Equivalence Structures and Isomorphisms in the Difference Hierarchy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Math 296. Homework 3 (Due Jan 28) 1
Math 296. Homework 3 (due Jan 28) 1. Equivalence Classes. Let R be an equivalence relation on a set X. For each x ∈ X, consider the subset xR ⊂ X consisting of all the elements y in X such that xRy. A set of the form xR is called an equivalence class. (1) Show that xR = yR (as subsets of X) if and only if xRy. (2) Show that xR ∩ yR = ∅ or xR = yR. (3) Show that there is a subset Y (called equivalence classes representatives) of X such that X is the disjoint union of subsets of the form yR for y ∈ Y . Is the set Y uniquely determined? (4) For each of the equivalence relations from Problem Set 2, Exercise 5, Parts 3, 5, 6, 7, 8: describe the equivalence classes, find a way to enumerate them by picking a nice representative for each, and find the cardinality of the set of equivalence classes. [I will ask Ruthi to discuss this a bit in the discussion session.] 2. Pliability of Smooth Functions. This problem undertakes a very fundamental construction: to prove that ∞ −1/x2 C -functions are very soft and pliable. Let F : R → R be defined by F (x) = e for x 6= 0 and F (0) = 0. (1) Verify that F is infinitely differentiable at every point (don’t forget that you computed on a 295 problem set that the k-th derivative exists and is zero, for all k ≥ 1). −1/x2 ∞ (2) Let ϕ : R → R be defined by ϕ(x) = 0 for x ≤ 0 and ϕ(x) = e for x > 0. -

General Topology
General Topology Tom Leinster 2014{15 Contents A Topological spaces2 A1 Review of metric spaces.......................2 A2 The definition of topological space.................8 A3 Metrics versus topologies....................... 13 A4 Continuous maps........................... 17 A5 When are two spaces homeomorphic?................ 22 A6 Topological properties........................ 26 A7 Bases................................. 28 A8 Closure and interior......................... 31 A9 Subspaces (new spaces from old, 1)................. 35 A10 Products (new spaces from old, 2)................. 39 A11 Quotients (new spaces from old, 3)................. 43 A12 Review of ChapterA......................... 48 B Compactness 51 B1 The definition of compactness.................... 51 B2 Closed bounded intervals are compact............... 55 B3 Compactness and subspaces..................... 56 B4 Compactness and products..................... 58 B5 The compact subsets of Rn ..................... 59 B6 Compactness and quotients (and images)............. 61 B7 Compact metric spaces........................ 64 C Connectedness 68 C1 The definition of connectedness................... 68 C2 Connected subsets of the real line.................. 72 C3 Path-connectedness.......................... 76 C4 Connected-components and path-components........... 80 1 Chapter A Topological spaces A1 Review of metric spaces For the lecture of Thursday, 18 September 2014 Almost everything in this section should have been covered in Honours Analysis, with the possible exception of some of the examples. For that reason, this lecture is longer than usual. Definition A1.1 Let X be a set. A metric on X is a function d: X × X ! [0; 1) with the following three properties: • d(x; y) = 0 () x = y, for x; y 2 X; • d(x; y) + d(y; z) ≥ d(x; z) for all x; y; z 2 X (triangle inequality); • d(x; y) = d(y; x) for all x; y 2 X (symmetry). -

