Guide for Newly Rooted Android Users a Free Guide Provided by the Team at Rescue Root, the Easiest Way to Root Your Android Device
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cross-Platform Analysis of Indirect File Leaks in Android and Ios Applications
Cross-Platform Analysis of Indirect File Leaks in Android and iOS Applications Daoyuan Wu and Rocky K. C. Chang Department of Computing, The Hong Kong Polytechnic University fcsdwu, [email protected] This paper was published in IEEE Mobile Security Technologies 2015 [47] with the original title of “Indirect File Leaks in Mobile Applications”. Victim App Abstract—Today, much of our sensitive information is stored inside mobile applications (apps), such as the browsing histories and chatting logs. To safeguard these privacy files, modern mobile Other systems, notably Android and iOS, use sandboxes to isolate apps’ components file zones from one another. However, we show in this paper that these private files can still be leaked by indirectly exploiting components that are trusted by the victim apps. In particular, Adversary Deputy Trusted we devise new indirect file leak (IFL) attacks that exploit browser (a) (d) parties interfaces, command interpreters, and embedded app servers to leak data from very popular apps, such as Evernote and QQ. Unlike the previous attacks, we demonstrate that these IFLs can Private files affect both Android and iOS. Moreover, our IFL methods allow (s) an adversary to launch the attacks remotely, without implanting malicious apps in victim’s smartphones. We finally compare the impacts of four different types of IFL attacks on Android and Fig. 1. A high-level IFL model. iOS, and propose several mitigation methods. four IFL attacks affect both Android and iOS. We summarize these attacks below. I. INTRODUCTION • sopIFL attacks bypass the same-origin policy (SOP), Mobile applications (apps) are gaining significant popularity which is enforced to protect resources originating from in today’s mobile cloud computing era [3], [4]. -

UPLC™ Universal Power-Line Carrier
UPLC™ Universal Power-Line Carrier CU4I-VER02 Installation Guide AMETEK Power Instruments 4050 N.W. 121st Avenue Coral Springs, FL 33065 1–800–785–7274 www.pulsartech.com THE BRIGHT STAR IN UTILITY COMMUNICATIONS March 2006 Trademarks All terms mentioned in this book that are known to be trademarks or service marks are listed below. In addition, terms suspected of being trademarks or service marks have been appropriately capital- ized. Ametek cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. This publication includes fonts and/or images from CorelDRAW which are protected by the copyright laws of the U.S., Canada and elsewhere. Used under license. IBM and PC are registered trademarks of the International Business Machines Corporation. ST is a registered trademark of AT&T Windows is a registered trademark of Microsoft Corp. Universal Power-Line Carrier Installation Guide ESD WARNING! YOU MUST BE PROPERLY GROUNDED, TO PREVENT DAMAGE FROM STATIC ELECTRICITY, BEFORE HANDLING ANY AND ALL MODULES OR EQUIPMENT FROM AMETEK. All semiconductor components used, are sensitive to and can be damaged by the discharge of static electricity. Be sure to observe all Electrostatic Discharge (ESD) precautions when handling modules or individual components. March 2006 Page i Important Change Notification This document supercedes the preliminary version of the UPLC Installation Guide. The following list shows the most recent publication date for the new information. A publication date in bold type indicates changes to that information since the previous publication. -

