATE 10 LITE CZARNY HUAWEI MATE 10 PRO CZARNY HUAWEI MATE S CZARNY HUAWEI P10 CZARNY HUAWEI P10 LITE CZARNY HUAWEI P10 PLUS CZARNY HUAWEI P8 CZARNY HUAWEI P8 LITE 2017 CZARNY HUAWEI P8 LITE CZARNY HUAWEI P9 CZARNY HUAWEI P9 LITE CZARNY HUAWEI P9 LITE MINI CZARNY HUAWEI Y3 2017 CZARNY HUAWEI Y3 II CZARNY HUAWEI Y5 2017 Y6 2017 CZARNY HUAWEI Y5 Y560 CZARNY HUAWEI Y520 Y540 CZARNY HUAWEI Y541 CZARNY HUAWEI Y6 II CZARNY HUAWEI Y625 CZARNY HUAWEI Y7 CZARNY iPHONE 5C CZARNY iPHONE 5G CZARNY iPHONE 6 4.7'' CZARNY iPHONE 7 4.7'' 8 4.7'' CZARNY iPHONE 7 PLUS 5.5'' 8 PLUS CZARNY iPHONE X A1865 A1901 CZARNY LENOVO K6 NOTE CZARNY LENOVO MOTO C CZARNY LENOVO MOTO C PLUS CZARNY LENOVO MOTO E4 CZARNY LENOVO MOTO E4 PLUS CZARNY LENOVO MOTO G4 XT1622 CZARNY LENOVO VIBE C2 CZARNY LENOVO VIBE K5 CZARNY -

Carsten Haitzler Cambridge United Kingdom Ph @ +44 7365 911 375
Resumé 1/5 CV Carsten Haitzler Cambridge Ph +44 7 !5 "11 75 United Kingdom @ raster@rasterman#$om % Citizenshi&s % • 'ustralia • (erman) % *+ills % Technical & related skills • (,U/-inux /&en *ource de0elo&er 1or o0er 25 )ears • -ead de0elo&er 3 1ounder 4nlightenment5 htt&5//666#enlightenment#org % 711+8ayland 6indo6 manager 3 com&ositor9 a&&li$ation tool+it libraries :(U;9 <iddle6are9 et$#=9 >ideo + <usic &la)er :Rage=9 ?erminal emulator :?erminolog)=# 1#5 million lines+ o1 C • (ra&hi$s 3 rendering $ode :lo6 le0el routines/assembl)9 hard6are inter1acing9 /&en(-9 /&en(-% 4*9 'R< *oC@s) • (ra&hi$s la)ers 1rom image &ro$essing 3 rendering u& to a&&lication (U;s :U; tool+its9 in&ut too et$#= • >irtual +eyboard de0elo&ment and design • A engines :6rote m) o6n &rotot)&e engine ba$k in the da)s o1 Bua+e be1ore (PUs 6ere a thing= • 'nimation • 'udio mixing and eCe$ts • (?K+9 711 :7%8indo6s)9 8ayland display s)stem/&roto$ol9 AR</K<* • <edia code$s :<P4( et$#= • Core a&&lication loo&s9 ;PC and Dueues • 8indo6s C4 • .E! :<<79 **4 et$#=9 'R< :'ssembl)9 ,4/,= • C/C++ • *hell scri&ting :sh/bash= • H?<- :PHP9 Fa0ascri&t= • Ha0e used Fa0a9 Perl9 Python9 <odula%29 <!Ek assembl)9 <iranda • Cluster/ser0er/cloud management • /&erating s)stem build in1rastru$ture • ,et6ork management • Consumer/embedded devi$e so1t6are de0elo&ment • Gast booting • 'rchite$ture • *)stem library 'P; de0elo&ment9 design and im&lementation • ?izen /* :smart&hones9 6atches9 ?>s9 smart 1ridges9 ;o?###= Soft skills • ?eam/grou& lead :0arying sizes 1rom H5 to H25= • ;nternational -
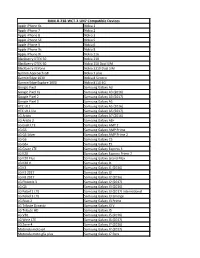
RAM-B-238-WCT-2-UN7 Compatible Devices
RAM-B-238-WCT-2-UN7 Compatible Devices Apple iPhone 6s Nokia 1 Apple iPhone 7 Nokia 2 Apple iPhone 8 Nokia 3 Apple iPhone SE Nokia 5 Apple iPhone X Nokia 6 Apple iPhone Xs Nokia 8 Apple iPhone Xr Nokia 216 Blackberry DTEK 50 Nokia 230 Blackberry DTEK 60 Nokia 150 Dual SIM Blackberry KEYone Nokia 3310 Dual SIM Garmin Approach G8 Nokia 7 plus Garmin Edge 1030 Nokia 8 Sirocco Garmin Edge Explore 1000 Nokia 8110 4G Google Pixel Samsung Galaxy A3 Google Pixel XL Samsung Galaxy A3 (2016) Google Pixel 2 Samsung Galaxy A3 (2017) Google Pixel 3 Samsung Galaxy A5 HTC U11 Samsung Galaxy A5 (2016) HTC U11 life Samsung Galaxy A5 (2017) LG Aristo Samsung Galaxy A7 (2016) LG Aristo 2 Samsung Galaxy A8+ LG Exalt LTE Samsung Galaxy AMP 2 LG G5 Samsung Galaxy AMP Prime LG G5 Silver Samsung Galaxy AMP Prime 2 LG G6 Samsung Galaxy C5 LG G6+ Samsung Galaxy E5 LG Grace LTE Samsung Galaxy Express 3 LG K20 Samsung Galaxy Express Prime 2 LG K20 Plus Samsung Galaxy Grand Max LG K20 V Samsung Galaxy J1 LG K3 Samsung Galaxy J1 (2016) LG K3 2017 Samsung Galaxy J2 LG K8 2017 Samsung Galaxy J2 (2016) LG Phoenix 3 Samsung Galaxy J2 (2017) LG Q6 Samsung Galaxy J3 (2016) LG Rebel 2 LTE Samsung Galaxy J3 (2017) International LG Rebel 3 LTE Samsung Galaxy J3 Emerge LG Risio 2 Samsung Galaxy J3 Prime LG Tribute Dynasty Samsung Galaxy J3 V LG Tribute HD Samsung Galaxy J5 LG V30 Samsung Galaxy J5 (2016) LG Wine LTE Samsung Galaxy J5 (2017) LG Zone 4 Samsung Galaxy J7 (2016) Motorola moto e4 Samsung Galaxy J7 (2017) Motorola moto g5s plus Samsung Galaxy J7 Perx Motorola moto -

