How to Take Advantage of Macos Big Sur Security Benefits
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
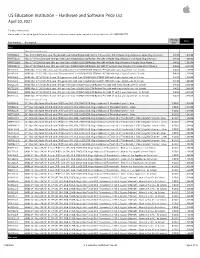
Apple US Education Price List
US Education Institution – Hardware and Software Price List April 30, 2021 For More Information: Please refer to the online Apple Store for Education Institutions: www.apple.com/education/pricelists or call 1-800-800-2775. Pricing Price Part Number Description Date iMac iMac with Intel processor MHK03LL/A iMac 21.5"/2.3GHz dual-core 7th-gen Intel Core i5/8GB/256GB SSD/Intel Iris Plus Graphics 640 w/Apple Magic Keyboard, Apple Magic Mouse 2 8/4/20 1,049.00 MXWT2LL/A iMac 27" 5K/3.1GHz 6-core 10th-gen Intel Core i5/8GB/256GB SSD/Radeon Pro 5300 w/Apple Magic Keyboard and Apple Magic Mouse 2 8/4/20 1,699.00 MXWU2LL/A iMac 27" 5K/3.3GHz 6-core 10th-gen Intel Core i5/8GB/512GB SSD/Radeon Pro 5300 w/Apple Magic Keyboard & Apple Magic Mouse 2 8/4/20 1,899.00 MXWV2LL/A iMac 27" 5K/3.8GHz 8-core 10th-gen Intel Core i7/8GB/512GB SSD/Radeon Pro 5500 XT w/Apple Magic Keyboard & Apple Magic Mouse 2 8/4/20 2,099.00 BR332LL/A BNDL iMac 21.5"/2.3GHz dual-core 7th-generation Core i5/8GB/256GB SSD/Intel IPG 640 with 3-year AppleCare+ for Schools 8/4/20 1,168.00 BR342LL/A BNDL iMac 21.5"/2.3GHz dual-core 7th-generation Core i5/8GB/256GB SSD/Intel IPG 640 with 4-year AppleCare+ for Schools 8/4/20 1,218.00 BR2P2LL/A BNDL iMac 27" 5K/3.1GHz 6-core 10th-generation Intel Core i5/8GB/256GB SSD/RP 5300 with 3-year AppleCare+ for Schools 8/4/20 1,818.00 BR2S2LL/A BNDL iMac 27" 5K/3.1GHz 6-core 10th-generation Intel Core i5/8GB/256GB SSD/RP 5300 with 4-year AppleCare+ for Schools 8/4/20 1,868.00 BR2Q2LL/A BNDL iMac 27" 5K/3.3GHz 6-core 10th-gen Intel Core i5/8GB/512GB -

Holiday Catalog
Brilliant for what’s next. With the power to achieve anything. AirPods Pro AppleCare+ Protection Plan†* $29 Key Features • Active Noise Cancellation for immersive sound • Transparency mode for hearing and connecting with the world around you • Three sizes of soft, tapered silicone tips for a customizable fit • Sweat and water resistant1 • Adaptive EQ automatically tunes music to the shape of your ear • Easy setup for all your Apple devices2 • Quick access to Siri by saying “Hey Siri”3 • The Wireless Charging Case delivers more than 24 hours of battery life4 AirPods Pro. Magic amplified. Noise nullified. Active Noise Cancellation for immersive sound. Transparency mode for hearing what’s happening around you. Sweat and water resistant.1 And a more customizable fit for all-day comfort. AirPods® AirPods AirPods Pro with Charging Case with Wireless Charging Case with Wireless Charging Case $159 $199 $249 1 AirPods Pro are sweat and water resistant for non-water sports and exercise and are IPX4 rated. Sweat and water resistance are not permanent conditions. The charging case is not sweat or water resistant. 2 Requires an iCloud account and macOS 10.14.4, iOS 12.2, iPadOS, watchOS 5.2, or tvOS 13.2 or later. 3Siri may not be available in all languages or in all areas, and features may vary by area. 4 Battery life varies by use and configuration. See apple.com/batteries for details. Our business is part of a select group of independent Apple® Resellers and Service Providers who have a strong commitment to Apple’s Mac® and iOS platforms and have met or exceeded Apple’s highest training and sales certifications. -

