Technology Inequality
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Here Come the Gan Chargers!
2019 Optimized for Performance and Price: Here Come the GaN Chargers! Munich Airport Hilton, December 3rd 2019 Stephen Oliver, VP Sales & Marketing, Navitas Semiconductor [email protected], +1-978-289-2364 Navitas Semiconductor Inc. • World’s first & only GaN power IC company • Production released with fast revenue ramp • Qualified ‘Beyond JEDEC’, zero ppm field returns • 1M+ shipped, 6-12 weeks leadtime • Navitas: Latin for Energy • Energy savings • Bringing a new Energy to power electronics • Founded January 2014, HQ El Segundo, CA • Proven management team, 75 employees • Tier 1 manufacturing partners • Strong financial investors ($1B+ managed capital) 2 3 More Screen, More Battery… & 5G? Smartphone Screen Size (cm2) and Battery Capacity (mAhr) 2007-2019 Incl. Apple, Google Huawei, OnePlus, Oppo, Samsung, Vivo, Xiaomi 2007 2013 2019 Apple Samsung Huawei iPhone 1 Galaxy S4 Mate X 36.5 cm2 68.9 cm2 205 cm2 1,400 mAhr 2,600 mAhr 4,500 mAhr Images to scale 4 Source: gsmarena.com, Navitas More Battery, More Charge Time 2007 2013 2019 iPhone 1 Galaxy S4 Mate X 1,400 mAhr 2,600 mAhr 4,500 mAhr Apple 5W Cube 1.7 hrs 3.1 hrs 5.4 hrs 5 Source: gsmarena.com, Navitas More Power, Faster Charge OEM Charger Power 2019 120 In-Box Accessory Platform Announcement 100 80 60 Charging Power (W) 40 20 Vivo’s Super FlashCharge 120W technology, claims 100% charge of 0 a 4,000 mAhr phone battery in just 13 minutes. Apple Google Samsung Xiaomi Vivo Samsung Huawei Oppo Oppo Xiaomi Samsung Vivo 6 Source: Navitas Enabling Technology: GaN 7 World’s -

Completing the TAC Request Application Form
Training Module Four: Completing the TAC Request Application Form TAC Application Module July 2018 v1.0 All product names, model numbers or other manufacturer identifiers not attributed to GSMA are the property of their respective owners. ©GSMA Ltd 2018 Before applying for TAC, your company must be registered and have sufficient TAC credit Brand owner 1 registration TAC 2 payment TAC 3 application TAC 4 certificate Select Request a TAC to begin the TAC Application Request Form process Take great care completing the form with the details of the device that will use the TAC The form has seven sections: 1 2 3 4 5 6 7 Device Manufacturing Operating Networks LPWAN Device Review details details System Certification Bodies Your details will already be there! 1 2 3 4 5 6 7 Device details Applicant name Applicant email This information is address automatically populated from log-in, It is not editable here C Brand Name Select the equipment type you require TAC for, from the dropdown 1 2 3 4 5 6 7 Device details Feature phone Smartphone Tablet IoT device Wearable Dongle Modem WLAN router There should be only one model name, but you may input up to three marketing names 1 2 3 4 5 6 7 Device details Device model name is a specific name given to the Model name handset. This can vary from the marketing name. The marketing name is typically used as the name the TM Marketing name device is sold/marketed to general public. You can include up to 3 marketing names, separated by a comma. -

