Opensuse Leap 15.1 Security Guide Opensuse Leap 15.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Suse Linux Enterprise Server 12 - Administration Guide Pdf, Epub, Ebook
SUSE LINUX ENTERPRISE SERVER 12 - ADMINISTRATION GUIDE PDF, EPUB, EBOOK Admin Guide Contributors | 630 pages | 28 Apr 2016 | Samurai Media Limited | 9789888406500 | English | none SUSE Linux Enterprise Server 12 - Administration Guide PDF Book To prevent the conflicts, before starting the migration, execute the following as a super user:. PA, IA In todays service oriented IT zero downtime becomes more and more a most wanted feature. If you want to change actions for single packages, right-click a package in the package view and choose an action. When debugging a problem, you sometimes need to temporarily install a lot of -debuginfo packages which give you more information about running processes. If you are only reading the release notes of the current release, you could miss important changes. However, this can be changed through macro configuration. In this case, the oldest zswap pages are written back to disk-based swap. YaST snapshots are labeled as zypp y2base in the Description column ; Zypper snapshots are labeled zypp zypper. Global variables, or environment variables, can be accessed in all shells. If it is 0 zero the command was successful, everything else marks an error which is specific to the command. The installation medium must be inserted in the HMC. Maintaining netgroup data. This option fetches changes in repositories, but keeps the disabled repositories in the same state—disabled. The rollback snapshots are therefore automatically deleted when the set number of snapshots is reached. The visible physical entity, as it is typically mounted to a motherboard or an equivalent. When using the self-signed certificate, you need to confirm its signature before the first connection. -

Mysql NDB Cluster 7.5.16 (And Later)
Licensing Information User Manual MySQL NDB Cluster 7.5.16 (and later) Table of Contents Licensing Information .......................................................................................................................... 2 Licenses for Third-Party Components .................................................................................................. 3 ANTLR 3 .................................................................................................................................... 3 argparse .................................................................................................................................... 4 AWS SDK for C++ ..................................................................................................................... 5 Boost Library ............................................................................................................................ 10 Corosync .................................................................................................................................. 11 Cyrus SASL ............................................................................................................................. 11 dtoa.c ....................................................................................................................................... 12 Editline Library (libedit) ............................................................................................................. 12 Facebook Fast Checksum Patch .............................................................................................. -
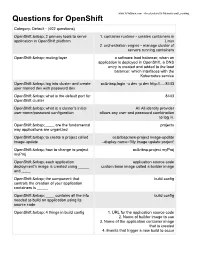
Questions for Openshift
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for OpenShift Category: Default - (402 questions) OpenShift: 2 primary tools to serve 1. container runtime - creates containers in application in OpenShift platform Linux 2. orchestration engine - manage cluster of servers running containers OpenShift: routing layer a software load balancer, when an application is deployed in OpenShift, a DNS entry is created and added to the load balancer, which interfaces with the Kubernetes service OpenShift: log into cluster and create oc login -u dev -p dev http://....:8443 user named dev with password dev OpenShift: what is the default port for 8443 OpenShift cluster OpenShift: what is a cluster's initial All All identity provider user name/password configuration allows any user and password combination to log in. OpenShift: ____ are the fundamental projects way applications are organized OpenShift: to create a project called oc new-project image-update image-update --display-name='My image update project' OpenShift: how to change to project oc project myProj myProj OpenShift: each application application source code deployment's image is created using _____ custom base image called a builder image and ____ OpenShift: the component that build config controls the creation of your application containers is _____ OpenShift: ____ contains all the info build config needed to build an application using its source code OpenShift: 4 things in build config 1. URL for the application source code 2. Name of builder image to use 3. Name of the application container image that is created 4. -
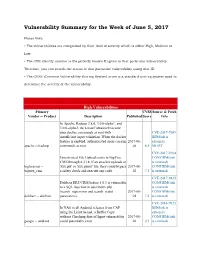
Vulnerability Summary for the Week of June 5, 2017
Vulnerability Summary for the Week of June 5, 2017 Please Note: • The vulnerabilities are categorized by their level of severity which is either High, Medium or Low. • The CVE identity number is the publicly known ID given to that particular vulnerability. Therefore, you can search the status of that particular vulnerability using that ID. • The CVSS (Common Vulnerability Scoring System) score is a standard scoring system used to determine the severity of the vulnerability. High Vulnerabilities Primary CVSS Source & Patch Vendor -- Product Description Published Score Info In Apache Hadoop 2.8.0, 3.0.0-alpha1, and 3.0.0-alpha2, the LinuxContainerExecutor runs docker commands as root with CVE-2017-7669 insufficient input validation. When the docker BID(link is feature is enabled, authenticated users can run 2017-06- external) apache -- hadoop commands as root. 04 8.5 MLIST CVE-2017-9364 Unrestricted File Upload exists in BigTree CONFIRM(link CMS through 4.2.18: if an attacker uploads an is external) bigtreecms -- 'xxx.pht' or 'xxx.phtml' file, they could bypass 2017-06- CONFIRM(link bigtree_cms a safety check and execute any code. 02 7.5 is external) CVE-2017-9435 Dolibarr ERP/CRM before 5.0.3 is vulnerable CONFIRM(link to a SQL injection in user/index.php is external) (search_supervisor and search_statut 2017-06- CONFIRM(link dolibarr -- dolibarr parameters). 05 7.5 is external) CVE-2014-9923 In NAS in all Android releases from CAF BID(link is using the Linux kernel, a Buffer Copy external) without Checking Size of Input vulnerability 2017-06- CONFIRM(link google -- android could potentially exist. -

