Course Bidding at Business Schools
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Text Editing in UNIX: an Introduction to Vi and Editing
Text Editing in UNIX A short introduction to vi, pico, and gedit Copyright 20062009 Stewart Weiss About UNIX editors There are two types of text editors in UNIX: those that run in terminal windows, called text mode editors, and those that are graphical, with menus and mouse pointers. The latter require a windowing system, usually X Windows, to run. If you are remotely logged into UNIX, say through SSH, then you should use a text mode editor. It is possible to use a graphical editor, but it will be much slower to use. I will explain more about that later. 2 CSci 132 Practical UNIX with Perl Text mode editors The three text mode editors of choice in UNIX are vi, emacs, and pico (really nano, to be explained later.) vi is the original editor; it is very fast, easy to use, and available on virtually every UNIX system. The vi commands are the same as those of the sed filter as well as several other common UNIX tools. emacs is a very powerful editor, but it takes more effort to learn how to use it. pico is the easiest editor to learn, and the least powerful. pico was part of the Pine email client; nano is a clone of pico. 3 CSci 132 Practical UNIX with Perl What these slides contain These slides concentrate on vi because it is very fast and always available. Although the set of commands is very cryptic, by learning a small subset of the commands, you can edit text very quickly. What follows is an outline of the basic concepts that define vi. -

AIX Globalization
AIX Version 7.1 AIX globalization IBM Note Before using this information and the product it supports, read the information in “Notices” on page 233 . This edition applies to AIX Version 7.1 and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 2010, 2018. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents About this document............................................................................................vii Highlighting.................................................................................................................................................vii Case-sensitivity in AIX................................................................................................................................vii ISO 9000.....................................................................................................................................................vii AIX globalization...................................................................................................1 What's new...................................................................................................................................................1 Separation of messages from programs..................................................................................................... 1 Conversion between code sets............................................................................................................. -
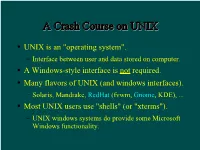
A Crash Course on UNIX
AA CCrraasshh CCoouurrssee oonn UUNNIIXX UNIX is an "operating system". Interface between user and data stored on computer. A Windows-style interface is not required. Many flavors of UNIX (and windows interfaces). Solaris, Mandrake, RedHat (fvwm, Gnome, KDE), ... Most UNIX users use "shells" (or "xterms"). UNIX windows systems do provide some Microsoft Windows functionality. TThhee SShheellll A shell is a command-line interface to UNIX. Also many flavors, e.g. sh, bash, csh, tcsh. The shell provides commands and functionality beyond the basic UNIX tools. E.g., wildcards, shell variables, loop control, etc. For this tutorial, examples use tcsh in RedHat Linux running Gnome. Differences are minor for the most part... BBaassiicc CCoommmmaannddss You need these to survive: ls, cd, cp, mkdir, mv. Typically these are UNIX (not shell) commands. They are actually programs that someone has written. Most commands such as these accept (or require) "arguments". E.g. ls -a [show all files, incl. "dot files"] mkdir ASTR688 [create a directory] cp myfile backup [copy a file] See the handout for a list of more commands. AA WWoorrdd AAbboouutt DDiirreeccttoorriieess Use cd to change directories. By default you start in your home directory. E.g. /home/dcr Handy abbreviations: Home directory: ~ Someone else's home directory: ~user Current directory: . Parent directory: .. SShhoorrttccuuttss To return to your home directory: cd To return to the previous directory: cd - In tcsh, with filename completion (on by default): Press TAB to complete filenames as you type. Press Ctrl-D to print a list of filenames matching what you have typed so far. Completion works with commands and variables too! Use ↑, ↓, Ctrl-A, & Ctrl-E to edit previous lines. -