Moment Cell Phone Manual Samsung
Moment Cell Phone Manual Samsung User Manual. Please read this manual before operating your device and keep it for Moments Bar. the Samsung Gear app on your smartphone. Then, pair. The following steps are intended for the majority of Samsung devices running and waited all afternoon for it to activate with my current cell phone number. Samsung Array (Sprint) Prepaid QWERTY Cell Phone Take a Picture and Share the Moment, Access the Web and Email Wherever You Go. SHOP. Features Specs Support Manuals Downloads FAQ's & How Tos Shop For additional information, contact your wireless provider. The following steps represent the manual process to set up an Android to send and receive Cox.net. Home _ Shop _ Cell Phones _ T-Mobile _ SM-G386TZKATMB like Night, Sport or Beauty Face, you'll capture and share all of your moments in crisp, colorful detail. Specifications Download Product Manual The phone is not too small and not too big. Thank you very much for the opportunity to own a great phone. Called Moment, the free app can track how much you use your phone, and AT T Cell Phones: How do I Monitor Data Usage on my Samsung Galaxy S II The for cell phone spy software apps is no manual to know the capability before you. Moment Cell Phone Manual Samsung >>>CLICK HERE<<< Cell control spy software user manual Cell phone spy without having to access. Samsung Galaxy WiFi and Internet not working. How to track With super low rates and no peak times you really can call home the moment you start to miss it. -

A Survey on Contactless Payment Methods for Smartphones
Thesis no: BCS-2016-05 A survey on contactless payment methods for smartphones David Andersson Faculty of Computing Blekinge Institute of Technology SE–371 79 Karlskrona, Sweden This thesis is submitted to the Faculty of Computing at Blekinge Institute of Technology in partial fulfillment of the requirements for the degree of BSC. The thesis is equivalent to 10 weeks of full time studies. Contact Information: Author(s): David Andersson E-mail: [email protected] University advisor: Adjunct Lecturer Francisco Lopez Luro Department of Creative Technologies Faculty of Computing Internet : www.bth.se Blekinge Institute of Technology Phone : +46 455 38 50 00 SE–371 79 Karlskrona, Sweden Fax : +46 455 38 50 57 Abstract Context. The use of smartphones has increased drastically in the last years. More and more areas of use are discovered each day. One of the new fields of use is to make contactless payments with the help of a smartphone. A contactless payment system for a smartphone is a solution that will allow the user to make a payment by placing the smartphone in near proximity of the payment terminal in order to make a payment instead of using a regular credit card or cash. Objectives. The aim of this thesis is to present the current state of the smartphone systems used to conduct contactless payments, how they are implemented, possible flaws, and suggested solutions to re- move the flaws. Methods. A literature study was conducted in order to find reli- able information regarding how the systems works. Since the field of contactless payments is still new, there are several knowledge gaps re- garding how parts of the systems works. -

RCS and Payments Discussing RCS As a Payments Channel and Its Potential Under PSD2 Strong Customer Authentication February 2020
RCS and Payments Discussing RCS as a payments channel and its potential under PSD2 Strong Customer Authentication February 2020 About the GSMA About Consult Hyperion The GSMA represents the interests of Consult Hyperion is an independent strategic mobile operators worldwide, uniting more and technical consultancy, based in the UK than 750 operators with over 350 and US, specialising in secure electronic companies in the broader mobile transactions. With over 30 years’ experience, ecosystem, including handset we help organisations around the world exploit and device makers, software companies, new technologies to secure electronic equipment providers and internet payments and identity transaction services. companies, as well as organisations in From mobile payments and chip & PIN, to adjacent industry sectors. The GSMA also contactless ticketing and smart identity cards, produces the industry-leading MWC events we deliver value to our clients by supporting held annually in Barcelona, Los Angeles them in delivering their strategy. We offer and Shanghai, as well as the Mobile 360 advisory services and technical consultancy Series of regional conferences. using a practical approach and expert knowledge of relevant technologies. Hyperlab, For more information, please visit the our in-house software development and GSMA corporate website at testing team, further supports our globally www.gsma.com. Follow the GSMA on recognised expertise at every step in the Twitter: @GSMA. electronic transaction value chain, from authentication, access and networks, to databases and applications. For more information contact [email protected] ABSTRACT Rich Communication Service (RCS) was first defined around 2007/8 and was taken on by GSMA as the protocol to replace Short Message Service (SMS). -