A U T O M at E D I N S Ta L L At
Proceedings of LISA '99: 13th Systems Administration Conference Seattle, Washington, USA, November 7–12, 1999 A U T O M AT E D I N S TA L L AT I O N O F L I N U X S Y S T E M S U S I N G YA S T Dirk Hohndel and Fabian Herschel THE ADVANCED COMPUTING SYSTEMS ASSOCIATION © 1999 by The USENIX Association All Rights Reserved For more information about the USENIX Association: Phone: 1 510 528 8649 FAX: 1 510 548 5738 Email: [email protected] WWW: http://www.usenix.org Rights to individual papers remain with the author or the author's employer. Permission is granted for noncommercial reproduction of the work for educational or research purposes. This copyright notice must be included in the reproduced paper. USENIX acknowledges all trademarks herein. Automated Installation of Linux Systems Using YaST Dirk Hohndel and Fabian Herschel – SuSE Rhein/Main AG ABSTRACT The paper describes how to allow a customized automated installation of Linux. This is possible via CDRom, network or tape, using a special boot disk that describes the system that should be set up and either standard SuSE Linux CDs, customized install CDs, an appropriately configured installation server, or a tape backup of an existing machine. A control file on the boot disk and additional (optional) control files on the install medium specify which settings should be used and which packages should be installed. This includes settings like language, key table, network setup, hard disk partitioning, packages to install, etc. After giving a quick overview of the syntax and capabilities of this installation method, considerations about how to plan the automated installation at larger sites are presented. -

(Un)Smashing the Stack
Hello, Interwebs Hi, and thanks for reading this. As I mentioned a number of times during the talk this was one long, hard slog of a topic for me. My intent was not to duplicate existing research (Johnson and Silberman @ BHUS05, others), but to try to make this topic comprehensible for the typical security professional, who (GASP! SHOCK! HORROR!) may not necessarily grasp all the hairy internals of exploit development, but still is tasked with protecting systems. For the other 90% of us out there, our job is not to be leet, but rather not to get owned, something I hope to get a little bit better at every day. Since exploit mitigation is something that might bring us all a little bit closer to that, I wanted to explore the topic. Thanks much to BH for giving me the opportunity to do so, and to all of you for listening. Thanks also to all the amazing people working on these technologies, especially the PaX team and Hiroaki Etoh of IBM. -- shawn P.S. It’s actually Thompson that had the Phil Collins hair, not Ritchie. Sorry, Dennis. 28 75 6e 29 53 6d 61 73 68 69 6e 67 20 74 68 65 20 53 74 61 63 6b 0d 0a (un)Smashing the Stack 4f 76 65 72 66 6c 6f 77 73 2c 20 43 6f 75 6e 74 65 72 6d 65 61 73 75 72 65 73 20 61 6e 64 20 74 68 65 20 52 65 61 6c 20 57 6f 72 6c 64 Overflows, Countermeasures and the Real World Shawn Moyer :: Chief Researcher ---- SpearTip Technologies ---> blackhat [at] cipherpunx [dot] org Hey, who is this guy? ShawnM: InfoSec consultant, (quasi-) developer, husband, father, and raging paranoid with obsessive tendencies Chief Researcher at SpearTip Technologies Security Consultancy in Saint Louis, MO Forensics, Assessment, MSSP, network analysis Weddings, Funerals, Bar Mitzvahs I like unsolvable problems, so I’m mostly interested in defense. -

