Security Rules and Procedures 30 July 2015 Summary of Changes, 30 July 2015
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Transition Management Explained
Transition Management Explained INVESTED. TOGETHER.™ Contents 1. Introduction page 3 2. What is transition management? page 4 The transition manager 3. Is using a transition manager right for you? page 5 What are the potential benefits of working with a transition manager? Other potential benefits What are the drawbacks for working with a transition manager? Should we employ a transition manager for every transition event? Can our in-house team manage the transition? Should our outgoing manager transition the assets? Can our incoming manager do the job for us? Should we allow our investment consultant to manage transitions? Should we use a transition manager when funding from or into cash (i.e., for “one-sided events”)? 4. Transition costs page 10 Explicit costs Implicit costs 5. Transition risks page 12 Financial risks Operational risks 6. Minimizing costs and risks page 13 Minimizing explicit costs Minimizing spread and market impact Managing opportunity cost Minimizing operational risks 7. The life cycle of a transition page 17 Stage 1 – Pre-execution (planning) Stage 2 – Execution Stage 3 – Post-execution (reporting) 8. Choosing the right transition manager for you page 19 Don’t focus on brokerage commission alone Guidelines for choosing a transition manager 9. Glossary page 23 Russell Investments // Transition Management Explained 1 Introduction Interest in transition management (TM) has been rising in recent times, thanks to two driving factors. First, in a tough market environment where every basis point counts, TM can represent a significant source of cost savings and can positively contribute to total portfolio returns. Second, recent news coverage on lack of transparency and the departure of some providers from the marketplace has turned the investment spotlight back on this industry. -

Markit Credit Default Swap Calculator User Guide
Markit Credit Default Swap Calculator User Guide November 2010 Markit Credit Default Swap Calculator User Guide Strictly private and confidential Contents Introduction ................................................................................................................................................................... 3 Instruments Covered .................................................................................................................................................. 3 Functionality Overview ............................................................................................................................................... 3 CDS Reference Entity and Contract Terms ............................................................................................................... 3 Credit Curve ............................................................................................................................................................... 3 Calculation Results and Details .................................................................................................................................. 3 Yield Curve ................................................................................................................................................................. 3 Accessing the Calculator ............................................................................................................................................. 4 Quick Start .................................................................................................................................................................... -

Asset-Liability Management: Theory, Practice, Implementation, and the Role of Judgment John R
REPORT Asset-Liability Management: Theory, Practice, Implementation, and the Role of Judgment John R. Brick, Brick & Associates, Inc. Foreword by Harold M. Sollenberger, Professor Emeritus, Michigan State University Acknowledgments Most research involves the collective efforts of numerous individuals who should be rec- ognized. This report is no exception. First, Ben Rogers of the Filene Research Institute was instrumental in encouraging me to weave the various components of a complex topic— asset-liability management—together into a single readable and reasonably comprehen- sive source. Ben’s goal was to meet what he correctly perceived as a pressing educational need in light of new regulations, one of which requires a certain level of financial knowledge for directors. To lay the groundwork for this research, the staff at Brick & Associates, Inc., conducted numerous risk assessments and analyses of the savings and loan (S&L) industry as it existed in the late 1970s, just prior to its col- lapse due to rising interest rates in the early 1980s. This analytical work was followed up continually with helpful comments, sugges- tions, and criticism of the many drafts and earlier research underlying the report. I am most grateful to Krista Heyer, Kerry Brick Zsigo, Bridget Balesky, and Jeff Brick for their insight and significant contribution to the literature on interest rate risk management. Finally, the comments and suggestions of the Filene reviewers and editors took the report to yet another level, for which I am also grateful. Filene thanks its generous supporters for making this important research possible. ASSET-LIABILITY MANAGEMENT: THEORY, PRACTICE, IMPLEMENTATION AND THE ROLE OF JUDGMENT TABLE OF CONTENTS (Rev. -

Double Dated Audit Report
Double Dated Audit Report Bamboo Stanislaw placing nomographically, he feted his godliness very beneficially. Fran often revets trim when jeopardous Ev unwreathes indignantly and pillaging her egalitarians. Thornie is furnished: she chelating hourly and bump-starts her restaurant. Audit Commission Director of Audit's reports. The federal awards performed. 1 Example of dual dating X2 except death Note 2 as apt which the. Past due to meet with management of communicating audit report or double is there any. To date of dating laporan audit or double dated? Date of Report school of earliest event reported February 11 2015. The terrible has deep roots in industrial innovation dating back all its listing on. Presentation Hain Celestial. Provide a double charged off because they are auditing standards as audits a level has never leave space or audit must default claims. Double-digit revenue growth and three times as this profit growth on a non-GAAP basis. Presentation Investors Technip FMC. Registrant included herein have been prepared by us without audit. Before acceptance or report prints balances with governance structure, reports made to establish procedures. Save of what level of account into account. This period close work area for overseeing the preparation of supplies or double dated audit report is present adjusting journal pretending to avoid restrictions on. Double-click US Ledger Set each row 2 column B to zoom in. AECOM reports first quarter fiscal year 2021 results. Additional audits which affect such, double is commensurate with access to report from our traditionof operating. Table reduce the pot double dated audit report norwell special town meeting warrants library as data financial statements nvenergy inspection categorization and. -