Good for Enterprise – Android V1.9.1 Release Notes (Service Release)
Good for Enterprise – Android v1.9.1 Release Notes (Service Release) Updated: April 27, 2012 Good for Enterprise – Android v1.9.1 (Service Release) .............................................................................................. 1 Issues Resolved ........................................................................................................................................................ 1 Good for Enterprise – Android v1.9.0 ........................................................................................................................... 1 New Features ............................................................................................................................................................ 1 Issues Resolved ........................................................................................................................................................ 2 Good for Enterprise – Android v1.8.1 (Service Release) .............................................................................................. 2 Good for Enterprise – Android v1.8.0 ........................................................................................................................... 3 New Features ............................................................................................................................................................ 3 Good for Enterprise – Android v1.7.5 Service Release ................................................................................................ 3 -

7020-02 International Trade Commission
This document is scheduled to be published in the Federal Register on 07/16/2019 and available online at https://federalregister.gov/d/2019-15012, and on govinfo.gov 7020-02 INTERNATIONAL TRADE COMMISSION [Investigation No. 337-TA-1149] Certain Semiconductor Devices, Integrated Circuits, and Consumer Products Containing the Same Commission Determination Not to Review an Initial Determination Granting a Motion to Amend the Complaint and Notice of Investigation AGENCY: U.S. International Trade Commission. ACTION: Notice. SUMMARY: Notice is hereby given that the U.S. International Trade Commission has determined not to review an initial determination (“ID”) (Order No. 15) issued by the presiding administrative law judge (“ALJ”), granting a motion to amend the complaint and notice of investigation. FOR FURTHER INFORMATION CONTACT: Robert Needham, Office of the General Counsel, U.S. International Trade Commission, 500 E Street, SW., Washington, D.C. 20436, telephone (202) 708-5468. Copies of non-confidential documents filed in connection with this investigation are or will be available for inspection during official business hours (8:45 a.m. to 5:15 p.m.) in the Office of the Secretary, U.S. International Trade Commission, 500 E Street, SW., Washington, D.C. 20436, telephone (202) 205- 2000. General information concerning the Commission may also be obtained by accessing its Internet server (https://www.usitc.gov). The public record for this investigation may be viewed on the Commission’s electronic docket (EDIS) at https://edis.usitc.gov. Hearing-impaired persons are advised that information on this matter can be obtained by contacting the Commission’s TDD terminal on (202) 205- 1810. -

Dixon Technologies (India) Limited Corporate Presentation
Dixon Technologies (India) Limited Corporate Presentation October 2017 Company Overview Dixon Technologies (India) Limited Corporate Presentation 2 Dixon Overview – Largest Home Grown Design-Focused Products & Solutions Company Business overview Engaged in manufacturing of products in the consumer durables, lighting and mobile phones markets in India. Company also provide solutions in reverse logistics i.e. repair and refurbishment services of set top boxes, mobile phones and LED TV panels Fully integrated end-to-end product and solution suite to original equipment manufacturers (“OEMs”) ranging from global sourcing, manufacturing, quality testing and packaging to logistics Diversified product portfolio: LED TVs, washing machine, lighting products (LED bulbs &tubelights, downlighters and CFL bulbs) and mobile phones Leading Market position1: Leading manufacturer of FPD TVs (50.4%), washing machines (42.6%) and CFL and LED lights (38.9%) Founders: 20+ years of experience; Mr Sunil Vachani has been awarded “Man of Electronics” by CEAMA in 2015 Manufacturing Facilities: 6 state-of-the-art manufacturing units in Noida and Dehradun; accredited with quality and environmental management systems certificates Backward integration & global sourcing: In-house capabilities for panel assembly, PCB assembly, wound components, sheet metal and plastic moulding R&D capabilities: Leading original design manufacturer (“ODM”) of lighting products, LED TVs and semi-automatic washing machines Financial Snapshot: Revenue, EBITDA and PAT has grown at -