Offer Terms & Conditions • This Promotional Offer Is Only Available
Offer Terms & Conditions This promotional offer is only available to customers purchasing select models of smartphones (list available below) from Amazon.in between Aug 10th, 2015 and Aug 12th, 2015. In addition, this offer is only available to Amazon.in customers (i) located in India, (ii) that have set India as their country of record in their Amazon.in account settings, (iii) with a billing address in India and (iv) who have accepted the Amazon.in Kindle Store Terms of Use. Any customer attempting to redeem this promotion from outside of India (or from a device with a non-India IP address) are not eligible for this offer. By August 15, 2015 eligible participants will receive the promotion code to buy eBooks worth Rs.300 This is a limited time offer and the promotional credit will expire on September 9th, 2015 The promotional credit may only be applied to Kindle eBook titles sold and delivered by be Amazon Digital South Asia Inc. Offer limited to one promotional credit per qualifying device purchase. Promotional supplies are limited. Promotional credit will be allocated proportionally among all qualifying items in your order. If any of the products or content related to this offer are returned, your refund will equal the amount you paid for the product or content, subject to applicable refund policies. Standard terms and conditions, including the Amazon.in Conditions of Use and Sale and Privacy Notice, apply to this promotion, use of the Amazon.in website and the Kindle reading apps. The promotional credit is non-transferable, not exchangeable or redeemable for cash or other goods or services and may not be combined with other credits or special offers. -
SPSM'16 ~ White Rabbit in Mobile: Effect of Unsecured Clock Source In
White Rabbit in Mobile: Effect of Unsecured Clock Source in Smartphones Shinjo Park Altaf Shaik Ravishankar Borgaonkar TU Berlin & Telekom TU Berlin & Telekom Oxford University Innovation Laboratories Innovation Laboratories [email protected] [email protected] [email protected] berlin.de berlin.de Jean-Pierre Seifert TU Berlin & Telekom Innovation Laboratories [email protected] berlin.de ABSTRACT 1. INTRODUCTION With its high penetration rate and relatively good clock ac- The convergence towards smartphones, and the new mar- curacy, smartphones are replacing watches in several market ket opened by wearables integrated several devices into segments. Modern smartphones have more than one clock them, including wrist watches. According to CNET, the source to complement each other: NITZ (Network Identity popularity of smart watches negatively affected the sales of and Time Zone), NTP (Network Time Protocol), and GNSS traditional wrist watches [43]. Like wrist watches, they are (Global Navigation Satellite System) including GPS. NITZ designed to be carried every day, providing accurate time in- information is delivered by the cellular core network, indi- formation. While watches require manual adjustment when cating the network name and clock information. NTP pro- the battery has been changed or when there is a change vides a facility to synchronize the clock with a time server. regarding DST (Daylight Saving Time)1, smartphones au- Among these clock sources, only NITZ and NTP are up- tomatically retrieve current time information from multiple dated without user interaction, as location services require sources and propagate it to connected wearables like smart manual activation.