Procedure Call Standard for the Arm Architecture Release 2020Q2
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Strict Protection for Virtual Function Calls in COTS C++ Binaries
vfGuard: Strict Protection for Virtual Function Calls in COTS C++ Binaries Aravind Prakash Xunchao Hu Heng Yin Department of EECS Department of EECS Department of EECS Syracuse University Syracuse University Syracuse University [email protected] [email protected] [email protected] Abstract—Control-Flow Integrity (CFI) is an important se- these binary-only solutions are unfortunately coarse-grained curity property that needs to be enforced to prevent control- and permissive. flow hijacking attacks. Recent attacks have demonstrated that existing CFI protections for COTS binaries are too permissive, While coarse-grained CFI solutions have significantly re- and vulnerable to sophisticated code reusing attacks. Accounting duced the attack surface, recent efforts by Goktas¸¨ et al. [9] for control flow restrictions imposed at higher levels of semantics and Carlini [10] have demonstrated that coarse-grained CFI is key to increasing CFI precision. In this paper, we aim to provide solutions are too permissive, and can be bypassed by reusing more stringent protection for virtual function calls in COTS large gadgets whose starting addresses are allowed by these C++ binaries by recovering C++ level semantics. To achieve this solutions. The primary reason for such permissiveness is the goal, we recover C++ semantics, including VTables and virtual lack of higher level program semantics that introduce certain callsites. With the extracted C++ semantics, we construct a sound mandates on the control flow. For example, given a class CFI policy and further improve the policy precision by devising two filters, namely “Nested Call Filter” and “Calling Convention inheritance, target of a virtual function dispatch in C++ must Filter”. -

Tricore Architecture Manual for a Detailed Discussion of Instruction Set Encoding and Semantics
User’s Manual, v2.3, Feb. 2007 TriCore 32-bit Unified Processor Core Embedded Applications Binary Interface (EABI) Microcontrollers Edition 2007-02 Published by Infineon Technologies AG 81726 München, Germany © Infineon Technologies AG 2007. All Rights Reserved. Legal Disclaimer The information given in this document shall in no event be regarded as a guarantee of conditions or characteristics (“Beschaffenheitsgarantie”). With respect to any examples or hints given herein, any typical values stated herein and/or any information regarding the application of the device, Infineon Technologies hereby disclaims any and all warranties and liabilities of any kind, including without limitation warranties of non- infringement of intellectual property rights of any third party. Information For further information on technology, delivery terms and conditions and prices please contact your nearest Infineon Technologies Office (www.infineon.com). Warnings Due to technical requirements components may contain dangerous substances. For information on the types in question please contact your nearest Infineon Technologies Office. Infineon Technologies Components may only be used in life-support devices or systems with the express written approval of Infineon Technologies, if a failure of such components can reasonably be expected to cause the failure of that life-support device or system, or to affect the safety or effectiveness of that device or system. Life support devices or systems are intended to be implanted in the human body, or to support and/or maintain and sustain and/or protect human life. If they fail, it is reasonable to assume that the health of the user or other persons may be endangered. User’s Manual, v2.3, Feb. -

CS 0449: Introduction to Systems Software
CS 0449: Introduction to Systems Software Jonathan Misurda Computer Science Department University of Pittsburgh [email protected] http://www.cs.pitt.edu/∼jmisurda Version 3, revision 1 Last modified: July 27, 2017 at 1:33 P.M. Copyright © 2017 by Jonathan Misurda This text is meant to accompany the course CS 0449 at the University of Pittsburgh. Any other use, commercial or otherwise, is prohibited without permission of the author. All rights reserved. Java is a registered trademark of Oracle Corporation. This reference is dedicated to the students of CS 0449, Fall 2007 (2081). Their patience in dealing with a changing course and feedback on the first version of this text was greatly appreciated. Contents Contents i List of Figures v List of Code Listings vii Preface ix 1 Pointers 1 1.1 Basic Pointers . 2 1.1.1 Fundamental Operations . 2 1.2 Passing Pointers to Functions . 4 1.3 Pointers, Arrays, and Strings . 5 1.3.1 Pointer Arithmetic . 6 1.4 Terms and Definitions . 7 2 Variables: Scope & Lifetime 8 2.1 Scope and Lifetime in C . 9 2.1.1 Global Variables . 11 2.1.2 Automatic Variables . 12 2.1.3 Register variables . 13 2.1.4 Static Variables . 13 2.1.5 Volatile Variables . 16 2.2 Summary Table . 17 2.3 Terms and Definitions . 17 ii Contents 3 Compiling & Linking: From Code to Executable 19 3.1 The Stages of Compilation . 19 3.1.1 The Preprocessor . 20 3.1.2 The Compiler . 21 3.1.3 The Linker . 22 3.2 Executable File Formats . -

