ESTONIAN INFORMATION TECHNOLOGY COLLEGE Indrek
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Firefox 1.1 for Nokia N900 Reviewer's Guide
Firefox 1.1 for Nokia N900 Reviewer’s Guide Firefox 1.1 for Nokia N900 Reviewer’s Guide Table of Contents What’s new in Firefox 1.1 for the Nokia N900 1 1. About Mozilla 2 2. Firefox for Mobile 2 3. Mozilla’s Mobile Vision 3 4. Getting Started 4 5. New & Improved 6 6. Do More With Your Web 7 7. Firefox Mobile and Desktop Browsing 9 8. A Summary of Firefox Features 11 9. Under the Hood 12 Firefox 1.1 for Nokia N900 Reviewer’s Guide What’s new in Firefox 1.1 for the Nokia N900 Highlights: tFirefox lets you browse in landscape and portrait mode tVolume rocker lets you zoom in and out tPersonalized Start page helps you pick up where you left off tAdd-ons auto-update and you can view the full add-on gallery tFill out forms more easily with autocomplete improvements tSmart Tapping lets you tap on links, widgets and other Web content with accuracy tContext Menu lets you Open in New Tab and Save Image by long tapping and holding a link tSave to PDF in the Site Menu lets you capture important content, like a receipt or boarding pass, to view offline or access quickly tForget Password in the Site Menu tells a website you no longer trust to forget your private data tAdd Search Engine in the Site Menu lets you quickly add a new search engine to your Awesome Screen tAnd many more Firefox features on page 11 Page 1 Firefox for Nokia N900 Reviewer’s Guide Firefox 1.1 for Nokia N900 Reviewer’s Guide 1. -

Ten Steps to Smartphone Security
Ten Steps to Smartphone Security Smartphones continue to grow in popularity and are now as powerful and functional as many computers. It is important to protect your smartphone just like you protect your computer as mobile cybersecurity threats are growing. These mobile security tips can help you reduce the risk of exposure to mobile security threats: 1. Set PINs and passwords. To prevent unauthorized access to your phone, set a password or Personal Identification Number (PIN) on your phone’s home screen as a first line of defense in case your phone is lost or stolen. When possible, use a different password for each of your important log-ins (email, banking, personal sites, etc.). You should configure your phone to automatically lock after five minutes or less when your phone is idle, as well as use the SIM password capability available on most smartphones. 2. Do not modify your smartphone’s security settings. Do not alter security settings for convenience. Tampering with your phone’s factory settings, jailbreaking, or rooting your phone undermines the built-in security features offered by your wireless service and smartphone, while making it more susceptible to an attack. 3. Backup and secure your data. You should backup all of the data stored on your phone – such as your contacts, documents, and photos. These files can be stored on your computer, on a removal storage card, or in the cloud. This will allow you to conveniently restore the information to your phone should it be lost, stolen, or otherwise erased. 4. Only install apps from trusted sources. -

The Technology That Brings Together All Things Mobile
NFC – The Technology That Brings Together All Things Mobile Philippe Benitez Wednesday, June 4th, 2014 NFC enables fast, secure, mobile contactless services… Card Emulation Mode Reader Mode P2P Mode … for both payment and non-payment services Hospitality – Hotel room keys Mass Transit – passes and limited use tickets Education – Student badge Airlines – Frequent flyer card and boarding passes Enterprise & Government– Employee badge Automotive – car sharing / car rental / fleet management Residential - Access Payment – secure mobile payments Events – Access to stadiums and large venues Loyalty and rewards – enhanced consumer experience 3 h h 1996 2001 2003 2005 2007 2014 2014 2007 2005 2003 2001 1996 previous experiences experiences previous We are benefiting from from benefiting are We Barriers to adoption are disappearing ! NFC Handsets have become mainstream ! Terminalization is being driven by ecosystem upgrades ! TSM Provisioning infrastructure has been deployed Barriers to adoption are disappearing ! NFC Handsets have become mainstream ! Terminalization is being driven by ecosystem upgrades ! TSM Provisioning infrastructure has been deployed 256 handset models now in market worldwide Gionee Elife E7 LG G Pro 2 Nokia Lumia 1020 Samsung Galaxy Note Sony Xperia P Acer E320 Liquid Express Google Nexus 10 LG G2 Nokia Lumia 1520 Samsung Galaxy Note 3 Sony Xperia S Acer Liquid Glow Google Nexus 5 LG Mach Nokia Lumia 2520 Samsung Galaxy Note II Sony Xperia Sola Adlink IMX-2000 Google Nexus 7 (2013) LG Optimus 3D Max Nokia Lumia 610 NFC Samsung -

