Sheeju Ranji Alex
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Christina Perri 3
MUSIC PRODUCTION GUIDE OFFICIAL NEWS GUIDE FROM YAMAHA & EASY SOUNDS FOR YAMAHA MUSIC PRODUCTION INSTRUMENTS 03|2015 Contents Interview Christina Perri 3 MOTIF Soundset „Air“ by DCP Productions 6 Yamaha Synth Book reloaded 8 VP1 Soundset for MOTIF XF / MOXF 11 MOTIF XS/XF/MOXF Exploring Sound: „Vintage Keyboards“ 15 MOTIF XF / MOXF Performance Soundset „Hybrid Performer“ Part 3 19 Yamaha DTX M12 Touch App 22 The new e-drum kit Yamaha DTX582k 24 CHRISTINA Yamaha KP100 Kick Pad 26 Sounds & Goodies 29 PERRI Imprint 43 DREAMS COME TRUE MUSIC PRODUCTION GUIDE 03|2015 CHRISTINA PERRI - DREAMS COME TRUE “Every time I dream something up, it’s so “I don’t take it lightly,” she says. “I tell everyone, ‘That’s small compared to what actually happens,” the moment my life changed.’ It was incredibly special.” says singer/songwriter Christina Perri. But even as her own life was changing, Perri was changing “Because what actually happens is just other people’s lives through her music. Just a year later, amazing.” her multi-platinum song, “A Thousand Years,” was As an unsigned artist, Christina once dreamed of making released as the second single from the soundtrack album a career out of performing and recording her deeply to The Twilight Saga: Breaking Dawn – Part 1. It achieved personal yet pop-friendly songs. Then one day four years multi-platinum status, with a video that inspired romantic ago, one of her recordings was featured on the hit TV visions among countless Twilight fans. show So You Think You Can Dance, and suddenly she “I had dreamed of having a song on the Twilight stopped dreaming the dream—and began living it. -
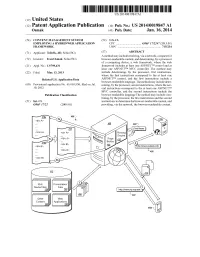
(12) Patent Application Publication (10) Pub. No.: US 2014/0019847 A1 Osmak (43) Pub
US 20140019847A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0019847 A1 OSmak (43) Pub. Date: Jan. 16, 2014 (54) CONTENT MANAGEMENT SYSTEM (52) U.S. Cl. EMPLOYINGA HYBRD WEB APPLICATION CPC .................................. G06F 17/2247 (2013.01) FRAMEWORK USPC .......................................................... 71.5/234 (71) Applicant: Telerik, AD, Sofia (BG) (57) ABSTRACT A method may include receiving, via a network, a request for (72) Inventor: Ivan Osmak, Sofia (BG) browser-renderable content, and determining, by a processor of a computing device, a web framework, where the web (21) Appl. No.: 13/799,431 framework includes at least one ASP.NETTM control and at least one ASP.NETTM MVC controller. The method may (22) Filed: Mar 13, 2013 include determining, by the processor, first instructions, where the first instructions correspond to the at least one Related U.S. Application Data ASP.NETTM control, and the first instructions include a browser-renderable language. The method may include deter (60) Provisional application No. 61/669,930, filed on Jul. mining, by the processor, second instructions, where the sec 10, 2012. ond instructions correspond to the at least one ASP.NETTM MVC controller, and the second instructions include the Publication Classification browser-renderable language The method may include com bining, by the processor, the first instructions and the second (51) Int. Cl. instructions to determine the browser-renderable content, and G06F 7/22 (2006.01) providing, via the network, the browser-renderable content. Routing Engine Ric Presentation Media Fies : Fies 22 Applications 28 Patent Application Publication Jan. 16, 2014 Sheet 1 of 8 US 2014/001.9847 A1 Patent Application Publication Jan. -