Linux in Your Lap Session 9365
Linux in Your Lap Session 9365 Rich Smrcina - Sytek Services, Inc. August 20, 2002 SHARE 99 – San Francisco GGiivviinngg CCrreeddiitt • UNIX is a registered trademark licensed exclusively through The Open Group. • LINUX is a registered trademark of Linus Torvalds & others. • Microsoft, Windows NT, Windows Millennium & MSDOS are registered trademarks of Microsoft Corporation • StarOffice Writer, Calc, & Impress are registered trademarks of Sun, Inc. • Applixware Words, Spreadsheets, Presents & Office are registered trademarks of VistaSource, Inc., a wholly-owned subsidiary of Applix, Inc. • Anyware Desktop & Anyware Realtime are registered trademarks of VistaSource, Inc. • WordPerfect Office 2000 is a registered trademark of Corel, Inc. • AbiWord & AbiSource are registered trademarks of AbiSource, Inc. • Gnumeric is copyright © 1998, 1999 by Michael de Icaza Amozurrutia • VMware is a trademark of VMware, Inc. • Wine is Copyright © 1993-2000 by the Wine Project authors. • Win4Lin is a registered trademark of NeTraverse Inc. • Satellite is a registered trademark of Toshiba Corporation. • Intel & Celeron are registered trademarks of Intel Corporation. • All other brand & product names are trademarks or registered trademarks of their respective companies Page 2 of “Linux in Your Lap”, Copyright 2002, Sytek Services, Inc. GGiivviinngg CCrreeddiitt • z/Linux &Turbolinux are registered trademarks of Turbolinux, Inc. • Red Hat is a registered trademark of Red Hat, Inc. • SuSE is a registered trademark of SuSE AG. Page 3 of “Linux in Your Lap”, Copyright 2002, Sytek Services, Inc. OOff CCoouurrssee • The Joys & Heartaches of Running Linux on a Laptop Speaker: Rich Smrcina, Sytek Services, Inc. Length: 1 hour Classification: Technical When: Tuesday 1:30pm Where: San Francisco Hilton Page 4 of “Linux in Your Lap”, Copyright 2002, Sytek Services, Inc. -

Guide to Open Source Solutions
White paper ___________________________ Guide to open source solutions “Guide to open source by Smile ” Page 2 PREAMBLE SMILE Smile is a company of engineers specialising in the implementing of open source solutions OM and the integrating of systems relying on open source. Smile is member of APRIL, the C . association for the promotion and defence of free software, Alliance Libre, PLOSS, and PLOSS RA, which are regional cluster associations of free software companies. OSS Smile has 600 throughout the World which makes it the largest company in Europe - specialising in open source. Since approximately 2000, Smile has been actively supervising developments in technology which enables it to discover the most promising open source products, to qualify and assess them so as to offer its clients the most accomplished, robust and sustainable products. SMILE . This approach has led to a range of white papers covering various fields of application: Content management (2004), portals (2005), business intelligence (2006), PHP frameworks (2007), virtualisation (2007), and electronic document management (2008), as well as PGIs/ERPs (2008). Among the works published in 2009, we would also cite “open source VPN’s”, “Firewall open source flow control”, and “Middleware”, within the framework of the WWW “System and Infrastructure” collection. Each of these works presents a selection of best open source solutions for the domain in question, their respective qualities as well as operational feedback. As open source solutions continue to acquire new domains, Smile will be there to help its clients benefit from these in a risk-free way. Smile is present in the European IT landscape as the integration architect of choice to support the largest companies in the adoption of the best open source solutions. -

