BOARD of STUDIES MEETING Master of Computer Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MCA III Sem Syllabus
SRI VENKATESWARA UNIVERISTY, TIRUPATI Department of Computer Applications ADOPTION OF CBCS SYSTEM FOR MCA PROGRAMME WITH EFFECT FROM 2016 – 2017 MCA IIIrd Semester Syllabus MCA 301: COMPUTER ORIENTED OPERATIONS RESEARCH UNIT-I Origin and Development of Operations Research - Nature and Scope of Operations Research-Models and Modeling in Operations Research- Computer Software for Operations Research-Applications of Operations Research-Linear Programming-Model formulation, Graphical Method, Simplex Method, Duality, Revised Simplex Method-Integer Programming Problem using Excel solver. UNIT-II Transportation Problem–Transshipment Model–Assignment Problem–Goal Programming - Network Techniques: Shortest-Path Model, Minimum Spanning Tree Problem, Maximum Flow Problem. UNIT-III Non-Linear Programming-Unconstrained Optimization, Constrained Optimization with and without inequalities-Kuhn-Tucker Conditions-Graphical Solution of Non–Linear Programming Problem-Quadratic Programming-Separable Programming-Convex and Non- Convex Programming. UNIT-IV Queuing Theory-Basic structure of Queuing System-Classification of Queuing Models- Single-Server Queuing Models-Multi-Server Queuing Models-Applications of Queuing Theory-Simulation-Monte-Carlo Simulation-Role of Computers in Simulation-Applications of Simulation. UNIT – V Decision Theory-Steps in Decision Theory Approach-Decision-Making Environments- Decision Making under Certainty, Uncertainty and Risk-Decision Tree Analysis-Game Theory. Text Books: 1. Taha H.A., Operations Research: An Introduction, Prentice-Hall -

Syllabus 2016-2019
PSGR KRISHNAMMAL COLLEGE FOR WOMEN College of Excellence (An Autonomous Institution, Affiliated to Bharathiar University) (Reaccredited with ‘A’ Grade by NAAC, An ISO 9001:2008 Certified Institution) Peelamedu, Coimbatore-641004 DEPARTMENT OF INFORMATION TECHNOLOGY CHOICE BASED CREDIT SYSTEM & OUTCOME BASED EDUCATION SYLLABUS BACHELOR OF INFORMATION TECHNOLOGY (B.Sc IT) 2016 – 2019 PSGR KRISHNAMMAL COLLEGE FOR WOMEN College of Excellence (An Autonomous Institution, Affiliated to Bharathiar University) (Reaccredited with ‘A’ Grade by NAAC, An ISO 9001:2008 Certified Institution) Peelamedu, Coimbatore-641004 PROGRAMME OUTCOMES After completion of the programme, the student will be able to PO1 : To provide broad range of information technology skills like technical, logical, analytical thinking and leadership quality. PO2 : To meet the industry standards and attain the project development capabilities to obtain placements. PO3 : To promote creativity, capability and competence through IT soft skills. PO4 : To make them world class professionals in IT and produce women entrepreneurs to increase more employability. PROGRAMME SPECIFIC OUTCOME The students at the time of graduation will PSO1 : Professionally equipped in the areas of programming, Cloud Infrastructure, Internet of Things, Mobile Application Development and to be ease with the recent technologies of various domain. PSO2 : Apply the knowledge of technology and soft skills to carry out societal software development. PSO3 : The ability to employ modern computer languages and applications -
First Year Curriculum Structure (W.E.F
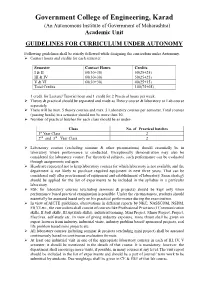
Government College of Engineering, Karad (An Autonomous Institute of Government of Maharashtra) Academic Unit GUIDELINES FOR CURRICULUM UNDER AUTONOMY Following guidelines shall be strictly followed while designing the curriculum under Autonomy. Ø Contact hours and credits for each semester Semester Contact Hours Credits I & II 60(30+30) 50(25+25) III & IV 60(30+30) 50(25+25) V & VI 60(30+30) 40(25+15) Total Credits 140(75+65) 1 credit for Lecture/ Tutorial hour and 1 credit for 2 Practical hours per week. Ø Theory & practical should be separated and made as Theory course & laboratory or Lab course separately. Ø There will be max. 5 theory courses and max. 5 Laboratory courses per semester. Total courses (passing heads) in a semester should not be more than 10. Ø Number of practical batches for each class should be as under- Class No. of Practical batches 1st Year Class 2 2nd and 3rd Year Class 2 Ø Laboratory courses (excluding seminar & other presentations) should essentially be in laboratory where performance is conducted. Exceptionally demonstration may also be considered for laboratory course. For theoretical subjects, such performance can be evaluated through assignments and quiz. Ø Heads are requested not to keep laboratory courses for which laboratory is not available and the department is not likely to purchase required equipment in next three years. That can be considered only after procurement of equipment and establishment of laboratory. Same strategy should be applied for the list of experiments to be included in the syllabus in a particular laboratory. Ø ESE for laboratory courses (excluding seminars & projects) should be kept only when performance based practical examination is possible. -

M.Sc. Computer Science SEMESTER –I
Curriculum for M.Sc Computer Science FATIMA COLLEGE (AUTONOMOUS) Re-Accredited with “A” Grade by NAAC (3rd Cycle) 74th Rank in India Ranking 2020 (NIRF) by MHRD Maryland, Madurai- 625 018, Tamil Nadu, India NAME OF THE DEPARTMENT : COMPUTER SCIENCE NAME OF THE PROGRAMME : M.SC PROGRAMME CODE : PSCS ACADEMIC YEAR : 2020 - 21 1 Curriculum for M.Sc Computer Science FATIMA COLLEGE (AUTONOMOUS), MADURAI-18 DEPARTMENT OF COMPUTER SCIENCE MAJOR CORE – 70 CREDITS PROGRAMME CODE:PSCS COURSE CIA ESE TOT. S.No SEM. COURSE TITLE HRS CREDITS CODE Mks Mks MKs Advanced 5 4 1. 19PG1B1 40 60 100 Programming in Java Distributed 4 4 2. 19PG1B2 40 60 100 Operating Systems Object Oriented 4 4 3. 19PG1B3 40 60 100 Software Engineering I Theory of 4 4 4. 19PG1B4 40 60 100 Computation Lab I – Advanced 5 3 5. 19PG1B5 40 60 100 Programming In Java 19PG1B6 Lab II – Operating 5 3 40 60 100 6. System 19PG2B7 Extreme 4 4 40 60 100 7. Programming – Asp.Net 19PG2B8 Mobile Application 4 4 40 60 100 8. Development Using Android Studio 19PG2B9 Design and Analysis 4 4 40 60 100 9. II of Algorithms 19PG2B10 Lab III – Extreme 5 3 40 60 100 10. Programming – Asp.Net 19PG2B11 Lab IV – Mobile 5 3 40 60 100 Application 11. Development using Android Studio 19PG3B12 Digital Image 5 5 50 50 100 12. Processing 19PG3B13 Data Mining and 5 5 40 60 100 13. Data Warehousing III 19PG3B14 Lab V – Digital 5 3 40 60 100 14. Image Processing 19PG3B15 Lab VI– Data Mining 5 3 40 60 100 15. -
Guidelines for R17 B
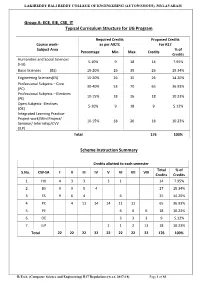
LAKIREDDY BALI REDDY COLLEGE OF ENGINEERING (AUTONOMOUS), MYLAVARAM Group A: ECE, EIE, CSE, IT Typical Curriculum Structure for UG Program Required Credits Proposed Credits Course work- as per AICTE For R17 Subject Area % of Percentage Min. Max. Credits Credits Humanities and Social Sciences 5-10% 9 18 14 7.95% (HU) Basic Sciences (BS) 15-20% 26 35 26 15.34% Engineering Sciences(ES) 15-20% 26 35 26 14.20% Professional Subjects – Core 30-40% 53 70 65 36.93% (PC) Professional Subjects – Electives 10-15% 18 26 18 10.23% (PE) Open Subjects- Electives 5-10% 9 18 9 5.12% (OE) Integrated Learning Practice- Project work/Mini Project/ 10-15% 18 26 18 10.23% Seminar/ Internship/CVV (ILP) Total 176 100% Scheme Instruction Summary Credits allotted to each semester Total % of S.No. CW-SA I II III IV V VI VII VIII Credits Credits 1. HU 4 3 3 3 1 14 7.95% 2. BS 9 9 5 4 27 15.34% 3. ES 9 6 4 6 25 14.20% 4. PC 4 11 14 14 11 11 65 36.93% 5. PE 6 6 6 18 10.23% 6. OE 3 3 3 9 5.12% 7. ILP 2 1 2 13 18 10.23% Total 22 22 22 22 22 22 22 22 176 100% B.Tech. (Computer Science and Engineering) R17 Regulations (w.e.f. 2017-18) Page 1 of 83 LAKIREDDY BALI REDDY COLLEGE OF ENGINEERING (AUTONOMOUS), MYLAVARAM List of Subjects / Course work / Subject Area Humanities and Social Sciences (HU)-14 credits Basic Sciences (BS)-26 Credits S.No Course Title Credits S.No Course Title Credits 1 Professional Communication-I 3 1 Applied Mathematics-I 4 2 Professional Communication-II 3 2 Applied Mathematics-II 4 3 Environmental Science 3 3 Applied Mathematics-III 4 Engineering -