Web Development and Perl 6 Talk
Click to add Title 1 “Even though I am in the thralls of Perl 6, I still do all my web development in Perl 5 because the ecology of modules is so mature.” http://blogs.perl.org/users/ken_youens-clark/2016/10/web-development-with-perl-5.html Web development and Perl 6 Bailador BreakDancer Crust Web Web::App::Ballet Web::App::MVC Web::RF Bailador Nov 2016 BreakDancer Mar 2014 Crust Jan 2016 Web May 2016 Web::App::Ballet Jun 2015 Web::App::MVC Mar 2013 Web::RF Nov 2015 “Even though I am in the thralls of Perl 6, I still do all my web development in Perl 5 because the ecology of modules is so mature.” http://blogs.perl.org/users/ken_youens-clark/2016/10/web-development-with-perl-5.html Crust Web Bailador to the rescue Bailador config my %settings; multi sub setting(Str $name) { %settings{$name} } multi sub setting(Pair $pair) { %settings{$pair.key} = $pair.value } setting 'database' => $*TMPDIR.child('dancr.db'); # webscale authentication method setting 'username' => 'admin'; setting 'password' => 'password'; setting 'layout' => 'main'; Bailador DB sub connect_db() { my $dbh = DBIish.connect( 'SQLite', :database(setting('database').Str) ); return $dbh; } sub init_db() { my $db = connect_db; my $schema = slurp 'schema.sql'; $db.do($schema); } Bailador handler get '/' => { my $db = connect_db(); my $sth = $db.prepare( 'select id, title, text from entries order by id desc' ); $sth.execute; layout template 'show_entries.tt', { msg => get_flash(), add_entry_url => uri_for('/add'), entries => $sth.allrows(:array-of-hash) .map({$_<id> => $_}).hash, -

The Globalization of K-Pop: the Interplay of External and Internal Forces
THE GLOBALIZATION OF K-POP: THE INTERPLAY OF EXTERNAL AND INTERNAL FORCES Master Thesis presented by Hiu Yan Kong Furtwangen University MBA WS14/16 Matriculation Number 249536 May, 2016 Sworn Statement I hereby solemnly declare on my oath that the work presented has been carried out by me alone without any form of illicit assistance. All sources used have been fully quoted. (Signature, Date) Abstract This thesis aims to provide a comprehensive and systematic analysis about the growing popularity of Korean pop music (K-pop) worldwide in recent years. On one hand, the international expansion of K-pop can be understood as a result of the strategic planning and business execution that are created and carried out by the entertainment agencies. On the other hand, external circumstances such as the rise of social media also create a wide array of opportunities for K-pop to broaden its global appeal. The research explores the ways how the interplay between external circumstances and organizational strategies has jointly contributed to the global circulation of K-pop. The research starts with providing a general descriptive overview of K-pop. Following that, quantitative methods are applied to measure and assess the international recognition and global spread of K-pop. Next, a systematic approach is used to identify and analyze factors and forces that have important influences and implications on K-pop’s globalization. The analysis is carried out based on three levels of business environment which are macro, operating, and internal level. PEST analysis is applied to identify critical macro-environmental factors including political, economic, socio-cultural, and technological. -

Algorithmic Reflections on Choreography
ISSN: 1795-6889 www.humantechnology.jyu.fi Volume 12(2), November 2016, 252–288 ALGORITHMIC REFLECTIONS ON CHOREOGRAPHY Pablo Ventura Daniel Bisig Ventura Dance Company Zurich University of the Arts Switzerland Switzerland Abstract: In 1996, Pablo Ventura turned his attention to the choreography software Life Forms to find out whether the then-revolutionary new tool could lead to new possibilities of expression in contemporary dance. During the next 2 decades, he devised choreographic techniques and custom software to create dance works that highlight the operational logic of computers, accompanied by computer-generated dance and media elements. This article provides a firsthand account of how Ventura’s engagement with algorithmic concepts guided and transformed his choreographic practice. The text describes the methods that were developed to create computer-aided dance choreographies. Furthermore, the text illustrates how choreography techniques can be applied to correlate formal and aesthetic aspects of movement, music, and video. Finally, the text emphasizes how Ventura’s interest in the wider conceptual context has led him to explore with choreographic means fundamental issues concerning the characteristics of humans and machines and their increasingly profound interdependencies. Keywords: computer-aided choreography, breaking of aesthetic and bodily habits, human– machine relationships, computer-generated and interactive media. © 2016 Pablo Ventura & Daniel Bisig, and the Agora Center, University of Jyväskylä DOI: http://dx.doi.org/10.17011/ht/urn.201611174656 This work is licensed under a Creative Commons Attribution-Noncommercial 4.0 International License. 252 Algorithmic Reflections on Choreography INTRODUCTION The purpose of this article is to provide a first-hand account of how a thorough artistic engagement with functional and conceptual aspects of software can guide and transform choreographic practice. -