SMM Rootkits
SMM Rootkits: A New Breed of OS Independent Malware Shawn Embleton Sherri Sparks Cliff Zou University of Central Florida University of Central Florida University of Central Florida [email protected] [email protected] [email protected] ABSTRACT 1. INTRODUCTION The emergence of hardware virtualization technology has led to A rootkit consists of a set of programs that work to subvert the development of OS independent malware such as the Virtual control of an Operating System from its legitimate users [16]. If Machine based rootkits (VMBRs). In this paper, we draw one were asked to classify viruses and worms by a single defining attention to a different but related threat that exists on many characteristic, the first word to come to mind would probably be commodity systems in operation today: The System Management replication. In contrast, the single defining characteristic of a Mode based rootkit (SMBR). System Management Mode (SMM) rootkit is stealth. Viruses reproduce, but rootkits hide. They hide is a relatively obscure mode on Intel processors used for low-level by compromising the communication conduit between an hardware control. It has its own private memory space and Operating System and its users. Secondary to hiding themselves, execution environment which is generally invisible to code rootkits are generally capable of gathering and manipulating running outside (e.g., the Operating System). Furthermore, SMM information on the target machine. They may, for example, log a code is completely non-preemptible, lacks any concept of victim user’s keystrokes to obtain passwords or manipulate the privilege level, and is immune to memory protection mechanisms. -
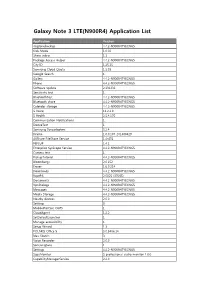
Galaxy Note 3 LTE(N900R4) Application List
Galaxy Note 3 LTE(N900R4) Application List Application Version ringtonebackup 4.4.2-N900R4TYECNG5 Kids Mode 1.0.02 Share video 1.1 Package Access Helper 4.4.2-N900R4TYECNG5 City ID 1.25.15 Samsung Cloud Quota 1.5.03 Google Search 1 Gallery 4.4.2-N900R4TYECNG5 Phone 4.4.2-N900R4TYECNG5 Software update 2.131231 Sensitivity test 1 BluetoothTest 4.4.2-N900R4TYECNG5 Bluetooth share 4.4.2-N900R4TYECNG5 Calendar storage 4.4.2-N900R4TYECNG5 S Voice 11.2.2.0 S Health 2.5.4.170 Communication Notifications 1 DeviceTest 1 Samsung Syncadapters 5.2.4 Drama 1.0.0.107_201400429 AllShare FileShare Service 1.4r476 PEN.UP 1.4.1 Enterprise SysScope Service 4.4.2-N900R4TYECNG5 Camera test 1 PickupTutorial 4.4.2-N900R4TYECNG5 Bloomberg+ 2.0.152 Eraser 1.6.0.214 Downloads 4.4.2-N900R4TYECNG5 RootPA 2.0025 (37085) Documents 4.4.2-N900R4TYECNG5 VpnDialogs 4.4.2-N900R4TYECNG5 Messages 4.4.2-N900R4TYECNG5 Media Storage 4.4.2-N900R4TYECNG5 Nearby devices 2.0.0 Settings 3 MobilePrintSvc_CUPS 1 CloudAgent 1.2.2 SetDefaultLauncher 1 Manage accessibility 1 Setup Wizard 1.3 POLARIS Office 5 5.0.3406.14 Idea Sketch 3 Voice Recorder 2.0.0 SamsungSans 1 Settings 4.4.2-N900R4TYECNG5 SapaMonitor S professional audio monitor 1.0.0 CapabilityManagerService 2.4.0 S Note 3.1.0 Samsung Link 1.8.1904 Samsung WatchON Video 14062601.1.21.78 Street View 1.8.1.2 Alarm 1 PageBuddyNotiSvc 1 Favorite Contacts 4.4.2-N900R4TYECNG5 Google Search 3.4.16.1149292.arm KNOX 2.0.0 Exchange services 4.2 GestureService 1 Weather 140211.01 Samsung Print Service Plugin 1.4.140410 Tasks provider 4.4.2-N900R4TYECNG5 -
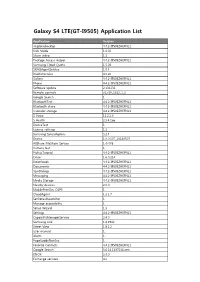