Sophos Mobile Security
Sophos Mobile Security Protect your Android devices against malware and other threats The market dominance of Android devices and the inherent openness of Android led to the proliferation of malware and Potentially Unwanted Applications (PUA). SophosLabs detected over a million new pieces of malware in 2014 alone, and the growth rate is accelerating. Malware can lead to data loss, reputation loss, additional costs, and reduced performance. Highlights Protection and performance The Sophos Mobile Security antivirus app protects your Android devices without compromising Ì Privacy Advisor warns performance or battery life. The app uses up-to-the-minute intelligence from SophosLabs and the Sophos of potential privacy core antivirus engine. This means your apps are automatically scanned for malware as you install them. breaches Sophos Mobile Security’s consistent performance has earned recognition from independent testing agencies including AV-Test. Ì Security Advisor gives tips to improve device Malware protection security Our Sophos Mobile Security antivirus app protects your Android devices with proactive identification of malware. Your apps are automatically scanned for malware as you install them. Sophos includes protection Ì Loss and Theft for PUAs and low-reputation apps—new apps that have no known history and may pose a threat. PUAs Protection include adware, rootkits, diallers, and any association the app may have to previous malicious behaviour such as a certificate that has been compromised. Ì App Protection with additional passwords for Web protection sensitive apps Surf securely on the internet from your Android device. Sophos Mobile Security checks all websites against a Ì Spam Filter SophosLabs database for known malicious sites and prevents users from accessing them. -
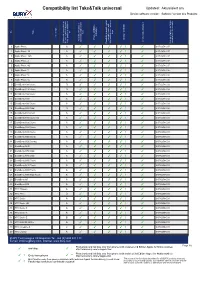
BURY Compatibility List Generator
Compatibility list Take&Talk universal Updated: Aktualisiert am: Device software version: Software Version des Produkts: on No key keys Type activation Set of tips Phone s REDIAL Charger available / private mode with Activation Bluetooth Article code (Charger) connection with device Bluetooth connection to used to test/ Comments after ignition is switched the last connected phone Bluetooth device / phones Possibility to switch car kit Version of phone software 1 Apple iPhone A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 2 Apple iPhone 3G A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 3 Apple iPhone 3GS A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 4 Apple iPhone 4 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 5 Apple iPhone 4S A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.07 6 Apple iPhone 5 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 7 Apple iPhone 5c A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 8 Apple iPhone 5s A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.08 9 BlackBerry 8300 Curve D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 10 BlackBerry 8310 Curve D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 11 BlackBerry 8520 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 12 BlackBerry 8800 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 13 BlackBerry 8900 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 14 BlackBerry 9000 Bold D ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.02 15 BlackBerry 9105 Pearl A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 16 BlackBerry 9300 Curve 3G A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 17 BlackBerry 9320 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 18 BlackBerry 9360 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 19 BlackBerry 9380 Curve A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 20 BlackBerry 9500 Storm A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 21 BlackBerry 9520 Storm2 A ✓ ✓ ✓ ✓ 1 ✓ 0-07-0258-0.01 22 BlackBerry 9630 A ✓ ✓ -

