ADS Chapter 545
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mysql NDB Cluster 7.5.16 (And Later)
Licensing Information User Manual MySQL NDB Cluster 7.5.16 (and later) Table of Contents Licensing Information .......................................................................................................................... 2 Licenses for Third-Party Components .................................................................................................. 3 ANTLR 3 .................................................................................................................................... 3 argparse .................................................................................................................................... 4 AWS SDK for C++ ..................................................................................................................... 5 Boost Library ............................................................................................................................ 10 Corosync .................................................................................................................................. 11 Cyrus SASL ............................................................................................................................. 11 dtoa.c ....................................................................................................................................... 12 Editline Library (libedit) ............................................................................................................. 12 Facebook Fast Checksum Patch .............................................................................................. -

Linux in Your Lap Session 9365
Linux in Your Lap Session 9365 Rich Smrcina - Sytek Services, Inc. August 20, 2002 SHARE 99 – San Francisco GGiivviinngg CCrreeddiitt • UNIX is a registered trademark licensed exclusively through The Open Group. • LINUX is a registered trademark of Linus Torvalds & others. • Microsoft, Windows NT, Windows Millennium & MSDOS are registered trademarks of Microsoft Corporation • StarOffice Writer, Calc, & Impress are registered trademarks of Sun, Inc. • Applixware Words, Spreadsheets, Presents & Office are registered trademarks of VistaSource, Inc., a wholly-owned subsidiary of Applix, Inc. • Anyware Desktop & Anyware Realtime are registered trademarks of VistaSource, Inc. • WordPerfect Office 2000 is a registered trademark of Corel, Inc. • AbiWord & AbiSource are registered trademarks of AbiSource, Inc. • Gnumeric is copyright © 1998, 1999 by Michael de Icaza Amozurrutia • VMware is a trademark of VMware, Inc. • Wine is Copyright © 1993-2000 by the Wine Project authors. • Win4Lin is a registered trademark of NeTraverse Inc. • Satellite is a registered trademark of Toshiba Corporation. • Intel & Celeron are registered trademarks of Intel Corporation. • All other brand & product names are trademarks or registered trademarks of their respective companies Page 2 of “Linux in Your Lap”, Copyright 2002, Sytek Services, Inc. GGiivviinngg CCrreeddiitt • z/Linux &Turbolinux are registered trademarks of Turbolinux, Inc. • Red Hat is a registered trademark of Red Hat, Inc. • SuSE is a registered trademark of SuSE AG. Page 3 of “Linux in Your Lap”, Copyright 2002, Sytek Services, Inc. OOff CCoouurrssee • The Joys & Heartaches of Running Linux on a Laptop Speaker: Rich Smrcina, Sytek Services, Inc. Length: 1 hour Classification: Technical When: Tuesday 1:30pm Where: San Francisco Hilton Page 4 of “Linux in Your Lap”, Copyright 2002, Sytek Services, Inc. -

Linux + Windows 95 Mini-HOWTO
Linux + Windows 95 mini−HOWTO Jonathon Katz [email protected] Joy Yokley − Converted document from HTML to DocBook 4.1 (SGML) 2001−03−01 Revision History Revision 1.1.1 2001−04−19 Revised by: DCM Corrected a typo. Revision 1.1 2001−02−28 Revised by: JEY Revision 1.0 1998−08−15 Revised by: JK Revision 0.9 1996−10−26 Revised by: JK Revision 0.8 1996−06−25 Revised by: JK This document details how to install Linux on a machine that currently runs Windows 95" Linux + Windows 95 mini−HOWTO Table of Contents 1. Introduction.....................................................................................................................................................1 2. Installation Options........................................................................................................................................2 2.1. I Have This Partition I Want to Spare!.............................................................................................2 2.2. What Is This 528M 1024th Cylinder Stuff?.....................................................................................2 3. What's Next.....................................................................................................................................................3 4. Using Your New System.................................................................................................................................4 4.1. Installing on a Drive with FAT32.....................................................................................................4 -

Veritas™Resiliency Platform 3.3 Third-Party Software License Agreements Veritas Resiliency Platform: Third Party Software License Agreements
Veritas™Resiliency Platform 3.3 Third-Party Software License Agreements Veritas Resiliency Platform: Third Party Software License Agreements Last updated: 2018-09-03 Document version: Document version: 3.3 Rev 0 Legal Notice Copyright © 2018 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas Logo, Veritas InfoScale, and NetBackup are trademarks or registered trademarks of Veritas Technologies LLC or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. This product may contain third-party software for which Veritas is required to provide attribution to the third party (“Third-Party Programs”). Some of the Third-Party Programs are available under open source or free software licenses. The License Agreement accompanying the Software does not alter any rights or obligations you may have under those open source or free software licenses. Refer to the third-party legal notices document accompanying this Veritas product or available at: https://www.veritas.com/licensing/process The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Veritas Technologies LLC and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. VERITAS TECHNOLOGIES LLC SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. -

