Network Management Card User's Guide
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-
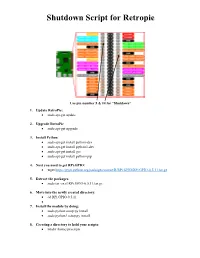
Shutdown Script for Retropie
Shutdown Script for Retropie Use pin number 5 & 14 for “Shutdown” 1. Update RetroPie: • sudo apt-get update 2. Upgrade RetroPie • sudo apt-get upgrade 3. Install Python • sudo apt-get install python-dev • sudo apt-get install python3-dev • sudo apt-get install gcc • sudo apt-get install python-pip 4. Next you need to get RPi.GPIO: • wget https://pypi.python.org/packages/source/R/RPi.GPIO/RPi.GPIO-0.5.11.tar.gz 5. Extract the packages: • sudo tar -zxvf RPi.GPIO-0.5.11.tar.gz 6. Move into the newly created directory: • cd RPi.GPIO-0.5.11 • 7. Install the module by doing: • sudo python setup.py install • sudo python3 setup.py install 8. Creating a directory to hold your scripts: • mkdir /home/pi/scripts 9. Call our script shutdown.py (it is written in python). Create and edit the script by doing: • sudo nano /home/pi/scripts/shutdown.py The content of the script: Paste it in the blank area #!/usr/bin/python import RPi.GPIO as GPIO import time import subprocess # we will use the pin numbering to match the pins on the Pi, instead of the # GPIO pin outs (makes it easier to keep track of things) GPIO.setmode(GPIO.BOARD) # use the same pin that is used for the reset button (one button to rule them all!) GPIO.setup(5, GPIO.IN, pull_up_down = GPIO.PUD_UP) oldButtonState1 = True while True: #grab the current button state buttonState1 = GPIO.input(5) # check to see if button has been pushed if buttonState1 != oldButtonState1 and buttonState1 == False: subprocess.call("shutdown -h now", shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE) oldButtonState1 = buttonState1 time.sleep(.1) Press CRTL X Then Y and Enter 10. -

Configuring UNIX-Specific Settings: Creating Symbolic Links : Snap
Configuring UNIX-specific settings: Creating symbolic links Snap Creator Framework NetApp September 23, 2021 This PDF was generated from https://docs.netapp.com/us-en/snap-creator- framework/installation/task_creating_symbolic_links_for_domino_plug_in_on_linux_and_solaris_hosts.ht ml on September 23, 2021. Always check docs.netapp.com for the latest. Table of Contents Configuring UNIX-specific settings: Creating symbolic links . 1 Creating symbolic links for the Domino plug-in on Linux and Solaris hosts. 1 Creating symbolic links for the Domino plug-in on AIX hosts. 2 Configuring UNIX-specific settings: Creating symbolic links If you are going to install the Snap Creator Agent on a UNIX operating system (AIX, Linux, and Solaris), for the IBM Domino plug-in to work properly, three symbolic links (symlinks) must be created to link to Domino’s shared object files. Installation procedures vary slightly depending on the operating system. Refer to the appropriate procedure for your operating system. Domino does not support the HP-UX operating system. Creating symbolic links for the Domino plug-in on Linux and Solaris hosts You need to perform this procedure if you want to create symbolic links for the Domino plug-in on Linux and Solaris hosts. You should not copy and paste commands directly from this document; errors (such as incorrectly transferred characters caused by line breaks and hard returns) might result. Copy and paste the commands into a text editor, verify the commands, and then enter them in the CLI console. The paths provided in the following steps refer to the 32-bit systems; 64-bit systems must create simlinks to /usr/lib64 instead of /usr/lib. -

ZD421 and ZD621 Users Guide (En)
ZD421 and ZD621 Series Link-OS® Printers User Guide P1123730-01EN ZEBRA and the stylized Zebra head are trademarks of Zebra Technologies Corporation, registered in many jurisdictions worldwide. All other trademarks are the property of their respective owners. © 2021 Zebra Technologies Corporation and/or its affiliates. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished under a license agreement or nondisclosure agreement. The software may be used or copied only in accordance with the terms of those agreements. For further information regarding legal and proprietary statements, please go to: SOFTWARE: zebra.com/linkoslegal COPYRIGHTS: zebra.com/copyright WARRANTY: zebra.com/warranty END USER LICENSE AGREEMENT: zebra.com/eula Terms of Use Proprietary Statement This manual contains proprietary information of Zebra Technologies Corporation and its subsidiaries (“Zebra Technologies”). It is intended solely for the information and use of parties operating and maintaining the equipment described herein. Such proprietary information may not be used, reproduced, or disclosed to any other parties for any other purpose without the express, written permission of Zebra Technologies. Product Improvements Continuous improvement of products is a policy of Zebra Technologies. All specifications and designs are subject to change without notice. Liability Disclaimer Zebra Technologies takes steps to ensure that its published Engineering specifications and manuals are -