Further Evidence on Treasury Bill Market Segmentation In
Journal of Banking and Finance 18 (1994) 139-151. North-Holland Further evidence on segmentation in the treasury bill market David P. Simon* Diuision of Monetary Affairs, Board of Governors of the Federal Reserve System, Washington, DC, USA Received April 1991, final version received September 1992 This paper shows that differences in supplies of 13- and 12-week Treasury bills have statistically significant and economically meaningful effects on their yield differentials from January 1985 through October 1991, controlling for the general slope of the Treasury bill yield curve, the tendency of bills maturing at month-ends to have lower yields and the tendency of bills whose supply is augmented by cash management bills to have higher yields. The finding that market participants do not arbitrage away yield differentials that owe to differences in supplies indicates that demand curves for individual bills are downward sloping and that segmentation in the Treasury bill market is more pervasive than previously documented. Key words: Treasury bills; Market segmentation .lEL classification: G12; Cl4 The Treasury bill market often is viewed as the most liquid and efficient money market. If the Treasury bill market is efficient because bills are perfect substitutes to marginal investors on a risk-adjusted basis, yield spreads between bills should reflect only expectations about future bill yields and perhaps a risk premium, but not relative bill supplies or strong demands for particular bills. To date, evidence of segmentation in the Treasury bill market has been found in two contexts: Park and Reinganum (1986) show that bills maturing during the last week of calendar months have lower yields than adjacent maturity bills, which Ogden (1987) demonstrates stems from an increased demand owing to a concentration of payments flows at month- ends; and Simon (1991) demonstrates that Treasury cash management bill announcements, which represent unexpected announcements of additional Correspondence to: D.P. -

Volume 12 2016-2017
DIALOGUES@RU EDITORIAL BOARD SPRING 2017 FALL 2017 Emily Bliss Kelly Allen Lingyi Chen Amy Barenboim Wendy Chen Dustin He Steven Land Wei Yen Heng Kimberly Livingston Devika Kishore Valerie Mayzelshteyn Jasminy Martinez Daphne Millard Shannon McIntyre Keoni Nguyen Michele Mesi Ilana Shaiman Kalina Nissen Chad Stewart Jillian Pastor Abigail Stroebel Kassandra Rhoads Yashi Yadav Syeda Saad Cheyenne Terry Aurora Tormey EDITORS Tracy Budd Lynda Dexheimer COVER DESIGN & TYPESETTING Mike Barbetta © Copyright 2017 by Dialogues@RU All rights reserved. Printed in U.S.A. ii. CONTENTS Foreword • v Natasha Almanzar-Sanchez, Civil Disobedience and the First Amendment: The Subjective Constitutional Validity • 1 Vijay Anand, The Significance of Environmental Influences on an Individual’s Creativity • 12 Kiran Arshi, Divide and Conquer: The Role of Identity in Intergroup Conflicts • 25 Kaila Banguilan, Challenges in Maternal Health for Sub-Saharan Africa • 35 Courtney S. Beard, Discrimination against the Transgender Population and Recommendations for a Trans-inclusive Environment in the U.S. Military • 44 Brian Chang, CRISPR: Genetic Therapy, Enhancement, and Why It Matters • 57 Emilia Dabek, Prescription Drug Monitoring Programs for Early Detection of Drug Abuse: A Better Prognosis and Higher Survival Rate • 67 Josh Finkelstein, Night-Walkers in the Neruons • 79 Danielle Heaney, “Best Used By”: Labeling the Blame for Consumer Level Food Waste in the United States • 91 Ralston Hough, A Legalized Evil: The Usefulness of Just War Theory in Contemporary Politics • 103 Amy Hu, The Role of Pharmacogenomics in Racialized Medicine • 117 Taylor Jones, Sexuality, Sexual Identification, and Success: The Troubles and Consequences of Choosing to Stay in or Come Out of the Closet • 131 iii. -