HPE Bladesystem Onboard Administrator User Guide
HPE BladeSystem Onboard Administrator User Guide Abstract This guide provides information on the initial setup and operation of the HPE BladeSystem Onboard Administrator. It also covers use of the Onboard Administrator GUI and enclosure Insight Display. The information in this guide applies to version 4.71 (or later) of the HPE BladeSystem Onboard Administrator. Part Number: 695522-403 Published: September 2017 Edition: 29 © Copyright 2006, 2017 Hewlett Packard Enterprise Development LP Notices The information contained herein is subject to change without notice. The only warranties for Hewlett Packard Enterprise products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Hewlett Packard Enterprise shall not be liable for technical or editorial errors or omissions contained herein. Confidential computer software. Valid license from Hewlett Packard Enterprise required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor's standard commercial license. Links to third-party websites take you outside the Hewlett Packard Enterprise website. Hewlett Packard Enterprise has no control over and is not responsible for information outside the Hewlett Packard Enterprise website. Acknowledgments Intel®, Itanium®, Pentium®, Intel Inside®, and the Intel Inside logo are trademarks of Intel Corporation in the United States and other countries. Microsoft® and Windows® are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. Adobe® and Acrobat® are trademarks of Adobe Systems Incorporated. -

Security and Hardening Guide Security and Hardening Guide SUSE Linux Enterprise Server 15 SP1
SUSE Linux Enterprise Server 15 SP1 Security and Hardening Guide Security and Hardening Guide SUSE Linux Enterprise Server 15 SP1 Introduces basic concepts of system security, covering both local and network security aspects. Shows how to use the product inherent security software like AppArmor, SELinux, or the auditing system that reliably collects information about any security-relevant events. Supports the administrator with security-related choices and decisions in installing and setting up a secure SUSE Linux Enterprise Server and additional processes to further secure and harden that installation. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its -

Linux Laptop-HOWTO
Linux Laptop−HOWTO Linux Laptop−HOWTO Table of Contents Linux Laptop−HOWTO.....................................................................................................................................1 Werner Heuser <[email protected]>....................................................................................................1 1. Preface..................................................................................................................................................1 2. Copyright, Disclaimer and Trademarks...............................................................................................1 3. Which Laptop to Buy?.........................................................................................................................1 4. Laptop Distribution..............................................................................................................................2 5. Installation...........................................................................................................................................2 6. Hardware In Detail...............................................................................................................................2 7. Palmtops, Personal Digital Assistants − PDAs, Handheld PCs − HPCs.............................................2 8. Cellular Phones, Pagers, Calculators, Digital Cameras, Wearable Computing...................................3 9. Accessories..........................................................................................................................................3 -

Open Source Licenses
Threat Protection System v5.1.0 Open Source Licenses The TippingPoint Threat Protection System (TPS) devices use open source components. Many open source license agreements require user documentation to contain notification that the open source software is included in the product. For inquiries about acquiring license code, contact support. The following agreements are for software that this product includes or may include: • "BIND License Agreement" on page 9 • "boost License Agreement" on page 10 • "coreutils License Agreement regarding coreutils & libmspack" on page 11 • "corosync License Agreement" on page 20 • "cpputest License Agreement" on page 21 • "License Agreement regarding dbus; ecryptfs-utils; gdb; glibc; gptfdisk; ipset; keyutils; libcgi; libnih; libstatgrab; linux; lm-sensors; lttng; mxml; net-tools; open-vm-tools; pam-tacplus; rng-tools; RRDTool; syslog-ng; upstart & util-linux" on page 22 • "gSoap License Agreement" on page 26 • "host-sflow License Agreement" on page 33 • "ipmitool License Agreement" on page 38 • "jitterentropy-rngd License Agreement" on page 39 • "libpcap License Agreement" on page 40 • "libxml License Agreement" on page 41 • "NTP License Agreement" on page 42 • "OpenSSH License Agreement" on page 43 • "License Agreement regarding OpenSSL & openssl-fips" on page 49 • "qDecoder License Agreement" on page 52 • "shadow License Agreement" on page 53 • "tcpdump License Agreement" on page 55 TippingPoint acknowledges that the following open source components may be used in this product: • Adaptive Public License -