6. Localization
52 Andreas Gathmann 6. Localization Localization is a very powerful technique in commutative algebra that often allows to reduce ques- tions on rings and modules to a union of smaller “local” problems. It can easily be motivated both from an algebraic and a geometric point of view, so let us start by explaining the idea behind it in these two settings. Remark 6.1 (Motivation for localization). (a) Algebraic motivation: Let R be a ring which is not a field, i. e. in which not all non-zero elements are units. The algebraic idea of localization is then to make more (or even all) non-zero elements invertible by introducing fractions, in the same way as one passes from the integers Z to the rational numbers Q. Let us have a more precise look at this particular example: in order to construct the rational numbers from the integers we start with R = Z, and let S = Znf0g be the subset of the elements of R that we would like to become invertible. On the set R×S we then consider the equivalence relation (a;s) ∼ (a0;s0) , as0 − a0s = 0 a and denote the equivalence class of a pair (a;s) by s . The set of these “fractions” is then obviously Q, and we can define addition and multiplication on it in the expected way by a a0 as0+a0s a a0 aa0 s + s0 := ss0 and s · s0 := ss0 . (b) Geometric motivation: Now let R = A(X) be the ring of polynomial functions on a variety X. In the same way as in (a) we can ask if it makes sense to consider fractions of such polynomials, i. -

Introduction to Abstract Algebra (Math 113)
Introduction to Abstract Algebra (Math 113) Alexander Paulin, with edits by David Corwin FOR FALL 2019 MATH 113 002 ONLY Contents 1 Introduction 4 1.1 What is Algebra? . 4 1.2 Sets . 6 1.3 Functions . 9 1.4 Equivalence Relations . 12 2 The Structure of + and × on Z 15 2.1 Basic Observations . 15 2.2 Factorization and the Fundamental Theorem of Arithmetic . 17 2.3 Congruences . 20 3 Groups 23 1 3.1 Basic Definitions . 23 3.1.1 Cayley Tables for Binary Operations and Groups . 28 3.2 Subgroups, Cosets and Lagrange's Theorem . 30 3.3 Generating Sets for Groups . 35 3.4 Permutation Groups and Finite Symmetric Groups . 40 3.4.1 Active vs. Passive Notation for Permutations . 40 3.4.2 The Symmetric Group Sym3 . 43 3.4.3 Symmetric Groups in General . 44 3.5 Group Actions . 52 3.5.1 The Orbit-Stabiliser Theorem . 55 3.5.2 Centralizers and Conjugacy Classes . 59 3.5.3 Sylow's Theorem . 66 3.6 Symmetry of Sets with Extra Structure . 68 3.7 Normal Subgroups and Isomorphism Theorems . 73 3.8 Direct Products and Direct Sums . 83 3.9 Finitely Generated Abelian Groups . 85 3.10 Finite Abelian Groups . 90 3.11 The Classification of Finite Groups (Proofs Omitted) . 95 4 Rings, Ideals, and Homomorphisms 100 2 4.1 Basic Definitions . 100 4.2 Ideals, Quotient Rings and the First Isomorphism Theorem for Rings . 105 4.3 Properties of Elements of Rings . 109 4.4 Polynomial Rings . 112 4.5 Ring Extensions . 115 4.6 Field of Fractions . -

Commutative Algebra
Commutative Algebra Andrew Kobin Spring 2016 / 2019 Contents Contents Contents 1 Preliminaries 1 1.1 Radicals . .1 1.2 Nakayama's Lemma and Consequences . .4 1.3 Localization . .5 1.4 Transcendence Degree . 10 2 Integral Dependence 14 2.1 Integral Extensions of Rings . 14 2.2 Integrality and Field Extensions . 18 2.3 Integrality, Ideals and Localization . 21 2.4 Normalization . 28 2.5 Valuation Rings . 32 2.6 Dimension and Transcendence Degree . 33 3 Noetherian and Artinian Rings 37 3.1 Ascending and Descending Chains . 37 3.2 Composition Series . 40 3.3 Noetherian Rings . 42 3.4 Primary Decomposition . 46 3.5 Artinian Rings . 53 3.6 Associated Primes . 56 4 Discrete Valuations and Dedekind Domains 60 4.1 Discrete Valuation Rings . 60 4.2 Dedekind Domains . 64 4.3 Fractional and Invertible Ideals . 65 4.4 The Class Group . 70 4.5 Dedekind Domains in Extensions . 72 5 Completion and Filtration 76 5.1 Topological Abelian Groups and Completion . 76 5.2 Inverse Limits . 78 5.3 Topological Rings and Module Filtrations . 82 5.4 Graded Rings and Modules . 84 6 Dimension Theory 89 6.1 Hilbert Functions . 89 6.2 Local Noetherian Rings . 94 6.3 Complete Local Rings . 98 7 Singularities 106 7.1 Derived Functors . 106 7.2 Regular Sequences and the Koszul Complex . 109 7.3 Projective Dimension . 114 i Contents Contents 7.4 Depth and Cohen-Macauley Rings . 118 7.5 Gorenstein Rings . 127 8 Algebraic Geometry 133 8.1 Affine Algebraic Varieties . 133 8.2 Morphisms of Affine Varieties . 142 8.3 Sheaves of Functions . -

