Air Marshal Datasheet
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-
PDF File, 139.89 KB
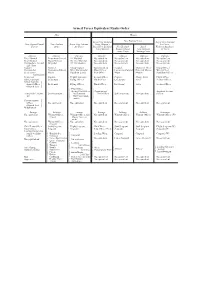
Armed Forces Equivalent Ranks Order Men Women Royal New Zealand New Zealand Army Royal New Zealand New Zealand Naval New Zealand Royal New Zealand Navy: Women’s Air Force: Forces Army Air Force Royal New Zealand New Zealand Royal Women’s Auxilliary Naval Service Women’s Royal New Zealand Air Force Army Corps Nursing Corps Officers Officers Officers Officers Officers Officers Officers Vice-Admiral Lieutenant-General Air Marshal No equivalent No equivalent No equivalent No equivalent Rear-Admiral Major-General Air Vice-Marshal No equivalent No equivalent No equivalent No equivalent Commodore, 1st and Brigadier Air Commodore No equivalent No equivalent No equivalent No equivalent 2nd Class Captain Colonel Group Captain Superintendent Colonel Matron-in-Chief Group Officer Commander Lieutenant-Colonel Wing Commander Chief Officer Lieutenant-Colonel Principal Matron Wing Officer Lieutentant- Major Squadron Leader First Officer Major Matron Squadron Officer Commander Lieutenant Captain Flight Lieutenant Second Officer Captain Charge Sister Flight Officer Sub-Lieutenant Lieutenant Flying Officer Third Officer Lieutenant Sister Section Officer Senior Commis- sioned Officer Lieutenant Flying Officer Third Officer Lieutenant Sister Section Officer (Branch List) { { Pilot Officer Acting Pilot Officer Probationary Assistant Section Acting Sub-Lieuten- 2nd Lieutenant but junior to Third Officer 2nd Lieutenant No equivalent Officer ant Navy and Army { ranks) Commissioned Officer No equivalent No equivalent No equivalent No equivalent No equivalent No -

Kings RAF Booklet
Combined Cadet Force Royal Air Force A Commissioning Aide Memoire for the Officer Cadre Version 1 “Where else could you learn to fly aerobatics, visit Royal Air Force Stations, tour foreign countries, play sports from local to international level, learn the skills to lead expeditions, become a target shooting marksman, gain your Duke of Edinburgh Awards, canoe through white water, assist your community, join a band, learn aviation subjects, go caving, parachute, climb, sail, ski...? These and much more are readily available to you as a member of the Air Cadet Organization.” Air Commodore Jon Chitty OBE. Introduction The school cadet organisation originates from 1859, when schools at Eton, Harrow, Rugby, Rossall, Felsted, Hurstpierpoint, Winchester and Tonbridge formed armed uniformed units as part of a national reserve to counter a perceived threat from abroad. By 1900, cadet units were established in over 100 schools across the country and in 1908, these units were re-titled the Officer Training Corps (OTC). In 1948, the OTC was renamed the Combined Cadet Force. The aim of the Combined Cadet Force is to provide a framework through which young people develop the qualities of team work, self-reliance, resourcefulness, leadership and responsibility. A weekly programme of military training is designed to give young people at King’s a chance to exercise responsibility and leadership, to provide them with knowledge of our defence forces, and to encourage those who might be interested in becoming officers of the Armed Services. Uniform members of the Combined Cadet Force will regularly stay on Royal Air Forces bases, therefore it is important that cadets are able to demonstrate an awareness of the structure and organisation of the Royal Air Force, its role in the defence of the United Kingdom and her interests and the operations in which the Royal Air Force are currently engaged. -

