A QUANTITATIVE ANALYSIS of AD BLOCKER USAGE by Josh Young
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Ethics for Digital Journalists
ETHICS FOR DIGITAL JOURNALISTS The rapid growth of online media has led to new complications in journalism ethics and practice. While traditional ethical principles may not fundamentally change when information is disseminated online, applying them across platforms has become more challenging as new kinds of interactions develop between jour- nalists and audiences. In Ethics for Digital Journalists , Lawrie Zion and David Craig draw together the international expertise and experience of journalists and scholars who have all been part of the process of shaping best practices in digital journalism. Drawing on contemporary events and controversies like the Boston Marathon bombing and the Arab Spring, the authors examine emerging best practices in everything from transparency and verifi cation to aggregation, collaboration, live blogging, tweet- ing, and the challenges of digital narratives. At a time when questions of ethics and practice are challenged and subject to intense debate, this book is designed to provide students and practitioners with the insights and skills to realize their potential as professionals. Lawrie Zion is an Associate Professor of Journalism at La Trobe University in Melbourne, Australia, and editor-in-chief of the online magazine upstart. He has worked as a broadcaster with the Australian Broadcasting Corporation and as a fi lm journalist for a range of print publications. He wrote and researched the 2007 documentary The Sounds of Aus , which tells the story of the Australian accent. David Craig is a Professor of Journalism and Associate Dean at the University of Oklahoma in the United States. A former newspaper copy editor, he is the author of Excellence in Online Journalism: Exploring Current Practices in an Evolving Environ- ment and The Ethics of the Story: Using Narrative Techniques Responsibly in Journalism . -

E Cost of Ad Blocking Pagefair and Adobe 2015 Ad Blocking Report
!e cost of ad blocking PageFair and Adobe 2015 Ad Blocking Report Introduction In the third annual ad blocking report, PageFair, with the help of Adobe, provides updated data on the scale and growth of ad blocking so"ware usage and highlights the global and regional economic impact associated with it. Additionally, this report explores the early indications surrounding the impact of ad blocking within the mobile advertising space and how mobile will change the ad blocking landscape. Table of Contents 3. Key insights 8. Effect of ad blocking by industry 13. A"erword 4. Global ad blocking growth 9. Google Chrome still the main driver of ad 14. Background 5. Usage of ad blocking so"ware in the United block growth 15. Methodology States 10. Mobile is yet to be a factor in ad blocking 16. Tables 6. Usage of ad blocking so"ware in Europe growth 17. Tables 7. !e cost of blocking ads 11. Mobile will facilitate future ad blocking growth 12. Reasons to start using an ad blocker PAGEFAIR AND ADOBE | 2015 Ad Blocking Report 2 Key Insights More consumers block ads, continuing the strong growth rates seen during 2013 and 2014. 41% YoY global growth Q2 2014 - Q2 2015 !e "ndings • Globally, the number of people using ad blocking so"ware grew by 41% year over year. • 16% of the US online population blocked ads during Q2 2015. • Ad block usage in the United States grew 48% during the past year, increasing to 45 million monthly active 45 million users (MAUs) during Q2 2015. Average MAUs in the United • Ad block usage in Europe grew by 35% during the past year, increasing to 77 million monthly active users States Q2 2015 during Q2 2015. -

The Impact of Ad-Blockers on Online Consumer Behavior
Marketing Science Institute Working Paper Series 2021 Report No. 21-119 The Impact of Ad-blockers on Online Consumer Behavior Vilma Todri “The Impact of Ad-blockers on Online Consumer Behavior” © 2021 Vilma Todri MSI Working Papers are Distributed for the benefit of MSI corporate and academic members and the general public. Reports are not to be reproduced or published in any form or by any means, electronic or mechanical, without written permission. Marketing Science Institute Working Paper Series The Impact of Ad-blockers on Online Consumer Behavior Vilma Todri Goizueta Business School, Emory University, Atlanta, GA 30322 [email protected] Digital advertising is on track to become the dominant form of advertising but ad-blocking technologies have recently emerged posing a potential threat to the online advertising ecosystem. A significant and increasing fraction of Internet users has indeed already started employing ad-blockers. However, surprisingly little is known yet about the effects of ad-blockers on consumers. This paper investigates the impact of ad- blockers on online search and purchasing behaviors by empirically analyzing a consumer-level panel dataset. Interestingly, the analyses reveal that ad-blockers have a significant effect on online purchasing behavior: online consumer spending decreases due to ad-blockers by approximately $14:2 billion a year in total. In examining the underlying mechanism of the ad-blocker effects, I find that ad-blockers significantly decrease spending for brands consumers have not experienced before, partially shifting spending towards brands they have experienced in the past. I also find that ad-blockers spur additional unintended consequences as they reduce consumers' search activities across information channels. -

