Copyright and Licensing Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Easy As Abc: Categorizing Open Source Licenses
EASY AS ABC: CATEGORIZING OPEN SOURCE LICENSES Andrew T. Pham1, Matthew B. Weinstein2, Jamie L. Ryerson3 With more than 180,000 open source projects available and its more than 1400 unique licenses, the complexity of deciding how to manage open source usage within “closed-source” commercial enterprises have dramatically increased.4 Because of the complexity and risks associated with open source—where source code is made freely available for all to review, edit, and use—many closed-source commercial enterprises discourage or prohibit use of open source; a common and short-sighted practice. With a proper open source management framework, open source can be an invaluable resource, and its risks can be understood, managed and controlled. This article proposes a simple, consistent and effective open source categorization and management system to enable a peaceful coexistence between open source and closed-source codes. Free and open source software (“FOSS” or collectively “open source”) is a valuable tool, but one that must be understood to be used effectively. The litany of risks associated with use of open source include: having to release a derivative product incorporating open source under the same open source license; incorporating code that infringes a patent; violating an open source license’s attribution requirements; and a lack of warranties and indemnities. Given the extensive investment of time, money and resources that goes into product development, it comes as no This article is an edited version of the original, which dealt not only with categorizing open source licenses but also a wider array of issues associated with implementing an open source policy. -

Security in Cloud Computing a Security Assessment of Cloud Computing Providers for an Online Receipt Storage
Security in Cloud Computing A Security Assessment of Cloud Computing Providers for an Online Receipt Storage Mats Andreassen Kåre Marius Blakstad Master of Science in Computer Science Submission date: June 2010 Supervisor: Lillian Røstad, IDI Norwegian University of Science and Technology Department of Computer and Information Science Problem Description We will survey some current cloud computing vendors and compare them to find patterns in how their feature sets are evolving. The start-up firm dSafe intends to exploit the promises of cloud computing in order to launch their business idea with only marginal hardware and licensing costs. We must define the criteria for how dSafe's application can be sufficiently secure in the cloud as well as how dSafe can get there. Assignment given: 14. January 2010 Supervisor: Lillian Røstad, IDI Abstract Considerations with regards to security issues and demands must be addressed before migrating an application into a cloud computing environment. Different vendors, Microsoft Azure, Amazon Web Services and Google AppEngine, provide different capabilities and solutions to the individual areas of concern presented by each application. Through a case study of an online receipt storage application from the company dSafe, a basis is formed for the evaluation. The three cloud computing vendors are assessed with regards to a security assessment framework provided by the Cloud Security Alliance and the application of this on the case study. Finally, the study is concluded with a set of general recommendations and the recommendation of a cloud vendor. This is based on a number of security as- pects related to the case study’s existence in the cloud. -
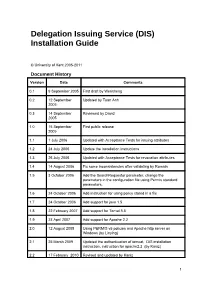
Installation Guide
Delegation Issuing Service (DIS) Installation Guide © University of Kent 2005-2011 Document History Version Date Comments 0.1 9 September 2005 First draft by Wensheng 0.2 12 September Updated by Tuan Anh 2005 0.3 14 September Reviewed by David 2005 1.0 15 September First public release 2005 1.1 1 July 2006 Updated with Acceptance Tests for issuing attributes 1.2 24 July 2006 Update the installation instructions 1.3 26 July 2006 Updated with Acceptance Tests for revocation attributes 1.4 14 August 2006 Fix some inconsistencies after validating by Romain 1.5 3 October 2006 Add the SearchRequestor parameter, change the parameters in the configuration file using Permis standard parameters. 1.6 24 October 2006 Add instruction for using policy stored in a file 1.7 24 October 2006 Add support for java 1.5 1.8 22 February 2007 Add support for Tomat 5.5 1.9 23 April 2007 Add support for Apache 2.2 2.0 12 August 2008 Using PERMIS v5 policies and Apache http server on Windows (by Linying) 2.1 25 March 2009 Updated the authentication of tomcat, DIS installation instruction, instruction for apache2.2 (by Kaniz) 2.2 17 February 2010 Revised and updated by Kaniz 1 2.3 16 April 2010 Updated by Mark 2.5 26 October 2010 Install guide rewritten and separated into its own document 2.5.2 2 November 2010 Java installation explained more fully. Tomcat native library installation corrected. Default DIS configuration file inserted. 2.5.4 5 November 2010 Addressed feedback from Kaniz 2.5.5 26 May 2011 Added alternative <FilesMatch> for PHP files. -