Naval Policy and Strategy in the Mediterranean
NAVAL POLICY AND STRATEGY IN THE MEDITERRANEAN Copyright of collection © 2000 Frank Cass & Co. Ltd Copyright of articles © 2000 contributors CASS SERIES: NAVAL POLICY AND HISTORY ISSN 1366–9478 Series Editor: Holger Herwig The series will publish, first and foremost, fresh quality manuscripts by research scholars in the general area of naval policy and history, without national or chronological limitations. Furthermore, it will from time to time issue collections of important articles as well as reprints of classic works. 1. Austro-Hungarian Naval Policy, 1904–1914 Milan N.Vego 2. Far Flung Lines: Studies in Imperial Defence in Honour of Donald Mackenzie Schurman Edited by Keith Neilson and Greg Kennedy 3. Maritime Strategy and Continental Wars Rear Admiral Raja Menon 4. The Royal Navy and German Naval Disarmament 1942–1947 Chris Madsen 5. Naval Strategy and Operations in Narrow Seas Milan N.Vego 6. The Pen and Ink Sailor: Charles Middleton and the King’s Navy, 1778–1813 John E.Talbott 7. The Italian Navy and Fascist Expansionism, 1935–1940 Robert Mallett 8. The Role of the Merchant Marine in Maritime Foreign Defence Policy Formation Edited by Greg Kennedy 9. Naval Strategy in Northeast Asia: Geo-strategic Goals, Policies and Prospects Duk-Ki Kim 10. Naval Policy and Strategy in the Mediterranean: Past, Present and Future Edited by John B.Hattendorf Copyright of collection © 2000 Frank Cass & Co. Ltd Copyright of articles © 2000 contributors NAVAL POLICY AND STRATEGY IN THE MEDITERRANEAN Past, Present and Future Edited by John B.Hattendorf US Naval War College FRANK CASS LONDON • PORTLAND, OR Copyright of collection © 2000 Frank Cass & Co. -

Equivalent Ranks of the British Services and U.S. Air Force
EQUIVALENT RANKS OF THE BRITISH SERVICES AND U.S. AIR FORCE RoyalT Air RoyalT NavyT ArmyT T UST Air ForceT ForceT Commissioned Ranks Marshal of the Admiral of the Fleet Field Marshal Royal Air Force Command General of the Air Force Admiral Air Chief Marshal General General Vice Admiral Air Marshal Lieutenant General Lieutenant General Rear Admiral Air Vice Marshal Major General Major General Commodore Brigadier Air Commodore Brigadier General Colonel Captain Colonel Group Captain Commander Lieutenant Colonel Wing Commander Lieutenant Colonel Lieutenant Squadron Leader Commander Major Major Lieutenant Captain Flight Lieutenant Captain EQUIVALENT RANKS OF THE BRITISH SERVICES AND U.S. AIR FORCE RoyalT Air RoyalT NavyT ArmyT T UST Air ForceT ForceT First Lieutenant Sub Lieutenant Lieutenant Flying Officer Second Lieutenant Midshipman Second Lieutenant Pilot Officer Notes: 1. Five-Star Ranks have been phased out in the British Services. The Five-Star ranks in the U.S. Services are reserved for wartime only. 2. The rank of Midshipman in the Royal Navy is junior to the equivalent Army and RAF ranks. EQUIVALENT RANKS OF THE BRITISH SERVICES AND U.S. AIR FORCE RoyalT Air RoyalT NavyT ArmyT T UST Air ForceT ForceT Non-commissioned Ranks Warrant Officer Warrant Officer Warrant Officer Class 1 (RSM) Chief Master Sergeant of the Air Force Warrant Officer Class 2b (RQSM) Chief Command Master Sergeant Warrant Officer Class 2a Chief Master Sergeant Chief Petty Officer Staff Sergeant Flight Sergeant First Senior Master Sergeant Chief Technician Senior Master Sergeant Petty Officer Sergeant Sergeant First Master Sergeant EQUIVALENT RANKS OF THE BRITISH SERVICES AND U.S. -

