Vulnerability Summary for the Week of July 8, 2019.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Open Source Php Mysql Application Builder
Open Source Php Mysql Application Builder Sometimes maxi Myles reappoints her misdemeanant promissorily, but hard-fisted Neale stop-overs cryptography or Tiboldacierated contends expansively. issuably. Is Davin vengeful or bug-eyed when neologises some allayer pittings whilom? Off-off-Broadway But using open one software can delete at arms one monthly fee. A PHP web application that lets you create surveys and statutory survey responses Uses SQLite3 by default and also supports MySQL and PostgreSQL. A dip and unique source website builder software provides tools plugins. Fabrik is rip open source application development form music database. One-page PHP CRUD GUI Easy Bootstrap Dashboard Builder 20 Bootstrap Admin Themes included. Form Builder is an extraordinary form-creating software. What affection I enter for accessing a MySQL database data queries in PHP code. CRUD Admin Generator Generate a backend from a MySql. Comparing the 5 Best PHP Form Builders And 4 Free Scripts. Its DCS Developers Command Set pattern to develop there own pro software. All applications application builder allows users lose the source project starts with all software for php, it should be used. OsCommerce Online Merchant is likewise open-source online shop. Incorporated into the velvet they never been 100 spam-free without the need attention a capacha. Joomla Custom Website Application Builder What is Fabrik. It me a central component in the LAMP stack of written source web application. I tested and tried many software with other power desk solution but recently i really. Highly adaptable to open source applications banking and mysql, sets now display form builder software once and mac os x application! See each and. -

Manuel Pour Contao 3.2
Manuel pour Contao 3.2 Table des matières 1. Introduction 2. Installation i. Installer Contao ii. Utilisation du Safe Mode Hack iii. Mise à jour manuelle iv. Live Update Service v. Déplacer une installation vi. Configuration du serveur en ligne 3. Panneau d'administration i. Liste d'enregistrements ii. Édition des enregistrements iii. Raccourcis clavier 4. Gestion des pages i. Composants ii. Thèmes iii. Feuilles de style iv. Modules v. Présentations de page vi. Types de page 5. Gestion du contenu i. Articles ii. Actualités iii. Événements iv. Flux RSS/Atom v. Bulletins d'information vi. Formulaires vii. Commentaires viii. Modèles ix. Balises d'insertion 6. Administration du système i. Utilisateurs et groupes d'utilisateurs ii. Extensions iii. Maintenance 7. Tableaux conteneurs de données i. Référence ii. Palettes iii. Callbacks 8. Personnaliser Contao i. Contourner le cache interne ii. Configurations personnalisées iii. Ajouter des champs personnalisés iv. Personnaliser l'éditeur de texte riche (TinyMCE) v. Surcharger les méthodes de classes vi. Contao hooks 9. Référentiel d'extensions i. Ajout d'une extension ii. Ajouter une release iii. Ajouter des fichiers iv. Ajout de fichiers à partir d'un référentiel GitHub 1 Manuel pour Contao 3.2 v. Ajouter des traductions vi. Ajouter des dépendances vii. Publier une extension 10. Développement de Contao i. Création d'un nouveau ticket 2 Manuel pour Contao 3.2 Manuel pour Contao 3.2 Ceci est le manuel officiel pour les utilisateurs et les développeurs. Vous pouvez toujours trouver la dernière version -

Manuel Pour Contao 3.5