Shell Scripting with Bash
Introduction to Shell Scripting with Bash Charles Jahnke Research Computing Services Information Services & Technology Topics for Today ● Introductions ● Basic Terminology ● How to get help ● Command-line vs. Scripting ● Variables ● Handling Arguments ● Standard I/O, Pipes, and Redirection ● Control Structures (loops and If statements) ● SCC Job Submission Example Research Computing Services Research Computing Services (RCS) A group within Information Services & Technology at Boston University provides computing, storage, and visualization resources and services to support research that has specialized or highly intensive computation, storage, bandwidth, or graphics requirements. Three Primary Services: ● Research Computation ● Research Visualization ● Research Consulting and Training Breadth of Research on the Shared Computing Cluster (SCC) Me ● Research Facilitator and Administrator ● Background in biomedical engineering, bioinformatics, and IT systems ● Offices on both CRC and BUMC ○ Most of our staff on the Charles River Campus, some dedicated to BUMC ● Contact: [email protected] You ● Who has experience programming? ● Using Linux? ● Using the Shared Computing Cluster (SCC)? Basic Terminology The Command-line The line on which commands are typed and passed to the shell. Username Hostname Current Directory [username@scc1 ~]$ Prompt Command Line (input) The Shell ● The interface between the user and the operating system ● Program that interprets and executes input ● Provides: ○ Built-in commands ○ Programming control structures ○ Environment -

Types and Programming Languages by Benjamin C
< Free Open Study > . .Types and Programming Languages by Benjamin C. Pierce ISBN:0262162091 The MIT Press © 2002 (623 pages) This thorough type-systems reference examines theory, pragmatics, implementation, and more Table of Contents Types and Programming Languages Preface Chapter 1 - Introduction Chapter 2 - Mathematical Preliminaries Part I - Untyped Systems Chapter 3 - Untyped Arithmetic Expressions Chapter 4 - An ML Implementation of Arithmetic Expressions Chapter 5 - The Untyped Lambda-Calculus Chapter 6 - Nameless Representation of Terms Chapter 7 - An ML Implementation of the Lambda-Calculus Part II - Simple Types Chapter 8 - Typed Arithmetic Expressions Chapter 9 - Simply Typed Lambda-Calculus Chapter 10 - An ML Implementation of Simple Types Chapter 11 - Simple Extensions Chapter 12 - Normalization Chapter 13 - References Chapter 14 - Exceptions Part III - Subtyping Chapter 15 - Subtyping Chapter 16 - Metatheory of Subtyping Chapter 17 - An ML Implementation of Subtyping Chapter 18 - Case Study: Imperative Objects Chapter 19 - Case Study: Featherweight Java Part IV - Recursive Types Chapter 20 - Recursive Types Chapter 21 - Metatheory of Recursive Types Part V - Polymorphism Chapter 22 - Type Reconstruction Chapter 23 - Universal Types Chapter 24 - Existential Types Chapter 25 - An ML Implementation of System F Chapter 26 - Bounded Quantification Chapter 27 - Case Study: Imperative Objects, Redux Chapter 28 - Metatheory of Bounded Quantification Part VI - Higher-Order Systems Chapter 29 - Type Operators and Kinding Chapter 30 - Higher-Order Polymorphism Chapter 31 - Higher-Order Subtyping Chapter 32 - Case Study: Purely Functional Objects Part VII - Appendices Appendix A - Solutions to Selected Exercises Appendix B - Notational Conventions References Index List of Figures < Free Open Study > < Free Open Study > Back Cover A type system is a syntactic method for automatically checking the absence of certain erroneous behaviors by classifying program phrases according to the kinds of values they compute. -
Adding a Shutdown Button to the Raspberry Pi B+ Version 1
Welcome, Guest Log in Register Activity Translate Content Search within content, members or groups Search Topics Resources Members Design Center Store All Places > Raspberry Pi > Raspberry Pi Projects > Documents Adding a Shutdown Button to the Raspberry Pi B+ Version 1 Created by ipv1 on Aug 4, 2015 3:05 AM. Last modified by ipv1 on Aug 18, 2015 9:52 AM. Introduction What do you need? Step 1. Setup the RPi Step 2. Connecting the button Step 3. Writing a Python Script Step 4. Adding it to startup Step 5. More to do Introduction For a beginner to the world of raspberry pi, there are a number of projects that can become the start of something big. In this article, I discuss such a simple project which is adding a button that can be used to shutdown the raspberry pi using a bit of software tinkering. I wrote a similar article in 2013 at my blog “embeddedcode.wordpress.com” and its got its share of attention since a lot of people starting out with a single board computer, kept looking for a power button. Additionally, those who wanted a headless system, needed a way to shutdown the computer without the mess of connecting to it over the network or attaching a monitor and keyboard to it. In this article, I revisit the tutorial on how to add a shutdown button while trying to explain the workings and perhaps beginners will find it an amusing to add find more things to do with this little recipe. What do you need? Here is a basic bill of materials required for this exercise. -