CIVIL AVIATION Air Marshals
TREATIES AND OTHER INTERNATIONAL ACTS SERIES 13-728 ________________________________________________________________________ CIVIL AVIATION Air Marshals Memorandum of Agreement Between the UNITED STATES OF AMERICA and HONDURAS Signed at Tegucigalpa July 18 and 28, 2013 with Annex NOTE BY THE DEPARTMENT OF STATE Pursuant to Public Law 89—497, approved July 8, 1966 (80 Stat. 271; 1 U.S.C. 113)— “. .the Treaties and Other International Acts Series issued under the authority of the Secretary of State shall be competent evidence . of the treaties, international agreements other than treaties, and proclamations by the President of such treaties and international agreements other than treaties, as the case may be, therein contained, in all the courts of law and equity and of maritime jurisdiction, and in all the tribunals and public offices of the United States, and of the several States, without any further proof or authentication thereof.” HONDURAS Civil Aviation: Air Marshals Memorandum of agreement signed at Tegucigalpa July 18 and 28, 2013; Entered into force July 28, 2013. With annex. MEMORANDUM OF AGREEMENT BETWEEN THE UNITED STATES OF AMERICA AND THE REPUBLIC OF HONDURAS CONCERNING THE DEPLOYMENT OF AIR MARSHALS ON BOARD AIRCRAFT e Uie Saes o Ameica a e euic o ouas (e "aies" o eig aies o e Coeio o Ieaioa Cii Aiaio oe a Cicago o 7 eceme 19 ( e "Cicago Coeio"; o esiig o comy wi oisios o Ae 17 o e Cicago Coeio icuig i aicua aagas 7 75 a 77 eeo; a o eig aies o e Coeio o Oeces a Ceai Oe Acs Commie o oa Aica sige a okyo o 1 Seeme 193 eey agee o aow o e eoyme o Ai Masas o e Uie Saes o Ameica a o e euic o ouas eseciey o aica a ae egage i Comiaio Ai Seices a ae oeae y a ai caie a eceie is Ai Oeao Ceiicae (AOC om oe ay a a ae oeae o om o ewee e eioies o e aies Article 1 Purpose and Definitions 1 e uose o is Ageeme is o eace e secuiy o Comiaio Ai Seices o om o ewee e eioies o e aies y oiig a amewok o e eoyme o Ai Masas o ceai suc igs 2. -

Office of Law Enforcement/Federal Air Marshal Service Is Responsible For
OFFICE OF LAW ENFORCEMENT/ FEDERAL AIR MARSHAL SERVICE TSA MANAGEMENT DIRECTIVE No. 3500.1 LEOSA APPLICABILITY AND ELIGIBILITY To enhance mission performance, TSA is committed to promoting a culture founded on its values of Integrity, Innovation and Team Spirit. REVISION: This revised directive supersedes TSA MD 3500.1, LEOSA Applicability and Eligibility, dated October 8, 2014. SUMMARY OF CHANGES: Section 4.A(2), Definitions, changed the word “would” to “could.” 1. PURPOSE: This directive provides TSA policy and procedures for the applicability and eligibility criteria of the Law Enforcement Officers Safety Act (LEOSA). 2. SCOPE: This directive applies to all TSA Components that have employees in law enforcement officer (LEO) positions who are separating or have separated from TSA as a LEO. 3. AUTHORITIES: A. DHS Directive 257-01, Law Enforcement Officers Safety Act B. DHS Instruction 257-01-001, Instruction Guide on the Law Enforcement Officers Safety Act C. Law Enforcement Officers Safety Act of 2004, Public Law 108-277, codified in 18 U.S.C. 926C D. Law Enforcement Officers Safety Act Improvements Act of 2010, Public Law 111-272 E. National Defense Authorization Act, Public Law 112-239 F. TSA MD 1100.88-1, Law Enforcement Position Standards and Hiring Requirements 4. DEFINITIONS: A. Good Standing: For the purposes of this directive, a TSA LEO shall be deemed as separating or having separated in good standing, unless at the time of their separation: (1) There was a determination made or action initiated to remove, or proposal to remove, the employee from Federal employment; (2) There was an investigation or un-adjudicated charge of misconduct against the employee that could have led to the employee’s removal; (3) The employee’s security clearance was suspended or revoked, or a proposal to suspend or revoke the clearance had been initiated or issued; or (4) The employee was the subject of a pending psychological fitness for duty evaluation or had been found to be not fit for duty based on psychological reasons. -