Practical Perl Tools Give As Good As You Get, My Tiny Dancer
Practical Perl Tools Give as Good as You Get, My Tiny Dancer DAVIDCOLUMNS BLANK-EDELMAN David N. Blank-Edelman is During our last time together, we had a chance to explore some of the features of the director of technology at the Web library for Perl, the seminal HTTP client distribution (more commonly the Northeastern University called LWP) . We saw how to fetch HTTP content from Web servers, POST data College of Computer and to them, and so on . I thought it might be interesting to look at the other side of Information Science and the author of the the coin and explore another way to construct Perl applications that serve data to O’Reilly book Automating System Administration HTTP clients like those from my April column . I say “another” way because all the with Perl (the second edition of the Otter rabid fans of this column (I’m waving to both of you!) will recall our forays into the book), available at purveyors of fine dead CGI::Application framework back in July and September of 2009 . CGI::Application trees everywhere. He has spent the past 24+ is still alive and kicking, but since then there have been a number of new frame- years as a system/network administrator in works released that some considered to be the new hotness . In this column we’ll large multi-platform environments, including look at one of those frameworks, and, if polling numbers stay high, we’ll look at a Brandeis University, Cambridge Technology “competing” framework in the next issue . Group, and the MIT Media Laboratory. -

Final CATALYST Framework Architecture
D2.3 F in al CATALYST Framework Architect ure WORKPACKAGE PROGRAMME IDENTIFIER WP2 H2020-EE-2016-2017 DOCUMENT PROJECT NUMBER D2.3 768739 VERSION START DATE OF THE PROJECT 1.0 01/10/2017 PUBLISH DATE DURATION 03/06/2019 36 months DOCUMENT REFERENCE CATALYST.D2.3.PARTNER.WP2.v1.0 PROGRAMME NAME ENERGY EFFICIENCY CALL 2016-2017 PROGRAMME IDENTIFIER H2020-EE-2016-2017 TOPIC Bringing to market more energy efficient and integrated data centres TOPIC IDENTIFIER EE-20-2017 TYPE OF ACTION IA Innovation action PROJECT NUMBER 768739 PROJECT TITLE CATALYST COORDINATOR ENGINEERING INGEGNERIA INFORMATICA S.p.A. (ENG) PRINCIPAL CONTRACTORS SINGULARLOGIC ANONYMI ETAIREIA PLIROFORIAKON SYSTIMATON KAI EFARMOGON PLIROFORIKIS (SiLO), ENEL.SI S.r.l (ENEL), ALLIANDER NV (ALD), STICHTING GREEN IT CONSORTIUM REGIO AMSTERDAM (GIT), SCHUBERG PHILIS BV (SBP), QARNOT COMPUTING (QRN), POWER OPERATIONS LIMITED (POPs), INSTYTUT CHEMII BIOORGANICZNEJ POLSKIEJ AKADEMII NAUK (PSNC), UNIVERSITATEA TEHNICA CLUJ-NAPOCA (TUC) DOCUMENT REFERENCE CATALYST.D2.3.PARTNER.WP2.v1.0 WORKPACKAGE: WP2 DELIVERABLE TYPE R (report) AVAILABILITY PU (Public) DELIVERABLE STATE Final CONTRACTUAL DATE OF DELIVERY 31/05/2019 ACTUAL DATE OF DELIVERY 03/06/2019 DOCUMENT TITLE Final CATALYST Framework Architecture AUTHOR(S) Marzia Mammina (ENG), Terpsi Velivassaki (SiLO), Tudor Cioara (TUC), Nicolas Sainthérant (QRN), Artemis Voulkidis (POPs), John Booth (GIT) REVIEWER(S) Artemis Voulkidis (POPs) Terpsi Velivassaki (SILO) SUMMARY (See the Executive Summary) HISTORY (See the Change History Table) -