Linux + Windows 95 Mini-HOWTO
Linux + Windows 95 mini−HOWTO Jonathon Katz [email protected] Joy Yokley − Converted document from HTML to DocBook 4.1 (SGML) 2001−03−01 Revision History Revision 1.1.1 2001−04−19 Revised by: DCM Corrected a typo. Revision 1.1 2001−02−28 Revised by: JEY Revision 1.0 1998−08−15 Revised by: JK Revision 0.9 1996−10−26 Revised by: JK Revision 0.8 1996−06−25 Revised by: JK This document details how to install Linux on a machine that currently runs Windows 95" Linux + Windows 95 mini−HOWTO Table of Contents 1. Introduction.....................................................................................................................................................1 2. Installation Options........................................................................................................................................2 2.1. I Have This Partition I Want to Spare!.............................................................................................2 2.2. What Is This 528M 1024th Cylinder Stuff?.....................................................................................2 3. What's Next.....................................................................................................................................................3 4. Using Your New System.................................................................................................................................4 4.1. Installing on a Drive with FAT32.....................................................................................................4 -

Red Hat Directory Server 11 Installation Guide
Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Last Updated: 2021-04-23 Red Hat Directory Server 11 Installation Guide Instructions for installing Red Hat Directory Server Marc Muehlfeld Red Hat Customer Content Services [email protected] Legal Notice Copyright © 2021 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Red Hat Enterprise Linux 6 6.4 Release Notes
Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Last Updated: 2017-10-20 Red Hat Enterprise Linux 6 6.4 Release Notes Release Notes for Red Hat Enterprise Linux 6.4 Edition 4 Red Hat Engineering Content Services Legal Notice Copyright © 2012 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Debian \ Amber \ Arco-Debian \ Arc-Live \ Aslinux \ Beatrix
Debian \ Amber \ Arco-Debian \ Arc-Live \ ASLinux \ BeatriX \ BlackRhino \ BlankON \ Bluewall \ BOSS \ Canaima \ Clonezilla Live \ Conducit \ Corel \ Xandros \ DeadCD \ Olive \ DeMuDi \ \ 64Studio (64 Studio) \ DoudouLinux \ DRBL \ Elive \ Epidemic \ Estrella Roja \ Euronode \ GALPon MiniNo \ Gibraltar \ GNUGuitarINUX \ gnuLiNex \ \ Lihuen \ grml \ Guadalinex \ Impi \ Inquisitor \ Linux Mint Debian \ LliureX \ K-DEMar \ kademar \ Knoppix \ \ B2D \ \ Bioknoppix \ \ Damn Small Linux \ \ \ Hikarunix \ \ \ DSL-N \ \ \ Damn Vulnerable Linux \ \ Danix \ \ Feather \ \ INSERT \ \ Joatha \ \ Kaella \ \ Kanotix \ \ \ Auditor Security Linux \ \ \ Backtrack \ \ \ Parsix \ \ Kurumin \ \ \ Dizinha \ \ \ \ NeoDizinha \ \ \ \ Patinho Faminto \ \ \ Kalango \ \ \ Poseidon \ \ MAX \ \ Medialinux \ \ Mediainlinux \ \ ArtistX \ \ Morphix \ \ \ Aquamorph \ \ \ Dreamlinux \ \ \ Hiwix \ \ \ Hiweed \ \ \ \ Deepin \ \ \ ZoneCD \ \ Musix \ \ ParallelKnoppix \ \ Quantian \ \ Shabdix \ \ Symphony OS \ \ Whoppix \ \ WHAX \ LEAF \ Libranet \ Librassoc \ Lindows \ Linspire \ \ Freespire \ Liquid Lemur \ Matriux \ MEPIS \ SimplyMEPIS \ \ antiX \ \ \ Swift \ Metamorphose \ miniwoody \ Bonzai \ MoLinux \ \ Tirwal \ NepaLinux \ Nova \ Omoikane (Arma) \ OpenMediaVault \ OS2005 \ Maemo \ Meego Harmattan \ PelicanHPC \ Progeny \ Progress \ Proxmox \ PureOS \ Red Ribbon \ Resulinux \ Rxart \ SalineOS \ Semplice \ sidux \ aptosid \ \ siduction \ Skolelinux \ Snowlinux \ srvRX live \ Storm \ Tails \ ThinClientOS \ Trisquel \ Tuquito \ Ubuntu \ \ A/V \ \ AV \ \ Airinux \ \ Arabian