KMM-MCA Syllabus-March 2015
DEPARTMENT OF COMPUTER SCIENCE MCA SYLLABUS (WITH EFFECT FORM 2015-2016) MCA 101 DISCRETE MATHEMATICS Unit-I: Function: Definition, type of functions, one to one, into and onto function, inverse function, composition of functions, recursively defined functions. Algebraic Structures: Definition, Properties, types: Semi Groups, Monoid, Groups, Abelian group, properties of groups, Subgroup, cyclic groups, Cosets, factor group, Permutation groups, Normal subgroup, Homomorphism and isomorphism of Groups, example and standard results, Rings and Fields: definition and standard results. Unit-II: Posets, Hasse Diagram and Lattices: Introduction, ordered set, Hasse diagram of partially, ordered set, isomorphic ordered set, well ordered set, properties of Lattices, and complemented lattices. Combinatorics: Basic Counting Technique, Pigeon-hole Principle, Recurrence Relation, Generating function, Polya's Counting Theorem Paths and Circuits : Isomorphism, Subgraphs, Walks, Paths and Circuits, Connected and disconnected graphs, Euler graphs, Operations on graphs, Hamiltonian graphs, Travelling salesman problem. Unit-III: Introduction and Basic Concepts : Definition, Representation of graphs, Finite and infinite graphs, Directed graphs, Incidence and degree, Bipartite graph, Planar graphs, Matrix representation of graphs, Applications of graph in computer science. Graphs: Simple graph, multi graph, graph terminology, representation of graphs, Bipartite, Regular, Planar and connected graphs, connected components in a graph, Euler graphs, Hamiltonian -

Course Handout
DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING COURSE HANDOUT PART-A Name of Course Instructor : Mr. L V Krishna rao Course Name & Code : Design and Analysis of Algorithms- 17CI08 L-T-P Structure : 3-0-0 Credits : 3 Program/Sem/Sec : B.Tech., CSE., IV-Sem., Sections- A A.Y : 2019-20 PRE-REQUISITE: : Basic of Programming language and Data structure COURSE EDUCATIONAL OBJECTIVES (CEOs): Students undergoing this course are expected to: Explain the fundamental concepts of various algorithm design techniques. Make the students familiar to conduct performance evaluation of algorithms. Expertise the students with the various existing algorithm design techniques .Motivate the students to design a new algorithms for various problems and introduce the concepts of P&NP-class problems. COURSE OUTCOMES (COs): At the end of the course, students are able to CO 1 Identify the basic properties and analysis methods of algorithms and design divide and conquer paradigm for solving a few example problems and analyze them. CO 2 Design Greedy algorithms for knapsack problem, minimum cost spanning tree,single source shortest path problem and analyze them. CO 3 Apply dynamic programming paradigm to solve travelling sales person problem,0/1 knapsack problem,Optimal binary search tree. CO 4 Apply Backtracking search methods on state space trees for few example problems CO 5 Analyze branch and bound search methods through problems such as 0/1 knapsack problem, Travelling salesperson problem. COURSE ARTICULATION MATRIX(Correlation between COs, POs & PSOs): PO PO1 PO3 PO4 PO5 PO6 PO7 PO8 PO9 PO10 PO11 PO12 PSO1 PSO2 PSO3 COs 2 CO1 3 3 2 - - - - - - - - - 3 CO2 2 3 1 - - - - - - - - - 3 CO3 2 3 1 - - - - - - - - - 3 CO4 2 3 1 - - - - - - - - - 1 CO5 2 3 1 - - - - - - - - - 1 Note: Enter Correlation Levels 1 or 2 or 3. -

B.Sc Information Technology 2018-2021
