An International Peer Reviewed Open Access Journal
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
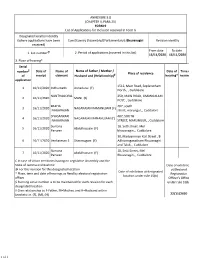
ANNEXURE 5.8 (CHAPTER V, PARA 25) FORM 9 List of Applica Ons For
ANNEXURE 5.8 (CHAPTER V, PARA 25) FORM 9 List of Applicaons for inclusion received in Form 6 Designated locaon identy (where applicaons have been Constuency (Assembly/£Parliamentary): Bhuvanagiri Revision identy received) From date To date 1. List number @ 2. Period of applicaons (covered in this list) 16/11/2020 16/11/2020 3. Place of hearing* Serial number $ Date of Name of Name of Father / Mother / Date of Time of Place of residence of receipt claimant Husband and (Relaonship) # hearing* hearing* applicaon 1512, Main Road, Seplanatham 1 16/11/2020 Indhumathi Annadurai (F) North , , Cuddalore NANTHAGOPAL 259, MAIN ROAD, UMANGALAM 2 16/11/2020 MANI (F) POST, , Cuddalore BAKIYA 407, south 3 16/11/2020 NAGARAJAN RAMANUJAM (F) NAGARAJAN street, marungur, , Cuddalore SIVASANKARI 407, SOUTH 4 16/11/2020 NAGARAJAN RANANUJAM (F) NAGARAJAN STREET, MARUNGUR, , Cuddalore Sumana 18, Se street, Mel 5 16/11/2020 Abdulhussain (F) Parveen bhuvanagiri, , Cuddalore 30, Mariyamman Koil Street , B 6 16/11/2020 Venkatesan S Shanmugam (F) Adhivaraganatham Bhuvanagiri and Taluk, , Cuddalore Sumana 18, Se Street, Mel 7 16/11/2020 Abdulhussain (F) Parveen Bhuvanagiri, , Cuddalore £ In case of Union territories having no Legislave Assembly and the State of Jammu and Kashmir Date of exhibion @ For this revision for this designated locaon at Electoral Date of exhibion at designated * Place, me and date of hearings as fixed by electoral registraon Registraon locaon under rule 15(b) officer Officer’s Office $ Running serial number is to be maintained for each revision for each under rule 16(b) designated locaon # Give relaonship as F-Father, M=Mother, and H=Husband within brackets i.e. -

On Contract Basis at SVRR GGH, Tirupati Vide Notification Date: 24-12-2020
Corrected Final Merit List of the candidates applied for the Post of Staff Nurses(BSC) on Contract Basis at SVRR GGH, Tirupati vide Notification date: 24-12-2020 / Weightage for ) / H Educational Qualification details completion of O H n 0 e / N / / n Date of 2 Course Total r s m o 0 H L e e ) 2 e s s d V SL. Applic- Name & Address of the Birth - Marks L c Y a H ( i u ( 7 n Caste Year of Pass NO of Weighta Mobile NO Remarks t N v s e e 0 O n NO. ation ID candidate DD-MM- a Marks 90% ( O + Q r - g u t e G e t 1 Qualifi- DD-MM- Max. Years ge upto A S a S 0 YYYY m Obtai- Marks ) t - o x cation YYYY Marks Complete 10 S w E ned on merit H d Marks P (A) (B) ( C) (D) ( E) (F) (G) (H) (I) (J) (K) (L) (M) (N) (O) (P) (Q) (R) (S) (T) Veguru Manjula D/o V.Meeraiah 1 318 F 6/12/1993 26Y SC NO NO NL BSC Jul-14 2600 2206 76.36 5 5 81.36 9182521467 Piduru, Manubolu Mandal,Nellore Dist., Poluri Kavitha, D/o Poluri Surendra babu, 2 238 Nallaguttapalli, F 5/15/1990 29Y OBC NO NO L BSC Dec-13 2600 2051 71.00 6 6 77.00 7702497477 Balaiahgaripalli, Chittoor Dist C.K.ViNOdhini, H/o C.Harikrishnappa, DBR Infra, 3rd Floor, 3 237 F 7/29/1989 30Y SC NO NO L BSC Nov-11 2600 1991 68.92 8 8 76.92 8971097808 Upadayayanagar, 14th cross, Tirupati, Chittoor Dist Nandyala Radha,H/o T.Chengaiah, 20-3- 4 274 124/T,Maruthingar, F 7/2/1984 35Y BC-B NO NO L BSC Dec-13 2100 1648 70.63 6 6 76.63 9490547906 Leelamahal, Tirupati, Chittoor Dist J.Divya, d/o JDS. -