Shutdown Policies with Power Capping for Large Scale Computing Systems Anne Benoit, Laurent Lefèvre, Anne-Cécile Orgerie, Issam Raïs
Shutdown Policies with Power Capping for Large Scale Computing Systems Anne Benoit, Laurent Lefèvre, Anne-Cécile Orgerie, Issam Raïs To cite this version: Anne Benoit, Laurent Lefèvre, Anne-Cécile Orgerie, Issam Raïs. Shutdown Policies with Power Capping for Large Scale Computing Systems. Euro-Par: International European Conference on Parallel and Distributed Computing, Aug 2017, Santiago de Compostela, Spain. pp.134 - 146, 10.1109/COMST.2016.2545109. hal-01589555 HAL Id: hal-01589555 https://hal.archives-ouvertes.fr/hal-01589555 Submitted on 18 Sep 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Shutdown policies with power capping for large scale computing systems Anne Benoit1, Laurent Lef`evre1, Anne-C´ecileOrgerie2, and Issam Ra¨ıs1 1 Univ. Lyon, Inria, CNRS, ENS de Lyon, Univ. Claude-Bernard Lyon 1, LIP 2 CNRS, IRISA, Rennes, France Abstract Large scale distributed systems are expected to consume huge amounts of energy. To solve this issue, shutdown policies constitute an appealing approach able to dynamically adapt the resource set to the actual workload. However, multiple constraints have to be taken into account for such policies to be applied on real infrastructures, in partic- ular the time and energy cost of shutting down and waking up nodes, and power capping to avoid disruption of the system. -

Master's Thesis Electronic Gatekeeper Using ETHERNET
University of West Bohemia Faculty of Applied Sciences Department of Computer Science and Engineering Master’s thesis Electronic Gatekeeper using ETHERNET Plzeň 2019 Hamza Elghoul Místo této strany bude zadání práce. Declaration I hereby declare that this master’s thesis is completely my own work and that I used only the cited sources. Plzeň, 2 May 2018 Hamza Elghoul Abstract The aim of this thesis is the analysis and the realization of a budget 2-way communication system using ETHERNET connection, more specific- ally a door intercom station (hereinafter ”Bouncer” or "Gatekeeper"), where it is possible to make voice calls between two CLIENTS, a CALLER and a CALLEE with an acceptable to minimal delay. There are many alternative methods available for implementing such sys- tems, this project will try to compare some of these solutions and choose the most convenient platform according to a number of factors, such as band- width, processing power needed and communication protocols in question. Keywords: VoIP, SIP,SDP, server, client, LAN, ethernet, embedded, audio, raspberry pi Contents Page List of Figures7 1 Preface 10 2 Analysis 11 2.1 Objectives and Requirements................. 11 2.2 Hardware............................ 12 2.2.1 Arduino......................... 12 2.2.2 RaspberryPi 3 Model B................ 13 2.2.3 Banana Pi........................ 14 2.2.4 Orange Pi........................ 15 2.2.5 CubieBoard 2...................... 16 2.2.6 Beagle Bone Black................... 16 2.3 Application........................... 18 2.4 Audio capture and digitalisation................ 19 2.4.1 Signaling Protocols................... 20 2.5 Communication Protocol.................... 23 2.5.1 Session Initiation Protocol............... 23 2.5.2 Real Time Protocol.................. -