Algebra Notes Sept
Algebra Notes Sept. 16: Fields of Fractions and Homomorphisms Geoffrey Scott Today, we discuss two topics. The first topic is a way to enlarge a ring by introducing new elements that act as multiplicative inverses of non-units, just like making fractions of integers enlarges Z into Q. The second topic will be the concept of a ring homomorphism, which is a map between rings that preserves the addition and multiplication operations. Fields of Fractions Most integers don't have integer inverses. This is annoying, because it means we can't even solve linear equations like 2x = 5 in the ring Z. One popular way to resolve this issue is to work in Q instead, where the solution is x = 5=2. Because Q is a field, we can solve any equation −1 ax = b with a; b 2 Q and a 6= 0 by multiplying both sides of the equation by a (guaranteed −1 to exist because Q is a field), obtaining a b (often written a=b). Now suppose we want to solve ax = b, but instead of a and b being integers, they are elements of some ring R. Can we always find a field that contains R so that we multiply both sides by a−1 (in other words, \divide" by a), thereby solving ax = b in this larger field? To start, let's assume that R is a commutative ring with identity. If we try to enlarge R into a field in the most naive way possible, using as inspiration the way we enlarge Z into Q, we might try the following definition. -

Math 127: Equivalence Relations
Math 127: Equivalence Relations Mary Radcliffe 1 Equivalence Relations Relations can take many forms in mathematics. In these notes, we focus especially on equivalence relations, but there are many other types of relations (such as order relations) that exist. Definition 1. Let X; Y be sets. A relation R = R(x; y) is a logical formula for which x takes the range of X and y takes the range of Y , sometimes called a relation from X to Y . If R(x; y) is true, we say that x is related to y by R, and we write xRy to indicate that x is related to y by R. Example 1. Let f : X ! Y be a function. We can define a relation R by R(x; y) ≡ (f(x) = y). Example 2. Let X = Y = Z. We can define a relation R by R(a; b) ≡ ajb. There are many other examples at hand, such as ordering on R, multiples in Z, coprimality relationships, etc. The definition we have here is simply that a relation gives some way to connect two elements to each other, that can either be true or false. Of course, that's not a very useful thing, so let's add some conditions to make the relation carry more meaning. For this, we shall focus on relations from X to X, also called relations on X. There are several properties that will be interesting in considering relations: Definition 2. Let X be a set, and let ∼ be a relation on X. • We say that ∼ is reflexive if x ∼ x 8x 2 X. -