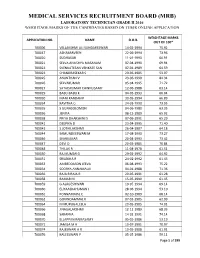
Weightage Marks of the Candidates Based on Their Online Application For
MEDICAL SERVICES RECRUITMENT BOARD (MRB) LABORATORY TECHNICIAN GRADE II 2016 WEIGHTAGE MARKS OF THE CANDIDATES BASED ON THEIR ONLINE APPLICATION WEIGHTAGE MARKS APPLICATION NO. NAME D.O.B. OUT OF 100* 700006 VELLAKSHMI ALI SUNDARESWARI 14-02-1994 75.92 700017 ASHABARVEEN 22-06-1994 73.96 700020 SUDHAKAR 11-01-1993 60.91 700021 SELVA ANUSHYA MASANAM 07-04-1990 69.94 700022 SVENKATESAN VENKATE SAN 07-01-1989 64.59 700023 CHANDRASEKAR S 29-06-1985 53.97 700025 ANANTHAN V 23-06-1990 84.34 700026 SELVAKUMAR 05-04-1995 71.72 700027 SATHISKUMAR CHINNUSAMY 12-06-1988 63.14 700029 BABU BABU K 04-05-1993 66.04 700030 MANI KANDAN P 30-05-1994 66.89 700034 KAVITHA G 24-03-1990 73.95 700035 S GUNASOLOMON 04-06-1980 63.35 700036 JENITA 08-12-1989 65.92 700038 PRIYA DHARSHINI S 07-06-1991 65.29 700041 DEEPIKA D 23-04-1995 71.40 700043 S JOTHILAKSHMI 26-04-1987 64.18 700044 SAMUNDEESWARI M 17-08-1990 73.27 700046 SIVAKUMAR 20-04-1993 73.42 700047 DEVI D 20-03-1985 70.84 700048 THILAK R 11-04-1978 61.51 700050 RAJ KUMAR G 29-01-1992 64.92 700051 SRILEKHA R 24-02-1992 61.43 700053 AMBEDDASON JEEVA 06-08-1993 75.22 700054 SOORYA ANNAMALAI 04-01-1988 71.36 700056 RAJA R RAJA R 20-05-1991 61.28 700058 RAMAR M 15-05-1990 61.45 700059 G ALAGESHWARI 19-05-1994 69.14 700060 ELIYAASRAHUMAN J 28-06-1994 53.10 700061 PONNAMMAL C 02-10-1989 68.14 700062 GOVINDAMMAL K 07-03-1985 62.99 700064 M MURUGALEELA 20-05-1985 74.01 700066 J NAGALAKSHMI 12-11-1989 68.33 700068 SARANYA 14-02-1991 74.14 700070 ELLAPPAN RAMASAMY 05-05-1986 53.19 700071 JAMILA M A 10-07-1991 70.97 700074 RAJESWARI A R 10-05-1988 61.91 700076 KALEESWARI P 05-05-1986 59.11 Page 1 of 199 MEDICAL SERVICES RECRUITMENT BOARD (MRB) LABORATORY TECHNICIAN GRADE II 2016 WEIGHTAGE MARKS OF THE CANDIDATES BASED ON THEIR ONLINE APPLICATION WEIGHTAGE MARKS APPLICATION NO. -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

1) Mana Desam ( Category/Genre = Social ) (Date: 24.11.1949 )
1) Mana Desam ( Category/Genre = Social ) (Date: 24.11.1949 ) 2) Shavukaru ( Category/Genre = Social ) (Date: 07.04.1950 ) 3) Palleturi Pilla ( Category/Genre = Social ) (Date: 27.04.1950 ) 4) Maya Rambha ( Category/Genre = Mythological ) (Date: 15.09.1950 ) 5) Samsaram ( Category/Genre = Social ) (Date: 29.12.1950 ) 6) Pathala Bhairavi ( Category/Genre = Classical ) (Date: 15.03.1951 ) 7) Mallishwari ( Category/Genre = Historical ) (Date: 20.12.1951 ) 8) Pelli Chesi Choodu ( Category/Genre = Social ) (Date: 29.02.1952 ) 9) Daasi ( Category/Genre = Social ) (Date: 1952 ) 10) Palleturu ( Category/Genre = Social ) (Date: 1952 ) 11) Ammalakkalu ( Category/Genre = Social ) (Date: 12.03.1953 ) 12) Pitchi Pulliah ( Category/Genre = Social ) (Date: 17.07.1953 ) 13) Chandi Rani ( Category/Genre = Classical ) (Date: 28.08.1953 ) 14) Chandraharam ( Category/Genre = Classical ) (Date: 06.01.1954 ) 15) Vaddante Dabbu ( Category/Genre = Social ) (Date: 19.02.1954 ) 16) Thodu Dongalu ( Category/Genre = Social ) (Date: 15.04.1954 ) 17) Rechukka ( Category/Genre = Classical ) (Date: 23.05.1954 ) 18) Raju Peda ( Category/Genre = Classical ) (Date: 25.06.1954 ) 19) Sangam ( Category/Genre = Social ) (Date: 10.07.1954 ) 20) Aggiramudu ( Category/Genre = Social ) (Date: 05.08.1954 ) 21) Parivarthana ( Category/Genre = Social ) (Date: 01.09.1954 ) 22) Iddaru Pellalu ( Category/Genre = Social ) (Date: 06.10.1954 ) 23) Missamma ( Category/Genre = Social ) (Date: 12.01.1955 ) 24) Vijaya Gowri ( Category/Genre = Classical ) (Date: 30.06.1955 ) 25) Cherapakura -

HISTORY Sri Sarada College for Women, (Autonomous) Reaccredited with ‘B++’ Grade by NAAC Affiliated to Periyar University, SALEM – 636 016
RETROSPECT PG & RESEARCH DEPARTMENT OF HISTORY Sri Sarada College for Women, (Autonomous) Reaccredited with ‘B++’ Grade by NAAC Affiliated to Periyar University, SALEM – 636 016. Volume – XV NEWSLETTER May 2021 (For Private Circulation only) Dear Colleagues, With the blessings of the Holy Trinity-Sri Ramakrishna Paramahamsa, Sri Sarada Devi and Swami Vivekananda, we have made an attempt to bring out this News Letter. We dedicate the Fifteenth Volume of News Letter to the sacred memories of Srimath Swami Chidhbavananda and Yatiswari Saradapriya Amba. Our humble pranams are due to Directress Yatiswari Vinayakapriya Amba and our College Secretary Guhapriya Amba. We are thankful to Dr. (Tmt.) R. Uma Rani, M.C.A., M.Phil., Ph.D., Principal for her kind advice, valuable suggestions and encouragement in bringing out this volume. In this volume we have given the activities of the department and achievements of the students of History in the academic year 2020-2021. Thanking You Editorial Board - Retrospect News “A generation which ignores History has no past and future” -Robert Heinlein About the Department Activities of the Department The Department of History was established Induction Programme in the year 1967 with Dr. R. Jagadambika, M.A., The classes for first year B.A. History was M.Lit., Ph.D., our former Principal as H.O.D. of started through online mode from 09.09.2020. the Department which was upgraded as P.G. First two days there was general induction Department in 1983 and Research Department programme. On the third day Departmental in 1994. Our staff members have published research papers in various National and Induction Programme was conducted. -
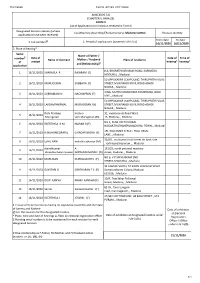
ANNEXURE 5.8 (CHAPTER V, PARA 25) FORM 9 List of Applica Ons For
11/21/2020 Form9_AC193_21/11/2020 ANNEXURE 5.8 (CHAPTER V, PARA 25) FORM 9 List of Applicaons for inclusion received in Form 6 Designated locaon identy (where Constuency (Assembly/£Parliamentary): Madurai Central Revision identy applicaons have been received) From date To date @ 2. Period of applicaons (covered in this list) 1. List number 16/11/2020 16/11/2020 3. Place of hearing* Serial Name of Father / $ Date of Date of Time of number Name of claimant Mother / Husband Place of residence of receipt hearing* hearing* and (Relaonship)# applicaon 8 A, BHARATHIYAR