B.Sc Information Technology 2018-2021 PSGRKRISHNAMMALCOLLEGE FOR WOMEN College of Excellence An Autonomous Institution - Affiliated to BharathiarUniversity Reaccredited with ‘A’ Grade by NAAC An ISO 9001:2015 Certified Institution Peelamedu, Coimbatore – 641 004 DEPARTMENT OF INFORMATION TECHNOLOGY PROGRAMME EDUCATIONAL OBJECTIVES Graduates will have successful careers in computer fields or will be able to successfully pursue higher studies. Graduates will apply their technical knowledge and skills to develop and implement solutions for the problems that accomplish goals to the industry, academic, government or research area. Contribute effectively to the Computing Profession by fostering effective interaction, ethical practices and communication skills, while pursuing education through lifelong learning. PROGRAMME OBJECTIVE To provide broad range of information technology skills like technical, logical, analytical thinking and leadership quality To meet the industry standards and attain the project development capabilities to obtain placements To promote creativity, capability and competence through IT soft skills To make them world class professionals in IT and produce women entrepreneurs to increase more employability. PSGRKRISHNAMMALCOLLEGE FOR WOMEN Programme& Branch: B.Sc Information Technology Scheme of Examination (Applicable to students admitted during the academic year 2018 – 2019 Batch: 2018-2021) (Semester I - VI) Examination Marks Credits l a Title of paper CA ESE Tot al Part week Code hours hours / Subject Subject -

Attachment=14607
www.vidyarthiplus.com DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING QUESTION BANK SUBJECT CODE: CS2055 Software Quality Assurance BRANCH&YEAR: CSE/IV SEMESTER: VIII UNIT – I PART – A 1. Define quality. 2. What is quality cost? 3. What are the building blocks of total quality management? 4. What are the 7 QC tools? 5. What is business process reengineering? 6. Define Quality Function Deployment. 7. Define six sigma. 8. What are the uses of arrow diagram? 9. What are the different dimensions of quality? 10. What is external failure? 11. What are the uses of control charts? 12. Steps involved in the bench marking process. 13. What is statistical process control? 14. Define TQM. 15. What is quality planning? 16. What is quality improvement? 17. What is quality management? 18. What are the benefits of QFD? 19. What is internal benchmarking>? 20. What are the four p’s focused on effective software project management? PART – B 1. Explain Quality Function Deployment in detail. 2. Describe in detail the standardization procedure of benchmarking. 3. Explain how software quality assurance is ensured in a software firm. 4. Explain the seven basic quality control tools in detail. www.vidyarthiplus.com www.vidyarthiplus.com UNIT – II PART - A 1. Define software configuration management. 2. What are the different measurable characteristics of an OO design? 3. What are CASE tools? 4. What are function-oriented metrics? 5. Define white box testing? 6. What are the steps implied by statistical quality assurance? 7. Define Verification and Validation. 8. What is RMM plan? 9. What are the qualities team leaders should posses? 10. -
CSE Course Structure and Syllabus
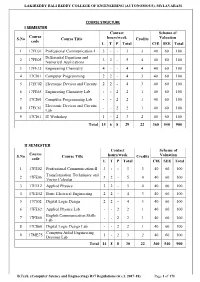
LAKIREDDY BALI REDDY COLLEGE OF ENGINEERING (AUTONOMOUS), MYLAVARAM COURSE STRUCTURE I SEMESTER Contact Scheme of Course S.No Course Title hours/week Credits Valuation code L T P Total CIE SEE Total 1 17FE01 Professional Communication-I 3 - - 3 3 40 60 100 Differential Equations and 2 17FE05 3 2 - 5 4 40 60 100 Numerical Applications 3 17FE15 Engineering Chemistry 4 - - 4 4 40 60 100 4 17CI01 Computer Programming 2 2 - 4 3 40 60 100 5 17EC02 Electronic Devices and Circuits 2 2 - 4 3 40 60 100 6 17FE65 Engineering Chemistry Lab - - 2 2 1 40 60 100 7 17CI60 Computer Programming Lab - - 2 2 1 40 60 100 Electronic Devices and Circuits 8 17EC61 - - 2 2 1 40 60 100 Lab 9 17CI61 IT Workshop 1 - 2 3 2 40 60 100 Total 15 6 8 29 22 360 540 900 II SEMESTER Contact Scheme of Course S.No Course Title hours/week Credits Valuation code L T P Total CIE SEE Total 1 17FE02 Professional Communication-II 3 - - 3 3 40 60 100 Transformation Techniques and 2 17FE06 3 2 - 5 4 40 60 100 Vector Calculus 3 17FE12 Applied Physics 3 2 - 5 4 40 60 100 4 17EE52 Basic Electrical Engineering 2 2 - 4 3 40 60 100 5 17CI02 Digital Logic Design 2 2 - 4 3 40 60 100 6 17FE62 Applied Physics Lab - - 2 2 1 40 60 100 English Communication Skills 7 17FE60 - - 2 2 1 40 60 100 Lab 8 17CS60 Digital Logic Design Lab - - 2 2 1 40 60 100 Computer Aided Engineering 9 17ME75 1 - 2 3 2 40 60 100 Drawing Lab Total 14 8 8 30 22 360 540 900 B.Tech. -