Galaxy S4 LTE(GT-I9505) Application List
Galaxy S4 LTE(GT-I9505) Application List Application Version ringtonebackup 4.4.2-I9505ZHEFNL1 Kids Mode 1.0.02 Share video 1.1 Package Access Helper 4.4.2-I9505ZHEFNL1 Samsung Cloud Quota 1.5.04 SKMSAgentService 1.0.4 DioDictService 4.0.20 Gallery 4.4.2-I9505ZHEFNL1 Phone 4.4.2-I9505ZHEFNL1 Software update 2.131231 Remote controls v2_f18_1312_1_1 Google Search 1 BluetoothTest 4.4.2-I9505ZHEFNL1 Bluetooth share 4.4.2-I9505ZHEFNL1 Calendar storage 4.4.2-I9505ZHEFNL1 S Voice 11.2.2.0 S Health 2.5.4.166 DeviceTest 1 License settings 1.1 Samsung Syncadapters 5.2.4 Drama 1.0.0.107_20140507 AllShare FileShare Service 1.4r476 Camera test 1 PickupTutorial 4.4.2-I9505ZHEFNL1 Eraser 1.6.0.214 Downloads 4.4.2-I9505ZHEFNL1 Documents 4.4.2-I9505ZHEFNL1 VpnDialogs 4.4.2-I9505ZHEFNL1 Messaging 4.4.2-I9505ZHEFNL1 Media Storage 4.4.2-I9505ZHEFNL1 Nearby devices 2.0.0 MobilePrintSvc_CUPS 1 CloudAgent 1.2.1.7 SetDefaultLauncher 1 Manage accessibility 1 Setup Wizard 1.3 Settings 4.4.2-I9505ZHEFNL1 CapabilityManagerService 2.4.0 Samsung Link 1.8.1902 Street View 1.8.1.2 User manual 1 Alarm 1 PageBuddyNotiSvc 1 Favorite Contacts 4.4.2-I9505ZHEFNL1 Google Search 3.6.14.1337016.arm KNOX 2.0.0 Exchange services 4.2 GestureService 1 Weather 140226.01 Samsung Print Service Plugin 1.3.140307 Tasks provider 4.4.2-I9505ZHEFNL1 Dev Tools 1 Google Backup Transport 4.4.2-1289630 Group Play 2.5.417 Safety assistance 1 Dialer Storage 4.4.2-I9505ZHEFNL1 Screen Mirroring 1 Travel wallpaper 1 Software update 6.140411 Maps 8.2.0 Service mode RIL 4.4.2-I9505ZHEFNL1 com.android.wallpapercropper -

Nujj University of California, Berkeley School of Information Karen Hsu
Nujj University of California, Berkeley School of Information Karen Hsu Kesava Mallela Alana Pechon Nujj • Table of Contents Abstract 1 Introduction 2 Problem Statement 2 Objective 2 Literature Review 3 Competitive Analysis 4 Comparison matrix 4 Competition 5 Hypothesis 6 Use Case Scenarios 7 Overall System Design 10 Server-side 12 Design 12 Implementation 12 Twitter and Nujj 14 Client-side 15 Design 17 Implementation 17 Future Work 18 Extended Functionality in Future Implementations 18 Acknowledgements 19 Abstract Nujj is a location based service for mobile device users that enables users to tie electronic notes to physical locations. It is intended as an initial exploration into some of the many scenarios made possible by the rapidly increasing ubiquity of location-aware mobile devices. It should be noted that this does not limit the user to a device with a GPS embedded; location data can now also be gleaned through methods such as cell tower triangulation and WiFi IP address lookup. Within this report, both social and technical considerations associated with exposing a user’s location are discussed. The system envisioned addresses privacy concerns, as well as attempts to overcome the poor rate of adoption of current location based services already competing in the marketplace. Although several possible use cases are offered, it is the authors’ firm belief that a well-designed location- based service should not attempt to anticipate all, or even most, of the potential ways that users will find to take advantage of it. Rather, the service should be focused on building a system that is sufficiently robust yet flexible to allow users to pursue their own ideas. -
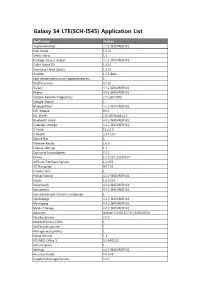
Galaxy S4 LTE(SCH-I545) Application List