Open Cloud Computing with the Simple Cloud API and Apache Libcloud Doug Tidwell Cloud Computing Evangelist, IBM [email protected]
Open Cloud Computing with the Simple Cloud API and Apache libcloud Doug Tidwell Cloud Computing Evangelist, IBM [email protected] Session 7665 Agenda • Portability and interoperability • A few words about APIs • The Simple Cloud API • Storage • Queues • Documents • Controlling VMs with Apache libcloud • Resources / Next steps The problem Vendor lock-in • If there’s a new technology, any talented programmer will want to use it. • Maybe the shiny new thing is appropriate for what we’re doing. • Maybe not. • We’re probably going to use it anyway. • The challenge is to walk the line between using the newest, coolest thing and avoiding vendor lock-in. Portability and Interoperability • In writing flexible code for the cloud, there are two key concepts: • Portability is the ability to run components or systems written for one cloud provider in another cloud provider’s environment. • Interoperability is the ability to write one piece of code that works with multiple cloud providers, regardless of the differences between them. How standards work • For a standards effort to work, three things have to happen: • The standard has to solve a common problem in an elegant way. • The standard has to be implemented consistently by vendors. • Users have to insist that the products they use implement the standard. How standards work • All three things have to happen. • If the standard doesn't solve a common problem, or if it solves it in an awkward way, the standard fails. • If the standard isn't implemented by anyone, the standard fails. • If customers buy and use products even though they don't implement the standard, the standard fails. -

An Introduction to Software Licensing
An Introduction to Software Licensing James Willenbring Software Engineering and Research Department Center for Computing Research Sandia National Laboratories David Bernholdt Oak Ridge National Laboratory Please open the Q&A Google Doc so that I can ask you Michael Heroux some questions! Sandia National Laboratories http://bit.ly/IDEAS-licensing ATPESC 2019 Q Center, St. Charles, IL (USA) (And you’re welcome to ask See slide 2 for 8 August 2019 license details me questions too) exascaleproject.org Disclaimers, license, citation, and acknowledgements Disclaimers • This is not legal advice (TINLA). Consult with true experts before making any consequential decisions • Copyright laws differ by country. Some info may be US-centric License and Citation • This work is licensed under a Creative Commons Attribution 4.0 International License (CC BY 4.0). • Requested citation: James Willenbring, David Bernholdt and Michael Heroux, An Introduction to Software Licensing, tutorial, in Argonne Training Program on Extreme-Scale Computing (ATPESC) 2019. • An earlier presentation is archived at https://ideas-productivity.org/events/hpc-best-practices-webinars/#webinar024 Acknowledgements • This work was supported by the U.S. Department of Energy Office of Science, Office of Advanced Scientific Computing Research (ASCR), and by the Exascale Computing Project (17-SC-20-SC), a collaborative effort of the U.S. Department of Energy Office of Science and the National Nuclear Security Administration. • This work was performed in part at the Oak Ridge National Laboratory, which is managed by UT-Battelle, LLC for the U.S. Department of Energy under Contract No. DE-AC05-00OR22725. • This work was performed in part at Sandia National Laboratories. -

