System I Access for Linux Version 6 Release 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
SUSE Linux Enterprise Server 9 SP3 for IBM Power
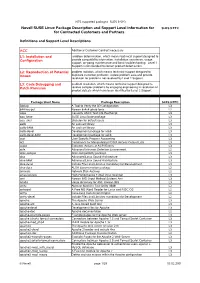
NTS supported packages SLES 9 SP3 Novell SUSE Linux Package Description and Support Level Information for SLES 9 PPC for Contracted Customers and Partners Definitions and Support Level Descriptions ACC Additional Customer Contract necessary L1: Installation and problem determination, which means technical support designed to Configuration provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of Potential problem isolation, which means technical support designed to Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed to Patch Provision resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Package Short Name Package Description SLES 9 PPC 3ddiag A Tool to Verify the 3D Configuration L3 844-ksc-pcf Korean 8x4x4 johab fonts L2 a2ps Converts ASCII Text into PostScript L3 aaa_base SuSE Linux base package L3 aaa_skel Skeleton for default users L3 aalib An ascii art library L3 aalib-64bit An ascii art library L3 aalib-devel Development package for aalib L3 aalib-devel-64bit Development package for aalib L3 acct User Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 acpid Executes Actions at ACPI Events L3 aide Advanced Intrusion Detection Environment L2 alice-compat Alice compatibility package L3 alsa Advanced Linux Sound Architecture L3 alsa-64bit Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development. -

Xview Developer's Notes
XView Developer’s Notes 2550 Garcia Avenue Mountain View, CA 94043 U.S.A. A Sun Microsystems, Inc. Business 1994 Sun Microsystems, Inc. 2550 Garcia Avenue, Mountain View, California 94043-1100 U.S.A. All rights reserved. This product and related documentation are protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or related documentation may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Portions of this product may be derived from the UNIX® and Berkeley 4.3 BSD systems, licensed from UNIX System Laboratories, Inc., a wholly owned subsidiary of Novell, Inc., and the University of California, respectively. Third-party font software in this product is protected by copyright and licensed from Sun’s font suppliers. RESTRICTED RIGHTS LEGEND: Use, duplication, or disclosure by the United States Government is subject to the restrictions set forth in DFARS 252.227-7013 (c)(1)(ii) and FAR 52.227-19. The product described in this manual may be protected by one or more U.S. patents, foreign patents, or pending applications. TRADEMARKS Sun, the Sun logo, Sun Microsystems, Sun Microsystems Computer Corporation, SunSoft, the SunSoft logo, Solaris, SunOS, OpenWindows, DeskSet, ONC, ONC+, and NFS are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and certain other countries. UNIX is a registered trademark of Novell, Inc., in the United States and other countries; X/Open Company, Ltd., is the exclusive licensor of such trademark. OPEN LOOK® is a registered trademark of Novell, Inc. -

International Language Environments Guide
International Language Environments Guide Sun Microsystems, Inc. 4150 Network Circle Santa Clara, CA 95054 U.S.A. Part No: 806–6642–10 May, 2002 Copyright 2002 Sun Microsystems, Inc. 4150 Network Circle, Santa Clara, CA 95054 U.S.A. All rights reserved. This product or document is protected by copyright and distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this product or document may be reproduced in any form by any means without prior written authorization of Sun and its licensors, if any. Third-party software, including font technology, is copyrighted and licensed from Sun suppliers. Parts of the product may be derived from Berkeley BSD systems, licensed from the University of California. UNIX is a registered trademark in the U.S. and other countries, exclusively licensed through X/Open Company, Ltd. Sun, Sun Microsystems, the Sun logo, docs.sun.com, AnswerBook, AnswerBook2, Java, XView, ToolTalk, Solstice AdminTools, SunVideo and Solaris are trademarks, registered trademarks, or service marks of Sun Microsystems, Inc. in the U.S. and other countries. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. in the U.S. and other countries. Products bearing SPARC trademarks are based upon an architecture developed by Sun Microsystems, Inc. SunOS, Solaris, X11, SPARC, UNIX, PostScript, OpenWindows, AnswerBook, SunExpress, SPARCprinter, JumpStart, Xlib The OPEN LOOK and Sun™ Graphical User Interface was developed by Sun Microsystems, Inc. for its users and licensees. Sun acknowledges the pioneering efforts of Xerox in researching and developing the concept of visual or graphical user interfaces for the computer industry. -

