Protecting Your Computer and Your Identity
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

A Crawler-Based Study of Spyware on the Web
A Crawler-based Study of Spyware on the Web Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy Department of Computer Science & Engineering University of Washington {anm, tbragin, gribble, levy}@cs.washington.edu Abstract servers [16]. The AOL scan mentioned above has provided simple summary statistics by directly examining desktop in- Malicious spyware poses a significant threat to desktop fections [2], while a recent set of papers have considered security and integrity. This paper examines that threat from user knowledge of spyware and its behavior [6, 29]. an Internet perspective. Using a crawler, we performed a In this paper we change perspective, examining the na- large-scale, longitudinal study of the Web, sampling both ture of the spyware threat not on the desktop but from an executables and conventional Web pages for malicious ob- Internet point of view. To do this, we conduct a large-scale jects. Our results show the extent of spyware content. For outward-looking study by crawling the Web, downloading example, in a May 2005 crawl of 18 million URLs, we found content from a large number of sites, and then analyzing it spyware in 13.4% of the 21,200 executables we identified. to determine whether it is malicious. In this way, we can At the same time, we found scripted “drive-by download” answer several important questions. For example: attacks in 5.9% of the Web pages we processed. Our analy- sis quantifies the density of spyware, the types of of threats, • How much spyware is on the Internet? and the most dangerous Web zones in which spyware is • Where is that spyware located (e.g., game sites, chil- likely to be encountered. -

(Fake Websites) Spam, Phishing and Pharming Are All Terms Relating to Dubious
Spam (Junk email and Phishing email) and Pharming (fake websites) Spam, phishing and pharming are all terms relating to dubious online practices, either to sale goods or services online or to gain access to confidential information, often with malicious intent. Spam is the term used to describe unwanted (junk) emails that are typically distributed in bulk. Spam messages will typically contain commercial content – examples include pornography, pharmaceuticals, dubious financial transactions, or ‘too good to be true’ offers. In most cases, spam emails are sent with fraudulent intent, but there are also cases where reputable companies or private users send mass emails too. An example of Junk email: (to many recipients, requesting a response) Spam can also be used to launch phishing attacks where users are sent emails tricking them into ‘updating’ their personal details online via a fake website (imitating a bank or similar). The tricky part is that phishers pretend to be someone you know, like a bank or even a department from right here at Purdue, to make you think they are trustworthy. That’s why it’s so important to keep in mind that CLA-IT or any other Purdue department will NEVER, under any circumstance, ask you for your login information via email or web form. Anyone asking for this type of information via email is undoubtedly a fraud. Spam can also be used as a means of distributing malicious software, which can install key-logging software on your PC without your knowledge. Pharming is the term used to describe the process of redirecting users to a fraudulent copy of a legitimate website, again with the aim of stealing personal data and passwords for criminal intent. -
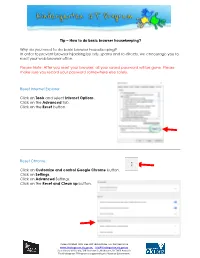
Tip – How to Do Basic Browser Housekeeping?
Tip – How to do basic browser housekeeping? Why do you need to do basic browser housekeeping? In order to prevent browser hijacking by ads, spams and re-directs, we encourage you to reset your web browser often. Please Note: After you reset your browser, all your saved password will be gone. Please make sure you record your password somewhere else safely. _______________________________________________________________________________________ Reset Internet Explorer Click on Tools and select Internet Options . Click on the Advanced tab. Click on the Reset button. _______________________________________________________________________________________ Reset Chrome Click on Customize and control Google Chrome button. Click on Settings . Click on Advanced Settings. Click on the Reset and Clean up button. Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Firefox In the address bar of the FireFox type in about:support and hit Enter. Click Refresh Firefox… button. A window will appear showing the details of this action. Click Refresh Firefox button. _______________________________________________________________________________________ Clear website data in Safari Click on Safari tab and select Preferences… Click Privacy tab. Click Manage Website Data… Click on Remove All . Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Edge Click on Settings and More button. -

