Computer Applications for Geothermal Energy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

JAWS® for Windows Training Bundle Outline
JAWS® for Windows Training Bundle Outline Introduction to the Training • Overview of topics to be covered in the training • Introduction to the DAISY format and why it is being used PlexTalk® Pocket Introduction • Description of physical layout • Basic functions: play/pause audio, fast forward/rewind, navigate by heading, navigate to different books • Specifics on navigating through the training bundle • Inserting, deleting, and moving to bookmarks VictorReader Stream Introduction • Description of physical layout • Basic functions: play/pause audio, fast forward/rewind, navigate by heading, navigate to different books • Specifics on navigating through the training bundle • Inserting, deleting, and moving to bookmarks Meet the Trainers • Introduction by Ryan and Dan Introduction to JAWS • What is JAWS? • What kinds of things are people able to do with it? • Silencing JAWS • Working with different types of computer keyboards o Laptop and desktop keyboards o Changing the JAWS keyboard layout • The JAWS key • Pressing multikey keyboard commands • Keyboard help mode • Opening and closing JAWS Working with Windows® Controls • Menus o Navigating vertically and horizontally o Opening submenus • Dialog boxes and their various controls o Edit, combo, check, radio, button, and slider o Moving through various controls • The JAWS Startup Wizard o Speech rate, JAWS startup options, keyboard layout, virtual ribbon feature, etc. Introduction to Windows • What is Windows and what is an operating system? • Differences between Windows 7 and 8 and why we -

Korean Style Guide
Korean Style Guide Published: February, 2019 Microsoft Korean Style Guide Contents 1 About this style guide............................................................................................................................................... 4 1.1 Recommended style references .............................................................................................................. 4 2 Microsoft voice .............................................................................................................................................................. 5 2.1 Choices that reflect Microsoft voice ..................................................................................................... 6 2.1.1 Flexibility ........................................................................................................................................................ 6 2.1.2 Word choice................................................................................................................................................. 7 2.1.3 Word-to-word translation.................................................................................................................. 8 2.1.4 Words and phrases to avoid ............................................................................................................ 9 2.1.5 세요 instead of 십시오 ...................................................................................................................... 11 2.2 Sample Microsoft voice text................................................................................................................... -
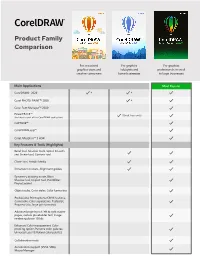
EXT EX Product Family Product Family for Occasional Graphics Users and Comparison Comparison Creative Consumers
TEXT EX Product Family Product Family For occasional graphics users and Comparison Comparison creative consumers For graphics hobbyists and home businesses For occasional For graphics For graphics graphics users and hobbyists and professionals in small Full-featured suite creative consumers home businesses to large businesses for graphics professionals in small to large businesses Main Applications Most Popular CorelDRAW® 2020 Corel PHOTO-PAINT™ 2020 Corel Font Manager™ 2020 PowerTRACE™ (Quick Trace only) (included as part of the CorelDRAW application) CAPTURE™ CorelDRAW.app™ Key Features & Tools (Highlights) Corel AfterShot™ 3 HDR Bevel tool, Shadow tools, Spiral, Smooth and Smear tool, Contour tool Key Features & Tools (Highlights) Clone Tool, Artistic Media Bevel tool, Shadow tools, Spiral, Smooth and Smear tool, Contour tool Key Features & Tools (Highlights) Dimension dockers, Alignment guides Clone Tool, Artistic Media Symmetry drawing mode, Block Shadow tool, Impact tool, Pointillizer, Dimension dockers, Alignment guides PhotoCocktail Barcode Wizard Symmetry drawing mode, Block Professional Print options Duplexing Wizard Shadow tool, Impact tool, Pointillizer, Remove (CMYK features, Composite, Color PhotoCocktail separations, Postscript, Prepress tabs) GPL Ghostscript for enhanced EPS Advanced page layout: left & right master Object styles, Color styles, Color harmonies and PS support pages, custom placeholder text, image rendering above 150dpi Professional Print options (CMYK features, Composite, Color separations, Postscript, Enhanced -

