IDOL Keyview XML Export SDK 12.4 Java Programming Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
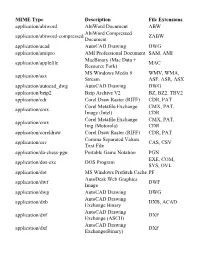
MIME Type Description File Extensions Application/Abiword
MIME Type Description File Extensions application/abiword AbiWord Document ABW AbiWord Compressed application/abiword-compressed ZABW Document application/acad AutoCAD Drawing DWG application/amipro AMI Professional Document SAM, AMI MacBinary (Mac Data + application/applefile MAC Resource Fork) MS Windows Media 9 WMV, WMA, application/asx Stream ASF, ASR, ASX application/autocad_dwg AutoCAD Drawing DWG application/bzip2 Bzip Archive V2 BZ, BZ2, TBV2 application/cdr Corel Draw Raster (RIFF) CDR, PAT Corel Metafile Exchange CMX, PAT, application/cmx Image (Intel) CDR Corel Metafile Exchange CMX, PAT, application/cmx Img (Motorola) CDR application/coreldraw Corel Draw Raster (RIFF) CDR, PAT Comma Separated Values application/csv CAS, CSV Text File application/da-chess-pgn Portable Game Notation PGN EXE, COM, application/dos-exe DOS Program SYS, OVL application/dot MS Windows Prefetch Cache PF AutoDesk Web Graphics application/dwf DWF Image application/dwg AutoCAD Drawing DWG AutoCAD Drawing application/dxb DXB, ACAD Exchange Binary AutoCAD Drawing application/dxf DXF Exchange (ASCII) AutoCAD Drawing application/dxf DXF Exchange(Binary) EMF, TMP, EMF, TMP, application/emf Windows Enhanced Metafile WMF application/envoy Envoy Document EVY, ENV Comma Separated Values application/excel CAS, CSV Text File MS Excel XLS, XLA, application/excel Worksheet/Add-In/Template XLT, XLB EXE, COM, application/exe DOS Program SYS, OVL EXE, VXD, application/exe MS Windows Driver (16 bit) SYS, DRV, 386 MS Windows Program (16 application/exe EXE, MOD, BIN bit) -

Windows Registry Troubleshooting
Halsey · Bettany BOOKS FOR PROFESSIONALS BY PROFESSIONALS® WINDOWS TROUBLESHOOTING SERIES Windows Registry Troubleshooting Windows Registry Troubleshooting Windows Windows Registry Troubleshooting will help IT pros diagnose and repair problems with any Windows version in the workplace, including hardware and so ware incompatibilities, corrupt registries and how to implement common tweaks and hacks. Whatever version of Windows you’re using—from Vista up to Windows 8.1—the registry is at the heart of your desktop experience. So ware installs and compatibility, hardware operation, and more are managed by a complex database of codes and numbers. When something goes wrong it can seem impossible to diagnose and repair the problem, and harder still to prevent a recurrence or make the subtle changes and tweaks required to x the problem. In Windows Registry Troubleshooting we’ll take you inside the workings of the Registry, and teach you how to repair, modify and clean it to keep your PCs running smoothly. Highlights include: • How to navigate the architecture of the Windows Registry • How to troubleshoot faulty and corrupt Registry items • How to edit and work with the Registry fi les of other users on a PC • What tools and utilities can help you work with and repair the Registry • How to secure the registry on a Windows PC Windows • What Registry tweaks and hacks can make using your Windows PC a better experience Registry Troubleshooting Diagnose and repair problems with any ISBN 978-1-4842-0993-6 Windows version from Vista to Windows 8.1 52499 US $24.99 — Shelve in Mike Halsey, MVP 9781484 209936 Windows/General Andrew Bettany, MVP www.apress.com For your convenience Apress has placed some of the front matter material after the index. -