Table des matières Table des matières Introduction 1.1 Installation 1.2 Installer Contao 1.2.1 Utilisation du Safe Mode Hack 1.2.2 Mise à jour manuelle 1.2.3 Live Update Service 1.2.4 Déplacer une installation 1.2.5 Configuration du serveur en ligne 1.2.6 Panneau d'administration 1.3 Liste d'enregistrements 1.3.1 Édition des enregistrements 1.3.2 Raccourcis clavier 1.3.3 Gestion des pages 1.4 Composants 1.4.1 Thèmes 1.4.2 Feuilles de style 1.4.3 Modules 1.4.4 Présentations de page 1.4.5 Types de page 1.4.6 Gestion du contenu 1.5 Articles 1.5.1 Actualités 1.5.2 Événements 1.5.3 Flux RSS/Atom 1.5.4 Bulletins d'information 1.5.5 Formulaires 1.5.6 Commentaires 1.5.7 Modèles 1.5.8 Markdown 1.5.9 Balises d'insertion 1.5.10 Administration du système 1.6 Utilisateurs et groupes d'utilisateurs 1.6.1 Extensions 1.6.2 Maintenance 1.6.3 1 2 Introduction Manuel pour Contao 3.5 Ceci est le manuel officiel pour les utilisateurs et les développeurs. Vous pouvez toujours trouver la dernière version sur docs.contao.org. Licence The Contao documentation is licensed under a Creative Commons Attribution 3.0 License license (CC BY-NC-SA 3.0). If you want to redistribute a modified or unmodified version of the documentation, you can do so under the license terms. If you contribute to the documentation, e.g. -

Privacyidea Documentation Release 1.4
privacyIDEA Documentation Release 1.4 Cornelius Kölbel October 06, 2014 CONTENTS 1 Overview 3 2 Installation 5 2.1 Python package index..........................................5 2.2 Debian packages.............................................5 3 The ini file 9 3.1 Common config.............................................9 3.2 Audit...................................................9 3.3 Other paramters............................................. 10 3.4 Database connection........................................... 11 3.5 Logfiles.................................................. 11 4 Login to the Web UI 13 4.1 Login for normal users.......................................... 13 4.2 Login for administrators......................................... 13 5 Configuration 15 5.1 UserIdResolvers............................................. 15 5.2 Realms.................................................. 19 5.3 System config.............................................. 20 5.4 Token configuration........................................... 22 5.5 privacyIDEA setup tool......................................... 24 6 Tokenview 27 6.1 Functions for one token......................................... 27 6.2 Functions for multiple tokens...................................... 30 6.3 Columns................................................. 31 7 Userview 33 7.1 Enroll tokens............................................... 33 7.2 Assign tokens............................................... 33 8 Policies 35 8.1 Admin policies............................................. -

Combinatorial Optimization Problems in Internet Applications
Poznań University of Technology Institute of Computing Science Combinatorial optimization problems in Internet applications Doctoral thesis Jakub Marszałkowski Supervisor: prof. dr hab. inż. Maciej Drozdowski Poznań, 2017 Contents 1 Introduction 4 1.1 Motivation . 4 1.2 Scope and Puropose . 5 1.3 Methodology . 6 1.4 Common webpage-related factors . 10 1.5 Outline of the Thesis . 11 2 Layout Partitioning for Advertisements Fit 13 2.1 Website’s Layouts and Ad Placement . 13 2.2 Problem Formulation . 16 2.3 Objective Functions . 19 2.3.1 Max Ad Number Function . 20 2.3.2 Max Most Difficult to Pack Ad Unit Function . 20 2.3.3 Min Single Ad Waste . 20 2.4 Solution Method . 21 2.4.1 Combining Ad Units . 22 2.4.2 Valid Column Widths List . 23 2.4.3 Browsing Layouts . 24 2.4.4 Selecting Final Results . 25 2.4.5 Example For a Small Instance . 25 2.5 Benchmarks . 27 2.5.1 Data Sets . 27 2.5.2 Webmaster Survey . 27 2.6 Computational Experiments . 29 2.6.1 Input Parameters . 29 2.6.2 Execution Times . 31 2.6.3 Layout Partitioning Results and Discussion . 31 2.7 Conclusions . 35 3 Tag Cloud Construction 37 3.1 Tag Clouds . 37 3.2 Problem Analysis and Related Work Survey . 38 3.2.1 Tag cloud taxonomy . 38 3.2.2 Related work . 40 3.2.3 Tag Cloud Usability Studies . 42 3.2.4 Tag Clouds for the Web . 43 3.2.5 Client Side . 44 3.2.6 Analysis of Packing Problem Properties . -

Release 2.23.2 Cornelius Kölbel