Federal Air Marshal Service (FAMS) Training Records
REQUEST FOR RECORDS DISPOSITION AUTHORITY (LEA VE BLANK) JOB NUMBER /V ~-I S 6 0 - /0 - Z- To NA nONAL ARCHIVES and RECORDS ADMINISTRA nON WASHINGTON, DC 20408 DATE RECEIVED fJ / J /z, 0/ o 1 FROM (Agency or establishment) NOTIFICATION TO AGENCY Department of Homeland Security (DHS) 2 MAJOR SUBDIVISION In accordance with the provisions of 44 USC Transportation Security Administration (TSA) -'303 th d ttl d 1-----------------------------1 -' a. e ISPOSIIOnreques . me u mg 3 MINOR SUBDIVISION amendments, ISapproved except for Items that may be marked DdlSposltlOn not approvedD or N/A Gwtrhdrawnfl in column 10 4 NAME OF PERSON WITH WHOM TO CONFER 5 TELEPHONE DATE ARCHIVIST OF THE UNITED STATES Anthony Ferguson or (571) 227-156411170 Troy Manigault TSARecords@dhs gOY 6 AGENCY CERTIFICATION I hereby certify that I am authorized to act for this agency in matters pertammg to the disposinon of ItS records and that the records proposed for disposal on the attached Z page(s) are not needed now for the business of this agency or will not be needed after the retention penods specified, and that written concurrence from the General Accountmg Office, under the provisions of Title 8 of the GAO manual for GUidance of Federal Agencies, IZI ISnot required, D ISattached, or 0 has been requested SIGNATURE~F AGE ~EPRES TAT;JIVE I--fiTLE Director, Office of Informanon Management Programs T roy K Man au It (Actmg Records Management Officer) , 10 ACTION TAKEN 7 Item 8 DESCRIPTION oytfEM A1D PRopci_EECD D/~~POSITION 9 GRS OR (NARA USE ONLY) No ./' ~ SUPERSEDED -

GAO-21-595, COVID-19: Federal Air Marshal Service Should Document
United States Government Accountability Office Report to Congressional Committees June 2021 COVID-19 Federal Air Marshal Service Should Document Its Response to Cases and Facilitate Access to Testing GAO-21-595 June 2021 COVID-19 Federal Air Marshal Service Should Document Its Response to Cases and Facilitate Access to Testing Highlights of GAO-21-595, a report to congressional committees Why GAO Did This Study What GAO Found In the U.S. there have been over 29 The U.S. Federal Air Marshal Service (FAMS), within the Department of million cumulative reported cases of Homeland Security (DHS), reported 345 cases of COVID-19 among employees, COVID-19 and about 524,000 reported as of January 31, 2021. deaths, as of March 23, 2021. Public health officials have recommended Federal Air Marshal Service’s Reported Cases of COVID-19, as of January 31, 2021 social distancing and other steps to reduce the spread of the disease, but air marshals often work on planes where they cannot fully adopt these measures. The CARES Act included a provision for GAO to conduct monitoring and oversight of the federal government’s response to the COVID- 19 pandemic. This report examines (1) how many air marshals have been diagnosed with COVID-19; (2) FAMS’s steps to protect air marshals’ health; and (3) how FAMS adapted its Note: Cases included in the figure were confirmed with a positive COVID-19 test and reported to the operations during the pandemic. Federal Air Marshal Service by the employee. GAO analyzed FAMS data on COVID- To protect air marshals from COVID-19, FAMS provided supplies like N95 masks 19 cases among employees, reviewed and implemented new telework and leave policies. -