PHP Introduction
PHP PHP ─ Introduction PHP started out as a small open source project that evolved as more and more people found out how useful it was. Rasmus Lerdorf unleashed the first version of PHP way back in 1994. PHP is a recursive acronym for "PHP: Hypertext Preprocessor". PHP is a server side scripting language that is embedded in HTML. It is used to manage dynamic content, databases, session tracking, even build entire e- commerce sites. It is integrated with a number of popular databases, including MySQL, PostgreSQL, Oracle, Sybase, Informix, and Microsoft SQL Server. PHP is pleasingly zippy in its execution, especially when compiled as an Apache module on the Unix side. The MySQL server, once started, executes even very complex queries with huge result sets in record-setting time. PHP supports a large number of major protocols such as POP3, IMAP, and LDAP. PHP4 added support for Java and distributed object architectures (COM and CORBA), making n-tier development a possibility for the first time. PHP is forgiving: PHP language tries to be as forgiving as possible. PHP Syntax is C-Like. Common Uses of PHP PHP performs system functions, i.e. from files on a system it can create, open, read, write, and close them. The other uses of PHP are: PHP can handle forms, i.e. gather data from files, save data to a file, thru email you can send data, return data to the user. You add, delete, modify elements within your database thru PHP. Access cookies variables and set cookies. Using PHP, you can restrict users to access some pages of your website. -
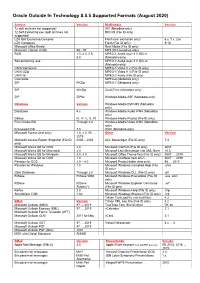
Supported Formats (August 2020)
Oracle Outside In Technology 8.5.5 Supported Formats (August 2020) Archive Version Multimedia Version 7z split archives not supported) AVI (Metadata only) 7z Self Extracting exe (split archives not DICOM (File ID only) supported) LZA Self Extracting Compres Flash (text extraction only) 6.x, 7.x, Lite LZH Compress Flash (File ID only) 9,10 Microsoft Office Binder Real Media (File ID only) Microsoft Cabinet (CAB) 95 – 97 MP3 (ID3 metadata only) RAR 1.5, 2.0, 2.9, MPEG-1 Audio layer 3 V ID3 v1 5.0 (Metadata only) Self-extracting .exe MPEG-1 Audio layer 3 V ID3 v2 (Metadata only) UNIX Compress MPEG-1 Video V 2 (File ID only) UNIX GZip MPEG-1 Video V 3 (File ID only) UNIX tar MPEG-2 Audio (File ID only) Uuencode MPEG-4 (Metadata only) ZIP PKZip MPEG-7 (Metadata only) ZIP WinZip QuickTime (Metadata only) ZIP ZIP64 Windows Media ASF (Metadata only) Database Version Windows Media DVR-MS (Metadata only) DataEase 4.x Windows Media Audio WMA (Metadata only) DBase III, IV, V, X, X1 Windows Media Playlist (File ID only) First Choice DB Through 3.0 Windows Media Video WMV (Metadata only) Framework DB 3.0 WAV (Metadata only) Microsoft Access (text only) 1.0, 2.0, 95 … Other Version 2019 Microsoft Access Report Snapshot (File ID 2000 – 2003 AOL Messenger (File ID only) 7.3 only) Microsoft Works DB for DOS 2.0 Microsoft InfoPath (File ID only) 2007 Microsoft Works DB for Macintosh 2.0 Microsoft Live Messenger (via XML filter) 10.0 Microsoft Works DB for Windows 3.0, 4.0 Microsoft Office Theme files (File ID only) 2007 … 2019 Microsoft Works DB for DOS -

Venture Capital Pitch Guide Toolkit #3
VENTURE CAPITAL PITCH GUIDE TOOLKIT #3 This project is part of This project has received funding from the European Union’s Horizon 2020 Programme under Grant Agreement Nº. 825014 HOW DOES IT WORK? Show how the solution to the problem you have found works By this time you should have answered the following: WHAT is the problem? WHO has the problem? WHY is it a problem? Does it solve the problem? WHAT is your value proposition? “The only way to win is to learn faster than anyone else” Eric Ries Technical Financial validation validation Minimize the time in this loop Market validation It is an Iterative process TOOLKIT #3 TOOLKIT #4 TOOLKIT #5 The next parts of the toolkit are to be seen as an iterative process as well What’s next? You have shown why your product/service is better for your target. Now it is time to show that magic! In the end you should be answering this: HOW does your product/service work? WHAT are the main features? WHAT is your development roadmap? Show how does it work We believe that the best way to put your idea to test is to have an iterative process that goes like a loop cycle of: building, measuring and learning. This is the idea behind the Lean Startup and MVP (minimum viable product)! So, what is an MVP? “The minimum viable product is that version of a new product a team uses to collect the maximum amount of validated learning about customers with the least effort." It’s meant to begin the process of learning. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -

Mac OS X: an Introduction for Support Providers
Mac OS X: An Introduction for Support Providers Course Information Purpose of Course Mac OS X is the next-generation Macintosh operating system, utilizing a highly robust UNIX core with a brand new simplified user experience. It is the first successful attempt to provide a fully-functional graphical user experience in such an implementation without requiring the user to know or understand UNIX. This course is designed to provide a theoretical foundation for support providers seeking to provide user support for Mac OS X. It assumes the student has performed this role for Mac OS 9, and seeks to ground the student in Mac OS X using Mac OS 9 terms and concepts. Author: Robert Dorsett, manager, AppleCare Product Training & Readiness. Module Length: 2 hours Audience: Phone support, Apple Solutions Experts, Service Providers. Prerequisites: Experience supporting Mac OS 9 Course map: Operating Systems 101 Mac OS 9 and Cooperative Multitasking Mac OS X: Pre-emptive Multitasking and Protected Memory. Mac OS X: Symmetric Multiprocessing Components of Mac OS X The Layered Approach Darwin Core Services Graphics Services Application Environments Aqua Useful Mac OS X Jargon Bundles Frameworks Umbrella Frameworks Mac OS X Installation Initialization Options Installation Options Version 1.0 Copyright © 2001 by Apple Computer, Inc. All Rights Reserved. 1 Startup Keys Mac OS X Setup Assistant Mac OS 9 and Classic Standard Directory Names Quick Answers: Where do my __________ go? More Directory Names A Word on Paths Security UNIX and security Multiple user implementation Root Old Stuff in New Terms INITs in Mac OS X Fonts FKEYs Printing from Mac OS X Disk First Aid and Drive Setup Startup Items Mac OS 9 Control Panels and Functionality mapped to Mac OS X New Stuff to Check Out Review Questions Review Answers Further Reading Change history: 3/19/01: Removed comment about UFS volumes not being selectable by Startup Disk. -

Netpbm Format - Wikipedia, the Free Encyclopedia
Netpbm format - Wikipedia, the free encyclopedia http://en.wikipedia.org/wiki/Portable_anymap Netpbm format From Wikipedia, the free encyclopedia (Redirected from Portable anymap) The phrase Netpbm format commonly refers to any or all Portable pixmap of the members of a set of closely related graphics formats used and defined by the Netpbm project. The portable Filename .ppm, .pgm, .pbm, pixmap format (PPM), the portable graymap format extension .pnm (PGM) and the portable bitmap format (PBM) are image file formats designed to be easily exchanged between Internet image/x-portable- platforms. They are also sometimes referred to collectively media type pixmap, -graymap, [1] as the portable anymap format (PNM). -bitmap, -anymap all unofficial Developed Jef Poskanzer Contents by 1 History Type of Image file formats 2 File format description format 2.1 PBM example 2.2 PGM example 2.3 PPM example 3 16-bit extensions 4 See also 5 References 6 External links History The PBM format was invented by Jef Poskanzer in the 1980s as a format that allowed monochrome bitmaps to be transmitted within an email message as plain ASCII text, allowing it to survive any changes in text formatting. Poskanzer developed the first library of tools to handle the PBM format, Pbmplus, released in 1988. It mainly contained tools to convert between PBM and other graphics formats. By the end of 1988, Poskanzer had developed the PGM and PPM formats along with their associated tools and added them to Pbmplus. The final release of Pbmplus was December 10, 1991. In 1993, the Netpbm library was developed to replace the unmaintained Pbmplus. -

SGML As a Framework for Digital Preservation and Access. INSTITUTION Commission on Preservation and Access, Washington, DC
DOCUMENT RESUME ED 417 748 IR 056 976 AUTHOR Coleman, James; Willis, Don TITLE SGML as a Framework for Digital Preservation and Access. INSTITUTION Commission on Preservation and Access, Washington, DC. ISBN ISBN-1-887334-54-8 PUB DATE 1997-07-00 NOTE 55p. AVAILABLE FROM Commission on Preservation and Access, A Program of the Council on Library and Information Resources, 1400 16th Street, NW, Suite 740, Washington, DC 20036-2217 ($20). PUB TYPE Reports Evaluative (142) EDRS PRICE MF01/PC03 Plus Postage. DESCRIPTORS *Access to Information; Computer Oriented Programs; *Electronic Libraries; *Information Retrieval; Library Automation; Online Catalogs; *Preservation; Standards IDENTIFIERS Digital Technology; *SGML ABSTRACT This report explores the suitability of Standard Generalized Markup Language (SGML) as a framework for building, managing, and providing access to digital libraries, with special emphasis on preservation and access issues. SGML is an international standard (ISO 8879) designed to promote text interchange. It is used to define markup languages, which can then encode the logical structure and content of any so-defined document. The connection between SGML and the traditional concerns of preservation and access may not be immediately apparent, but the use of descriptive markup tools such as SGML is crucial to the quality and long-term accessibility of digitized materials. Beginning with a general exploration of digital formats for preservation and access, the report provides a staged technical tutorial on the features and uses of SGML. The tutorial covers SGML and related standards, SGML Document Type Definitions in current use, and related projects now under development. A tiered metadata model is described that could incorporate SGML along with other standards to facilitate discovery and retrieval of digital documents. -