Galaxy S4 LTE(SCH-I545) Application List Application Version ringtonebackup 4.4.2-I545VREFNK1 Kids Mode 1.0.02 Share video 1.1 Package Access Helper 4.4.2-I545VREFNK1 Caller Name ID 1.31.0 Samsung Cloud Quota 1.5.01 Audible 1.5.5 Beta com.verizon.permissions.appdirectedsms 1 DioDictService 4.0.20 Gallery 4.4.2-I545VREFNK1 Phone 4.4.2-I545VREFNK1 Verizon Remote Diagnostics 2.42.167.5002 Google Search 1 BluetoothTest 4.4.2-I545VREFNK1 NFL Mobile 9.0.1 Isis Wallet 2.02.00-build.12.2 Bluetooth share 4.4.2-I545VREFNK1 Calendar storage 4.4.2-I545VREFNK1 S Voice 11.2.2.0 S Health 2.5.4.154 DeviceTest 1 VMware Ready 1.6.0 License settings 1.1 Samsung Syncadapters 5.2.2 Drama 1.0.0.107_20140507 AllShare FileShare Service 1.4r476 VZ Navigator 9.0.7.51 Camera test 1 PickupTutorial 4.4.2-I545VREFNK1 Eraser 1.6.0.214 Downloads 4.4.2-I545VREFNK1 Documents 4.4.2-I545VREFNK1 com.verizon.permissions.vzwappapn 1 VpnDialogs 4.4.2-I545VREFNK1 Messaging 4.4.2-I545VREFNK1 Media Storage 4.4.2-I545VREFNK1 Appstore release-8.0005.557.1C_638000510 Nearby devices 2.0.0 MobilePrintSvc_CUPS 1 SetDefaultLauncher 1 Manage accessibility 1 Setup Wizard 1.3 POLARIS Office 5 5.0.3405.02 SamsungSans 1 Settings 4.4.2-I545VREFNK1 Amazon Kindle 4.4.0.48 CapabilityManagerService 2.4.0 Samsung Link 1.8.1826 Samsung WatchON Video 14062601.1.21.78 Street View 1.8.1.2 Alarm 1 PageBuddyNotiSvc 1 Favorite Contacts 4.4.2-I545VREFNK1 Google Search 3.6.14.1337016.arm KNOX 2.0.0 Exchange services 4.2 GestureService 1 Weather 140226.01.01 Samsung Print Service Plugin 1.3.140307 Tasks provider -

Android Apps Samsung Note3 2014 9005
ANDROID APPS SAMSUNG NOTE3 2014 9005 ************************************ For routing instructions according to specific chipset, to rooting kit, and with the installation of the ClockWork Recovery Mode (CWM) Computer under Windows with Internet Cable USB Mini/Normal (Computer to device) Search google: "routing galaxy note 3" for the latest Rooting Kit (Unlock the Boot Loader, Install Recovery Mode & SuperSU) Device with enough battery Turn off device POWER + VOLUMEDOWN + HOME = Recovery Mode POWER + VOLUMEUP + HOME = Boot Loader ? ######### #ROOTING# ######### Download to the Computer: ************************* -SAMSUNG_USB_Driver_for_Mobile_Phones.exe 23 Mo -Odin3v185.zip stockroms.net -n9005-cwm-recovery-6.0.4.7-kk(0125).tar -android_root.exe kingoapp.com -SuperSU.apk -Busybox.apk Device Configuration: ********************* -Android 4.4.2 Samsung Touchwiz rooted CWM -USB Debugging for ADB cable connection -Development Options -Unknowed Sources -No Automatic Over The Air Samsung Update (OTA) Running Rooting Apps: ********************* SuperSU (root) = Grant/Deny/Prompt & manage root permission for apps, Apps with root Permissions (0) Busy Box free = Unix Tools (0) (free version) BusyBox = Unix Tools (trademark version) Titanium Backup (root) = Apps+Sys+Nandroid Greenify (root) = Apps Hibernation (1) ES File Explorer (root) = File Explorer AFWall+ (root) = Firewall en/disable Apps to access to Wifi/3G Wifi Protector (root) = Against ARP Attacks (DOS, Man In The Middle) Startup Manager (root) = Dis/Able User/System apps at boot Rooting -

The Myth of the Superuser: Fear, Risk, and Harm Online