Crypto Wars of the 1990S
Danielle Kehl, Andi Wilson, and Kevin Bankston DOOMED TO REPEAT HISTORY? LESSONS FROM THE CRYPTO WARS OF THE 1990S CYBERSECURITY June 2015 | INITIATIVE © 2015 NEW AMERICA This report carries a Creative Commons license, which permits non-commercial re-use of New America content when proper attribution is provided. This means you are free to copy, display and distribute New America’s work, or in- clude our content in derivative works, under the following conditions: ATTRIBUTION. NONCOMMERCIAL. SHARE ALIKE. You must clearly attribute the work You may not use this work for If you alter, transform, or build to New America, and provide a link commercial purposes without upon this work, you may distribute back to www.newamerica.org. explicit prior permission from the resulting work only under a New America. license identical to this one. For the full legal code of this Creative Commons license, please visit creativecommons.org. If you have any questions about citing or reusing New America content, please contact us. AUTHORS Danielle Kehl, Senior Policy Analyst, Open Technology Institute Andi Wilson, Program Associate, Open Technology Institute Kevin Bankston, Director, Open Technology Institute ABOUT THE OPEN TECHNOLOGY INSTITUTE ACKNOWLEDGEMENTS The Open Technology Institute at New America is committed to freedom The authors would like to thank and social justice in the digital age. To achieve these goals, it intervenes Hal Abelson, Steven Bellovin, Jerry in traditional policy debates, builds technology, and deploys tools with Berman, Matt Blaze, Alan David- communities. OTI brings together a unique mix of technologists, policy son, Joseph Hall, Lance Hoffman, experts, lawyers, community organizers, and urban planners to examine the Seth Schoen, and Danny Weitzner impacts of technology and policy on people, commerce, and communities. -

Tutorial on Web Services
Tutorial on Web Services HY559 Infrastructure Technologies for Large- Scale Service-Oriented Systems Jason Polakis [email protected] Required Software •Eclipse IDE for Java developers EE http://www.eclipse.org/downloads/ •Netbeans IDE http://netbeans.org/downloads/ •Apache Tomcat http://tomcat.apache.org/ •Apache AXIS2 http://axis.apache.org/axis2/java/core/download.cgi •Apache JUDDI http://juddi.apache.org/releases.html Getting Software • Either directly from given links, or: • In Ubuntu (as root) • To search for software – apt -cache search <program name> – Returns list of <packages> with short description • To install software – apt-get install <package> – Installs software, as well as dependencies Web Services “Any piece of software that makes itself available over the Internet and uses a standardized XML messaging system” •Extremely available •Language and platform independent •Distributed application components •Discoverable via a simple find mechanism •Components of Web Services – SOAP (Simple Object Access Protocol) – WSDL (Web Services Description Language) – UDDI (Universal Description, Discovery and Integration) Web Service Architecture •Web Service Protocol Stack –Service transport (transport messages between applications) •HTTP, SMTP, FTP –XML messaging (encode messages in common XML format ) • XML-RPC, WS-Addressing, and SOAP –Service description (describe public interface of service) –Service discovery (centralize services into common registry) •Programming models: –REST-based web services –SOAP-based web services SOAP-based Services •Use SOAP –protocol for exchanging structured information •Use WSDL –xml-based language for describing Web services •WSDL file –created based on the JAVA code in the service –exposed on the net •To use service, must create a client –based on WSDL info •Messages exchanged in SOAP •Java API for XML Web Services (JAX-WS) model also used for SOAP services. -

Software As a Service
Software as a Service Haojie Hang Ogheneovo Dibie Executive Summary • In this presentation, we go through the Software as a Service Methodology, examine its benefits and drawbacks and talk about two state-of-art SaaS systems– Amazon Web Service and Google App Engine • We also look into Service Oriented Architecture powering SaaS applications and its impact on modern web 2.0 applications • Finally, we examine hybrids of traditional and SaaS applications Overview • What is Software as a Service (SaaS) • Background o Brief history o Concept o Big picture o Related terms • Computing Today o SasS is everywhere o The SaaS Market • Benefits of SaaS • Drawbacks of SaaS o Robustness o Privacy o Security o Reliability • Service Oriented Architectures (SOA) o Guiding principles of SOA • Case studies o Amazon Web Services (AWS) o Google App Engine • Influence of SOA on Web 2.0 development o Zend Framework • Hybrids of Traditional and SaaS applications o Dropbox o Microsoft Office • Summary • References What is SaaS? • Definition: Software as a Service (SaaS), a.k.a. on- demand software, is a software delivery model in which software and its associated data are hosted centrally and accessed using a thin-client, usually a web browser over the internet. – Wikipedia • Simply put, SaaS is a method for delivering software that provides remote access to software as a web- based service. The software service can be purchased with a monthly fee and pay as you go. What is SaaS? • Where does the term SaaS come from? o The SAAS acronym allegedly first appeared -