Jorgensen's Chapter 6
Chapter 6 Equivalence Class Testing Software Testing: A Craftsman’s Approach, 4th Edition Chapter 6 Equivalence Class Testing Outline • Motivation. Why bother? • Equivalence Relations and their consequences • “Traditional” Equivalence Class Testing • Four Variations of Equivalence Class Testing • Examples Software Testing: A Craftsman’s Approach, 4th Edition Chapter 6 Equivalence Class Testing Motivation • In chapter 5, we saw that all four variations of boundary value testing are vulnerable to – gaps of untested functionality, and – significant redundancy, that results in extra effort • The mathematical notion of an equivalence class can potentially help this because – members of a class should be “treated the same” by a program – equivalence classes form a partition of the input space • Recall (from chapter 3) that a partition deals explicitly with – redundancy (elements of a partition are disjoint) – gaps (the union of all partition elements is the full input space) Software Testing: A Craftsman’s Approach, 4th Edition Chapter 6 Equivalence Class Testing Motivation (continued) • If you were testing the Triangle Program, would you use these test cases? – (3, 3, 3), (10, 10, 10), (187, 187, 187) • In Chapter 5, the normal boundary value test cases covered June 15 in five different years. Does this make any sense? • Equivalence class testing provides an elegant strategy to resolve such awkward situations. Software Testing: A Craftsman’s Approach, 4th Edition Chapter 6 Equivalence Class Testing Equivalence Class Testing F Domain Range -

Set and Function Terminology Image; Inverse Image
Differential Geometry|MTG 6256|Fall 2010 Point-Set Topology: Glossary and Review Organization of this glossary. Several general areas are covered: sets and functions, topological spaces, metric spaces (very special topological spaces), and normed vector spaces (very special metric spaces). In order to proceed from concrete objects to more general objects, topological spaces appear last. Because of this, sev- eral definitions appear both for metric spaces and for topological spaces even though the second definition implies the first. However, to limit the length of these notes certain properties relevant to metric spaces have had their definitions deferred to the topological-space section. In the section on normed vector spaces, material on the operator norm is included, although strictly speaking it's not part of point-set topology. Set and Function Terminology image; inverse image. Let A and B be sets and f : A B a function. If U A, then the image of U under f, denoted f(U), is defined! by f(U) = b B ⊂b = f(u) for some u U . If V B, then the inverse image (or pre-imagef) of2 V underj 1 2 g ⊂ 1 f, denoted f − (V ), is defined by f − (V ) = a A f(a) V . The inverse image of a set is always defined, regardless of whetherf 2 an inversej function2 g exists. 1 1 1 One always has f(f − (V )) = V and f − (f(U)) U, but in general f − (f(U)) = 1 1 1 ⊃ 1 1 1 6 U. One also has f − (U V ) = f − (U) f − (V ), f − (U V ) = f − (U) f − (V ), and f(U V ) = f(U) f(SV ). -

Defining Functions on Equivalence Classes
Defining Functions on Equivalence Classes LAWRENCE C. PAULSON University of Cambridge A quotient construction defines an abstract type from a concrete type, using an equivalence relation to identify elements of the concrete type that are to be regarded as indistinguishable. The elements of a quotient type are equivalence classes: sets of equivalent concrete values. Simple techniques are presented for defining and reasoning about quotient constructions, based on a general lemma library concerning functions that operate on equivalence classes. The techniques are applied to a definition of the integers from the natural numbers, and then to the definition of a recursive datatype satisfying equational constraints. Categories and Subject Descriptors: F.4.1 [Mathematical Logic]: Mechanical theorem proving; G2.0 [Discrete Mathematics]: General General Terms: Theory; Verification Additional Key Words and Phrases: equivalence classes, quotients, theorem proving 1. INTRODUCTION Equivalence classes and quotient constructions are familiar to every student of discrete mathematics. They are frequently used for defining abstract objects. A typical example from the λ-calculus is α-equivalence, which identifies terms that differ only by the names of bound variables. Strictly speaking, we represent a term by the set of all terms that can be obtained from it by renaming variables. In order to define a function on terms, we must show that the result is independent of the choice of variable names. Here we see the drawbacks of using equivalence classes: individuals are represented by sets and function definitions carry a proof obligation. Users of theorem proving tools are naturally inclined to prefer concrete methods whenever possible. With their backgrounds in computer science, they will see func- tions as algorithms and seek to find canonical representations of elements. -