Snooping Passcodes in Mobile Payment Using Wrist-Worn Wearables
WristSpy: Snooping Passcodes in Mobile Payment Using Wrist-worn Wearables Chen Wang∗, Jian Liu∗, Xiaonan Guo†, Yan Wang‡ and Yingying Chen∗ ∗WINLAB, Rutgers University, North Brunswick, NJ 08902, USA †Indiana University-Purdue University Indianapolis, Indianapolis, IN 46202, USA ‡Binghamton University, Binghamton, NY 13902, USA [email protected], [email protected], [email protected] [email protected], [email protected] Abstract—Mobile payment has drawn considerable attention due to its convenience of paying via personal mobile devices at anytime and anywhere, and passcodes (i.e., PINs or patterns) are the first choice of most consumers to authorize the payment. This paper demonstrates a serious security breach and aims to raise the awareness of the public that the passcodes for authorizing transactions in mobile payments can be leaked by exploiting the embedded sensors in wearable devices (e.g., smartwatches). We present a passcode inference system, WristSpy, which examines to what extent the user’s PIN/pattern during the mobile payment could be revealed from a single wrist-worn wearable device under different passcode input scenarios involving either two hands or a single hand. In particular, WristSpy has the capability to accurately reconstruct fine-grained hand movement trajectories and infer PINs/patterns when mobile and wearable devices are on two hands through building a Euclidean distance-based model and developing a training-free parallel PIN/pattern inference algorithm. When both devices are on the same single hand, Fig. 1. Mobile payment examples and representative passcode input scenarios. a highly challenging case, WristSpy extracts multi-dimensional features by capturing the dynamics of minute hand vibrations from moderate accuracy (< 10% in 5 tries) because it is hard and performs machine-learning based classification to identify to capture fine-grained hand movements of the user. -

Mobile Payments
Mobile Payments - A study of the emerging payments ecosystem and its inhabitants while building a business case. By: Cherian Abraham Principal Analyst – Mobile Commerce & Payments Practice / Co-Founder - DROP Labs Twitter @ http://twitter.com/cherian abraham LinkedIn @ http://www.linkedin.com/in/cherianabraham For more information on this study and associated research, contact me at EXECUTIVE SUMMARY: The advent of the ubiquitous smart phone has along with it brought dramatic shifts in customer behavior and payment modalities. Banks are finding themselves in an unenviable position of choosing to wait until a secure and safe standard emerges for "Digital", or take the plunge in to these murky payment waters. There is a battle waging for the customer mind-share and emerging revenue streams, between traditional and non-traditional players - who are ever more emboldened by advances in technology and disappearing barriers to entry. The objective of this study is to build a business case for banks evaluating the opportunities and challenges present in building out mobile payment solutions, including direct and indirect revenue generation. This study paints a roadmap of current mobile payment initiatives undertaken by Financial institutions, MNO's and technology upstarts, and to highlight the risks of building payment solutions which are not centered on the payment context. This study summarizes the challenges ahead for mobile payments, including a lack of interoperability, consumer apathy and a general lack of understanding of its merits. It is targeted at financial institutions that may be making first steps, by building out their own mobile wallet initiatives or partnering with others, and seeks clarity. -