Self-Encrypting Deception: Weaknesses in the Encryption of Solid State Drives
Self-encrypting deception: weaknesses in the encryption of solid state drives Carlo Meijer Bernard van Gastel Institute for Computing and Information Sciences School of Computer Science Radboud University Nijmegen Open University of the Netherlands [email protected] and Institute for Computing and Information Sciences Radboud University Nijmegen Bernard.vanGastel@{ou.nl,ru.nl} Abstract—We have analyzed the hardware full-disk encryption full-disk encryption. Full-disk encryption software, especially of several solid state drives (SSDs) by reverse engineering their those integrated in modern operating systems, may decide to firmware. These drives were produced by three manufacturers rely solely on hardware encryption in case it detects support between 2014 and 2018, and are both internal models using the SATA and NVMe interfaces (in a M.2 or 2.5" traditional form by the storage device. In case the decision is made to rely on factor) and external models using the USB interface. hardware encryption, typically software encryption is disabled. In theory, the security guarantees offered by hardware encryp- As a primary example, BitLocker, the full-disk encryption tion are similar to or better than software implementations. In software built into Microsoft Windows, switches off software reality, we found that many models using hardware encryption encryption and completely relies on hardware encryption by have critical security weaknesses due to specification, design, and implementation issues. For many models, these security default if the drive advertises support. weaknesses allow for complete recovery of the data without Contribution. This paper evaluates both internal and external knowledge of any secret (such as the password). -

Third-Party License Acknowledgments
Symantec Privileged Access Manager Third-Party License Acknowledgments Version 3.4.3 Symantec Privileged Access Manager Third-Party License Acknowledgments Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. Copyright © 2021 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. 2 Symantec Privileged Access Manager Third-Party License Acknowledgments Contents Activation 1.1.1 ..................................................................................................................................... 7 Adal4j 1.1.2 ............................................................................................................................................ 7 AdoptOpenJDK 1.8.0_282-b08 ............................................................................................................ 7 Aespipe 2.4e aespipe ........................................................................................................................ -

License Agreement
TAGARNO MOVE, FHD PRESTIGE/TREND/UNO License Agreement Version 2021.08.19 Table of Contents Table of Contents License Agreement ................................................................................................................................................ 4 Open Source & 3rd-party Licenses, MOVE ............................................................................................................ 4 Open Source & 3rd-party Licenses, PRESTIGE/TREND/UNO ................................................................................. 4 atk ...................................................................................................................................................................... 5 base-files ............................................................................................................................................................ 5 base-passwd ...................................................................................................................................................... 5 BSP (Board Support Package) ............................................................................................................................ 5 busybox.............................................................................................................................................................. 5 bzip2 ................................................................................................................................................................. -

Web Application for Generating a Standard Coordinated Documentation for CS Students’ Graduation Project in Gaza Universities Ibrahim M
International Journal of Engineering and Information Systems (IJEAIS) ISSN: 2000-000X Vol. 1 Issue 6, September – 2017, Pages: 155-167 Web Application for Generating a Standard Coordinated Documentation for CS Students’ Graduation Project in Gaza Universities Ibrahim M. Nasser, Samy S. Abu-Naser Faculty of Engineering and Information Technology, Al-Azhar University, Gaza, Palestine [email protected] Abstract: The computer science (CS) graduated students suffered from documenting their projects and specially from coordinating it. In addition, students’ supervisors faced difficulties with guiding their students to an efficient process of documenting. In this paper, we will offer a suggestion as a solution to the mentioned problems; that is an application to make the process of documenting computer science (CS) student graduation project easy and time-cost efficient. This solution will decrease the possibility of human mistakes and reduce the effort of documenting process. Keywords: web applications, cost efficient, time-cost efficient, documenting, software engineering, graduation projects. 1. INTRODUCTION Computer science (CS) is the study of the occurrences adjoining computers [1]. It's also defined as the study of computers and computational systems, computer scientists deal usually with software (unlike electrical and computer engineers), Primary parts of study inside Computer Science consist of computer systems, operating systems, networks, database systems, artificial intelligence, computer architecture, security, computer graphics, human computer interaction, systems analysis, software engineering, theory of computing and programming languages [11,17-28]. In computing, a web application is a client–server application that means, the client (like user interface) works in a web browser [2]. The general distinction between a web application and a dynamic web page is vague, web sites that we can name them as "web applications" are those have comparable functionality to a mobile application or to a desktop applications [3].