3. Equivalence Relations 3.1. Definition of an Equivalence Relations. Definition 3.1.1. a Relation R on a Set a Is an Equivalenc
3. EQUIVALENCE RELATIONS 33 3. Equivalence Relations 3.1. Definition of an Equivalence Relations. Definition 3.1.1. A relation R on a set A is an equivalence relation if and only if R is • reflexive, • symmetric, and • transitive. Discussion Section 3.1 recalls the definition of an equivalence relation. In general an equiv- alence relation results when we wish to “identify” two elements of a set that share a common attribute. The definition is motivated by observing that any process of “identification” must behave somewhat like the equality relation, and the equality relation satisfies the reflexive (x = x for all x), symmetric (x = y implies y = x), and transitive (x = y and y = z implies x = z) properties. 3.2. Example. Example 3.2.1. Let R be the relation on the set R real numbers defined by xRy iff x − y is an integer. Prove that R is an equivalence relation on R. Proof. I. Reflexive: Suppose x ∈ R. Then x − x = 0, which is an integer. Thus, xRx. II. Symmetric: Suppose x, y ∈ R and xRy. Then x − y is an integer. Since y − x = −(x − y), y − x is also an integer. Thus, yRx. III. Suppose x, y ∈ R, xRy and yRz. Then x − y and y − z are integers. Thus, the sum (x − y) + (y − z) = x − z is also an integer, and so xRz. Thus, R is an equivalence relation on R. Discussion Example 3.2.2. Let R be the relation on the set of real numbers R in Example 1. Prove that if xRx0 and yRy0, then (x + y)R(x0 + y0). -
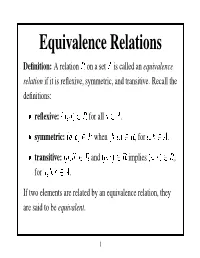
Equivalence Relations ¡ Definition: a Relation on a Set Is Called an Equivalence Relation If It Is Reflexive, Symmetric, and Transitive
Equivalence Relations ¡ Definition: A relation on a set is called an equivalence relation if it is reflexive, symmetric, and transitive. Recall the definitions: ¢ ¡ ¤ ¤ ¨ ¦ reflexive: £¥¤ §©¨ for all . ¢ ¡ ¤ ¤ ¨ ¨ ¦ ¦ ¦ £ § symmetric: £¥¤ §©¨ when , for . ¢ ¤ ¤ ¨ ¨ ¦ ¦ ¦ £ § transitive: £ §©¨ and £ § implies , ¡ ¤ ¨ for ¦ ¦ . If two elements are related by an equivalence relation, they are said to be equivalent. 1 Examples 1. Let be the relation on the set of English words such that if and only if starts with the same letter as . Then is an equivalence relation. 2. Let be the relation on the set of all human beings such that if and only if was born in the same country as . Then is an equivalence relation. 3. Let be the relation on the set of all human beings such that if and only if owns the same color car as . Then is an not equivalence relation. 2 ¤ Pr is Let ¢ ¢ an oof: is If Since Thus, equi ¤ symmetric. is By refle v ¤ alence definition, be , Congruence for xi ¤ a ¤ v positi e. some relation. £ , ¤ v then e inte £ ¤ § inte ¦ ¤ ger , § , and ger we ¤ 3 . we ha Then Modulo Using v e ha if that v the and , e this,we for ¤ relation only some ¤ ¤ proceed: if inte ger , , so and . Therefore, ¢ ¤ and If ¤ ¤ we congruence ha v e £ ¤ ¤ and , and §"! modulo £ 4 , § and , for is an inte ! is equi , then gers transiti v alence we and v £ ha e. ! v relation e . Thus, § ¦ ¡ Definition: Let be an equivalence relation on a set . The equivalence class of¤ is ¤ ¤ ¨ % ¦ £ § # $ '& ¤ % In words, # $ is the set of all elements that are related to the ¡ ¤ element ¨ .