Introduction to Unix Shell (Part I)
Introduction to Unix shell (part I) Evgeny Stambulchik Faculty of Physics, Weizmann Institute of Science, Rehovot 7610001, Israel Joint ICTP-IAEA School on Atomic Processes in Plasmas February 27 – March 3, 2017 Trieste, Italy Contrary to popular belief, Unix is user friendly. It just happens to be very selective about who it decides to make friends with. Unknown Initially used at Bell Labs, but soon licensed to academy (notably, U. of California, Berkeley) and commercial vendors (IBM, Sun, etc). There are two major products that came out of Berkeley: LSD and Unix. We don’t believe this to be a coincidence. Jeremy S. Anderson, Unix systems administrator Historical overview (kind of) Unix is a family of multiuser, multitasking operating systems stemming from the original Unix developed in the 1970’s at Bell Labs by Ken Thompson, Dennis Ritchie1, and others. Some consider Unix to be the second most important invention to come out of AT&T Bell Labs after the transistor. Dennis Ritchie 1Also famous for creating the C programming language. Historical overview (kind of) Unix is a family of multiuser, multitasking operating systems stemming from the original Unix developed in the 1970’s at Bell Labs by Ken Thompson, Dennis Ritchie1, and others. Some consider Unix to be the second most important invention to come out of AT&T Bell Labs after the transistor. Dennis Ritchie Initially used at Bell Labs, but soon licensed to academy (notably, U. of California, Berkeley) and commercial vendors (IBM, Sun, etc). There are two major products that came out of Berkeley: LSD and Unix. -

Comparative Studies of 10 Programming Languages Within 10 Diverse Criteria Revision 1.0
Comparative Studies of 10 Programming Languages within 10 Diverse Criteria Revision 1.0 Rana Naim∗ Mohammad Fahim Nizam† Concordia University Montreal, Concordia University Montreal, Quebec, Canada Quebec, Canada [email protected] [email protected] Sheetal Hanamasagar‡ Jalal Noureddine§ Concordia University Montreal, Concordia University Montreal, Quebec, Canada Quebec, Canada [email protected] [email protected] Marinela Miladinova¶ Concordia University Montreal, Quebec, Canada [email protected] Abstract This is a survey on the programming languages: C++, JavaScript, AspectJ, C#, Haskell, Java, PHP, Scala, Scheme, and BPEL. Our survey work involves a comparative study of these ten programming languages with respect to the following criteria: secure programming practices, web application development, web service composition, OOP-based abstractions, reflection, aspect orientation, functional programming, declarative programming, batch scripting, and UI prototyping. We study these languages in the context of the above mentioned criteria and the level of support they provide for each one of them. Keywords: programming languages, programming paradigms, language features, language design and implementation 1 Introduction Choosing the best language that would satisfy all requirements for the given problem domain can be a difficult task. Some languages are better suited for specific applications than others. In order to select the proper one for the specific problem domain, one has to know what features it provides to support the requirements. Different languages support different paradigms, provide different abstractions, and have different levels of expressive power. Some are better suited to express algorithms and others are targeting the non-technical users. The question is then what is the best tool for a particular problem. -

Unix-And-Radiance.Pdf
UNIX and RADIANCE Giulio Antonutto & Andrew McNeil Unix Terminal 3 Starting the Terminal Application 3 Useful Unix Commands 3 Wildcard Characters 4 Directory Characters 4 Process control 4 Pipes and Redirection 4 Shell Redirection Operators 5 Makefile 5 X11 - X Window Server 7 Launching X11 7 The First Time 7 SCRIPTING 8 HOW TO START 8 HOW TO CONTINUE 9 Create the file ‘run’ 9 Give the proper permissions 9 Run the new tool 9 Future 9 UNIX and RADIANCE 2 Unix Terminal Starting the Terminal Application On a Mac the terminal program can be found in the /Applications/Utilities folder. When launched a window titled “Terminal - Bash - 80 x 24” will appear. This window contains a Unix prompt (which is in some ways similar to a DOS prompt for those familiar with windows). At the prompt you can type commands that will be executed within the terminal window. Useful Unix Commands The following UNIX commands will allow the user to navigate through the file system, manipulate files, check and terminate running processes. Command Description Usage Useful options ls list directory contents ls -l lists additional file info ls folder/ -a lists all files (including hidden files) cd change directory cd folder/folder2/ cd .. more view a text file one page at a time more file.txt cp copy file cp file.txt newfile.txt mv move a file mv oldloc.txt newloc..txt rm remove a file rm file DANGER, DO NOT USE: rm * ps list currently running processes ps top list the currently running processes top -u -s 5 5 and various system statistic UNIX and RADIANCE 3 Command Description Usage Useful options kill kills a running process kill pid pid is the process id number which can be found by using ps. -