Cisco Telepresence ISDN Link API Reference Guide (IL1.1)
Cisco TelePresence ISDN Link API Reference Guide Software version IL1.1 FEBRUARY 2013 CIS CO TELEPRESENCE ISDN LINK API REFERENCE guide D14953.02 ISDN Link API Referenec Guide IL1.1, February 2013. Copyright © 2013 Cisco Systems, Inc. All rights reserved. 1 Cisco TelePresence ISDN Link API Reference Guide ToC - HiddenWhat’s in this guide? Table of Contents text The top menu bar and the entries in the Table of Introduction ........................................................................... 4 Description of the xConfiguration commands ......................17 Contents are all hyperlinks, just click on them to go to the topic. About this guide ...................................................................... 5 Description of the xConfiguration commands ...................... 18 User documentation overview.............................................. 5 We recommend you visit our web site regularly for Technical specification ......................................................... 5 Description of the xCommand commands .......................... 44 updated versions of the user documentation. Support and software download .......................................... 5 Description of the xCommand commands ........................... 45 What’s new in this version ...................................................... 6 Go to:http://www.cisco.com/go/isdnlink-docs Description of the xStatus commands ................................ 48 Automatic pairing mode ....................................................... 6 Description of the -

Technical Data Specifications & Capacities
5669 (supersedes 5581)-0114-L9 1 Technical Data Specifications & Capacities Crawler Crane 300 Ton (272.16 metric ton) CAUTION: This material is supplied for reference use only. Operator must refer to in-cab Crane Rating Manual and Operator's Manual to determine allowable crane lifting capacities and assembly and operating procedures. Link‐Belt Cranes 348 HYLAB 5 5669 (supersedes 5581)-0114-L9 348 HYLAB 5 Link‐Belt Cranes 5669 (supersedes 5581)-0114-L9 Table Of Contents Upper Structure ............................................................................ 1 Frame .................................................................................... 1 Engine ................................................................................... 1 Hydraulic System .......................................................................... 1 Load Hoist Drums ......................................................................... 1 Optional Front-Mounted Third Hoist Drum................................................... 2 Boom Hoist Drum .......................................................................... 2 Boom Hoist System ........................................................................ 2 Swing System ............................................................................. 2 Counterweight ............................................................................ 2 Operator's Cab ............................................................................ 2 Rated Capacity Limiter System ............................................................. -

User's Manual 2
USER'S MANUAL 2 - © 2018. All Rights Reserved. Nitro 5 Covers: AN515-42 / AN515-52 This revision: March 2018 Important This manual contains proprietary information that is protected by copyright laws. The information contained in this manual is subject to change without notice. Some features described in this manual may not be supported depending on the Operating System version. Images provided herein are for reference only and may contain information or features that do not apply to your computer. Acer Group shall not be liable for technical or editorial errors or omissions contained in this manual. Register your Acer product 1. Ensure you are connected to the Internet. 2. Open the Acer Product Registration app. 3. Install any required updates. 4. Sign up for an Acer ID or sign in if you already have an Acer ID, it will automatically register your product. After we receive your product registration, you will be sent a confirmation email with important data. Model number: _________________________________ Serial number: _________________________________ Date of purchase: ______________________________ Place of purchase: ______________________________ Table of contents - 3 TABLE OF CONTENTS First things first 6 BIOS utility 39 Your guides ............................................. 6 Boot sequence....................................... 39 Basic care and tips for using your Setting passwords ................................. 39 computer.................................................. 6 Power management 40 Turning your computer off.......................... -

The Linux Command Line
The Linux Command Line Fifth Internet Edition William Shotts A LinuxCommand.org Book Copyright ©2008-2019, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042. A version of this book is also available in printed form, published by No Starch Press. Copies may be purchased wherever fine books are sold. No Starch Press also offers elec- tronic formats for popular e-readers. They can be reached at: https://www.nostarch.com. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. Release History Version Date Description 19.01A January 28, 2019 Fifth Internet Edition (Corrected TOC) 19.01 January 17, 2019 Fifth Internet Edition. 17.10 October 19, 2017 Fourth Internet Edition. 16.07 July 28, 2016 Third Internet Edition. 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. Table of Contents Introduction....................................................................................................xvi Why Use the Command Line?......................................................................................xvi