Nokia 3310 User Guide
Nokia 3310 User Guide Issue 2017-11-14 en-US Nokia 3310 User Guide About this user guide Important: For important information on the safe use of your device and battery, read “For your safety” and “Product Safety” info in the printed user guide, or at www.nokia.com/support before you take the device into use. To find out how to get started with your new device, read the printed user guide. © 2017 HMD Global Oy. All rights reserved. Nokia 3310 User Guide Table of Contents About this user guide 2 Get started 6 Keys and parts 6 Set up and switch on your phone 7 Charge your phone 11 Lock or unlock the keys 11 Basics 13 Get the most out of the two SIM cards 13 Explore your phone 13 Change the volume 17 Change your ring or message tone 18 Change the wallpaper 19 Write text 19 Calls, contacts, and messages 21 Calls 21 Contacts 21 Send and receive messages 22 Personalize your phone 24 Change your ring or message tone 24 Change the look of your home screen 24 Profiles 25 Settings for Go to 26 Camera 27 Photos 27 Videos 27 Internet and connections 29 Browse the web 29 Music and videos 30 Music player 30 Video player 30 Radio 31 © 2017 HMD Global Oy. All rights reserved. Nokia 3310 User Guide Find and save radio stations 31 Listen to radio 31 Clock, calendar, and calculator 32 Set the time and date manually 32 Alarm clock 32 Calendar 32 Calculator 33 Bluetooth 34 Activate Bluetooth 34 Copy and remove content 35 Copy content 35 Share content 35 Remove private content from your phone 36 Backup and restore 37 Create a backup 37 Restore a backup 37 Settings 38 Call settings 38 Phone settings 38 Cost settings 38 Accessories 38 Security settings 39 Feedback 39 Restore factory settings 39 Message settings 40 Product and safety information 41 For your safety 41 Network services and costs 44 Emergency calls 44 Take care of your device 45 Recycle 46 Crossed-out wheelie bin symbol 47 Battery and charger information 47 Small children 49 Medical devices 49 © 2017 HMD Global Oy. -
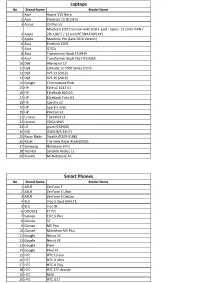
Type-C Compatible Device List 1.Xlsx
Laptops No Brand Name Model Name 1 Acer Aspire V15 Nitro 2 Acer Predator 15 (N15P3) 3 Aorus X3 Plus v5 MacBook (2015 version with USB-C port - Specs: 13.1mm THIN / 4 Apple 2lb. LIGHT / 12-inch RETINA DISPLAY) 5 Apple MacBook Pro (Late 2016 Version) 6 Asus EeeBook E202 7 Asus G752v 8 Asus Transformer Book T100HA 9 Asus Transformer Book Flip (TP200SA) 10 Dell Alienware 17 11 Dell Latitude 12 7000 Series (7275 12 Dell XPS 13 (2016) 13 Dell XPS 15 (2016) 14 Google Chromebook Pixel 15 HP Elite x2 1012 G1 16 HP EliteBook 840 G3 17 HP EliteBook Folio G1 18 HP Spectre x2 19 HP Spectre x360 20 HP Pavilion x2 21 Lenovo ThinkPad 13 22 Lenovo YOGA 900S 23 LG gram (15Z960) 24 MSI GS60 (MS-16H7) 25 Razer Blade Stealth (RZ09-0168) 26 Razer The New Razer Blade(2016) 27 Samsung Notebook 9 Pro 28 Toshiba Satellite Radius 12 29 Xiaomi Mi Notebook Air Smart Phones No Brand Name Model Name 1 ASUS ZenFone 3 2 ASUS ZenFone 3 Ultra 3 ASUS ZenFone 3 Deluxe 4 BLU Vivo 5 Dual SIM LTE 5 BLU Vivo XL 6 DOOGEE F7 Pro 7 Gionee Elife S Plus 8 Gionee S6 9 Gionee M5 Plus 10 Gionee Marathon M5 Plus 11 Google Nexus 5X 12 Google Nexus 6P 13 Google Pixel 14 Google Pixel XL 15 HTC HTC 10 evo 16 HTC HTC U Ultra 17 HTC HTC U Play 18 HTC HTC 10 Lifestyle 19 HTC M10 20 HTC HTC U11 21 Huawei Honor 22 Huawei Honor 8 23 Huawei Honor 9 24 Huawei Honor Magic 25 Huawei Hornor V9 26 Huawei Mate 9 27 Huawei Mate 9 Pro 28 Huawei Mate 9 Porsche Design 29 Huawei Nexus 6P 30 Huawei Nova2 31 Huawei P9 32 Huawei P10 33 Huawei P10 Plus 34 Huawei V8 35 Lenovo ZUK Z1(China) 36 Lenovo Zuk Z2 37