The Myth of the Superuser: Fear, Risk, and Harm Online ∗ Paul Ohm Fear of the powerful computer user, the “Superuser,” dominates debates about online conflict. He is a mythic figure: difficult to find, immune to technological constraints, and aware of legal loopholes. Policymakers, fearful of his power, too often overreact by passing overbroad, ambiguous laws intended to ensnare the Superuser but which are instead used against inculpable, ordinary users. This response is unwarranted because the Superuser is often a marginal figure whose power has been greatly exaggerated. The exaggerated focus on the Superuser reveals a pathological characteristic of the study of power, crime, and security online, which springs from a widely held fear of the Internet. Building on the social science fear literature, this Article challenges the conventional wisdom and ∗ Associate Professor of Law and Telecommunications, University of Colorado Law School. Thanks to Tim Wu, Orin Kerr, Phil Weiser, Julie Cohen, Pierre Schlag, Brett Frischmann, Victor Fleischer, Miranda Fleischer, Viva Moffat, and Jean Camp for their helpful comments. Thanks also for suggestions and support from participants in the University of Colorado Law School Faculty Workshop, including Clare Huntington, Nestor Davidson, Scott Peppett, Mimi Wesson, Amy Schmitz, Sarah Krakoff, and Brad Bernthal; the Intellectual Property Scholars Conference; and the Telecommunications Policy Research Conference. Thanks also to Todd Blair and Michael Beylkin for outstanding research assistance. 1327 1328 University of California, Davis [Vol. 41:1327 standard assumptions about the role of experts. Unlike dispassionate experts in other fields, computer experts are as susceptible as laypeople to exaggerate the power of the Superuser. -

Free, Functional, and Secure
Free, Functional, and Secure Dante Catalfamo What is OpenBSD? Not Linux? ● Unix-like ● Similar layout ● Similar tools ● POSIX ● NOT the same History ● Originated at AT&T, who were unable to compete in the industry (1970s) ● Given to Universities for educational purposes ● Universities improved the code under the BSD license The License The license: ● Retain the copyright notice ● No warranty ● Don’t use the author's name to promote the product History Cont’d ● After 15 years, the partnership ended ● Almost the entire OS had been rewritten ● The university released the (now mostly BSD licensed) code for free History Cont’d ● AT&T launching Unix System Labories (USL) ● Sued UC Berkeley ● Berkeley fought back, claiming the code didn’t belong to AT&T ● 2 year lawsuit ● AT&T lost, and was found guilty of violating the BSD license History Cont’d ● BSD4.4-Lite released ● The only operating system ever released incomplete ● This became the base of FreeBSD and NetBSD, and eventually OpenBSD and MacOS History Cont’d ● Theo DeRaadt ○ Originally a NetBSD developer ○ Forked NetBSD into OpenBSD after disagreement the direction of the project *fork* Innovations W^X ● Pioneered by the OpenBSD project in 3.3 in 2002, strictly enforced in 6.0 ● Memory can either be write or execute, but but both (XOR) ● Similar to PaX Linux kernel extension (developed later) AnonCVS ● First project with a public source tree featuring version control (1995) ● Now an extremely popular model of software development anonymous anonymous anonymous anonymous anonymous IPSec ● First free operating system to implement an IPSec VPN stack Privilege Separation ● First implemented in 3.2 ● Split a program into processes performing different sub-functions ● Now used in almost all privileged programs in OpenBSD like httpd, bgpd, dhcpd, syslog, sndio, etc. -

Jasperreports Server Administrator Guide