COVID-19 Updates and Resources for Local Governments G Tuesday, March 23, 2021 Welcome Greeting
COVID-19 Updates and Resources for Local Governments g Tuesday, March 23, 2021 Welcome Greeting Kayla Rosen Departmental Analyst, Community Engagement and Finance, Department of Treasury 2 Tools and Resources for Local Governments: 11th Webinar Tuesday, March 23, 2021 – 2 p.m. – 3 p.m. I. Welcome & Introductions Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury I. Treasury Update a. CARES Act Grant b. FDCVT Grant c. Overviews of Recreational Marijuana Payments d. American Rescue Plan Eric Bussis, Chief Economist and Director of the Office of Revenue and Tax Analysis, Michigan Department of Treasury I. Cybersecurity for Local Governments Derek Larson, Acting Deputy Chief Security Officer, Department of Technology, Management and Budget (DTMB) I. Question and Answer II. Closing Remarks Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury 3 Welcome & Introductions Heather Frick Bureau Director, Bureau of Local Government and School Services, Department of Treasury 4 Treasury Local Government Funding Update Eric Bussis Chief Economist and Director Office of Revenue and Tax Analysis Michigan Department of Treasury 5 Treasury Update • CARES Act Grant • FDCVT Grant Agenda • Overviews of Recreational Marijuana Payments • American Rescue Plan 6 First Responder Hazard Pay Premiums Program (FRHPPP) • Payments made to 740 applicants, supporting approximately 37,500 first responders • 97 applications were selected for further federal -

Component 3 Learning Aim B Cyber Security- B1 Threats to Data Why Systems Are Attacked
Component 3 Learning Aim B Cyber Security- B1 Threats to Data Why Systems are Attacked Key Vocabulary Intellectual Property An idea that you invented that belongs to you, for example, an image that is copyrighted. Ransomware A form of malware, usually infecting unprotected digital systems, occurring when users open malicious email attachments. Malware A malicious form of software that is transferred to, and then executed on, a user’s machine to damage or disrupt the system or allow unauthorised access to data. Denial-of-Service (DoS) attacks Attack a remote computer by making it unable to respond to legitimate user requests. Cybersecurity The combination of policies, procedures, technologies and the actions of individuals to protect from both internal and external threats. Organisations have become reliant on digital systems to hold data and perform vital business functions. Data and information theft Many organisations have their digital systems attacked daily. Industrial Espionage Data and information both have value as they can be sold The reasons these attacks may occur are varied Intellectual property (designs, business strategy for financial gain. etc) can be stolen through organised cyberattacks. This can be done by stealing customer payment information and then using it to purchase goods These types of assets can be highly valuable, leading •Fun/ illegally. to cheaper, fake copies of products being sold and Breaches of data and information are a major cause of •challenge the original organisation suffering a loss of income. identity theft. •Data and Financial Gain Fun/ Challenge •Industrial information • Hackers may attack systems for the thrill, adrenaline espionage theft A very simple motive: money. -

The Emergence of Exploit-As-A-Service
Manufacturing Compromise: The Emergence of Exploit-as-a-Service Chris Grier† Lucas Ballard2 Juan Caballerox Neha Chachra∗ Christian J. Dietrichq Kirill Levchenko∗ Panayiotis Mavrommatis2 Damon McCoyz Antonio Nappax Andreas Pitsillidis∗ Niels Provos2 M. Zubair Rafiquex Moheeb Abu Rajab2 Christian Rossowq Kurt Thomasy Vern Paxson† Stefan Savage∗ Geoffrey M. Voelker∗ y University of California, Berkeley ∗ University of California, San Diego 2 Google International Computer Science Institute x IMDEA Software Institute q University of Applied Sciences Gelsenkirchen z George Mason University ABSTRACT 1. INTRODUCTION We investigate the emergence of the exploit-as-a-service model for In this work we investigate the emergence of a new paradigm: the driveby browser compromise. In this regime, attackers pay for an exploit-as-a-service economy that surrounds browser compromise. exploit kit or service to do the “dirty work” of exploiting a vic- This model follows in the footsteps of a dramatic evolution in the tim’s browser, decoupling the complexities of browser and plugin world of for-profit malware over the last five years, where host com- vulnerabilities from the challenges of generating traffic to a web- promise is now decoupled from host monetization. Specifically, the site under the attacker’s control. Upon a successful exploit, these means by which a host initially falls under an attacker’s control are kits load and execute a binary provided by the attacker, effectively now independent of the means by which an(other) attacker abuses transferring control of a victim’s machine to the attacker. the host in order to realize a profit. This shift in behavior is exem- In order to understand the impact of the exploit-as-a-service plified by the pay-per-install model of malware distribution, where paradigm on the malware ecosystem, we perform a detailed anal- miscreants pay for compromised hosts via the underground econ- ysis of the prevalence of exploit kits, the families of malware in- omy [4, 41]. -