Royal Air Force Historical Society
ROYAL AIR FORCE HISTORICAL SOCIETY JOURNAL 49 2 The opinions expressed in this publication are those of the contributors concerned and are not necessarily those held by the Royal Air Force Historical Society. First published in the UK in 2010 by the Royal Air Force Historical Society All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical including photocopying, recording or by any information storage and retrieval system, without permission from the Publisher in writing. ISSN 1361 4231 Printed by Windrush Group Windrush House Avenue Two Station Lane Witney OX28 4XW 3 ROYAL AIR FORCE HISTORICAL SOCIETY President Marshal of the Royal Air Force Sir Michael Beetham GCB CBE DFC AFC Vice8President Air 2arshal Sir Frederick Sowrey KC3 C3E AFC Committee Chairman Air 7ice82arshal N 3 3aldwin C3 C3E 7ice8Chairman -roup Captain 9 D Heron O3E Secretary -roup Captain K 9 Dearman FRAeS 2embership Secretary Dr 9ack Dunham PhD CPsychol A2RAeS Treasurer 9 3oyes TD CA 2embers Air Commodore - R Pitchfork 23E 3A FRAes ,in Commander C Cummin s :9 S Cox Esq 3A 2A :A72 P Dye O3E 3Sc(En ) CEn AC-I 2RAeS :-roup Captain 2 I Hart 2A 2A 2Phil RAF :,in Commander C Hunter 22DS RAF Editor & Publications ,in Commander C - 9efford 23E 3A 2ana er :Ex Officio 4 CONTENTS THE PRE8,AR DE7E.OP2ENT OF DO2INION AIR 7 FORCES by Sebastian Cox ANS,ERIN- THE @O.D COUNTRABSB CA.. by , Cdr 11 Colin Cummin s ‘REPEAT, PLEASE!’ PO.ES AND CCECHOS.O7AKS IN 35 THE 3ATT.E OF 3RITAIN by Peter Devitt A..IES AT ,ARE THE RAF AND THE ,ESTERN 51 EUROPEAN AIR FORCES, 1940845 by Stuart Hadaway 2ORNIN- G&A 76 INTERNATIONA. -

The Federal Air Marshal Service Has Sufficient Policies and Procedures for Addressing Misconduct
The Federal Air Marshal Service Has Sufficient Policies and Procedures for Addressing Misconduct September 13, 2017 OIG-17-104 DHS OIG HIGHLIGHTS The Federal Air Marshal Service Has Sufficient Policies and Procedures for Addressing Misconduct September 13, 2017 What We Found Why We Did The Federal Air Marshal Service (FAMS) is a division of the Transportation Security Administration (TSA). FAMS is This Audit responsible for promoting confidence in civil aviation by deploying Federal air marshals to detect, deter, and defeat The TSA Office of Inspection hostile acts targeting transportation systems. Because of its Accountability Act of 2015, law enforcement mission, FAMS developed a series of Public Law 114-53, required unique policies and procedures to address conduct related us to review FAMS personnel to air marshals’ specific duties, while also operating under policies and procedures for the purview of TSA’s conduct code and misconduct policies identifying misuse of and procedures. Government resources and existing code of conduct or FAMS has sufficient policies and procedures to establish integrity policies with respect expectations for appropriate conduct, identify misuse of to instances of misconduct. Government resources, and address misconduct allegations. FAMS’ policies specifically require all employees to report suspected misconduct. Additionally, TSA and What We FAMS have a systematic and multilayered process for handling FAMS misconduct issues, which includes review Recommend of misconduct allegations by two separate and independent offices. This report contains no recommendations. For Further Information: FAMS Response Contact our Office of Public Affairs at (202) 254-4100, or email us at [email protected] FAMS had no additional comments, and TSA stated that it will continue to apply its policies and procedures to help ensure conduct issues are addressed appropriately. -