Vmware Fusion 12 Vmware Fusion Pro 12 Using Vmware Fusion
Using VMware Fusion 8 SEP 2020 VMware Fusion 12 VMware Fusion Pro 12 Using VMware Fusion You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents Using VMware Fusion 9 1 Getting Started with Fusion 10 About VMware Fusion 10 About VMware Fusion Pro 11 System Requirements for Fusion 11 Install Fusion 12 Start Fusion 13 How-To Videos 13 Take Advantage of Fusion Online Resources 13 2 Understanding Fusion 15 Virtual Machines and What Fusion Can Do 15 What Is a Virtual Machine? 15 Fusion Capabilities 16 Supported Guest Operating Systems 16 Virtual Hardware Specifications 16 Navigating and Taking Action by Using the Fusion Interface 21 VMware Fusion Toolbar 21 Use the Fusion Toolbar to Access the Virtual-Machine Path 21 Default File Location of a Virtual Machine 22 Change the File Location of a Virtual Machine 22 Perform Actions on Your Virtual Machines from the Virtual Machine Library Window 23 Using the Home Pane to Create a Virtual Machine or Obtain One from Another Source 24 Using the Fusion Applications Menus 25 Using Different Views in the Fusion Interface 29 Resize the Virtual Machine Display to Fit 35 Using Multiple Displays 35 3 Configuring Fusion 37 Setting Fusion Preferences 37 Set General Preferences 37 Select a Keyboard and Mouse Profile 38 Set Key Mappings on the Keyboard and Mouse Preferences Pane 39 Set Mouse Shortcuts on the Keyboard and Mouse Preference Pane 40 Enable or Disable Mac Host Shortcuts on the Keyboard and Mouse Preference Pane 40 Enable Fusion Shortcuts on the Keyboard and Mouse Preference Pane 41 Set Fusion Display Resolution Preferences 41 VMware, Inc. -

Apple Accessories & Prices Input Devices Apple Magic Mouse 2 (APPX333) £65.50 Imac, Mac Mini and Accessories Magic Mouse 2 - Space Grey (APPX015) £82.50
Apple Accessories & Prices Input Devices Apple Magic Mouse 2 (APPX333) £65.50 iMac, Mac Mini and Accessories Magic Mouse 2 - Space Grey (APPX015) £82.50 Magic Trackpad 2 (APPX335) £107.50 Magic Trackpad 2 - Space Grey (APPX016) £124.00 Magic Keyboard (APPK005) £79.95 Magic Keyboard - Numeric (APPK006) £105.00 Magic Keyboard - Numeric - Space Grey (APPK007) £124.00 Adapters and Network Mini DisplayPort to DVI Adapter (APPX117) £23.95 Mini DisplayPort to VGA Adapter (APPX142) £23.95 USB-C to USB-A (APPX281) £14.95 USB-C to Digital AV (APPX099) £62.50 Misc. Accessories USB Retina Superdrive (APPX228) £65.50 HomePod Mini Smart Speakers - Available in Space Grey and Silver (APPX137/138) £82.50 HomePod Smart Speakers - Available in Space Grey and Silver (APPX013/014) £232.50 Many other adapters and accessories also available! Guernsey33 Commercial Arcade, Computers St. Peter Port Tel 01481-728738 Ltd E. & O. E. 18th August 2021 Mac Products & Specifications Mac Products & Specifications Mac Mini - i5 2.6GHz (APPC022) £915.00 iMac 27” i5 3.1GHz - 5K Retina Display (APPC028) £1499.00 3.0GHz 6-Core i5 Processor w/ 9MB shared L3 cache - Turbo Boost 3.1GHz 6-Core i5 Processor (Turbo Boost up to 4.5GHz), 8GB up to 4.1GHz, 8GB DDR4 RAM, 256GB Solid State Drive, Intel UHD DDR4 RAM, 256GB Solid State Drive, Radeon Pro 5300 Graphics Graphics 630, 802.11ac Wi-Fi (802.11 a/b/g/n compatible) & Bluetooth 5.0 (4GB), 802.11ac Wi-Fi (802.11 a/b/g/n compatible) & Bluetooth 5.0 Mac Mini - M1 8-Core Processor (APPC031) £582.00 iMac 27” i5 3.3GHz - 5K Retina Display -

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

Get Apple TV+ Free When You Buy a New Iphone, Ipad, Ipod Touch, Apple TV, Or Mac
Get Apple TV+ free when you buy a new iPhone, iPad, iPod touch, Apple TV, or Mac. Terms and conditions • Offer is available for a limited time only. • Eligible devices activated July 1, 2021 or later will qualify for offers of 3 months free Apple TV+, while those activated on June 30, 2021 or earlier will qualify for offers of 1 year free Apple TV+. • Offer cannot be combined with Apple One. • Only one offer per Family, regardless of number of devices purchased. You can share your Apple TV+ subscription with up to 5 other family members via Family Sharing. • The 3 months free Apple TV+ offer is not available if you or your Family have previously accepted the Apple TV+ one year free offer. • Make sure your device is running the latest iOS, iPadOS, tvOS, or macOS. • Offer must be claimed in the Apple TV app within 3 months after first setting up your new device. To see the offer appear, you will need to sign in with your Apple ID on your new device. • Upon claiming the offer, you agree to a SAR 19.99/month subscription that starts immediately after the free offer period and automatically renews until cancelled. You can cancel at any time in Settings at least one day before each renewal date. If you cancel during your free offer period, you and your family members will immediately lose access to Apple TV+ and the remainder of your free trial. You can’t reactivate this trial. Eligible devices • Any new iPhone, iPad, iPod touch, Apple TV, or Mac capable of running the latest iOS, iPadOS, tvOS, or macOS, from Apple or an Apple authorized reseller. -