Development of a Novel Combined Catalyst and Sorbent for Hydrocarbon Reforming Justinus A
Chemical and Biological Engineering Publications Chemical and Biological Engineering 2005 Development of a novel combined catalyst and sorbent for hydrocarbon reforming Justinus A. Satrio Iowa State University Brent H. Shanks Iowa State University, [email protected] Thomas D. Wheelock Iowa State University, [email protected] Follow this and additional works at: http://lib.dr.iastate.edu/cbe_pubs Part of the Chemical Engineering Commons The ompc lete bibliographic information for this item can be found at http://lib.dr.iastate.edu/ cbe_pubs/220. For information on how to cite this item, please visit http://lib.dr.iastate.edu/ howtocite.html. This Article is brought to you for free and open access by the Chemical and Biological Engineering at Iowa State University Digital Repository. It has been accepted for inclusion in Chemical and Biological Engineering Publications by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. Development of a novel combined catalyst and sorbent for hydrocarbon reforming Abstract A combined catalyst and sorbent was prepared and utilized for steam reforming methane and propane in laboratory-scale systems. The am terial was prepared in the form of small spherical pellets having a layered structure such that each pellet consisted of a highly reactive lime or dolime core enclosed within a porous but strong protective shell made of alumina in which a nickel catalyst was loaded. The am terial served two functions by catalyzing the reaction of hydrocarbons with steam to produce hydrogen while simultaneously absorbing carbon dioxide formed by the reaction. The in situ er moval of CO 2 shifted the reaction equilibrium toward increased H 2 concentration and production. -

Embracing Containers Agile and Flexible Software-Defined Hybrid Cloud Infrastructure
Overview Embracing containers Agile and flexible software-defined hybrid cloud infrastructure Introduction Containers and container orchestration have emerged as highly desirable technologies that give enterprises the agility to embrace new business opportunities in a cloud-centric world. To capture these opportunities, organizations must respond more quickly than ever to retain customers and grow the business in the face of increasing global competitive pressures. The customer experience is paramount, and having the right applications and infrastructure in place at the right time — secured This architecture blueprint and ready to scale — can make or break critical strategic initiatives. is based on customer implementations that Modern hyperscale public clouds redefine possibilities for applications and infrastructure, yield- illustrate common elements ing highly available, resilient, and massively scalable services. Containers also open new opportuni- for a multiproduct ties for applications that are deployed on a private cloud. Built to enable the hybrid cloud, containers architecture blueprint. represent a fundamental opportunity to move beyond traditional, slow, and cost-intensive ways of developing and deploying applications toward truly programmable infrastructure without arbitrary limitations. Beyond merely moving applications to the cloud, containers fully exploit the benefits of Product combination cloud environments — whether public, private, or hybrid in nature. • Red Hat OpenShift® It is no surprise that container usage is -

Bachelorarbeit
BACHELORARBEIT Realisierung von verzögerungsfreien Mehrbenutzer Webapplikationen auf Basis von HTML5 WebSockets Hochschule Harz University of Applied Sciences Wernigerode Fachbereich Automatisierung und Informatik im Fach Medieninformatik Erstprüfer: Prof. Jürgen K. Singer, Ph.D. Zweitprüfer: Prof. Dr. Olaf Drögehorn Erstellt von: Lars Häuser Datum: 16.06.2011 Einleitung Inhaltsverzeichnis 1 Einleitung ................................................................................................................. 5 1.1 Zielsetzung ..................................................................................................... 5 1.2 Aufbau der Arbeit ........................................................................................... 6 2 Grundlagen .............................................................................................................. 8 2.1 TCP/IP ............................................................................................................ 8 2.2 HTTP .............................................................................................................. 9 2.3 Request-Response-Paradigma (HTTP-Request-Cycle) .............................. 10 2.4 Klassische Webanwendung: Synchrone Datenübertragung ....................... 11 2.5 Asynchrone Webapplikationen .................................................................... 11 2.6 HTML5 ......................................................................................................... 12 3 HTML5 WebSockets ............................................................................................. -