MAIN ROAD, KARIMEDU 1 16/11/2020 SHARMILA R RAJARAM (F) MADURAI, , Madurai 50 UPPUKARAR COMPOUND, THIRUPPATHI VILAS 2 16/11/2020 MURUGESAN SUBBAIYA (F) STREET, MUNIYANDI KOVIL ROAD ASHOK NAGAR, , Madurai 1/NA, MUTHU MANICKAM COMPOUND, BODI 3 16/11/2020 SUBRAMANI N NACHIAPPAN (F) LINE, , Madurai 50 UPPUKARAR COMPOUND, THIRUPPATHI VILAS 4 16/11/2020 LAKSHMIYAMMAL MURUGESAN (H) STREET, MUNIYANDI KOVIL ROAD ASHOK NAGAR, , Madurai Rishi Pradeep krishna 32, vivekananda Road Ward 5 16/11/2020 Murugesan veni Murugesan (M) 13, Madurai, , Madurai NO 1, ROSE VEETHI KURAL 6 16/11/2020 KEERTHIGA R M MARAN R (F) NAGAR,THATHANERI,MADURAI, TOWN, , Madurai 19J, KAZEEMAR STREET, PALLI VASAL 7 16/11/2020 K MOHAMEDRAFIQ G KADAR BASHA (F) LANE, , Madurai 32/8G , muniyandi Kovil street stc back side 8 16/11/2020 EZHIL RANI malathi rajkumar (M) , vaithiyanathapuram , , Madurai dineshkumar A 151/25, north perumal maistery 9 16/11/2020 dineshkumarsrinivasan GOPALAKRISHNAN (O) street, madurai, , Madurai -

Seniority List of Sgts in Krishna District-For Preponement Purpose
Seniority List of SGTs in Krishna District-for Preponement purpose D M DSC DS D M B.E MET MET RE Sl.No Name of the Desig Ca O O YEA C D M O O YO DEG d/ HOD- HOD- SUBJ MA PHC PHC (OR/V Percent . Teacher n School Mandal ste B B YOB R RA OJ OJ YOJ R R R REE TTC SUB1 SUB2 SUB3 1 2 PG ECTS IDT RKS H/ HI) age 26 TELUGU HISTORY POLITICS TELUGU 1 G.N.V.LAKSHMI SGT MPPS ROY NAGAR GANNAVARAM Gannavaram OC 1 1956 1979 29 3 2 1979 3 2 1979 B.A B.Ed SS OH 40% COMMERCe TELUGU 2 P.VANI SGT MPPS.INAMPUDI(AA) Pamidimukkala OC 1 4 1956 1979 69 27 1 1979 27 1 1979 INTER TTC ECO CIVICS SOCIAL 3 M.M.NIRMALA RANI SGT MPPS VARAHAPATNAM Kaikaluru BC 16 10 1959 1979 31 3 1979 31 3 1979 - - - - - - - - - - 4 M.Sukha Veni SGT MPPS, Puritigadda Challapalli OC 24 6 1960 1980 0 14 8 1980 14 8 1980 - D.Ed 5 K.Anuradha SGT MPPS, Nadakuduru Challapalli OC 1 8 1960 1980 0 16 10 1980 16 10 1980 - D.Ed - - - - - - - - 6 B.Rama Devi SGT MPUPS BUDAWADA Jaggaiahpet BC 1 7 1955 1980 0 27 10 1980 27 10 1980 - TTC KANDULLA VEERA.NANCHARAMMA 10 T.T.C HISTORY POLITICS SOCIALOGY 7 SGT MPPS.GUDURU II WARD Guduru SC 3 1955 1980 136 8 1 1980 8 1 1980 B.A POLITICS 8 T.Jhansi Lakshmi SGT MPPS TAPASIPUDI Machilipatnam R OC 14 5 1957 1980 29 7 1980 29 7 1980 BA BED Telugu HIS SOC TEL -- -- No 9 V.Bujji SGT P.Prolu OC 1 10 1955 1980 20 8 1980 20 8 1980 BA B.Ed H P T SS Tel - - MPPS Konakanchi V.SURYANARAYANA 11/2/1981 Relinqushed 10 SGT MPPS-P.A.PALLI(M) Unguturu OC 10 9 1956 1981 0 7 12 1978 11 2 1981 BA BED HIS ECO CIV SS ENG - - 11 P.KARIMUNNISA SGT MPPS KALAVAPAMULA Vuyyuru OC 1 6 1955 -

NT All Pages 2019.Indd
MONDAY 8 25 FEBRUARY 2019 newstodaynet.com newstodaydaily ntchennai CHENNAI Rami Malek, who played the late Freddie Mercury in the fi lm Bohemian Rhapsody, accepts the Oscar for AND THE best actor Two fi lms lead the nomination roster OSCAR GOES TO... - Roma and The Favourite, both u Green Book adjudged the best fi lm u Rami Malek, competing for Olivia Colman emerge winners Best Picture and other major Lady Gaga gets emotional as she accepts the Oscar for best Oscars, original song Shallow from the fi lm A Star