Cataloging User's Guide
Voyager® 9.2 Cataloging User’s Guide November 2015 Ex Libris Confidential CONFIDENTIAL INFORMATION The information herein is the property of Ex Libris Ltd. or its affiliates and any misuse or abuse will result in economic loss. DO NOT COPY UNLESS YOU HAVE BEEN GIVEN SPECIFIC WRITTEN AUTHORIZATION FROM EX LIBRIS LTD. This document is provided for limited and restricted purposes in accordance with a binding contract with Ex Libris Ltd. or an affiliate. The information herein includes trade secrets and is confidential. DISCLAIMER The information in this document will be subject to periodic change and updating. Please confirm that you have the most current documentation. There are no warranties of any kind, express or implied, provided in this documentation, other than those expressly agreed upon in the applicable Ex Libris contract. This information is provided AS IS. Unless otherwise agreed, Ex Libris shall not be liable for any damages for use of this document, including, without limitation, consequential, punitive, indirect or direct damages. Any references in this document to third-party material (including third-party Web sites) are provided for convenience only and do not in any manner serve as an endorsement of that third-party material or those Web sites. The third-party materials are not part of the materials for this Ex Libris product and Ex Libris has no liability for such materials. TRADEMARKS ʺEx Libris,ʺ the Ex Libris Bridge to Knowledge , Primo, Aleph, Voyager, SFX, MetaLib, Verde, DigiTool, Rosetta, bX, URM, Alma , and other marks are trademarks or registered trademarks of Ex Libris Ltd. or its affiliates. -

R-Photo User's Manual
User's Manual © R-Tools Technology Inc 2020. All rights reserved. www.r-tt.com © R-tools Technology Inc 2020. All rights reserved. No part of this User's Manual may be copied, altered, or transferred to, any other media without written, explicit consent from R-tools Technology Inc.. All brand or product names appearing herein are trademarks or registered trademarks of their respective holders. R-tools Technology Inc. has developed this User's Manual to the best of its knowledge, but does not guarantee that the program will fulfill all the desires of the user. No warranty is made in regard to specifications or features. R-tools Technology Inc. retains the right to make alterations to the content of this Manual without the obligation to inform third parties. Contents I Table of Contents I Start 1 II Quick Start Guide in 3 Steps 1 1 Step 1. Di.s..k.. .S..e..l.e..c..t.i.o..n.. .............................................................................................................. 1 2 Step 2. Fi.l.e..s.. .M..a..r..k.i.n..g.. ................................................................................................................ 4 3 Step 3. Re..c..o..v..e..r.y.. ...................................................................................................................... 6 III Features 9 1 File Sorti.n..g.. .............................................................................................................................. 9 2 File Sea.r.c..h.. ............................................................................................................................ -

Forcepoint DLP Supported File Formats and Size Limits
Forcepoint DLP Supported File Formats and Size Limits Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 This article provides a list of the file formats that can be analyzed by Forcepoint DLP, file formats from which content and meta data can be extracted, and the file size limits for network, endpoint, and discovery functions. See: ● Supported File Formats ● File Size Limits © 2021 Forcepoint LLC Supported File Formats Supported File Formats and Size Limits | Forcepoint DLP | v8.8.1 The following tables lists the file formats supported by Forcepoint DLP. File formats are in alphabetical order by format group. ● Archive For mats, page 3 ● Backup Formats, page 7 ● Business Intelligence (BI) and Analysis Formats, page 8 ● Computer-Aided Design Formats, page 9 ● Cryptography Formats, page 12 ● Database Formats, page 14 ● Desktop publishing formats, page 16 ● eBook/Audio book formats, page 17 ● Executable formats, page 18 ● Font formats, page 20 ● Graphics formats - general, page 21 ● Graphics formats - vector graphics, page 26 ● Library formats, page 29 ● Log formats, page 30 ● Mail formats, page 31 ● Multimedia formats, page 32 ● Object formats, page 37 ● Presentation formats, page 38 ● Project management formats, page 40 ● Spreadsheet formats, page 41 ● Text and markup formats, page 43 ● Word processing formats, page 45 ● Miscellaneous formats, page 53 Supported file formats are added and updated frequently. Key to support tables Symbol Description Y The format is supported N The format is not supported P Partial metadata -

Technical User's Guide
Voyager® 7.2 Technical User’s Guide May 2011 CONFIDENTIAL INFORMATION The information herein is the property of Ex Libris Ltd. or its affiliates and any misuse or abuse will result in economic loss. DO NOT COPY UNLESS YOU HAVE BEEN GIVEN SPECIFIC WRITTEN AUTHORIZATION FROM EX LIBRIS LTD. This document is provided for limited and restricted purposes in accordance with a binding contract with Ex Libris Ltd. or an affiliate. The information herein includes trade secrets and is confidential. DISCLAIMER The information in this document will be subject to periodic change and updating. Please confirm that you have the most current documentation. There are no warranties of any kind, express or implied, provided in this documentation, other than those expressly agreed upon in the applicable Ex Libris contract. This information is provided AS IS. Unless otherwise agreed, Ex Libris shall not be liable for any damages for use of this document, including, without limitation, consequential, punitive, indirect or direct damages. Any references in this document to third-party material (including third-party Web sites) are provided for convenience only and do not in any manner serve as an endorsement of that third-party material or those Web sites. The third-party materials are not part of the materials for this Ex Libris product and Ex Libris has no liability for such materials. TRADEMARKS "Ex Libris," the Ex Libris bridge , Primo, Aleph, Alephino, Voyager, SFX, MetaLib, Verde, DigiTool, Preservation, URM, ENCompass, Endeavor eZConnect, WebVoyáge, Citation Server, LinkFinder and LinkFinder Plus, and other marks are trademarks or registered trademarks of Ex Libris Ltd. -