Total Defense Mobile Security
USER'S GUIDE Total Defense Mobile Security Total Defense Mobile Security User's Guide Publication date 2015.04.09 Copyright© 2015 Total Defense Mobile Security Legal Notice All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without written permission from an authorized representative of Total Defense. The inclusion of brief quotations in reviews may be possible only with the mention of the quoted source. The content can not be modified in any way. Warning and Disclaimer. This product and its documentation are protected by copyright. The information in this document is provided on an “as is” basis, without warranty. Although every precaution has been taken in the preparation of this document, the authors will not have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the information contained in this work. This book contains links to third-party Websites that are not under the control of Total Defense, therefore Total Defense is not responsible for the content of any linked site. If you access a third-party website listed in this document, you will do so at your own risk. Total Defense provides these links only as a convenience, and the inclusion of the link does not imply that Total Defense endorses or accepts any responsibility for the content of the third-party site. Trademarks. Trademark names may appear in this book. -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Android 4.4 home screen Company / developer Google Open Handset Alliance Android Open Source Project (AOSP) Programmed in C (core), C++, Java (UI) OS family Unix-like Working state Current Source model Open source with proprietary components Initial release September 23, 2008 Latest stable release 4.4.2 KitKat / December 9, 2013 Marketing target Smartphones Tablet computers Available language(s) Multi-lingual (46 languages) Package manager Google Play, APK Supported platforms 32-bit ARM, MIPS, x86 Kernel type Monolithic (modified Linux kernel) [1] [2] [3] Userland Bionic libc, shell from NetBSD, native core utilities with a few from NetBSD Default user interface Graphical (Multi-touch) License Apache License 2.0 Linux kernel patches under GNU GPL v2 [4] Official website www.android.com Android is an operating system based on the Linux kernel, and designed primarily for touchscreen mobile devices such as smartphones and tablet computers. Initially developed by Android, Inc., which Google backed financially Android (operating system) 2 and later bought in 2005, Android was unveiled in 2007 along with the founding of the Open Handset Alliance: a consortium of hardware, software, and telecommunication companies devoted to advancing open standards for mobile devices. The first publicly available smartphone running Android, the HTC Dream, was released on October 22, 2008. The user interface of Android is based on direct manipulation, using touch inputs that loosely correspond to real-world actions, like swiping, tapping, pinching and reverse pinching to manipulate on-screen objects. Internal hardware such as accelerometers, gyroscopes and proximity sensors are used by some applications to respond to additional user actions, for example adjusting the screen from portrait to landscape depending on how the device is oriented. -

Mobile Security Companion to the CIS Critical Security Controls (Version 6)
Mobile Security Companion to the CIS Critical Security Controls (Version 6) 1 Mobile Security Companion to the CIS Critical Security Controls (Version 6) Introduction ................................................................................................................................................................................................................................................................. 3 Description ................................................................................................................................................................................................................................................................... 5 CIS Critical Security Controls (Version 6): Mobile Security .................................................................................................................................................................... 5 2 Introduction Mobile devices are starting to replace laptops for regular business use. Organizations are building or porting their applications to mobile platforms, so users are increasingly accessing the same data with mobile as with their laptops. Also, organizations have increasingly implemented Bring Your Own Device (BYOD) policies to manage this trend. However, many organizations have been struggling with the increase of personal mobile devices, and don’t fully understand the security risks they may bring. There are concerns that their compact size makes them easy to lose, that they run newer operating systems that don’t -

Vitaly Repin T+358 504876392 Vitaly Repin
Espoo, Finland [email protected] vitaly repin T+358 504876392 Vitaly Repin Experience 05.2012 { 04.2013. CBTec Oy. Helsinki, Finland. Chief software architect • Nokia N9 project. Details per request. • CTO functions for the startup company (eLearning). Details per request. 2008 { 2012. Nokia Oyj, Maemo and MeeGo devices. Helsinki, Finland. Software architect, Technical Product Owner • E-Mail and MfE (Exchange ActiveSync) subsystems for Nokia N9. Qt-based MeeGo/Harmattan E-Mail client. Fully responsible for the software architecture and project execution. • E-Mail subsystem for Nokia N900. Architecture routines and project management. Open source e-mail client modest. • MailForExchange subsystem for Nokia N900. Bringing MfE sup- port on board in 4 months with 0 crashes in sales release. Defining the ar- chitecture, leading the team. Cooperation with multiple geographically- spreaded teams. After sales release in addition to my engineering re- sponsibilities I was communicating with customers through maemo.org (public channel) and Nokia Care (private channel). • QMF (Qt Messaging Framework) Bringing on board in Nokia Linux- based platform "Harmattan" MeeGo. Deployment (storage part) in Nokia N900 device (first Linux phone made by Nokia). • Processes: Architecture review process, established code review pro- cess for email team, hiring interviews with the candidates for technical positions. • Technical contribution: participating in Harmattan MeeGo architec- ture board (influencing the Harmattan MeeGo architecture, leading crash meetings (core dump analysis), taking the lead in analysis of the most complex issues with the email and MfE subsystem at the development stage (performance, battery life, hangs, non-reproducible crashes etc), defining architecture for the email subsystem in general and email client in particular, defining architecture for ActiveSync solution. -