BIG-IP® Systems and Safenet® Luna SA HSM: Implementation
BIG-IP® Systems and SafeNet® Luna SA HSM: Implementation Version 11.5 Table of Contents Table of Contents Legal Notices and Acknowledgments......................................................................................5 Legal Notices.....................................................................................................................5 Acknowledgments..............................................................................................................6 Implementing the SafeNet Luna HSM with BIG-IP Systems.................................................23 Overview: Implementing the SafeNet Luna SA HSM with BIG-IP Systems.....................23 Task summary..................................................................................................................23 Prerequisites for implementing BIG-IP and SafeNet Luna SA HSM.....................23 Preparing to install the Luna SA client on the BIG-IP system...............................24 Installing and registering the Luna SA client.........................................................24 Generating a key/certificate using tmsh................................................................25 Generating a key/certificate using the Luna SA client...........................................25 Importing external HSM keys using tmsh..............................................................26 Adding certificates using tmsh..............................................................................26 Creating a client SSL profile to use an external -
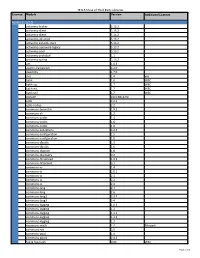
Third Party Libraries License Module Version Additional Licenses
TE 8.5.5 Use of Third Party Libraries License Module Version Additional Licenses Apache (1.1/2.0) activemq-broker 5.13.2 activemq-client 5.13.2 activemq-client 5.14.2 activemq-jms-pool 5.13.2 activemq-kahadb-store 5.13.2 activemq-openwire-legacy 5.13.2 activemq-pool 5.13.2 activemq-protobuf 1.1 activemq-spring 5.13.2 ant 1.6.3 avalon-framework 4.2.0 awaitility 1.7.0 axis 1.4 yes batik 1.6 W3C batik-css 1.7 W3C batik-ext 1.7 W3C batik-util 1.7 W3C BoneCP 0.8.0.RELEASE cglib 2.2.1 cglib-nodep 2.2 commons-beanutils 1.9.2 commons-cli 1.2 commons-codec 1.4 commons-codec 1.6 commons-codec 1.9 commons-collections 3.2.2 commons-configuration 1.5 commons-configuration 1.8 commons-dbutils 1.3 commons-dbutils 1.6 commons-digester 1.8 commons-discovery 0.2 commons-fileupload 1.3.2 commons-httpclient 3.1 commons-io 1.4 commons-io 2.0.1 commons-io 2.1 commons-io 2.2 commons-io 2.4 commons-lang 2.4 commons-lang 2.6 commons-lang3 3.3.2 commons-lang3 3.4 commons-logging 1.0.3 commons-logging 1.1 commons-logging 1.1.1 commons-logging 1.1.3 commons-logging 1.2 commons-math 2.2 Minpack commons-net 3.5 commons-pool 1.4 commons-pool2 2.4.2 fop & fop-hyph 0.94 W3C Page 1 of 8 TE 8.5.5 Use of Third Party Libraries License Module Version Additional Licenses geronimo-j2ee-management_1.1_spec 1.0.1 geronimo-jms_1.1_spec 1.1.1 geronimo-jta_1.0.1B_spec 1.0.1 google-gin 1.5.0 google-guava r09 google-guava 11.0.2 google-guava 14.0.1 google-guava 15.0 google-guava 16.0.1 google-guava 18.0 google-guava 20 google-guava 21 google-guava-gwt 15.0 guava-retrying 2.0.0 google-guice -
Opensuse Leap 42.2 Security Guide Opensuse Leap 42.2
Security Guide openSUSE Leap 42.2 Security Guide openSUSE Leap 42.2 Introduces basic concepts of system security, covering both local and network secu- rity aspects. Shows how to use the product inherent security software like AppAr- mor or the auditing system that reliably collects information about any security-rel- evant events. Publication Date: November 05, 2018 SUSE LLC 10 Canal Park Drive Suite 200 Cambridge MA 02141 USA https://www.suse.com/documentation Copyright © 2006– 2018 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Docu- mentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see http://www.suse.com/company/legal/ . All other third-party trademarks are the prop- erty of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xv 1 Security and Confidentiality 1 1.1 Local Security and Network Security 1 Local Security 3 • Network Security 6 -

Cisco Telepresence ISDN Link IL1.0 Open Source Documentation
Open Source Used In Cisco TelePresence ISDN Link IL1.0 This document contains the licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of the source code to which you are entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License) , please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-18510928 Contents 1.1 bash 4.2 1.1.1 Available under license 1.2 coreutils 8.15 1.2.1 Available under license 1.3 curl 7.24.0 1.3.1 Available under license 1.4 dbus 1.4.10 1.4.1 Available under license 1.5 dbus-glib 0.88 1.5.1 Available under license 1.6 dhcp 4.1.1 1.6.1 Available under license 1.7 eventlog 0.2.12 Open Source Used In Cisco TelePresence ISDN Link IL1.0 1 1.7.1 Available under license 1.8 expat 2.0.1 1.8.1 Available under license 1.9 fuse 2.8.7 1.9.1 Available under license 1.10 gawk 3.1.6 1.10.1 Available under license 1.11 glib 2.24.0 1.11.1 Available under license 1.12 glibc 2.13 1.12.1 Available under license 1.13 glibmm 2.20.1 1.13.1 Available under license 1.14 grep 2.6.3 :2.el6 1.14.1 Available under license 1.15 gzip 1.4 1.15.1 Available under license 1.16 icu4c 3.8.1 1.16.1 Available under license 1.17 ipcalc 1.3 1.17.1 Available under license 1.18 iproute2 2.6.34 1.18.1 Available under license 1.19 iptables 1.4.13 1.19.1 Available under license 1.20 iputils s20100214 1.20.1