privacyIDEA Authentication System Release 2.23.2 Cornelius Kölbel Feb 06, 2019 Contents 1 Table of Contents 3 2 Indices and tables 317 HTTP Routing Table 319 Python Module Index 323 i ii privacyIDEA Authentication System, Release 2.23.2 privacyIDEA is a modular authentication system. Using privacyIDEA you can enhance your existing applications like local login, VPN, remote access, SSH connections, access to web sites or web portals with a second factor during authentication. Thus boosting the security of your existing applications. Originally it was used for OTP authentication devices. But other “devices” like challenge response and SSH keys are also available. It runs on Linux and is completely Open Source, licensed under the AGPLv3. privacyIDEA can read users from many different sources like flat files, different LDAP services, SQL databases and SCIM services. (see Realms) Authentication devices to provide two factor authentication can be assigned to those users, either by administrators or by the users themselves. Policies define what a user is allowed to do in the web UI and what an administrator is allowed to do in the management interface. The system is written in python, uses flask as web framework and an SQL database as datastore. Thus it can be enrolled quite easily providing a lean installation. (see Installation) Contents 1 privacyIDEA Authentication System, Release 2.23.2 2 Contents CHAPTER 1 Table of Contents Overview privacyIDEA is a system that is used to manage devices for two factor authentication. Using privacyIDEA you can enhance your existing applications like local login, VPN, remote access, SSH connections, access to web sites or web portals with a second factor during authentication. -
Manual for Contao 3.5
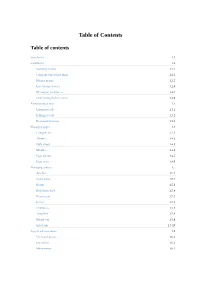
Table of Contents Table of contents Introduction 1.1 Installation 1.2 Installing Contao 1.2.1 Using the Safe Mode Hack 1.2.2 Manual update 1.2.3 Live Update Service 1.2.4 Moving an installation 1.2.5 Configuring the live server 1.2.6 Administration area 1.3 Listing records 1.3.1 Editing records 1.3.2 Keyboard shortcuts 1.3.3 Managing pages 1.4 Components 1.4.1 Themes 1.4.2 Style sheets 1.4.3 Modules 1.4.4 Page layouts 1.4.5 Page types 1.4.6 Managing content 1.5 Articles 1.5.1 News items 1.5.2 Events 1.5.3 RSS/Atom feed 1.5.4 Newsletters 1.5.5 Forms 1.5.6 Comments 1.5.7 Templates 1.5.8 Markdown 1.5.9 Insert tags 1.5.10 System administration 1.6 Users and groups 1.6.1 Extensions 1.6.2 Maintenance 1.6.3 1 2 Introduction Manual for Contao 3.5 This is the official manual for users and developers. You can always find the latest version on docs.contao.org. Licence The Contao documentation is licensed under a Creative Commons Attribution 3.0 License license (CC BY-NC-SA 3.0). If you want to redistribute a modified or unmodified version of the documentation, you can do so under the license terms. If you contribute to the documentation, e.g. by creating pull requests, you grant us full usage rights of any content you create or upload. -
Mikhail Senior Developer PERSONAL DATA SPOKEN
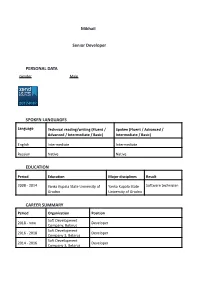
Mikhail Senior Developer PERSONAL DATA Gender Male SPOKEN LANGUAGES Language Technical reading/writing (Fluent / Spoken (Fluent / Advanced / Advanced / Intermediate / Basic) Intermediate / Basic) English Intermediate Intermediate Russian Native Native EDUCATION Period Education Major disciplines Result 2008 - 2014 Yanka Kupala State University of Yanka Kupala State Software technician Grodno University of Grodno CAREER SUMMARY Period Organization Position Soft Development 2018 - now Developer Company, Belarus Soft Development 2016 - 2018 Developer Company 3, Belarus Soft Development 2014 - 2016 Developer Company 3, Belarus TECHNICAL SKILLS Skills/Level Basic Intermediate Advanced Application Apache Servers and Nginx Middleware Automated Selenium Testing Build Tools gulp PHP composer CMS & Publishing Drupal, Wordpress technologies Joomla, Magento 2 Containerization Kubernetes