Revealing Injection Vulnerabilities by Leveraging Existing Tests
Revealing Injection Vulnerabilities by Leveraging Existing Tests Katherine Hough1, Gebrehiwet Welearegai2, Christian Hammer2 and Jonathan Bell1 1George Mason University, Fairfax, VA, USA 2University of Potsdam, Potsdam, Germany [email protected],[email protected],[email protected],[email protected] Abstract just one of over 8,200 similar code injection exploits discovered in Code injection attacks, like the one used in the high-prole 2017 recent years in popular software [44]. Code injection vulnerabilities Equifax breach, have become increasingly common, now ranking have been exploited in repeated attacks on US election systems [10, #1 on OWASP’s list of critical web application vulnerabilities. Static 18, 39, 61], in the theft of sensitive nancial data [56], and in the analyses for detecting these vulnerabilities can overwhelm develop- theft of millions of credit card numbers [33]. In the past several ers with false positive reports. Meanwhile, most dynamic analyses years, code injection attacks have persistently ranked at the top rely on detecting vulnerabilities as they occur in the eld, which of the Open Web Application Security Project (OWASP) top ten can introduce a high performance overhead in production code. most dangerous web aws [46]. Injection attacks can be damaging This paper describes a new approach for detecting injection vul- even for applications that are not traditionally considered critical nerabilities in applications by harnessing the combined power of targets, such as personal websites, because attackers can use them human developers’ test suites and automated dynamic analysis. as footholds to launch more complicated attacks. Our new approach, Rivulet, monitors the execution of developer- In a code injection attack, an adversary crafts a malicious in- written functional tests in order to detect information ows that put that gets interpreted by the application as code rather than may be vulnerable to attack. -

The Lift Approach
Science of Computer Programming 102 (2015) 1–19 Contents lists available at ScienceDirect Science of Computer Programming www.elsevier.com/locate/scico Analyzing best practices on Web development frameworks: The lift approach ∗ María del Pilar Salas-Zárate a, Giner Alor-Hernández b, , Rafael Valencia-García a, Lisbeth Rodríguez-Mazahua b, Alejandro Rodríguez-González c,e, José Luis López Cuadrado d a Departamento de Informática y Sistemas, Universidad de Murcia, Campus de Espinardo, 30100 Murcia, Spain b Division of Research and Postgraduate Studies, Instituto Tecnológico de Orizaba, Mexico c Bioinformatics at Centre for Plant Biotechnology and Genomics, Polytechnic University of Madrid, Spain d Computer Science Department, Universidad Carlos III de Madrid, Spain e Department of Engineering, School of Engineering, Universidad Internacional de La Rioja, Spain a r t i c l e i n f oa b s t r a c t Article history: Choosing the Web framework that best fits the requirements is not an easy task for Received 1 October 2013 developers. Several frameworks now exist to develop Web applications, such as Struts, Received in revised form 18 December 2014 JSF, Ruby on Rails, Grails, CakePHP, Django, and Catalyst. However, Lift is a relatively new Accepted 19 December 2014 framework that emerged in 2007 for the Scala programming language and which promises Available online 5 January 2015 a great number of advantages and additional features. Companies such as Siemens© and Keywords: IBM®, as well as social networks such as Twitter® and Foursquare®, have now begun to Best practices develop their applications by using Scala and Lift. Best practices are activities, technical Lift or important issues identified by users in a specific context, and which have rendered Scala excellent service and are expected to achieve similar results in similar situations.