Create Directory on Windows Without the Fleeting DOS Window Hsiwei Yu (Michael), People Technology Solution Inc, Edison, NJ Gary Huang, Infostat Inc., Belle Mead, NJ
Create Directory on Windows Without the Fleeting DOS Window Hsiwei Yu (Michael), People Technology Solution Inc, Edison, NJ Gary Huang, InfoStat Inc., Belle Mead, NJ copy “source directory” “target directory” ABSTRACT for copying files from source directory to target directory. On newer Windows environments, the pipe feature on a filename statement can be used to create directory without the fleeting Most DOS commands return nothing when successful. Some DOS window. This is better than the X command approach. Any commands, like DIR and COPY, return useful information that DOS commands can be used in the filename pipe feature. Finally can be further analyzed. we will show example of managing directories on remote machine Filename fileref PIPE ‘dir “c:\a dir”’; from local SAS session. Data important_message; Infile fileref length= LNG; Input @; INTRODUCTION /* Put _infile_; */ Sometimes we need to create or delete a directory from within a /* Additional logic to parse the directory SAS session. Previously we can use the X command construct to contents for further analysis. */ issue such create directory (MKDIR) command. However this if LNG >= 8 then do; technique results in an annoying DOS window, flashing and input last_modified_date mmddyy8. @; vanishing on screen. On newer Windows environment and with … the filename pipe feature, we can accomplish the same without end; the extra DOS window. Run; THE FILENAME PIPE FEATURE APPLICATON: MANAGE DIRECTORY ON The filename pipe feature is available is in the Windows environment in both SAS 6.12 -

UNIX Reference Card Create a Directory Called Options: -I Interactive Mode
File System Manipulation Move (Rename) Files and Directories mv present-filename new-filename to rename a file Create (or Make) a Directory mv source-filename destination-directory to move a file into another directory mkdir directory-name directory-name UNIX Reference Card create a directory called options: -i interactive mode. Must confirm file overwrites. Anatomy of a Unix Command Look at a File Copy Files more filename man display file contents, same navigation as cp source-filename destination-filename to copy a file into command-name -option(s) filename(s) or arguments head filename display first ten lines of a file another file tail filename display last ten lines of a file Example: wc -l sample cp source-filename destination-directory to copy a file into another directory : options options: The first word of the command line is usually the command name. This -# replace # with a number to specify how many lines to show is followed by the options, if any, then the filenames, directory name, or -i interactive mode. Must confirm overwrites. Note: this other arguments, if any, and then a RETURN. Options are usually pre- option is automatically used on all IT’s systems. -R recursive delete ceded by a dash and you may use more than one option per command. List Files and Directories The examples on this reference card use bold case for command names Remove (Delete) Files and Directories and options and italics for arguments and filenames. ls lists contents of current directory ls directory-name list contents of directory rm filename to remove a file rmdir directory-name to remove an Important Note about UNIX Commands empty directory : options options: -a list all files including files that start with “.” UNIX commands are case sensitive. -
50 Most Frequently Used UNIX / Linux Commands (With Examples)
17/10/13 50 Most Frequently Used UNIX / Linux Commands (With Examples) Home Free eBook Start Here Archives Contact About 50 Most Frequently Used UNIX / Linux Commands (With Examples) by Ramesh Natarajan on November 8, 2010 290 Curtir 375 Tw eet 325 This article provides practical examples for 50 most frequently used commands in Linux / UNIX. This is not a comprehensive list by any means, but this should give you a jumpstart on some of the common Linux commands. Bookmark this article for your future reference. Did I miss any frequently used Linux commands? Leave a comment and let me know. 1. tar command examples Create a new tar archive. $ tar cvf archive_name.tar dirname/ Extract from an existing tar archive. $ tar xvf archive_name.tar View an existing tar archive. www.thegeekstuff.com/2010/11/50-linux-commands/ 1/32 17/10/13 50 Most Frequently Used UNIX / Linux Commands (With Examples) $ tar tvf archive_name.tar More tar examples: The Ultimate Tar Command Tutorial with 10 Practical Examples 2. grep command examples Search for a given string in a file (case in-sensitive search). $ grep -i "the" demo_file Print the matched line, along with the 3 lines after it. $ grep -A 3 -i "example" demo_text Search for a given string in all files recursively $ grep -r "ramesh" * More grep examples: Get a Grip on the Grep! – 15 Practical Grep Command Examples 3. find command examples Find files using file-name ( case in-sensitve find) # find -iname "MyCProgram.c" Execute commands on files found by the find command $ find -iname "MyCProgram.c" -exec md5sum {} \; Find all empty files in home directory # find ~ -empty More find examples: Mommy, I found it! — 15 Practical Linux Find Command Examples 4. -