Kmm Institute of Postgraduate Studies
Page 1 of 25 KMM INSTITUTE OF POSTGRADUATE STUDIES (Affiliated to S.V.University, Tirupati) MASTER OF COMPUTER APPLICATIONS (MCA) (With effect from the academic year 2011-12) (Common for both the students of CBCS and Non-CBCS) MCA 101: DISCRETE MATHEMATICAL STRUCTURES UNIT I: Logic and Proof, Sets and Functions – Logic Propositional equivalence, Predicates and Quantities, Nested quantifiers, Methods of Proof, sets, set operations, functions. UNIT II: The Integers and Division, Integers and Algorithms, Applications of Number theory, Mathematical reasoning, Induction and Recursion – Proof strategy, Sequences and Summations, Mathematical induction. Recursive definitions and Structural induction, Recursive algorithms, Program correctness. UNIT III:- The basics of counting, the pigeonhole principle, Permatations and Combinations, Binomial coefficients, Generalized permutations and combinations, Generating permutations and combinations, Recurrence relations, Solving recurrence relations. UNIT IV:- Relations – Relations and their properties, n-ary Relations and their applications, Representing Relations, Closures of relations, Equivalence relations, Partial orderings. Languages and Grammers, Finite state machines with output, Finite state machines with no output, Language recognition, Turing machines. UNIT V:- Graphs – Introduction to Graphs, Graph terminology, Representing graphs and Graph isomorphism, Connectivity, Euler and Hamilton Faths, Shortest Path problems, Planar graphs, Graph coloring. Text Book: Rosen K.H. Discrete Mathematics and its Applications, 5th edition, Tata McGraw – Hills, 2003. REFERENCE BOOKS: 1. Johnson Baugh R, and Carman R, Discrete mathematics, 5th edition, Person Education, 2003. 2. Kolman B, Busoy R.C, and Ross S.C, Discrete Mathematical Structures, 5th edition, Pretitice – Hall, 2004. 3. Mott J.L, Kandel A, and Bake T.P, Discrete Mathematics for Computer Scientists & Mathematicians, 2nd edition, Prentice-Hall of India, 2002. -
Course Outcomes (Subject Wise)
MALLA REDDY COLLEGE OF ENGINEERING & TECHNOLOGY (Autonomous Institution – UGC, Govt. of India) (Affiliated to JNTUH, Hyderabad, Approved by AICTE - Accredited by NBA & NAAC – ‘A’ Grade - ISO 9001:2015 Certified) Maisammaguda, Dhulapally (Post Via. Hakimpet), Secunderabad – 500100, Telangana State, INDIA. DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING SUBJECT WISE-COURSE OUTCOMES II Year I Semester Probability and Statistics CO1: students will be able to analyze the basic principles of probability CO2: students will be able to apply conditional probability 8 CO3: students have ability to apply the basic discrete distributions (Binomial) 1 CO4: students have ability to apply the basic continuous distributions (Uniform) A3000 Statistics CO5: students will be able to collect, organize, and represent data, and be able to Probability and Probability and recognize and describe relationships Mathematical Foundations of Computer Science Co1: Students will be able to analyze the validity of argument by using propositional and predicate calculus. Co2: Students will be able to apply basic counting techniques to solve the combinatorial problems. 4 Computer Computer Co3: Students will be able to understand the relationship between sequences and 2 recurrence relations and able to solve recurrence relations. A3050 Co4: Students will be able to apply sets, relations and digraphs to solve applied Science problems. Mathematical Mathematical Co5: Students will be able to use basic concepts of graph theory and problems efficiently.. Foundations of Data Structures CO1: Students will be able to analyze algorithms and to determine algorithm correctness, time and efficiency class. CO2: Students will be able to apply various searching and sorting techniques to solve computing problems. CO3: Students can Demonstrate abstract properties of various data structures such 2 as stacks, queues, lists, trees and graphs.