Association of Gene Ontology Categories with Decay Rate for Hepg2 Experiments These Tables Show Details for All Gene Ontology Categories
Supplementary Table 1: Association of Gene Ontology Categories with Decay Rate for HepG2 Experiments These tables show details for all Gene Ontology categories. Inferences for manual classification scheme shown at the bottom. Those categories used in Figure 1A are highlighted in bold. Standard Deviations are shown in parentheses. P-values less than 1E-20 are indicated with a "0". Rate r (hour^-1) Half-life < 2hr. Decay % GO Number Category Name Probe Sets Group Non-Group Distribution p-value In-Group Non-Group Representation p-value GO:0006350 transcription 1523 0.221 (0.009) 0.127 (0.002) FASTER 0 13.1 (0.4) 4.5 (0.1) OVER 0 GO:0006351 transcription, DNA-dependent 1498 0.220 (0.009) 0.127 (0.002) FASTER 0 13.0 (0.4) 4.5 (0.1) OVER 0 GO:0006355 regulation of transcription, DNA-dependent 1163 0.230 (0.011) 0.128 (0.002) FASTER 5.00E-21 14.2 (0.5) 4.6 (0.1) OVER 0 GO:0006366 transcription from Pol II promoter 845 0.225 (0.012) 0.130 (0.002) FASTER 1.88E-14 13.0 (0.5) 4.8 (0.1) OVER 0 GO:0006139 nucleobase, nucleoside, nucleotide and nucleic acid metabolism3004 0.173 (0.006) 0.127 (0.002) FASTER 1.28E-12 8.4 (0.2) 4.5 (0.1) OVER 0 GO:0006357 regulation of transcription from Pol II promoter 487 0.231 (0.016) 0.132 (0.002) FASTER 6.05E-10 13.5 (0.6) 4.9 (0.1) OVER 0 GO:0008283 cell proliferation 625 0.189 (0.014) 0.132 (0.002) FASTER 1.95E-05 10.1 (0.6) 5.0 (0.1) OVER 1.50E-20 GO:0006513 monoubiquitination 36 0.305 (0.049) 0.134 (0.002) FASTER 2.69E-04 25.4 (4.4) 5.1 (0.1) OVER 2.04E-06 GO:0007050 cell cycle arrest 57 0.311 (0.054) 0.133 (0.002) -

Supported File Types and Size Limits
Data Security Supported File Formats and Size Limits Supported File Formats and Size Limits | Data Security Solutions | Version 7.7.x This article provides a list of all the Supported File Formats that can be analyzed by Websense Data Security, as well as the File Size Limits for network, endpoint, and discovery functions. Supported File Formats Supported File Formats and Size Limits | Data Security Solutions | Version 7.7.x This article provides a list of all the file formats that Websense Data Security supports. The file formats supported are constantly being updated and added to. File Type Description 7-Zip 7-Zip format Ability Comm Communication Ability Ability DB Database Ability Ability Image Raster Image Ability Ability SS Spreadsheet Ability Ability WP Word Processor Ability AC3 Audio File Format AC3 Audio File Format ACE ACE Archive ACT ACT AD1 AD1 evidence file Adobe FrameMaker Adobe FrameMaker Adobe FrameMaker Book Adobe FrameMaker Book Adobe Maker Interchange Adobe Maker Interchange format Adobe PDF Portable Document Format Advanced Streaming Microsoft Advanced Streaming file Advanced Systems Format Advanced Systems Format (ASF) Data Security - Supported Files Types and Size Limits 1 Data Security Supported File Formats and Size Limits File Type Description Advanced Systems Format Advanced Systems Format (WMA) Advanced Systems Format Advanced Systems Format (WMV) AES Multiplus Comm Multiplus (AES) Aldus Freehand Mac Aldus Freehand Mac Aldus PageMaker (DOS) Aldus PageMaker for Windows Aldus PageMaker (Mac) Aldus PageMaker -

Symantec Web Security Service Policy Guide
Web Security Service Policy Guide Revision: NOV.07.2020 Symantec Web Security Service/Page 2 Policy Guide/Page 3 Copyrights Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. Copyright © 2020 Broadcom. All Rights Reserved. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. Policy Guide/Page 4 Symantec WSS Policy Guide The Symantec Web Security Service solutions provide real-time protection against web-borne threats. As a cloud-based product, the Web Security Service leverages Symantec's proven security technology, including the WebPulse™ cloud community. With extensive web application controls and detailed reporting features, IT administrators can use the Web Security Service to create and enforce granular policies that are applied to all covered users, including fixed locations and roaming users. If the WSS is the body, then the policy engine is the brain. While the WSS by default provides malware protection (blocks four categories: Phishing, Proxy Avoidance, Spyware Effects/Privacy Concerns, and Spyware/Malware Sources), the additional policy rules and options you create dictate exactly what content your employees can and cannot access—from global allows/denials to individual users at specific times from specific locations.