Designing and Developing a Model for Converting Image Formats Using Java API for Comparative Study of Different Image Formats
International Journal of Scientific and Research Publications, Volume 4, Issue 7, July 2014 1 ISSN 2250-3153 Designing and developing a model for converting image formats using Java API for comparative study of different image formats Apurv Kantilal Pandya*, Dr. CK Kumbharana** * Research Scholar, Department of Computer Science, Saurashtra University, Rajkot. Gujarat, INDIA. Email: [email protected] ** Head, Department of Computer Science, Saurashtra University, Rajkot. Gujarat, INDIA. Email: [email protected] Abstract- Image is one of the most important techniques to Different requirement of compression in different area of image represent data very efficiently and effectively utilized since has produced various compression algorithms or image file ancient times. But to represent data in image format has number formats with time. These formats includes [2] ANI, ANIM, of problems. One of the major issues among all these problems is APNG, ART, BMP, BSAVE, CAL, CIN, CPC, CPT, DPX, size of image. The size of image varies from equipment to ECW, EXR, FITS, FLIC, FPX, GIF, HDRi, HEVC, ICER, equipment i.e. change in the camera and lens puts tremendous ICNS, ICO, ICS, ILBM, JBIG, JBIG2, JNG, JPEG, JPEG 2000, effect on the size of image. High speed growth in network and JPEG-LS, JPEG XR, MNG, MIFF, PAM, PCX, PGF, PICtor, communication technology has boosted the usage of image PNG, PSD, PSP, QTVR, RAS, BE, JPEG-HDR, Logluv TIFF, drastically and transfer of high quality image from one point to SGI, TGA, TIFF, WBMP, WebP, XBM, XCF, XPM, XWD. another point is the requirement of the time, hence image Above mentioned formats can be used to store different kind of compression has remained the consistent need of the domain. -
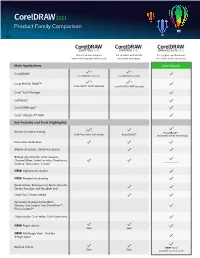
Coreldraw 2021 Product Family Comparison Matrix
TM Product Family Comparison For occasional graphics For graphics enthusiasts For graphics professionals users and those just starting out and home businesses in small to large businesses Main Applications Most Popular CorelDRAW® CorelDRAW Essentials CorelDRAW Standard Corel PHOTO-PAINT™ Corel PHOTO-PAINT Essentials Corel PHOTO-PAINT Standard Corel® Font Manager CAPTURE™ CorelDRAW.app™ Corel® AfterShot™ HDR Key Features and Tools (Highlights) ( ) Bitmap-to-vector tracing PowerTRACE™️ Quick Trace (one-click tracing) PowerTRACE™️ (Advanced with AI technology) Interactive Guidelines Alignment guides, Guidelines docker Bitmap adjustments: Color balance, Channel Mixer, Selective color, Desaturate, + many more! Gamma, Tone curve, + more NEW! Adjustments docker NEW! Perspective drawing Bevel docker, Shadow tool, Spiral, Smooth, Smear, Smudge, and Roughen tool Clone Tool, Artistic Media Symmetry drawing mode, Block Shadow tool, Impact tool, Pointillizer™, PhotoCocktail™ Object styles, Color styles, Color harmonies NEW! Pages docker Basic Basic NEW! Multipage View - Flexible design space Replace Colors NEW! More Basic Basic powerful, more intuitive Key Features and Tools (Highlights) Most Popular Enhanced Color management, Color proofing option, spot color support on output Professional Print options (CMYK features, Composite, Color separations, Postscript, Prepress tabs, large print preview) ENHANCED! Collaboration tools** Automation support (VSTA, VBA), Macro Manager Content Vector images 1,000 Over 7,000 High-resolution digital photos 100 1,000 -