Will Ad Blocking Break the Internet?
NBER WORKING PAPER SERIES WILL AD BLOCKING BREAK THE INTERNET? Ben Shiller Joel Waldfogel Johnny Ryan Working Paper 23058 http://www.nber.org/papers/w23058 NATIONAL BUREAU OF ECONOMIC RESEARCH 1050 Massachusetts Avenue Cambridge, MA 02138 January 2017 Johnny Ryan is an employee of PageFair, a firm that measures the extent of ad blocking and offers ad-recovery technologies that enable publishers to display ads in a manner that adblockers cannot block. Neither Shiller nor Waldfogel has received any compensation for the research in the paper. PageFair was allowed to review the paper for accuracy but did not have control over the paper's findings nor conclusions. The views expressed herein are those of the authors and do not necessarily reflect the views of the National Bureau of Economic Research. NBER working papers are circulated for discussion and comment purposes. They have not been peer-reviewed or been subject to the review by the NBER Board of Directors that accompanies official NBER publications. © 2017 by Ben Shiller, Joel Waldfogel, and Johnny Ryan. All rights reserved. Short sections of text, not to exceed two paragraphs, may be quoted without explicit permission provided that full credit, including © notice, is given to the source. Will Ad Blocking Break the Internet? Ben Shiller, Joel Waldfogel, and Johnny Ryan NBER Working Paper No. 23058 January 2017 JEL No. L81,L82 ABSTRACT Ad blockers allow Internet users to obtain information without generating ad revenue for site owners; and by 2016 they were used by roughly a quarter of site visitors. Given the ad-supported nature of much of the web, ad blocking poses a threat to site revenue and, if revenue losses undermine investment, a possible threat to consumers' access to appealing content. -

Storytelling and Social Media
NIEMAN REPORTS Storytelling and Social Media HANNA, one of the subjects in “Maidan: Portraits from the Black Square,” Kiev, February 2014 Nieman Online From the Archives For some photojournalists, it’s the shots they didn’t take they remember best. In the Summer 1998 issue of Nieman Reports, Nieman Fellows Stan Grossfeld, David Turnley, Steve Northup, Stanley Forman, and Frank Van Riper reflect on the shots they missed, whether by mistake or by choice, in “The Best Picture I Never Took” series. Digital Strategy at The New York Times In a lengthy memo, The New York Times revealed that it hopes to double its “Made in Boston: Stories of Invention and Innovation” brought together, from left, author digital revenue to $800 million by 2020. Ben Mezrich, Boston Globe reporter Hiawatha Bray, author Steve Almond, WGBH’s “Innovation The paper plans to simplify subscriptions, Hub” host Kara Miller, NPR’s “On Point” host Tom Ashbrook, “Our Bodies, Ourselves” improve advertising and sponsorships, co-founder Judy Norsigian, journalist Laurie Penny, and MIT Media Lab director Joi Ito optimize for different mediums, and nieman.harvard.edu, events extend its international reach. No Comments An in-depth look at why seven major news organizations—Reuters, Mic, The Week, Popular Science, Recode, The Verge, and USA Today’s FTW—suspended user comments, the results of that decision, and Innovators “always said how these media outlets are using social no when other people media to encourage reader engagement. said yes and they always 5 Questions: Geraldine Brooks Former Wall Street Journal foreign said yes when other correspondent and Pulitzer Prize-winning novelist Geraldine Brooks talks with her old Columbia Journalism School classmate people said no. -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