Phishing – a Growing Threat to E-Commerce
Phishing – A Growing Threat to E-Commerce M. Tariq Banday* and Jameel A. Qadri** * Department of Electronics & Instrumentation Technology, The University of Kashmir, Srinagar – 190006, email: [email protected]. ** School of Computing, Middlesex University, Hendon, London, UK, email: [email protected]. Abstract: In today’s business environment, it is difficult to imagine a workplace without access to the web, yet a variety of email born viruses, spyware, adware, Trojan horses, phishing attacks, directory harvest attacks, DoS attacks, and other threats combine to attack businesses and customers. This paper is an attempt to review phishing – a constantly growing and evolving threat to Internet based commercial transactions. Various phishing approaches that include vishing, spear phishng, pharming, keyloggers, malware, web Trojans, and others will be discussed. This paper also highlights the latest phishing analysis made by Anti-Phishing Working Group (APWG) and Korean Internet Security Center. Introduction commerce has given a boon to both customers and Electronic Commerce (E-Commerce) is commercial businesses by driving down costs and prices. E- transactions conducted electronically especially commerce allows real-time business across using a computer over a large network like Internet. geographical borders round the clock. In developed It involves exchange of business information using countries almost all business employs e-commerce electronic data interchange (EDI), email, electronic or has e-commerce provisions and in developing bulletin boards, fax transmissions, electronic funds countries like India, it is registering a rapid growth transfer, etc. Internet shopping, online stock and in terms of both popularity among consumers and bond transactions, selling and purchase of soft the revenue generated through e-commerce merchandise like documents, graphics, music, (Vashitha–2005). -

Spyware & Adware Products
AdwareAdware/Spyware/Spyware ProductsProducts && RecommendationsRecommendations UCLAUCLA OfficeOffice ofof InstructionalInstructional DevelopmentDevelopment MikeMike TakahashiTakahashi AgendaAgenda WhatWhat isis AdwareAdware/Spyware/Spyware KnownKnown AdwareAdware/Spyware/Spyware ProductsProducts AntiAnti AdwareAdware/Spyware/Spyware RemovalRemoval ProductProduct ComparisonsComparisons TipsTips && RecommendationsRecommendations AdwareAdware AdwareAdware cancan bebe softwaresoftware thatthat generatesgenerates advertisementsadvertisements suchsuch asas poppop--upup windowswindows oror hotlinkshotlinks onon webweb pages.pages. ItIt maymay addadd linkslinks toto youryour favoritesfavorites andand youryour desktop.desktop. ItIt cancan changechange youryour homehome pagepage andand youryour searchsearch engineengine toto sitessites thatthat earnearn incomeincome fromfrom variousvarious advertisers.advertisers. Source http://www.microsoft.com/windows/ie/community/columns/adware.mspx AdwareAdware ExamplesExamples What?!What?! MyMy computercomputer isis infected!infected! OrOr isis it?it? AdwareAdware ExamplesExamples WellWell--knownknown AdwareAdware ProgramsPrograms toto AvoidAvoid HotbarHotbar (Add(Add--ons)ons) Adds graphical skins to Browser and Email clients Adds toolbars and search button BlockCheckerBlockChecker ClipGenieClipGenie CometComet CursorCursor GatorGator WinFixerWinFixer StumbleUponStumbleUpon WeatherBugWeatherBug SpywareSpyware SpywareSpyware isis computercomputer softwaresoftware thatthat collectscollects -