Compatibility
Apple at Work Compatibility Compatible with your existing systems. Apple devices work with most enterprise systems and apps that your company already uses—mail and messaging, network connectivity, file sharing, collaboration and more—giving your employees access to everything they need to do their jobs. Connect to your infrastructure iPhone, iPad and Mac support WPA2 Enterprise to provide secure access to your enterprise Wi-Fi network. With the integration of iOS, iPadOS, macOS and the latest technology from Cisco, businesses everywhere can seamlessly connect to networks, optimize the performance of business-critical apps, and collaborate using voice and video—all with the security that businesses need. Secure access to private corporate networks is available in iOS, iPadOS and macOS using established industry-standard virtual private network protocols. Out of the box, iOS, iPadOS and macOS support IKEv2, Cisco IPSec and L2TP over IPSec, as well as on-demand VPN and per-app VPN. Work with your existing enterprise systems Apple devices work with key corporate services including Microsoft Exchange, giving your employees full access to their business email, calendar and contacts, across all their Apple devices. Employees can use the built-in Apple apps like Mail, Calendar, Contacts, Reminders and Notes to collaborate and optionally use apps like Microsoft Outlook for working with Microsoft Exchange. iPhone, iPad and Mac devices support a wide range of connectivity options including standards-based systems like IMAP and CalDAV. Popular productivity and collaboration tools like Microsoft Office, Google G Suite, Slack, Cisco Webex and Zoom deliver the functionality you know and expect. Access all your documents and files The Files app in iOS and iPadOS lets you access your Box, DropBox, OneDrive and Google Drive files all from one place. -

IBM Security Maas360 with Watson Consolidated Device Use Cases
IBM Security MaaS360 with Watson A deep dive into how MaaS360 supports any device and any operating system Introduction Apple iOS, macOS, & iPadOS Google Android & Chrome OS Microsoft Windows Ruggedized & IoT Request a demo The basics This is your primer on IBM Security MaaS360 with Watson, IBM’s industry-leading unified endpoint management (UEM) solution. Before we dive in, let’s make clear that, of course, any enrolled device can be locked to the passcode screen, pinged for its last known location, wiped remotely, have a passcode configured, have WiFi networks and VPN profiles distributed, and all of the other basic functions expected from bare bones mobile device management (MDM). But in this era of instant connectivity, an increasingly mobile workforce, and the expansion of non-traditional wearable, ruggedized, and virtualized endpoints, we wanted to make sure you get a little bit more out of the content you download. That said, if you’re still curious what else IBM Security MaaS360 can do once you’ve finished thumbing through here, take it for a spin with a free trial or connect with an IBMer for a demo. IBM Security MaaS360 with Watson 2 Introduction Apple iOS, macOS, & iPadOS Google Android & Chrome OS Microsoft Windows Ruggedized & IoT Request a demo Contents Apple iOS, macOS, & iPadOS Google Android & Chrome OS Microsoft Windows Ruggedized & IoT Apple Business Manager (ABM) Android Enterprise enrollment OOBE, Bulk Enrollment, Windows 10 Autopilot Device compliance & security and Over-the-Air (OTA) enrollment Apple device policy -

Staying Connected
Staying Connected Why you need to stay connected Feeling connected is essential for our physical and mental wellness. Physical distancing during COVID-19 limits all of our social engagements - dinners at Grandma's, nights out with friends, and catching a local concert or sporting event. This new normal also greatly reduces our simple day-to-day interactions like holding a door open for a stranger or small talk with a shop owner. While it is more difficult to remain feeling connected to our extended family and friends during this time, it is possible. To make up for these social interactions, it's important to reach out using technology to Social Connection Ideas connect with our family and friends more frequently. Here are some ideas for you to connect virtually with your loved ones using the apps: How to stay connected Celebrate holidays, birthdays, and other special moments virtually in a video call There are many ways to connect with your Recruit a loved one to help support your social circle while you stay safely at home. child with their online learning program Apps like FaceTime, WhatsApp, Facebook Host a virtual event for friends - teach Messenger, and Zoom allow you to group them how to make your favourite recipe, video chat with your family and friends. play live music, or share a story Schedule regular family suppers via group Messenger Kids is another free app that video chat to enjoy meals together allows your children to connect with friends Host an online talent show, dance party, and family (while parents maintain full or karaoke singalong control of their children's contact list). -