Is Born have 10 THE COMPLETE LIST Best Picture Green Book nominations Best Director Alfonso Cuaron,Roma each Best Actress Olivia Colman, The Favourite Best Actor Rami Malek, Bohemian Rhapsody Oscars are actress Best Supporting Actress Regina King, Cicely Tyson, com- If Beale Street Could Talk poser Lalo Schi- Best Supporting Actor Mahershala Ali, Green Book frin and publicist Best Foreign Film Roma (Mexico) Marvin Levy while producers Kathleen Best Animated Feature Film Spider-Man: Into The Spider-Verse Kennedy and Frank Best Original Screenplay Green Book Gustavo Dudamel and the Los Angeles Philharmonic perform on stage during the In Memoriam Marshall receive the tribute segment. Irving G Thalberg Best Adapted Screenplay BlacKkKlansman Memorial Award. Best Original Score Black Panther t’s fi nally Oscar day and the the redoubtable Glenn Close. Period. End Of Sentence, set in The Oscars have Best Original Song Shallow from A Star Is Born I91st Academy Awards in Los Rami Malek won Best Actor India, won Best Documentary been mired in con- Angeles saw Regina King tak- for his performance as Freddie Short. -

Annual Return – MGT-7
FORM NO. MGT-7 Annual Return [Pursuant to sub-Section(1) of section 92 of the Companies Act, 2013 and sub-rule (1) of rule 11of the Companies (Management and Administration) Rules, 2014] Form language English Hindi Refer the instruction kit for filing the form. I. REGISTRATION AND OTHER DETAILS (i) * Corporate Identification Number (CIN) of the company L14102TG1991PLC013299 Pre-fill Global Location Number (GLN) of the company * Permanent Account Number (PAN) of the company AABCP2100Q (ii) (a) Name of the company POKARNA LIMITED (b) Registered office address 1ST FLOOR, 105,SURYA TOWERS, SECUNDERABAD. A.P Telangana 500003 India (c) *e-mail ID of the company [email protected] (d) *Telephone number with STD code 04027897722 (e) Website www.pokarna.com (iii) Date of Incorporation 09/10/1991 (iv) Type of the Company Category of the Company Sub-category of the Company Public Company Company limited by shares Indian Non-Government company (v) Whether company is having share capital Yes No (vi) *Whether shares listed on recognized Stock Exchange(s) Yes No Page 1 of 15 (a) Details of stock exchanges where shares are listed S. No. Stock Exchange Name Code 1 B.S.E Limited 1 2 National Stock Exchange of India 1,024 (b) CIN of the Registrar and Transfer Agent U72400TG2017PTC117649 Pre-fill Name of the Registrar and Transfer Agent KFIN TECHNOLOGIES PRIVATE LIMITED Registered office address of the Registrar and Transfer Agents Selenium, Tower B, Plot No- 31 & 32, Financial District, Nanakramguda, Serilingampally (vii) *Financial year From date 01/04/2020 (DD/MM/YYYY) To date 31/03/2021 (DD/MM/YYYY) (viii) *Whether Annual general meeting (AGM) held Yes No (a) If yes, date of AGM (b) Due date of AGM 30/09/2021 (c) Whether any extension for AGM granted Yes No (f) Specify the reasons for not holding the same II. -

Employee Salary Details of Guntur Division for the Month of September 2020 से��ट�बर 2020 के मह�ने के �लए गंटु र मंडल का कमचार� � वेतन �ववरण S.No