TIBCO JASPERREPORTS® SERVER ADMINISTRATOR GUIDE RELEASE 6.1 http://www.jaspersoft.com Copyright ©2005-2015, TIBCO Software Inc. All rights reserved. Printed in the U.S.A. TIBCO, the TIBCO logo, TIBCO Jaspersoft, the TIBCO Jaspersoft logo, TIBCO Jaspersoft iReport Designer, TIBCO JasperReports Library, TIBCO JasperReports Server, TIBCO Jaspersoft OLAP, TIBCO Jaspersoft Studio, and TIBCO Jaspersoft ETL are trademarks and/or registered trademarks of TIBCO Software Inc. in the United States and in jurisdictions throughout the world. All other company and product names are or may be trade names or trademarks of their respective owners. This is version 0915-JSP61-24 of the JasperReports Server Administrator Guide. TABLE OF CONTENTS Chapter 1 Overview of JasperReports Server Administration 11 1.1 Overview of Organizations 12 1.1.1 Single Default Organization 12 1.1.2 Multiple Organizations 13 1.1.3 Levels of Administrators 13 1.2 Overview of the Repository 14 1.2.1 Folder Structure 14 1.2.2 Resources 14 1.2.3 Sample Data 15 1.2.4 Browsing and Searching 16 1.3 Overview of Users and Roles 17 1.3.1 Administering Users and Roles 17 1.3.2 Delegated Administration 17 1.4 Overview of Security 18 1.5 Administrator Login 20 1.5.1 JasperReports Server Heartbeat 20 1.5.2 Administrator Email 20 1.6 Administrator Pages 21 Chapter 2 Organization, User, and Role Management 23 2.1 Managing Organizations 24 2.1.1 Viewing Organization Properties 25 2.1.2 Creating an Organization 25 2.1.3 Default Folders for Organizations 26 2.1.4 Editing an Organization 27 2.1.5 Deleting an Organization 28 2.2 Managing Users 28 2.2.1 Viewing User Properties 29 2.2.2 Creating a User 30 2.2.3 Editing a User 31 2.2.4 Enabling or Disabling Multiple Users 32 2.2.5 Deleting One or More Users 32 2.3 Managing Roles 32 TIBCO Software Inc. -

Samsung GALAXY S4, S4 Active and S4 Mini Companions for Every Business the Optimum Choice for Work and Life
Samsung GALAXY S4, S4 Active and S4 Mini Companions for every business The optimum choice for work and life. Increase your business competence with work styles and environments often vary. Because of this best-in-class smartphones Samsung provides three models of Samsung GALAXY S4 designed to serve those different business needs, all with Today’s fast-paced, global business world necessitates the same superior quality and features that businesses a shift towards the creation of seamless business expect from Samsung smartphones. environments to ensure the productivity and efficiency that businesses need for success. Introducing Samsung GALAXY S4 portfolio - companions for every business Smartphones play a vital role in a creating seamless business environment, and are changing the ways Samsung GALAXY S4. Aimed to meet work and life needs enterprises do business. Now business professionals can with powerful performance and mobility, Samsung GALAXY access corporate data on devices in the palm of their hands S4 can help you work more efficiently. Perfectly optimized at any location at any time to quickly respond to fast- display settings and features allow touchless access to changing business situations. As smartphones have become functions, convenient translation at all times, and secure essential for the workplace, the question then becomes wireless connections for quick collaboration. what the best device for enterprise purposes is. Samsung GALAXY S4 Active. Geared for durability Corporate IT is no longer in sole charge of making the especially for the work out in the field, Samsung GALAXY choice for mobile devices for business users. With the S4 Active stands up to not only impact from drops but also rapid consumerization of smartphones, due in large part to water and dust.