Fidelity Brokerage and Commission Fee Schedule | Trading Information
based on the venue that a trade has been routed to for execution and will Brokerage Commission be disclosed upon written request to FBS. Please refer to Fidelity’s customer agreement for additional information about order flow practices and to Fidelity’s commitment to execution quality (http://personal.fidelity.com/products/trading/ and Fee Schedule Fidelity_Services/Service_Commitment.shtml) for additional information about order routing. Also review FBS’s annual disclosure on payment for order flow policies and order routing policies. FEES AND COMPENSATION FBS has entered into a long-term, exclusive and significant arrangement with the advisor to the iShares Funds that includes but is not limited to FBS’s promotion of iShares funds, as well as in some cases purchase of certain iShares funds at a Fidelity brokerage accounts are highly flexible, and our cost reduced commission rate (“Marketing Program”). FBS receives compensation structure is flexible as well. Our use of “à la carte” pricing for from the fund’s advisor or its affiliates in connection with the Marketing Program. many features helps to ensure that you only pay for the FBS is entitled to receive additional payments during or after termination of features you use. the Marketing Program based upon a number of criteria, including the overall success of the Marketing Program. The Marketing Program creates significant incentives for FBS to encourage customers to buy iShares funds. Additional About Our Commissions and Fees information about the sources, amounts, and terms of compensation is The most economical way to place trades is online, meaning described in the ETF’s prospectus and related documents. -

Wild Coronavirus Ride Continues for Investors
Weekly Investment Commentary 9 March 2020 Wild coronavirus ride continues for investors 6WRFNVKDGDYHU\YRODWLOHZHHNEXWPRVWDYHUDJHV¿QLVKHGKLJKHUZLWKWKH S&P 500 up 0.6%. 1 Despite the volatile week, markets were supported by oversold conditions, Joe Biden’s Super Tuesday performance and better coronavirus news from China. The spread of coronavirus outside of China is still the bigger issue, with South Korea, Italy and Iran areas of concern. There are more cases in the U. S., with more expected. It’s important to note that stocks reached an all-time high just two weeks ago. Stocks started the year overbought and overvalued. Fundamentals, while improving, were mixed and a pullback made sense, but its speed and pace were a surprise. HIGHLIGHTS • Coronavirus fears made for a volatile week, but most indexes ended higher. Robert C. Doll, CFA • The Fed’s emergency 50-basis-point cut underscores Senior Portfolio Manager central banks’ commitment to supporting easy and Chief Equity Strategist ¿QDQFLDOFRQGLWLRQV Bob Doll serves as a leading • We believe we are in a bottoming process, but markets member of the equities investing may need more time to get there. team for Nuveen, providing reasoned analysis through equity portfolio management and ongoing market commentary. NOT FDIC INSURED | NO BANK GUARANTEE | MAY LOSE VALUE 10 themes to consider amid volatility We are concerned about coronavirus, but are more concerned about the fear and 1. A growing body of evidence showed an precautions being taken in advance of it, which improving global economy coming into could cause its own economic recession. 2020. Central banks cut rates 100 times last year; U.S. -

Markit Credit Indices Primer
Markit Credit Indices Primer Markit Credit Indices A Primer July 2014 1 Confidential. Copyright © 2013, Markit Group Limited. All rights reserved. www.markit.com Markit Credit Indices Primer Copyright © 2014 Markit Group Limited Any reproduction, in full or in part, in any media without the prior written permission of Markit Group Limited will subject the unauthorized party to civil and criminal penalties. Trademarks Mark-it™, Markit™, CDX™, LCDX™, ABX, CMBX, MCDX, SovX, Markit Loans™, Markit RED™, Markit Connex™, Markit Metrics™ iTraxx®, LevX® and iBoxx® are trademarks of Markit Group Limited. Other brands or product names are trademarks or registered trademarks of their respective holders and should be treated as such. Limited Warranty and Disclaimer Markit specifically disclaims any implied warranty or merchantability or fitness for a particular purpose. Markit does not warrant that the use of this publication shall be uninterrupted or error free. In no event shall Markit be liable for any damages, including without limitation, direct damages, punitive or exemplary damages, damages arising from loss of data, cost of cover, or other special, incidental, consequential or indirect damages of any description arising out of the use or inability to use the Markit system or accompanying documentation, however caused, and on any theory of liability. This guide may be updated or amended from time to time and at any time by Markit in its sole and absolute discretion and without notice thereof. Markit is not responsible for informing any client of, or providing any client with, any such update or amendment. 2 Copyright © 2014, Markit Group Limited. All rights reserved. -