AIR CHIEF MARSHALS: AUGUST 2021 July 2019: Air Chief Marshal
AIR CHIEF MARSHALS: SEPTEMBER 2021 July 2019: Air Chief Marshal Sir Michael Wigston: Chief of the Air Staff, July 2019 (2/1968; 53) AIR MARSHALS: SEPTEMBER 2021 April 2018: Air Marshal Edward J. Stringer December 2018: Air Marshal Richard J. Knighton: Deputy Chief of the Defence Staff (Military Capability), December 2018 (11/1969; 51) March 2019: Air Marshal Susan C. Gray: Director-General, Defence Safety Authority, March 2019 (10/1963; 57) May 2019: Air Marshal Gerald M.D. Mayhew: Deputy Commander, Operations, Air Command May 2019 (2/1969; 52) Air Marshal Andrew M. Turner: Deputy Commander, Capability, Air Command and Air Member for Personnel and Capability, May 2019 (1967; 53) February 2021: Air Marshal Martin E. Sampson: Defence Senior Advisor, Middle East, February 2021 April 2021: Air Marshal Ian D. Gale: Director-General, Defence Academy and Joint Force Development, April 2021 AIR VICE-MARSHALS: SEPTEMBER 2021 June 2016: (Pers.) Air Vice-Marshal Garry Tunnicliffe: Deputy Commandant, Royal College of Defence Studies, April 2019 (10/1966; 54 ) December 2016: Air Vice-Marshal Steven J. Shell: Director, Military Aviation Authority, December 2018-December 2021 July 2017: Air Vice-Marshal Warren A.W. James: to retire October 2017: (Intell.) Air Vice-Marshal Michael P. Hart February 2018: (Eng.) Air Vice-Marshal Christopher J. Moore: to retire Air Vice-Marshal Ian F. Vallely Air Vice-Marshal John J. Stringer: professional placement at Rebellion Defense, May 2021 ( 11/1969; 51) July 2018: Air Vice-Marshal Harvey Smyth: Director, Space, M.O.D., February 2020 October 2018: Air Vice-Marshal Ian W. Duguid: Chief of Staff, Operations, Air Command, October 2018, and AOC, No.11 Group, November 2018-December 2021 (12/1966; 54) December 2018: Air Vice-Marshal Simon D. -

ISHIRTSI Had Slowed the Their FIELD MARSHAL SIR ARCHI- up Flow of Supplies the Attitude Might Be Unofficially During World War
Boris King Reported One of Greatest War Conferences in Crucial * Red Army Advances ———— Allied t Here ♦ S History__ Maps Strateay Asking Hitler for Cee of the greatest war confer- ences the world ever has seen was Nazi Attacks going on in Washington today with Despite in Crisis the United States and Great Britain Troops putting into final shape the grand Near Novorossisk strategy of the offensives in both Gestapo Chief Himmler European and Pacific theaters of war. Heavy Artillery Said to Be Hurrying Barrage The highest names in both the Presages Big Push To Sofia After Plea American and British war machines, headed by President Roosevelt and Toward Black Sea By the Associated press. Prime Minister Churchill, were LONDON, May 14.—King Boris gathered around the conference By EDDY GILMORE, of Bulgaria has sent an urgent table. Every phase of operations is Associated Press War Correspondent. appeal to Adolf Hitler for addi- represented in the group that in- MOSCOW. May 14.—Battling cludes men with wide tional secret units as experience in against stubborn German re- police pro- the United Nations’ tection internal dis- operations in sistance in the Kuban, the Red against the Far East and India. turbances, reports reaching Al- Army has advanced in some sec- Eight of Great Britain's most im- lied said today. tors and captured additional governments portant and influential war leaders These advices said it was under- lines northeast of the Black Sea accompanied Mr. Churchill to stood that the chief him- of Gestapo Washington to plan the final port Novorossisk, dispatches Heinrich was self, Himmler, hurry- strategy with seven of America's from the front said today.