RTL-To-Gates Synthesis Using Synopsys Design Compiler
RTL-to-Gates Synthesis using Synopsys Design Compiler CS250 Tutorial 5 (Version 091210b) September 12, 2010 Yunsup Lee In this tutorial you will gain experience using Synopsys Design Compiler (DC) to perform hardware synthesis. A synthesis tool takes an RTL hardware description and a standard cell library as input and produces a gate-level netlist as output. The resulting gate-level netlist is a completely structural description with standard cells only at the leaves of the design. Internally, a synthesis tool performs many steps including high-level RTL optimizations, RTL to unoptimized boolean logic, technology independent optimizations, and finally technology mapping to the available standard cells. Good RTL designers will familiarize themselves with the target standard cell library so that they can develop an intuition on how their RTL will be synthesized into gates. In this tutorial you will use Synopsys Design Compiler to elaborate RTL, set optimization constraints, synthesize to gates, and prepare various area and timing reports. You will also learn how to read the various DC text reports and how to use the graphical Synopsys Design Vision tool to visualize the synthesized design. Synopsys provides a library called Design Ware which includes highly optimized RTL for arithmetic building blocks. DC can automatically determine when to use Design Ware components and it can then efficiently synthesize these components into gate-level implementations. In this tutorial you will learn more about what Design Ware components are available and how to best encourage DC to use them. The following documentation is located in the course locker (~cs250/manuals) and provides ad- ditional information about Design Compiler, Design Vision, the Design Ware libraries, and the Synopsys 90nm Standard Cell Library. -

IDL Quick Reference
IDL Quick Reference IDL Version 6.2 July 2005 Edition Copyright © RSI All Rights Reserved 0705IDL62QR Restricted Rights Notice The IDL®, ION Script™, and ION Java™ software programs and the accompanying procedures, functions, and documentation described herein are sold under license agreement. Their use, dupli- cation, and disclosure are subject to the restrictions stated in the license agreement. RSI reserves the right to make changes to this document at any time and without notice. Limitation of Warranty RSI makes no warranties, either express or implied, as to any matter not expressly set forth in the license agreement, including without limitation the condition of the software, merchantability, or fitness for any particular purpose. RSI shall not be liable for any direct, consequential, or other damages suffered by the Licensee or any others resulting from use of the IDL or ION software packages or their documentation. Permission to Reproduce this Manual If you are a licensed user of this product, RSI grants you a limited, nontransferable license to repro- duce this particular document provided such copies are for your use only and are not sold or dis- tributed to third parties. All such copies must contain the title page and this notice page in their entirety. Acknowledgments IDL® is a registered trademark and ION™, ION Script™, ION Java™, are trademarks of ITT Industries, registered in the United States Patent and Trademark Office, for the computer program described herein. Numerical Recipes™ is a trademark of Numerical Recipes Software. Numerical Recipes routines are used by permission. GRG2™ is a trademark of Windward Technologies, Inc. -

UEFI Shell Specification
UEFI Shell Specification January 26, 2016 Revision 2.2 The material contained herein is not a license, either expressly or impliedly, to any intellectual property owned or controlled by any of the authors or developers of this material or to any contribution thereto. The material contained herein is provided on an "AS IS" basis and, to the maximum extent permitted by applicable law, this information is provided AS IS AND WITH ALL FAULTS, and the authors and developers of this material hereby disclaim all other warranties and conditions, either express, implied or statutory, including, but not limited to, any (if any) implied warranties, duties or conditions of merchantability, of fitness for a particular purpose, of accuracy or completeness of responses, of results, of workmanlike effort, of lack of viruses and of lack of negligence, all with regard to this material and any contribution thereto. Designers must not rely on the absence or characteristics of any features or instructions marked "reserved" or "undefined." The Unified EFI Forum, Inc. reserves any features or instructions so marked for future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them. ALSO, THERE IS NO WARRANTY OR CONDITION OF TITLE, QUIET ENJOYMENT, QUIET POSSESSION, CORRESPONDENCE TO DESCRIPTION OR NON-INFRINGEMENT WITH REGARD TO THE SPECIFICATION AND ANY CONTRIBUTION THERETO. IN NO EVENT WILL ANY AUTHOR OR DEVELOPER OF THIS MATERIAL OR ANY CONTRIBUTION THERETO BE LIABLE TO ANY OTHER PARTY FOR THE COST OF PROCURING SUBSTITUTE GOODS OR SERVICES, LOST PROFITS, LOSS OF USE, LOSS OF DATA, OR ANY INCIDENTAL, CONSEQUENTIAL, DIRECT, INDIRECT, OR SPECIAL DAMAGES WHETHER UNDER CONTRACT, TORT, WARRANTY, OR OTHERWISE, ARISING IN ANY WAY OUT OF THIS OR ANY OTHER AGREEMENT RELATING TO THIS DOCUMENT, WHETHER OR NOT SUCH PARTY HAD ADVANCE NOTICE OF THE POSSIBILITY OF SUCH DAMAGES. -