IAR C/C++ Compiler Reference Guide for V850
IAR Embedded Workbench® IAR C/C++ Compiler Reference Guide for the Renesas V850 Microcontroller Family CV850-9 COPYRIGHT NOTICE © 1998–2013 IAR Systems AB. No part of this document may be reproduced without the prior written consent of IAR Systems AB. The software described in this document is furnished under a license and may only be used or copied in accordance with the terms of such a license. DISCLAIMER The information in this document is subject to change without notice and does not represent a commitment on any part of IAR Systems. While the information contained herein is assumed to be accurate, IAR Systems assumes no responsibility for any errors or omissions. In no event shall IAR Systems, its employees, its contractors, or the authors of this document be liable for special, direct, indirect, or consequential damage, losses, costs, charges, claims, demands, claim for lost profits, fees, or expenses of any nature or kind. TRADEMARKS IAR Systems, IAR Embedded Workbench, C-SPY, visualSTATE, The Code to Success, IAR KickStart Kit, I-jet, I-scope, IAR and the logotype of IAR Systems are trademarks or registered trademarks owned by IAR Systems AB. Microsoft and Windows are registered trademarks of Microsoft Corporation. Renesas is a registered trademark of Renesas Electronics Corporation. V850 is a trademark of Renesas Electronics Corporation. Adobe and Acrobat Reader are registered trademarks of Adobe Systems Incorporated. All other product names are trademarks or registered trademarks of their respective owners. EDITION NOTICE Ninth edition: May 2013 Part number: CV850-9 This guide applies to version 4.x of IAR Embedded Workbench® for the Renesas V850 microcontroller family. -

Secure Coding in Modern C++
MASARYK UNIVERSITY FACULTY OF INFORMATICS Secure coding in modern C++ MASTER'S THESIS Be. Matěj Plch Brno, Spring 2018 MASARYK UNIVERSITY FACULTY OF INFORMATICS Secure coding in modern C++ MASTER'S THESIS Be. Matěj Plch Brno, Spring 2018 This is where a copy of the official signed thesis assignment and a copy of the Statement of an Author is located in the printed version of the document. Declaration Hereby I declare that this paper is my original authorial work, which I have worked out on my own. All sources, references, and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Be. Matěj Plch Advisor: RNDr. Jifi Kur, Ph.D. i Acknowledgements I would like to thank my supervisor Jiří Kůr for his valuable guidance and advice. I would also like to thank my parents for their support throughout my studies. ii Abstract This thesis documents how using modern C++ standards can help with writing more secure code. We describe common vulnerabilities, and show new language features which prevent them. We also de• scribe coding conventions and tools which help programmers with using modern C++ features. This thesis can be used as a handbook for programmers who would like to know how to use modern C++ features for writing secure code. We also perform an extensive static analysis of open source C++ projects to find out how often are obsolete constructs of C++ still used in practice. iii Keywords secure coding, modern C++, vulnerabilities, ISO standard, coding conventions, -

Resource Management and Tuples in C∀
Resource Management and Tuples in C8 by Robert Schluntz A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree of Master of Mathematics in Computer Science Waterloo, Ontario, Canada, 2017 © Robert Schluntz 2017 I hereby declare that I am the sole author of this thesis. This is a true copy of the thesis, including any required final revisions, as accepted by my examiners. I understand that my thesis may be made electronically available to the public. ii Abstract C8 is a modern, non-object-oriented extension of the C programming language. This thesis addresses several critical deficiencies of C, notably: resource management, a limited function- return mechanism, and unsafe variadic functions. To solve these problems, two fundamental language features are introduced: tuples and constructors/destructors. While these features exist in prior programming languages, the contribution of this work is engineering these features into a highly complex type system. C is an established language with a dedicated user-base. An important goal is to add new features in a way that naturally feels like C, to appeal to this core user-base, and due to huge amounts of legacy code, maintaining backwards compatibility is crucial. iii Acknowledgements I would like to thank my supervisor, Professor Peter Buhr, for all of his help, including reading the many drafts of this thesis and providing guidance throughout my degree. This work would not have been as enjoyable, nor would it have been as strong without Peter’s knowledge, help, and encouragement. I would like to thank my readers, Professors Gregor Richards and Patrick Lam for all of their helpful feedback. -