Detection of Pharming Attack on Websites Using Svm Classifier
INTERNATIONAL JOURNAL OF SCIENTIFIC & TECHNOLOGY RESEARCH VOLUME 8, ISSUE 11, NOVEMBER 2019 ISSN 2277-8616 Detection Of Pharming Attack On Websites Using Svm Classifier Saloni Manhas, Swapnesh Taterh, Dilbag Singh Abstract: Attackers are constantly trying to con users and organizations to cause financial damage, loss of sensitive information, and ruin their reputation. Pharming attacks are becoming a headache for website users due to its severe consequences. This attack is achieved by stealing user’s credentials and redirect them to malicious websites by using DNS based techniques. Therefore, to give additional safety Transport Layer Security/Secure Sockets Layer (TLS/SSL) was introduced. It operates by authorizing the actual web server for you to the customer, vice a new versa in so doing each party confirming the actual reliability by using digital certificates. However, SSL is still vulnerable to pharming attacks. Results show that the proposed technique provides 97% accuracy along with high performance in F-measure, sensitivity and specificity which is commendable and proves that SVM is an adequate machine learning method to successfully carry out detection of pharming attack. Index Terms: Phishing, Support Vector Machine (SVM), Secure Socket Layer (SSL) attacks, Malicious websites, Pharming, Machine learning, Network attacks. —————————— —————————— 1. INTRODUCTION DNS cache poisoning, pharming attack is executed and It is quite evident that all of the advances seen in the leaves user facing dire consequences like password information technology realm helped both the good guys hijacking, stolen credentials etc. It is often said that HTTP and the bad. Subsequently, we have seen a steep increase should not be used to pass sensitive information. -

Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software comes with more or less unwanted add-ons or browser toolbars. These are quite annoying because they may: Change your homepage and your search engine without your permission or awareness Track your browsing activities and searches Display annoying ads and manipulate search results Take up a lot of (vertical) space inside the browser Slow down your browser and degrade your browsing experience Fight against each other and make normal add-on handling difficult or impossible Become difficult or even impossible for the average user to fully uninstall Toolbars are not technically not a virus, but they do exhibit plenty of malicious traits, such as rootkit capabilities to hook deep into the operating system, browser hijacking, and in general just interfering with the user experience. The industry generally refers to it as a “PUP,” or potentially unwanted program. Generally speaking, toolbars are ad-supported (users may see additional banner, search, pop-up, pop-under, interstitial and in-text link advertisements) cross web browser plugin for Internet Explorer, Firefox and Chrome, and distributed through various monetization platforms during installation. Very often users have no idea where did it come from, so it’s not surprising at all that most of them assume that the installed toolbar is a virus. For example, when you install iLivid Media Player, you will also agree to change your browser homepage to search.conduit.com, set your default search engine to Conduit Search, and install the AVG Search-Results Toolbar. -

Informational Supplement Best Practices on Spyware Prevention and Detection the Internet Has Become a Popular Method for Both C
Informational Supplement Best Practices on Spyware Prevention and Detection The Internet has become a popular method for both conducting business and managing finances through online banking relationships. While most financial institutions and some individuals have taken steps to protect their computers, many firewall and anti-virus software packages do not protect computers from one of the latest threats, “spyware” – a form of software that collects personal and confidential information about a person or organization without their proper knowledge or informed consent, and reports it to a third party. This informational supplement describes the various challenges and best practices related to spyware. Financial institutions should consider these recommendations to prevent and detect spyware on both bank-owned and customer computers. Spyware Infection Spyware is usually installed without a user’s knowledge or permission. However, users may intentionally install spyware without understanding the full ramifications of their actions. A user may be required to accept an End User Licensing Agreement (EULA), which often does not clearly inform the user about the extent or manner in which information is collected. In such cases, the software is installed without the user’s “informed consent.” Spyware can be installed through the following methods: • Downloaded with other Internet downloads in a practice called “bundling.” In many cases, all the licensing agreements may be included in one pop-up window that, unless read carefully, may leave the user unaware of “bundled” spyware. • Directly downloaded by users who were persuaded that the technology offers a benefit. Some spyware claims to offer increased productivity, virus scanning capabilities or other benefits.