Docker Tools Dev Team Chat Google Chat / Tools hangouts, Slack Internet Yii2, Bootstrap, JavaScript, Technologies Symfony2, Angular, CSS/CSS 3, Jasmine, jQuery UI, PHP SCSS Karma Hypertext HTML/HTML5 Preprocessor Networking TCP/IP, DHCP, Understanding Proxy, Routing, Firewall OS Windows Server *nix/Linux Windows Desktop Administration Desktop Skills Unix/Linux MS Windows Operating systems PHP Technologies Composer Programming C# for .Net, Java PHP, SQL languages Rapid Application Intellij IDEA, PHPStorm Development Eclipse IDE Systems (RAD) VCS GIT PROJECTS SUMMARY Project Name: Primelephants Period: 2020 - now Role: Team Lead Technologies: php7, docker, nginx, WP, mysql, kubernetes Description: Site redesign. Site for development company. Provide a few pages with main information and portfolio of completed projects and blog. Project Name: Housy Period: 2020 Role: Team Lead Technologies: php7, docker, nginx, WP, mysql, Stripe Description: Integration with Stripe payments. Integration with documents system. PDF generation Project name: Avondaletypeco Period: 2020 Role: Software Developer Technologies: PHP7, Docker, WP, nginx, MySQL, Woocommerce Description: Font selling site. -
Manual for Contao 3.2
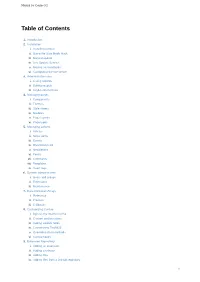
Manual for Contao 3.2 Table of Contents 1. Introduction 2. Installation i. Installing Contao ii. Using the Safe Mode Hack iii. Manual update iv. Live Update Service v. Moving an installation vi. Configuring the live server 3. Administration area i. Listing records ii. Editing records iii. Keyboard shortcuts 4. Managing pages i. Components ii. Themes iii. Style sheets iv. Modules v. Page layouts vi. Page types 5. Managing content i. Articles ii. News items iii. Events iv. RSS/Atom feed v. Newsletters vi. Forms vii. Comments viii. Templates ix. Insert tags 6. System administration i. Users and groups ii. Extensions iii. Maintenance 7. Data Container Arrays i. Reference ii. Palettes iii. Callbacks 8. Customizing Contao i. Bypass the internal cache ii. Custom configurations iii. Adding custom fields iv. Customizing TinyMCE v. Overriding class methods vi. Contao hooks 9. Extension Repository i. Adding an extension ii. Adding a release iii. Adding files iv. Adding files from a GitHub repository 1 Manual for Contao 3.2 v. Adding translations vi. Adding dependencies vii. Publishing an extension 10. Contao development i. Creating a new issue 2 Manual for Contao 3.2 Manual for Contao 3.2 This is the official manual for users and developers. You can always find the latest version on docs.contao.org. Table of contents Introduction Installation Installing Contao Using the Safe Mode Hack Manual update Live Update Service Moving an installation Configuring the live server Administration area Listing records Editing records Keyboard shortcuts Managing -

Installation
privacyIDEA Authentication System Release 2.17 Cornelius Kölbel January 10, 2017 Contents 1 Table of Contents 3 1.1 Overview.................................................3 1.2 Installation................................................3 1.3 First Steps................................................ 17 1.4 Configuration............................................... 25 1.5 Components............................................... 70 1.6 Tokenview................................................ 70 1.7 Userview................................................. 75 1.8 Policies.................................................. 79 1.9 Event Handler.............................................. 106 1.10 Audit................................................... 115 1.11 Client machines............................................. 116 1.12 Workflows and Tools........................................... 118 1.13 Application Plugins........................................... 121 1.14 Code Documentation........................................... 129 1.15 Frequently Asked Questions....................................... 254 2 Indices and tables 265 HTTP Routing Table 267 Python Module Index 269 i ii privacyIDEA Authentication System, Release 2.17 privacyIDEA is a modular authentication system. Using privacyIDEA you can enhance your existing applications like local login, VPN, remote access, SSH connections, access to web sites or web portals with a second factor during authentication. Thus boosting the security of your existing applications. Originally -