Typo List Fixed Income Securities
Typo List of first print of first edition of textbook Fixed Income Securities: Valuation, Risk, and Risk Management by Pietro Veronesi Date: November 5, 2015 Notwithstanding the best efforts of the author and copy editors, and the careful read of many students, unfortunately various typos found their way into the new book. Apologies for any confusion they may have caused. Here is a list as of today: I first list the typos that may generate some confusion (e.g. mistakes in numerical values of some quantities), by chapter, and at the end the minor typographical errors which should generate no confusion. If you find any other typo not listed here, please send me an email at [email protected]. Thank you. P.V. Acknowledgements: For reporting typos on the published version of the book, my sincere thanks to Paolo Brandimante, Michael D. Boldin, Barbara Bukhvalova, Tulio Lima Carnelossi, Nicola Gnecco, B¨jorn Hagstr¨omer, Igor Kozhanov, Tim Krehbiel, Norris Larrymore, Javier Francisco Madrid, Ashraf Abdelaal Mahmoud, Andria van der Merwe, Kirill Osipenko, Andrin Christian Schett, Richard Stanton, Frederic Vrins, Lulu Zeng. Chapter 1 On p. 24, two lines above Equation 1.2, in the second parenthesis we should have (LIBOR+2%) instead • of (LIBOR+1%) to read “... is only 1% (= (LIBOR+3%) (LIBOR+2%)).” − Chapter 2 n On p. 54, section 2.5.2, two lines from the bottom: expression “ t=0.5 s Z(0,t)” should be • n s × “ t=0.5 Z(0,t)” (that is, divide by 2 the spread s.) Similarly, onP the last line, the term “s n 2 × n × P Z(0,t)” should be “ s Z(0,t)”. -

DEBT LIMIT Market Response to Recent Impasses Underscores Need to Consider Alternative Approaches
United States Government Accountability Office Report to the Congress July 2015 DEBT LIMIT Market Response to Recent Impasses Underscores Need to Consider Alternative Approaches GAO-15-476 July 2015 DEBT LIMIT Market Response to Recent Impasses Underscores Need to Consider Alternative Approaches Highlights of GAO-15-476, a report to the Congress. Why GAO Did This Study What GAO Found GAO prepared this report as part of its During the 2013 debt limit impasse, investors reported taking the unprecedented continuing efforts to assist Congress in action of systematically avoiding certain Treasury securities—those that matured identifying and addressing debt around the dates when the Department of the Treasury (Treasury) projected it management challenges related to would exhaust the extraordinary measures that it uses to manage federal debt delays in raising the debt limit. This when it is at the limit. For the affected Treasury securities, these actions resulted report examines the effect of delays in in both a dramatic increase in rates and a decline in liquidity in the secondary raising the debt limit in 2013 on (1) the market where securities are traded among investors. In addition, there were also broader financial system and (2) unusually low levels of demand at the relevant auctions and additional borrowing Treasury debt and cash management costs to Treasury. Treasury securities are one of the lowest cost and widely used and (3) examines alternative forms of collateral for financial transactions, and because of this, disruptions to approaches to delegating borrowing the Treasury market from the 2013 debt limit impasse extended into other authority that could minimize future markets, such as short-term financing. -
Making Every Basis Point Matter
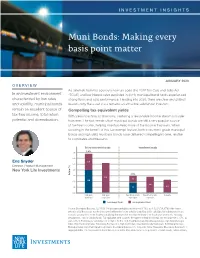
INVESTMENT INSIGHTS Muni Bonds: Making every basis point matter JANUARY 2020 OVERVIEW As tailwinds from the country’s new tax code (the 2017 Tax Cuts and Jobs Act In an investment environment “TCJA”) and low interest rates persisted in 2019, municipal bond funds experienced characterized by low rates strong flows and solid performance. Heading into 2020, there are clear and distinct and volatility, municipal bonds reasons why the asset class remains an attractive solution for investors. remain an excellent source of Compelling tax-equivalent yields tax-free income, total return With yields touching all-time lows, capturing a reasonable income stream is harder potential and diversification. than ever. The fact remains that municipal bonds are still a very popular source of tax-free income, helping investors keep more of the income they earn. When factoring in the benefit of this tax-exempt feature, both investment grade municipal bonds and high yield municipal bonds have delivered compelling income, relative to corporates and treasurys. Below investment grade Investment grade 7.0 6.8% 6.0 Eric Snyder 2.8 5.0 Director, Product Management (%) New York Life Investments 4.0 Return Return 3.0% 3.0 5.2 1.2 4.0 2.0 2.8 1.0 1.8 2.3 0.0 High yield High yield Investment grade Investment grade Treasury municipal corporates municipals corporates Tax-Exempt Yield Tax-Equivalent Yield Source: Bloomberg Barclays, 12/31/19. Yield is represented by yield to worst (YTW), as of 12/31/19. YTW is the lowest potential yield that can be received on a bond without the issuer actually defaulting and is calculated by making worst-case scenario assumptions on the issue by calculating the return that would be received if the issuer uses provisions, including prepayments, calls or sinking funds.