In-Datacenter Performance Analysis of a Tensor Processing Unit
In-Datacenter Performance Analysis of a Tensor Processing Unit Presented by Josh Fried Background: Machine Learning Neural Networks: ● Multi Layer Perceptrons ● Recurrent Neural Networks (mostly LSTMs) ● Convolutional Neural Networks Synapse - each edge, has a weight Neuron - each node, sums weights and uses non-linear activation function over sum Propagating inputs through a layer of the NN is a matrix multiplication followed by an activation Background: Machine Learning Two phases: ● Training (offline) ○ relaxed deadlines ○ large batches to amortize costs of loading weights from DRAM ○ well suited to GPUs ○ Usually uses floating points ● Inference (online) ○ strict deadlines: 7-10ms at Google for some workloads ■ limited possibility for batching because of deadlines ○ Facebook uses CPUs for inference (last class) ○ Can use lower precision integers (faster/smaller/more efficient) ML Workloads @ Google 90% of ML workload time at Google spent on MLPs and LSTMs, despite broader focus on CNNs RankBrain (search) Inception (image classification), Google Translate AlphaGo (and others) Background: Hardware Trends End of Moore’s Law & Dennard Scaling ● Moore - transistor density is doubling every two years ● Dennard - power stays proportional to chip area as transistors shrink Machine Learning causing a huge growth in demand for compute ● 2006: Excess CPU capacity in datacenters is enough ● 2013: Projected 3 minutes per-day per-user of speech recognition ○ will require doubling datacenter compute capacity! Google’s Answer: Custom ASIC Goal: Build a chip that improves cost-performance for NN inference What are the main costs? Capital Costs Operational Costs (power bill!) TPU (V1) Design Goals Short design-deployment cycle: ~15 months! Plugs in to PCIe slot on existing servers Accelerates matrix multiplication operations Uses 8-bit integer operations instead of floating point How does the TPU work? CISC instructions, issued by host. -

Troubleshooting Rosetta Stone Log-In Issues on Mobile
Portal > Knowledgebase > Teaching Learning and Research > Rosetta Stone > Troubleshooting Rosetta Stone Log-in Issues on Mobile Troubleshooting Rosetta Stone Log-in Issues on Mobile Kyle A. Oliveira - 2019-05-31 - 0 Comments - in Rosetta Stone A recent update to the Rosetta Stone apps on both iOS and Android may cause authentication issues. Please refer to the information below for resolving these issues. iOS To prevent any further issues regarding logging into the app on iOS, you must avoid opening the app unless you've authenticated through Brown's log in portal. Opening the app outside of logging in through Brown, will most likely result in the inability to log in and use the app. If you are having issues logging into it: Solution 1 1. Open your device's web browser, visit rosettastone.brown.edu, and log in 2. Click the “Launch Rosetta Stone Language Lessons” link to launch the app 3. You will experience the same problem as in the past - you will just see a "splash" screen instead of being logged in. On this screen, click Enterprise And Education Learners. 4. On the login screen that appears, type three random values (just a single letter will work) into the Username, Password, and Namespace fields. 5. You will see an error message. Click Try again and proceed with the next step. 6. Return to your web browser and again, visit rosettastone.brown.edu. 7. Click the “Launch Rosetta Stone Language Lessons” link to launch the app again. 8. Wait for the login to proceed - it should work. If you still see the error message, click the Try Again option. -

Pooch Manual In
What’s New As of August 21, 2011, Pooch is updated to version 1.8.3 for use with OS X 10.7 “Lion”: Pooch users can renew their subscriptions today! Please see http://daugerresearch.com/pooch for more! On November 17, 2009, Pooch was updated to version 1.8: • Linux: Pooch can now cluster nodes running 64-bit Linux, combined with Mac • 64-bit: Major internal revisions for 64-bit, particularly updated data types and structures, for Mac OS X 10.6 "Snow Leopard" and 64-bit Linux • Sockets: Major revisions to internal networking to adapt to BSD Sockets, as recommended by Apple moving forward and required for Linux • POSIX Paths: Major revisions to internal file specification format in favor of POSIX paths, recommended by Apple moving forward and required for Linux • mDNS: Adapted usage of Bonjour service discovery to use Apple's Open Source mDNS library • Pooch Binary directory: Added Pooch binary directory support, making possible launching jobs using a remotely-compiled executable • Minor updates and fixes needed for Mac OS X 10.6 "Snow Leopard" Current Pooch users can renew their subscriptions today! Please see http://daugerresearch.com/pooch for more! On April 16, 2008, Pooch was updated to version 1.7.6: • Mac OS X 10.5 “Leopard” spurs updates in a variety of Pooch technologies: • Network Scan window • Preferences window • Keychain access • Launching via, detection of, and commands to the Terminal • Behind the Login window behavior • Other user interface and infrastructure adjustments • Open MPI support: • Complete MPI support using libraries