CFFI Documentation Release 1.5.2
CFFI Documentation Release 1.5.2 Armin Rigo, Maciej Fijalkowski February 13, 2016 Contents 1 What’s New 3 1.1 v1.5.2...................................................3 1.2 v1.5.1...................................................3 1.3 v1.5.0...................................................3 1.4 v1.4.2...................................................3 1.5 v1.4.1...................................................3 1.6 v1.4.0...................................................3 1.7 v1.3.1...................................................4 1.8 v1.3.0...................................................4 1.9 v1.2.1...................................................5 1.10 v1.2.0...................................................5 1.11 v1.1.2...................................................5 1.12 v1.1.1...................................................5 1.13 v1.1.0...................................................6 1.14 v1.0.3...................................................6 1.15 v1.0.2...................................................6 1.16 v1.0.1...................................................6 1.17 v1.0.0...................................................6 2 Installation and Status 7 2.1 Platform-specific instructions......................................8 3 Overview 11 3.1 Simple example (ABI level, in-line)................................... 11 3.2 Out-of-line example (ABI level, out-of-line).............................. 12 3.3 Real example (API level, out-of-line).................................. 13 3.4 Struct/Array Example -

Lecture 21: Calling Conventions Menu Calling Convention Calling Convention X86 C Calling Convention
CS216: Program and Data Representation University of Virginia Computer Science Spring 2006 David Evans Menu Lecture 21: Calling Conventions • x86 C Calling Convention • Java Byte Code Wizards http://www.cs.virginia.edu/cs216 UVa CS216 Spring 2006 - Lecture 21: Calling Conventions 2 Calling Convention Calling Convention • Rules for how the caller and the Caller Callee callee make subroutine calls • Where to put • Where to find • Caller needs to know: params params • What registers can I • What registers – How to pass parameters assume are same must I not bash – What registers might be bashed by • Where to find result • Where to put result called function • State of stack • State of stack – What is state of stack after return – Where to get result UVa CS216 Spring 2006 - Lecture 21: Calling Conventions 3 UVa CS216 Spring 2006 - Lecture 21: Calling Conventions 4 Calling Convention: x86 C Calling Convention Easiest for Caller Caller Callee Caller Callee • Where to put • Where to find • Params on stack in • Find params on stack params params reverse order in reverse order • What registers can I • What registers • Can assume EBX, • Must not bash EBX, assume are same must I not bash EDI and ESI are EDI or ESI – All of them – None of them same • Put result in EAX • Where to find result • Where to put result • Find result in EAX • Stack rules next • State of stack • State of stack • Stack rules next Need to save and Need to save and restore restore EBX, EDI (EAX), ECX, EDX and ESI UVa CS216 Spring 2006 - Lecture 21: Calling Conventions 5 UVa CS216 -
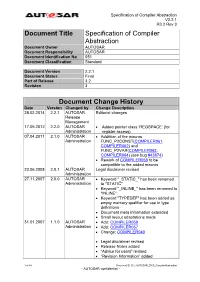
Specification of Compiler Abstraction
Specification of Compiler Abstraction V2.2.1 R3.2 Rev 3 Document Title Specification of Compiler Abstraction Document Owner AUTOSAR Document Responsibility AUTOSAR Document Identification No 051 Document Classification Standard Document Version 2.2.1 Document Status Final Part of Release 3.2 Revision 3 Document Change History Date Version Changed by Change Description 28.02.2014 2.2.1 AUTOSAR Editorial changes Release Management 17.05.2012 2.2.0 AUTOSAR Added pointer class ‘REGSPACE’ (for Administration register access) 07.04.2011 2.1.0 AUTOSAR Addtition of the macros Administration FUNC_P2CONST(COMPILER061, COMPILER062) and FUNC_P2VAR(COMPILER063, COMPILER064) (see bug #43874) Rework of COMPILER058 to be compatible to the added macros 23.06.2008 2.0.1 AUTOSAR Legal disclaimer revised Administration 27.11.2007 2.0.0 AUTOSAR Keyword "_STATIC_" has been renamed Administration to "STATIC" Keyword "_INLINE_" has been renamed to "INLINE" Keyword "TYPEDEF" has been added as empty memory qualifier for use in type definitions Document meta information extended Small layout adaptations made 31.01.2007 1.1.0 AUTOSAR Add: COMPILER058 Administration Add: COMPILER057 Change: COMPILER040 Legal disclaimer revised Release Notes added “Advice for users” revised “Revision Information” added 1 of 44 Document ID 051: AUTOSAR_SWS_CompilerAbstraction - AUTOSAR confidential - Specification of Compiler Abstraction V2.2.1 R3.2 Rev 3 Document Change History Date Version Changed by Change Description 27.04.2006 1.0.0 AUTOSAR Initial Release Administration 2 of 44 Document ID 051: AUTOSAR_SWS_CompilerAbstraction - AUTOSAR confidential - Specification of Compiler Abstraction V2.2.1 R3.2 Rev 3 Disclaimer This specification and the material contained in it, as released by AUTOSAR is for the purpose of information only. -