27587 Apply Knowledge of Legislative Requirements in the Signmaking
NZQA registered unit standard 30160 version 1 Page 1 of 4 Title Demonstrate knowledge of and process vector and raster graphics files for sign production Level 4 Credits 30 Purpose This unit standard is for people working in the signmaking industry. People credited with this unit standard are able to demonstrate knowledge of graphic files and process vector and raster graphic files for sign production. Classification Sign Making > Sign Making - Core Available grade Achieved Explanatory notes 1 Reference Health and Safety at Work Act 2015. 2 File extension acronyms used: AI – Adobe illustrator file BMP – Bitmap CDL – Signlab vector graphics file CDR – Corel vector graphics file CPT – Corel photo paint file DXF – Drawing exchange file EPS – Encapsulated postscript vector graphics file FS – Flexisign file GIF – Graphics interchange format HPGL– HP graphics language plotter file JPEG– Joint photographic expert group PDF – Portable document format PNG – Portable network graphic PSD – Photoshop document RAW – Camera raw image file SVG – Scaleable vector graphics file TIFF – Tagged image file format 3 Definition Raster file – dot matrix pixel data structure representing an image. Workplace procedures – procedures used by the organisation carrying out the work and applicable to the tasks being carried out. Examples are – standard operating procedures, site safety procedures, equipment operating procedures, codes of Competenz New Zealand Qualifications Authority 2017 SSB Code 101571 NZQA registered unit standard 30160 version 1 Page 2 of 4 practice, quality management practices and standards, procedures to comply with legislative and local body requirements 4 Assessment information All evidence requirements must be performed in accordance with workplace procedures. Outcomes and evidence requirements Outcome 1 Demonstrate knowledge of graphic files for sign production. -

2020 Product Family Comparison
Product Family Comparison For occasional For graphics For graphics graphics users and hobbyists and professionals in small creative consumers home businesses to large businesses Main Applications Most Popular CorelDRAW® 2020 CorelDRAW Essentials 2020 CorelDRAW Standard 2020 Corel PHOTO-PAINT™ 2020 Corel PHOTO-PAINT Standard 2020 Corel Font Manager™ 2020 Remove PowerTRACE™️ CAPTURE™ CorelDRAW.app™ Corel AfterShot™ 3 HDR Key Features & Tools (Highlights) New row Bitmap-to-vector tracing ( ) Bitmap-to-vector tracing PowerTRACE™️ PowerTRACE™️ Quick Trace (one-click tracing) PowerTRACE™️ Bevel tool, Shadow tools, Spiral, Smooth Bevel tool, Shadow tool, Spiral, Smooth (Advanced with AI technology) (Advanced with AI technology) and Smear tool, Contour tool and Smear tool Bevel tool, Shadow tool, Spiral, Smooth and Smear tool Dimension dockers, Alignment guides Alignment guides, Guidelines docker Clone Tool, Artistic Media Alignment guides, Guidelines docker Symmetry drawing mode, Block Shadow tool, Impact tool, Pointillizer, PhotoCocktail Object styles, Color styles, Color harmonies Professional Print options (CMYK features, Composite, Color separations, Postscript, Prepress tabs, large print preview) Advanced page layout: left & right master pages, custom placeholder text, image Advanced page layout: left & right master rendering above 150dpi pages, custom placeholder text Enhanced Color management, Color Enhanced Color management, Color Enhanced Color management, Color proofing option, Pantone color palettes, proofing option, spot color support -

Cataloging User's Guide
Voyager® 9.1 Cataloging User’s Guide November 2014 Ex Libris Confidential CONFIDENTIAL INFORMATION The information herein is the property of Ex Libris Ltd. or its affiliates and any misuse or abuse will result in economic loss. DO NOT COPY UNLESS YOU HAVE BEEN GIVEN SPECIFIC WRITTEN AUTHORIZATION FROM EX LIBRIS LTD. This document is provided for limited and restricted purposes in accordance with a binding contract with Ex Libris Ltd. or an affiliate. The information herein includes trade secrets and is confidential. DISCLAIMER The information in this document will be subject to periodic change and updating. Please confirm that you have the most current documentation. There are no warranties of any kind, express or implied, provided in this documentation, other than those expressly agreed upon in the applicable Ex Libris contract. This information is provided AS IS. Unless otherwise agreed, Ex Libris shall not be liable for any damages for use of this document, including, without limitation, consequential, punitive, indirect or direct damages. Any references in this document to third-party material (including third-party Web sites) are provided for convenience only and do not in any manner serve as an endorsement of that third-party material or those Web sites. The third-party materials are not part of the materials for this Ex Libris product and Ex Libris has no liability for such materials. TRADEMARKS ʺEx Libris,ʺ the Ex Libris Bridge to Knowledge , Primo, Aleph, Voyager, SFX, MetaLib, Verde, DigiTool, Rosetta, bX, URM, Alma , and other marks are trademarks or registered trademarks of Ex Libris Ltd. or its affiliates.