Mastering the VI Editor
University of Hawaii at Manoa College of Engineering Mastering the VI editor Index • Introduction • Conventions • Before You Begin • Starting the VI Editor • Getting Out of VI • The Two Modes of VI • How to Type Commands in Command Mode • Some Simple VI Commands • Text Buffers in VI • Cutting and Yanking • Pasting • Indenting Your Code and Checking • Word and Character Searching • Settings for VI (and EX) • Abbreviations and Mapping Keys to Other Keys • The EXINIT Environment Variable and the .exrc file • Recovering Your Work When Something Goes Wrong with Your Terminal • Warning About Using VI on the Workstations • Summary of VI Commands o Cutting and Pasting/Deleting text o Inserting New Text o Moving the Cursor Around the Screen o Replacing Text o Searching for Text or Characters o Manipulating Character/Line Formatting o Saving and Quitting o Miscellany o EX Commands Introduction The VI editor is a screen-based editor used by many Unix users. The VI editor has powerful features to aid programmers, but many beginning users avoid using VI because the different features overwhelm them. This tutorial is written to help beginning users get accustomed to using the VI editor, but also contains sections relevant to regular users of VI as well. Examples are provided, and the best way to learn is to try these examples, and think of your own examples as well... There's no better way than to experience things yourself. Conventions In this tutorial, the following convention will be used: ^X denotes a control character. For example, if you see: ^d in the tutorial, that means you hold down the control key and then type the corresponding letter. -
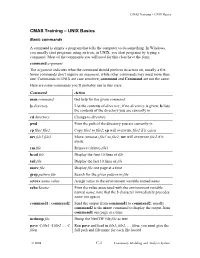
CMAS Training – UNIX Basics
CMAS Training – UNIX Basics CMAS Training – UNIX Basics Basic commands A command is simply a program that tells the computer to do something. In Windows, you usually start programs using an icon; in UNIX, you start programs by typing a command. Most of the commands you will need for this class have the form: command argument The argument indicates what the command should perform its action on, usually a file. Some commands don’t require an argument, while other commands may need more than one. Commands in UNIX are case sensitive; command and Command are not the same. Here are some commands you’ll probably use in this class: Command Action man command Get help for the given command ls directory List the contents of directory; if no directory is given, ls lists the contents of the directory you are currently in cd directory Change to directory pwd Print the path of the directory you are currently in cp file1 file2 Copy file1 to file2; cp will overwrite file2 if it exists mv file1 file2 Move (rename) file1 to file2; mv will overwrite file2 if it exists rm file Remove (delete) file1 head file Display the first 10 lines of file tail file Display the last 10 lines of file more file Display file one page at a time grep pattern file Search for the given pattern in file setenv name value Assign value to the environment variable named name echo $name Print the value associated with the environment variable named name; note that the $ character immediately precedes name (no space) command1 | command2 Send the output from command1 to command2; usually command2 is the more command to display the output from command1 one page at a time ncdump file Dump the NetCDF file file as text pave -f file1 -f file2 … -f Run pave and load in file1, file2, … filen; you must give the filen full path and file name for each file loaded © 2008 C-1 Community Modeling and Analysis System CMAS Training – UNIX Basics Files and directories Files in UNIX are organized into directories, similar to folders in Windows. -

Linux Programmer's Manual ICONV(1)
ICONV(1) Linux Programmer’s Manual ICONV(1) NAME iconv − character set conversion SYNOPSIS iconv [-c][-s][-f encoding][-t encoding][inputfile ...] iconv -l DESCRIPTION The iconv program converts text from one encoding to another encoding. More precisely, it converts from the encoding given for the -f option to the encoding given for the -t option. Either of these encod- ings defaults to the encoding of the current locale. All the inputfiles are read and converted in turn; if no inputfile is given, the standard input is used. The converted text is printed to standard output. When option -c is given, characters that cannot be converted are silently discarded, instead of leading to a conversion error. When option -s is given, error messages about invalid or unconvertible characters are omitted, but the actual converted text is unaffected. The encodings permitted are system dependent. For the libiconv implementation, they are listed in the iconv_open(3) manual page. The iconv -l command lists the names of the supported encodings, in a system dependent format. For the libiconv implementation, the names are printed in upper case, separated by whitespace, and alias names of an encoding are listed on the same line as the encoding itself. SEE ALSO iconv_open(3), locale(7) GNU January 13, 2002 1 ICONV(3) Linux Programmer’s Manual ICONV(3) NAME iconv − perform character set conversion SYNOPSIS #include <iconv.h> size_t iconv (iconv_t cd, const char* * inbuf , size_t * inbytesleft, char* * outbuf , size_t * outbytesleft); DESCRIPTION The argument cd must be a conversion descriptor created using the function iconv_open. The main case is when inbuf is not NULL and *inbuf is not NULL.