EECS 373 Design of Microprocessor-Based Systems
Procedures Procedures are very important for writing reusable and maintainable code in assembly and high-level languages. How are they implemented? · Application Binary Interfaces · Calling Conventions · Recursive Calls · Examples Reference: PowerPC Embedded ABI General Concepts · Caller: The calling procedure Callee: The procedure called by the caller ¼ int mult(x, y) prod = mult (a, b) ¼ ¼ return (x * y) · Caller and callee must agree on: · How to pass parameters · How to return the return value(s), if any · How to maintain relevant information across calls · PowerPC architecture does not define ªagreementº. Instead, common policies are defined by convention. PowerPC Features The PowerPC ISA provides the following features to support procedure/function calls: · link register (p. 2-11) · bl: branch and link (p. 4-41) · blr: branch to link register (Table F-4) A Very Simple Calling Convention · Passing arguments · Use GPRs r3 to r10 in order · Use stack in main memory if more than 8 arguments · Passing return value · Leave result in r3 Example int func(int a, int b) { return (a + b); } main { ¼ func(5,6); ¼ } Another Example int func2(int a, int b) { return func(a , b); } main { ¼ func2(5,6); ¼ } The Stack · Information for each function invocation (e.g. link register) is saved on the call stack or simply stack. · Each function invocation has its own stack frame (a.k.a. activation record ). high address func2 stack frame func stack frame stack pointer low address Using the Stack main ¼ Describe the stack and LR contents ¼ · right before -

A Multilanguage Static Analysis of Python Programs with Native C Extensions Raphaël Monat, Abdelraouf Ouadjaout, Antoine Miné
A Multilanguage Static Analysis of Python Programs with Native C Extensions Raphaël Monat, Abdelraouf Ouadjaout, Antoine Miné To cite this version: Raphaël Monat, Abdelraouf Ouadjaout, Antoine Miné. A Multilanguage Static Analysis of Python Programs with Native C Extensions. Static Analysis Symposium (SAS), Oct 2021, Chicago, Illinois, United States. hal-03313409 HAL Id: hal-03313409 https://hal.archives-ouvertes.fr/hal-03313409 Submitted on 3 Aug 2021 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. A Multilanguage Static Analysis of Python Programs with Native C Extensions∗ Raphaël Monat1�, Abdelraouf Ouadjaout1�, and Antoine Miné1;2� [email protected] 1 Sorbonne Université, CNRS, LIP6, F-75005 Paris, France 2 Institut Universitaire de France, F-75005, Paris, France Abstract. Modern programs are increasingly multilanguage, to benefit from each programming language’s advantages and to reuse libraries. For example, developers may want to combine high-level Python code with low-level, performance-oriented C code. In fact, one in five of the 200 most downloaded Python libraries available on GitHub contains C code. Static analyzers tend to focus on a single language and may use stubs to model the behavior of foreign function calls. -

C and C++ Functions Variadic User-Defined Standard Predefined
MODULE 4 FUNCTIONS Receive nothing, return nothing-receive nothing, return something- receive something, return something-receive something, return nothing And they do something. That is a function! My Training Period: hours Note: Function is one of the important topics in C and C++. Abilities ▪ Able to understand and use function. ▪ Able to create user defined functions. ▪ Able to understand Structured Programming. ▪ Able to understand and use macro. ▪ Able to appreciate the recursive function. ▪ Able to find predefined/built-in standard and non-standard functions resources. ▪ Able to understand and use predefined/built-in standard and non-standard functions. ▪ Able to understand and use the variadic functions. 4.1 Some Definition - Most computer programs that solve real-world problem are large, containing thousand to million lines of codes and developed by a team of programmers. - The best way to develop and maintain large programs is to construct them from smaller pieces or modules, each of which is more manageable than the original program. - These smaller pieces are called functions. In C++ you will be introduced to Class, another type smaller pieces construct. - The function and class are reusable. So in C / C++ programs you will encounter and use a lot of functions. There are standard (normally called library) such as maintained by ANSI C / ANSI C++, ISO/IEC C, ISO/IEC C++ and GNU’s glibc or other non-standard functions (user defined or vendors specific or implementations or platforms specific). - If you have noticed, in the previous Modules, you have been introduced with many functions, including the main(). main() itself is a function but with a program execution point.