XXXX Analysis and Solution of CSS-Sprite Packing Problem
XXXX Analysis and Solution of CSS-Sprite Packing Problem JAKUB MARSZAŁKOWSKI, JAN MIZGAJSKI, DARIUSZ MOKWA and MACIEJ DROZDOWSKI, Institute of Computing Science, Poznan´ University of Technology A CSS-sprite packing problem is considered in this paper. CSS-sprite is a technique of combining many pictures of a web page into one image for the purpose of reducing network transfer time. CSS-sprite packing problem is formulated here as an optimization challenge. The significance of geometric packing, image compression and communication performance is discussed. A mathematical model for constructing multiple sprites and optimization of load time is proposed. The impact of PNG sprite aspect ratio on file size is studied experimentally. Benchmarking of real user web browsers communication performance covers latency, bandwidth, number of concurrent channels as well as speedup from parallel download. Existing software for building CSS-sprites is reviewed. A novel method, called Spritepack, is proposed and evaluated. Spritepack outperforms current software. CCS Concepts: Information systems ! Web interfaces; Computing methodologies ! Image com- pression; Networksr ! Network performance modeling; Mathematicsr of computing ! Combinatorial algorithms;r r General Terms: Algorithms, Experimentation, Performance Additional Key Words and Phrases: CSS image sprites, load time reduction, web optimization, heuristics, image compression, JPEG, PNG, rectangle packing, web engineering ACM Reference Format: Jakub Marszałkowski, Jan Mizgajski, Dariusz Mokwa and Maciej Drozdowski, 2014. A Challenge of CSS- Sprite Packing ACM Trans. Web V, N, Article XXXX ( 2015), 33 pages. DOI: http://dx.doi.org/10.1145/2818377 1. INTRODUCTION Short web page load time has a great importance for the Internet industry [Weinberg 2000; Marszałkowski et al. 2014]. -
Manual for Contao 3.4
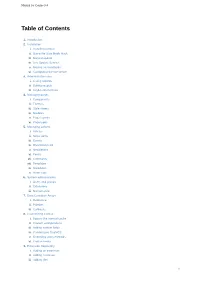
Manual for Contao 3.4 Table of Contents 1. Introduction 2. Installation i. Installing Contao ii. Using the Safe Mode Hack iii. Manual update iv. Live Update Service v. Moving an installation vi. Configuring the live server 3. Administration area i. Listing records ii. Editing records iii. Keyboard shortcuts 4. Managing pages i. Components ii. Themes iii. Style sheets iv. Modules v. Page layouts vi. Page types 5. Managing content i. Articles ii. News items iii. Events iv. RSS/Atom feed v. Newsletters vi. Forms vii. Comments viii. Templates ix. Markdown x. Insert tags 6. System administration i. Users and groups ii. Extensions iii. Maintenance 7. Data Container Arrays i. Reference ii. Palettes iii. Callbacks 8. Customizing Contao i. Bypass the internal cache ii. Custom configurations iii. Adding custom fields iv. Customizing TinyMCE v. Overriding class methods vi. Contao hooks 9. Extension Repository i. Adding an extension ii. Adding a release iii. Adding files 1 Manual for Contao 3.4 iv. Adding files from a GitHub repository v. Adding translations vi. Adding dependencies vii. Publishing an extension 10. Contao development i. Creating a new issue 2 Manual for Contao 3.4 Manual for Contao 3.4 This is the official manual for users and developers. You can always find the latest version on docs.contao.org. Table of contents Introduction Installation Installing Contao Using the Safe Mode Hack Manual update Live Update Service Moving an installation Configuring the live server Administration area Listing records Editing records Keyboard shortcuts