What's Podcasting to You? Exploring Perspectives of Consumers and Producers
What's Podcasting to you? Exploring Perspectives of Consumers and Producers Student Name - Arshdeep Chawla Module - COMM5600: Dissertation & Research Methods Course - MA New Media Submitted on - 3 September 2018 Page !1 of !79 TABLE OF CONTENTS Introduction 4 Chapter I - Literature Review 6 Podcasting 6 Overview: Podcasting Industry 7 Overview: Podcast Production 11 Experimental Application Perpective 16 Emerging Technologies - Redefining Podcast Discovery? 17 Pivotal Shows and Trends 21 Chapter II - Methodology 23 Interview 24 Chapter III - Findings, Discussions and Analysis 29 Podcasting 29 Software 33 Smart Speakers 34 Production, Distribution and Technology 36 Closing Remarks 41 Chapter IV - Conclusion 42 List of References 45 Appendices 54 Appendix I - Transcripts 54 Appendix II - Ethics Form 76 Appendix III - Research Checklist 77 Appendix IV - Information Sheet 78 Page !2 of !79 Abstract Past research has widely investigated podcasting in academia and education. Some research has investigated motivations of podcasters and listeners using quantitive methods. However, little is known about perspectives of podcast users and producers with respect to technological and cultural changes in the medium. This dissertation outlines findings from interviews conducted with podcast users and a podcast producer that lays out thoughts about the medium on themes like technology, production, distribution etc. Page !3 of !79 Introduction Podcasting, an automated subscription-based system of recorded audio/video content powered by the internet, finds its origins in the early 2000s and witnessed wide adoption in 2005. This makes podcasting older than Facebook or Twitter, two very popular products of the internet age. Although, podcasting has not been able to replicate the same success as those social networking sites, it has had a few pivotal moments that left an indelible impact on the digital media industry. -

Security Now! #521 - 08-18-15 Security Is Difficult
Security Now! #521 - 08-18-15 Security is Difficult This week on Security Now! ● Android StageFright, two steps forward, one step back ● Windows 10 new privacy concerns ● High profile Malvertising surfaces ● Kaspersky, Lenovo, HTC and AT&T each in their own doghouses. ● Some miscellaneous tidbits... ● Some additional thoughts about surfing safety and web advertising. Security News Android StageFright: ● First the good news: Phones are getting patched and reporting non-vulnerable. ● Ernest Koch @nullconmedia ○ @SGgrc After yesterday's patch, my Nexus 6 is showing not vulnerable. ● Simon Zerafa confirmed that both his Nexus 6 & 7 were just updated. ○ Nexus 6 Android 5.1.1 build LMY48I gets 6 greens on the Zimperium StageFright test :-) ● Joe McDaniel @joem5636 ○ @SGgrc just got my Nexus 5.1.1 upgrade. Oddly, did not change version! ○ (Confirmed that all testing apps now show safe.) ● Eric Throndson @EricThrondson ○ @SGgrc My Nexus 6 is getting MMS messages from random numbers that I assume have #Stagefright. I'm patched, but nervous and annoyed. ● Bob Thibodeau @bobthibincs ○ @SGgrc: got a notice from AT&T to update, no longer vulnerable to Stagefright, One of the critical Android Stagefright patches was incomplete ● Exodus Intelligence: (CVE-2015-3864) Stagefright: Mission Accomplished? ○ https://blog.exodusintel.com/2015/08/13/stagefright-mission-accomplished/ ● Stagefright Patch Incomplete Leaving Android Devices Still Exposed ○ https://threatpost.com/stagefright-patch-incomplete-leaving-android-devices-still-e xposed/114267 ● Patch Comment: When the sum of the 'size' and 'chunk_size' variables is larger than 2^32, an integer overflow occurs. Using the resulting (overflowed) value to allocate memory leads to an undersized buffer allocation and later a potentially exploitable heap corruption condition. -

Understanding Ad Blockers
Understanding Ad Blockers A Major Qualifying Project Submitted to the Faculty of Worcester Polytechnic Institute In partial fulfillment of the requirements for the Degree of Bachelor of Science In Computer Science By _________________________________ Doruk Uzunoglu March 21, 2016 _______________________ Professor Craig E. Wills, Project Advisor Professor and Department Head Department of Computer Science ABSTRACT This project aims to provide useful information for users and researchers who would like to learn more about ad blocking. Three main research areas are explored in this project. The first research area provides general information about ad blocking tools and aims to explore ad blockers from a user’s perspective. The second research area provides analyses regarding thirdparty sites that appear on popular firstparty sites in order to explore the behavior of thirdparties. Finally, the third research area provides analyses regarding filter lists, which are sets of ad filtering rules used by ad blocking tools. The third research area aims to convey the differences and similarities between individual filter lists as well as sets of filter lists that form the defaults of ad blocking tools. 1 ACKNOWLEDGEMENTS I would like to thank Professor Craig Wills for advising my project, providing insight, and gathering the popular thirdparty domains data which I analyzed as part of this project. In addition, I would like to thank Jinyan Zang for sharing the thirdparty data regarding mobile apps, which they have gathered as part of their 2015 paper named “Who Knows What About Me? A Survey of Behind the Scenes Personal Data Sharing to Third Parties by Mobile Apps.” The data provided by Jinyan Zang was also analyzed as part of this project. -