Xlib − C Language X Interface X Window System Standard X Version 11, Release 6.7
Xlib − C Language X Interface X Window System Standard X Version 11, Release 6.7 James Gettys Cambridge Research Laboratory Digital Equipment Corporation Robert W. Scheifler Laboratory for Computer Science Massachusetts Institute of Technology with contributions from Chuck Adams, Tektronix, Inc. Vania Joloboff, Open Software Foundation Hideki Hiura, Sun Microsystems, Inc. Bill McMahon, Hewlett-Packard Company Ron Newman, Massachusetts Institute of Technology Al Tabayoyon, Tektronix, Inc. Glenn Widener, Tektronix, Inc. Shigeru Yamada, Fujitsu OSSI The X Window System is a trademark of The Open Group. TekHVC is a trademark of Tektronix, Inc. Copyright © 1985, 1986, 1987, 1988, 1989, 1990, 1991, 1994, 1996, 2002 The Open Group Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documenta- tion files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions: The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Soft- ware. THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTIC- ULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE X CONSORTIUM BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTH- ERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. -

Macanova Users' Guide
This file consists of a Appendix C to MacAnova User’s Guide by Gary W. Oehlert and Christopher Bingham, issued as part of a revision of Technical Report Number 617, School of Statistics, University of Minnesota, September 1997, describing Version 4.05 of MacAnova This manual is Copyright © 1997 by Christopher Bingham and Gary W. Oehlert, all rights reserved. Fonts used in this manual are Palatino, Courier, and Symbol. For information concerning MacAnova, write University of Minnesota, Department of Applied Statistics, 352 Classroom Office Building, 1994 Buford Avenue, St. Paul, MN 55108-6042. MacAnova Version 4.05 Appendix C DOS versions of MacAnova on an IBM™ Compatible C.1 Introduction This appendix summarizes features special to the DOS versions of MacAnova. See Appendix D for information on the Windows version. There are two versions of MacAnova that run under MSDOS™ on IBM™ compatible computers – an extended memory version (MACANODJ) and a limited memory version (MACANOBC). They both have the full range of MacAnova commands and use the same help and macro files and files produced by save() (Sec. 2.17, 7.7) are compatible. The executable files are MACANODJ.EXE and MACANOBC.EXE. In the discussion below, it is assumed that either MACANODJ.EXE, MACANOBC.EXE or both are in directory C:\MACANOVA. C.1.1 Extended memory version (MACANODJ) MACANODJ.EXE runs in “protected mode” and requires a 80386 or better processor. It can access all available memory and in fact uses “virtual memory” on the hard disk when necessary so that the size of variables is limited only by disk capacity. -

Name Usage Synopsis Description
LINK2RCS(1) General Commands Manual LINK2RCS(1) NAME link2rcs −rcs directory template USAGE link2rcs [options] [file-specifications] SYNOPSIS Link2rcs makes (an empty) template of an existing directory tree. All directory names are copied; "RCS" directories are transformed into symbolic links pointing to the original tree. DESCRIPTION Link2rcs is used to makeaworking copyofasource-controlled module which is configured in a tree of di- rectories (e.g., bin, lib, include, src, with dependent subdirectories). By making a template directory (i.e., with the same relative pathnames), you may check-out files and continue to develop the module. By mak- ing symbolic links to the original set of rcs directories, link2rcs facilitates the use of rcs: ci and co assume that the rcs files are in a subdirectory named "RCS". OPTIONS Link2rcs recognizes the following options: −a process all directory names. Likethe ls option "-a", this enables the processing of names beginning with ".". −bnum directs link2rcs to avoid generating directories which do not correspond to a source-directory with the given rcs baseline. Use "-b0" to suppress directories which do not correspond to any rcs baseline. −dpath specifies the destination directory.You must always specify this if you don’tspecify the "-s"option. −eenv (Apollo only) specifies the name of an environment variable which can be used to substitute for the be- ginning of the link-text. −f makes links to files as well as directories. −F makes hard links to files as well as directories. −m merge against destination, i.e., don’tquit if a target directory or link is found. −n (no-op) causes link2rcs to compute the modifications and to display them (according to the setting of "-q"and "-v"), but not to modify the target directory tree. -