IPAS Reports EMPLOYEE SALARY DETAILS OF GUNTUR DIVISION FOR THE MONTH OF SEPTEMBER 2020 सेटबर 2020 के महने के लए गंटु र मंडल का कमचार वेतन ववरण S.NO. GROSSPAY .सं. EMPNAME कमचार का नाम DESIGNATION पदनाम DESCRIPTION ववरण सकल भुगतान 1 Y V RAMANA ADFM SALARY BILL OF GAZETTED OFFICERS OF Sr.D.F.M OFFICE/GUNTUR. 132126 2 K RANGA SAI BABU ADFM SALARY BILL OF GAZETTED OFFICERS OF Sr.D.F.M OFFICE/GUNTUR. 132126 3 B V SUDHAKAR BABU DFM SALARY BILL OF GAZETTED OFFICERS OF Sr.D.F.M OFFICE/GUNTUR. 104905 4 PILLI SATISH BABU SE(IT) SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. 63552 5 MANORANJAN MISHAL Sr. SO Acct SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. 88218 6 N.SWAMULU Sr. SO Acct SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. 146284 7 AVV VENUGOPALA RAO STENO SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. 115626 8 J.SREE NAGA KUMAR AC SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. 33462 9 P.V.SESHAGIRI RAO Sr. SO Acct SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. 159528 10 MANDLA VENKATA NARASAIAH JAA SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. 68074 11 K.CHIRANJEEVI JAA SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. 68074 12 P PRATHAP SE(IT) SALARY BILL OF NON-GAZETTED STAFF OF Sr.D.F.M OFFICE/GUNTUR. -
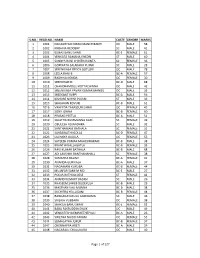
S.No. Regd.No. Name Caste Gender Marks 1 1001
S.NO. REGD.NO. NAME CASTE GENDER MARKS 1 1001 NAGASHYAM KIRAN MANCHIKANTI OC MALE 58 2 1002 KRISHNA REDDERY SC MALE 41 3 1003 ELMAS BANU SHAIK BC-E FEMALE 61 4 1004 VENKATA RAMANA KHEDRI ST MALE 60 5 1005 SANDYA RANI CHINTHAKUNTA SC FEMALE 36 6 1006 GOPINATH SALAKARU PUJARI SC MALE 28 7 1007 SREENIVASA REDDY GOTLURI OC MALE 78 8 1008 LEELA RANI B BC-A FEMALE 57 9 1009 RADHIKA KONDA OC FEMALE 30 10 1010 SREEDHAR M BC-D MALE 68 11 1011 CHANDRAMOULI KOTTACHINNA OC MALE 42 12 1012 SREENIVASA PAVAN KUMAR MANGU OC MALE 35 13 1013 SREEKANT SUPPI BC-A MALE 56 14 1014 KISHORE NAYAK PUJARI ST MALE 39 15 1015 SHAJAHAN KOVURI BC-B MALE 61 16 1016 VAHEEDA TABASSUM SHAIK OC FEMALE 45 17 1017 SONY JONNA BC-B FEMALE 60 18 1018 PRASAD PEETLA BC-A MALE 51 19 1019 SUJATHA BUMMANNA GARI SC FEMALE 49 20 1020 OBULESH ADIANDHRA SC MALE 32 21 1021 SANTHAMANI BATHALA SC FEMALE 31 22 1022 SARASWATHI GOLLA BC-D FEMALE 47 23 1023 LAVANYA GAJULA OC FEMALE 55 24 1024 SATEESH KUMAR MAHESWARAM BC-B MALE 38 25 1025 KRANTHI NALLAGATLA BC-B FEMALE 33 26 1026 RAVI KUMAR BATHALA BC-B MALE 68 27 1027 ADI LAKSHMI BANTHANAHALL SC FEMALE 38 28 1028 SAMATHA BALIMI BC-A FEMALE 41 29 1030 ANANDA GURIKALA BC-A MALE 37 30 1031 NAGAMANI KURUBA BC-B FEMALE 44 31 1032 MUJAFAR SAMI M MD BC-E MALE 27 32 1033 POOJA RATHOD DESE ST FEMALE 42 33 1034 ANAND KUMART BADIGI SC MALE 26 34 1035 KHASEEM SAHEB DUDEKULA BC-B MALE 29 35 1036 MASTHAN VALI MUNNA BC-B MALE 38 36 1037 SUCHITRA YELLUGANI BC-B FEMALE 44 37 1038 RANGANAYAKULU GUDIDAMA SC MALE 46 38 1039 SAILAJA VUBBARA OC FEMALE 38 39 1040 SHAKILA BANU SHAIK BC-E FEMALE 52 40 1041 BABA FAKRUDDIN SHAIK OC MALE 49 41 1042 VENKATESH DEMAKETHEPALLI BC-A MALE 26 42 1043 SWETHA NAIDU PAKAM OC FEMALE 55 43 1044 SUMALATHA JUKUR BC-B FEMALE 37 44 1047 CHENNAPPA ARETI BC-A MALE 29 45 1048 NAGARAJU CHALUKURU OC MALE 40 Page 1 of 127 S.NO.