Nokia Phones: from a Total Success to a Total Fiasco
Portland State University PDXScholar Engineering and Technology Management Faculty Publications and Presentations Engineering and Technology Management 10-8-2018 Nokia Phones: From a Total Success to a Total Fiasco Ahmed Alibage Portland State University Charles Weber Portland State University, [email protected] Follow this and additional works at: https://pdxscholar.library.pdx.edu/etm_fac Part of the Engineering Commons Let us know how access to this document benefits ou.y Citation Details A. Alibage and C. Weber, "Nokia Phones: From a Total Success to a Total Fiasco: A Study on Why Nokia Eventually Failed to Connect People, and an Analysis of What the New Home of Nokia Phones Must Do to Succeed," 2018 Portland International Conference on Management of Engineering and Technology (PICMET), Honolulu, HI, 2018, pp. 1-15. This Article is brought to you for free and open access. It has been accepted for inclusion in Engineering and Technology Management Faculty Publications and Presentations by an authorized administrator of PDXScholar. Please contact us if we can make this document more accessible: [email protected]. 2018 Proceedings of PICMET '18: Technology Management for Interconnected World Nokia Phones: From a Total Success to a Total Fiasco A Study on Why Nokia Eventually Failed to Connect People, and an Analysis of What the New Home of Nokia Phones Must Do to Succeed Ahmed Alibage, Charles Weber Dept. of Engineering and Technology Management, Portland State University, Portland, Oregon, USA Abstract—This research intensively reviews and analyzes the management made various strategic changes to take the strategic management of technology at Nokia Corporation. Using company back into its leading position, or at least into a traditional narrative literature review and secondary sources, we position that compensates or reduces the losses incurred since reviewed and analyzed the historical transformation of Nokia’s then. -

Securing and Managing Wearables in the Enterprise
White Paper: Securing and Managing Wearables in the Enterprise Streamline deployment and protect smartwatch data with Samsung Knox Configure White Paper: Securing and Managing Wearables in the Enterprise 2 Introduction: Smartwatches in the Enterprise As the wearable device market heats up, wrist-worn devices Industries as varied as healthcare, such as smartwatches are leading the pack. According to CCS Insight, forecasts for global sales of smart wearable devices finance, energy, transportation, will grow strongly over the next five years, with the global public safety, retail and hospitality market reaching nearly $30 billion by 2023.1 are deploying smartwatches for While smartwatches for fitness and activity tracking are popular, consumer demand is only part of the equation. added business value. Enterprises are also seeing business value in wearable devices. In a report by Robert Half Technology, 81 percent of CIOs surveyed expect wearable devices like smartwatches to Samsung has been working to address these concerns and become common tools in the workplace.2 has developed the tools to make its Galaxy and Galaxy Active smartwatches customizable, easily manageable and highly secure for enterprise users. This white paper will look at how these tools address key wearable security and manageability challenges, as well as considerations for smartwatch 81% deployments. of CIOs surveyed expect wearable devices like smartwatches to become common tools in the workplace. Industries as varied as healthcare, finance, energy, transportation, public safety, retail and hospitality are deploying smartwatches for added business value, such as hands-free communication for maintenance workers, task management, as well as physical monitoring of field workers in dangerous or remote locations. -

Nokia N900 User Guide
Nokia N900 User Guide Issue 4 2Contents Contents About your device 19 About the desktop 20 Application menu 21 Safety 6 Status area and status menu 21 About your device 6 Dashboard 23 Network services 7 About the touch screen 24 Shared memory 7 Text input 25 Protect your device 29 Find help 8 Explore Ovi 29 Read the user guide 8 Support 8 Personalise your device 30 Settings 8 Edit and personalise the desktop 30 Access codes 8 Profile settings 31 Prolong battery life 9 Change the background image 31 View information about your device 9 Change the device language 31 Visit maemo.nokia.com 9 Change themes 32 Get started 10 Connect your device 32 Set up your device 10 About connectivity 32 Keys and parts 14 Network settings 32 First start-up 15 Use a WLAN connection 33 Kickstand 16 Use a packet data connection 37 Stylus 16 Active data connections 38 Use accessories 17 Disable wireless connections 38 Internet connection settings 38 Introduction 18 Bluetooth connectivity 39 Key features 18 USB connections 41 About Maemo software 18 © 2010 Nokia. All rights reserved. Contents 3 Browse the web 42 Options during a call 58 About browser 42 Call timers 58 Open and browse web pages 42 Emergency calls 58 Browser toolbar 43 Organise bookmarks 44 Send text and instant messages 59 Clear private data 44 About Conversations 59 Connection security 45 Send text messages 60 Download files 45 Send instant messages 61 Save web pages 46 Delete messages and conversations 63 View browsing history 46 Filter conversations 63 Install a plug-in or an add-on 46 Text