Observation and Analysis of BGP Behavior Under Stress — a Study of BGP’S Reaction to the Nimda Worm Attack
Observation and Analysis of BGP Behavior Under Stress — A Study of BGP’s Reaction to the Nimda Worm Attack Lan Wang, Dan Pei, Lixia Zhang, UCLA Xiaoliang Zhao, Daniel Massey, Allison Mankin, USC/ISI Randy Bush, IIJ, Felix Wu, UC Davis http://fniisc.nge.isi.edu/ 11/25/02 1 Problem Statement Investigate BGP behavior during Nimda worm attack in Sept. 2001 Renesys Corp.: “Global routing instability …” [1] 9/18/01 (2pm, 3pm): 1.5M What caused the spike? •Worm? SANS Institute: “the (Nimda) activity jumped dramatically at approximately 13:00 GMT (on Sept. 18, 2001) and then proceeded to taper off in the following hours …” •BGP implementation bugs? 9/18/01 (12pm, 1pm): 50.7K •BGP protocol design issues? •Misconfiguration? •Other causes? Hourly BGP Update Count at RIPE NCC rrc00 11/25/02 2 Data BGP update messages collected by RIPE NCC (rrc00) from 9/10/01 to 9/30/01 12 BGP Peers 3 US peers: AT&T, Verio, Global Crossing 4 peers in Netherlands: RIPE NCC, SURFnet, Tiscali, KPNQwest 2 peers in Switzerland: CERN, Nextra 1 in Germany: Global Access 1 in London: Global Crossing 1 in Japan: NSPIXP2 11/25/02 3 Identifying What Caused the Spike Classify BGP update messages Identify the causes of each class BGP Updates Announcements Withdrawals New Duplicate Implicit Withdrawals Table Flap NADA Plain SPATH DPATH Exchange (New Announcement New (Same AS Path) (Different AS Path) Different Attributes) 11/25/02 4 Classification Example Time | Type | Prefix | ASPATH | Community Attribute t0 | session reset New Ann -> Table Exchange t1 | A | 200.16.216.0/24| -

Alterpath ACS V.2.6.1 Command Reference Guide
AlterPath™ ACS Command Reference Guide Software Version 2.6.1 ACS ALTERPATH AlterPath 32 LINUX INSIDE Cyclades Corporation 3541 Gateway Boulevard Fremont, CA 94538 USA 1.888.CYCLADES (292.5233) 1.510.771.6100 1.510.771.6200 (fax) http://www.cyclades.com Release Date: April 2006 Part Number: PAC0193 © 2006 Cyclades Corporation, all rights reserved Information in this document is subject to change without notice. The following are registered or registration-pending trademarks of Cyclades Corporation in the United States and other countries: Cyclades and AlterPath. All trademarks, trade names, logos and service marks referenced herein, even when not specifically marked as such, belong to their respective companies and are not to be considered unprotected by law. Table of Contents ................................................................. Preface xix Purpose . xix Audience and User Levels. xix New Users. xix Power Users . xx How to use the CLI . xxi Modes of Operation . xxi Keywords meanings . xxii Interactive Mode . xxii CLI arguments. xxv Other important features of the CLI . xxv List of CLI Keywords . xxvii . How to use this Guide xxx Conventions and Symbols. xxxi Typeface and Fonts . xxxi Hypertext Links. xxxi Glossary Entries . xxxi Quick Steps . xxxi Parameter Syntax . xxxii Brackets and Hyphens (dashes) . xxxii Ellipses. xxxii Pipes. xxxii Greater-than and Less-than signs. xxxii Spacing and Separators . xxxiii Cautionary and Instructional Information. xxxiii Networking Settings . 1 Performing Basic Network Configuration Using the wiz Command . 1 Log Into ACS Through the Console . 1 Password . 2 Security Advisory . 2 Use the wiz Command to Configure Network Parameters. 4 Table of Contents Selecting A Security Profile. 6 To Select a Security Profile . -

Simulating Verilog RTL Using Synopsys VCS
Simulating Verilog RTL using Synopsys VCS CS250 Tutorial 4 (Version 091209a) September 12, 2010 Yunsup Lee In this tutorial you will gain experience using Synopsys VCS to compile cycle-accurate executable simulators from Verilog RTL. You will also learn how to use the Synopsys Waveform viewer to trace the various signals in your design. Figure 1 illustrates the basic VCS toolflow and RISC-V toolchain. For more information about the RISC-V toolchain consult Tutorial 3: Build, Run, and Write RISC-V Programs. VCS takes a set of Verilog files as input and produces a simulator. When you execute the simulator you need some way to observe your design so that you can measure its performance and verify that it is working correctly. There are two primary ways to observe your design: (1) you can use $display statements in your Verilog RTL to output textual trace information, or (2) you can instruct the simulator to automatically write transition information about each signal in your design to a file. There is standard text format for this type of signal transition trace information called the Value Change Dump format (VCD). Unfortunately, these textual trace files can become very large very quickly, so Synopsys uses a proprietary compressed binary trace format called VCD Plus (VPD). You can view VPD files using the Synopsys waveform viewer called Discovery Visual Environment (DVE). Verilog Verilog ASM C Source Library Source Source (RTL) (RTL) Code Code VCS RISC-V toolchain RTL RISC-V Sim Binary Execute SIM Test VPD Outputs DVE GUI Figure 1: VCS Toolflow and RISC-V Assembler Toolchain CS250 Tutorial 4 (Version 091209a), Fall 2010 2 You will be using a simple unpipelined RISC-V v1 processor as your design example for this tutorial, and thus you will also learn how to build and run test codes on the processor simulator.