Apple Podcasts, Google Play, Stitcher, and Blubrry (Explained Later in This Chapter)
IN THIS CHAPTER » Finding out what podcasting is » Creating a podcast » Finding and subscribing to podcasts Chapter 1 Getting the Scoop on Podcasting ometimes the invention that makes the biggest impact on our daily lives isn’t an invention at all, but the convergence of existing technologies, Sprocesses, and ideas. Podcasting may be the perfect example of that principle — and it’s changing the relationship people have with their radios, music collections, books, education, and more. The podcasting movement is actually a spin-off of another communications boom: blogs. Blogs sprang up right and left in the early 2000s, providing nonpro- grammers and designers a clean, elegant interface that left many on the technol- ogy side wondering why they hadn’t thought of it sooner. Everyday people could chronicle their lives, hopes, dreams, and fears and show them to anyone who cared to read. And oddly enough, people did care to read — and still do. Then COPYRIGHTEDin 2003, former MTV VeeJay Adam MATERIAL Curry started collaborating with pro- grammer Dave Winer about improving RSS (which stands for Really Simple Syndi- cation ) that not only allowed you to share text and images, but media attachments which included compressed audio and video fi les. Soon after, Curry released his fi rst podcast catching client. Thus launched the media platform of podcasting. Podcasting combines the instant information exchange of blogging with audio and video fi les that you can play on a computer or portable media device. When CHAPTER 1 Getting the Scoop on Podcasting 11 0004944333.INDD 11 Trim size: 7.375 in × 9.25 in September 12, 2020 1:30 AM you make your podcast publicly available on the Internet, you are exposing your craft to anyone with a computer or mobile device and a connection capable of streaming data. -

Snowwall: a Visual Firewall for the Surveillance Society
Imperial College London Department of Computing SnowWall: A Visual Firewall for the Surveillance society Madalina-Ioana Sas [email protected] June 2017 Supervised by Dr. William J. Knottenbelt Submitted in part fulfillment of the requirements for the degree of Master of Engineering in Computing of Imperial College London. 2 Abstract In the past two decades we have seen a steady increase in the adoption of various technologies that fit into what can be described as a digital lifestyle. Sharing data, experiences and our most intimate thoughts has become second nature to most people connected to the Internet. And as market trends shift so did the approach that companies and governments have in regards to each individual's digital footprint. The uncharted wild west that used to be the internet of yesteryear has become a battleground where everyone is fighting over who knows the user better. Findings such as the Snowden and the Vault7 leaks have deeply shaken the status quo in privacy. This project revolves around giving the end user back insight and control over what they involuntarily share with the world. We present SnowWall: a networking tool designed to provide insights and control into the networking activity on a Windows-based system. SnowWall interacts with the operating system, intercepts every inbound and outbound connection, provides information on the connection's state, lifetime, owning process, and most importantly, remote end point, such as geolocation and ownership information. SnowWall is a powerful tool designed to be user-friendly, which allows anyone to block unwanted connections with high-level firewall rules, such as blocking by country or by owning organization name. -
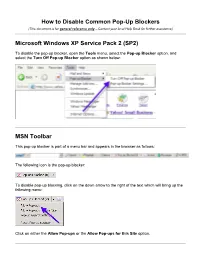
How to Disable Common Pop-Up Blockers Microsoft Windows XP
How to Disable Common Pop-Up Blockers (This document is for general reference only – Contact your local Help Desk for further assistance) Microsoft Windows XP Service Pack 2 (SP2) To disable the pop-up blocker, open the Tools menu, select the Pop-up Blocker option, and select the Turn Off Pop-up Blocker option as shown below: MSN Toolbar This pop-up blocker is part of a menu bar and appears in the browser as follows: The following icon is the pop-up blocker: To disable pop-up blocking, click on the down arrow to the right of the text which will bring up the following menu: Click on either the Allow Pop-ups or the Allow Pop-ups for this Site option. Google Toolbar The following icon is the pop-up blocker: To allow pop-ups to appear, merely click on the icon. You should now see the following: Yahoo! Toolbar The following icon is the pop-up blocker: To disable pop-up blocking, click on the down arrow beside the icon to bring up its menu, as follows: Click on the Enable Pop-Up Blocker option to remove the checkmark beside it, disabling the pop-up blocking. AOL Toolbar The following icon is the pop-up blocker: To allow pop-ups to appear, merely click on the icon. You should now see the following: Mozilla Firefox Open the Tools menu and click on Options. The following window will appear: Select the Content icon. Remove the checkmark from beside the Block pop-up windows option. Click OK to close the window.