Abusing Third-Party Web Services As C&C Channels Artturi Lehtiö
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Guide to Onedrive
Microsoft’s OneDrive Quick start guide for students OneDrive Quick start guide Contents About this guide ...................................................................................................................... 3 What is OneDrive? .................................................................................................................. 3 Important considerations ....................................................................................................... 3 Bandwidth best practice ................................................................................................... 3 Getting started ..................................................................................................................... 4 Technical support ................................................................................................................ 4 Appropriate Use ................................................................................................................... 4 Sharing files ........................................................................................................................ 4 School vs Personal files ............................................................................................... 5 Enrolment status ........................................................................................................... 5 General advice.............................................................................................................. 5 Getting started with OneDrive -

Windows 10 Conquering the Basics and Beyond
SUN CITY SUMMERLIN COMPUTER CLUB WINDOWS 10 CONQUERING THE BASICS AND BEYOND MAKING THE TRANSITION FROM EARLIER EDITIONS OF WINDOWS PARTICIPANT’S PDF MANUAL Updated: August 20, 2016 now at 267 pages BY BILL WILKINSON TABLE OF CONTENTS THE ENTIRE MANUAL IS INDEXED. JUST PRESS CTRL + F TO ACCESS A SEARCH (FIND) FUNCTION CHAPTER ONE (Overview) CHAPTER FOURTEEN (Settings) CHAPTER TWO (Backup and Recovery) CHAPTER FIFTEEN (Notifications/Actions) CHAPTER THREE (Data History) CHAPTER SIXTEEN (new features) CHAPTER FOUR (Microsoft and Local CHAPTER SEVENTEEN (Edge browser) Accounts) CHAPTER EIGHTEEN (Cortana) CHAPTER FIVE (keyboard shortcuts) CHAPTER NINETEEN (Microsoft Store) CHAPTER SIX (Start Menu, Start Screen) CHAPTER TWENTY (tablet mode) CHAPTER SEVEN (Desktop) CHAPTER TWENTY-ONE (great free CHAPTER EIGHT (Search) programs) CHAPTER NINE (Apps) CHAPTER TWENTY-TWO (restore, CHAPTER TEN (File Explorer) refresh, reset) CHAPTER ELEVEN (OneDrive) CHAPTER TWENTY-THREE (other issues) CHAPTER TWELVE (Defender) CHAPTER TWENTY-FOUR (laptop issues) CHAPTER THIRTEEN (updates) CHAPTER ONE AN OVERVIEW WINDOWS 10 COMBINES THE BEST OF WINDOWS 7 AND WINDOWS 8.1 Windows 10 is designed to be intuitive for users of both Windows 7 and Windows 8.1, incorporating the “best of both worlds” to enhance your experience and help you be more productive. A GUIDE TO THE BARE-BONES BASICS OF WINDOWS 10 If you have just downloaded and installed Windows 10, you might find the following list of questions and answers will give you a “jump start” to your basic understanding of your new operating system. Where’s the Start Button? It’s in the lower-left corner of the Desktop. Click once to open and see the Start Menu. -
How-To-Use-Microsoft-Onedrive.Pdf
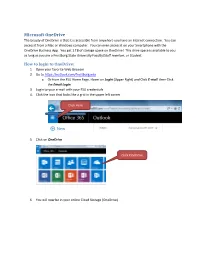
Microsoft OneDrive The beauty of OneDrive is that it is accessible from anywhere you have an Internet connection. You can access it from a Mac or Windows computer. You can even access it on your Smartphone with the OneDrive Business App. You get 1 TB of storage space on OneDrive! This drive space is available to you as long as you are a Frostburg State University Faculty/Staff member, or Student. How to login to OneDrive: 1. Open your favorite Web Browser 2. Go to https://outlook.com/frostburg.edu a. Or from the FSU Home Page, Hover on Login (Upper Right) and Click E-mail, then Click the Email Login 3. Login to your e-mail with your FSU credentials 4. Click the icon that looks like a grid in the upper left corner Click Here 5. Click on OneDrive Click OneDrive 6. You will now be in your online Cloud Storage (OneDrive) 3 ways to Save a File to OneDrive: First Way - Create a new file using OneDrive 1. Login to OneDrive if you are not already 2. Click the New Button Click New 3. Choose Word document, Excel workbook, PowerPoint presentation, etc. 4. It will open using the online version of Word, Excel, etc. 5. Type your information. 6. Click File - Save As… (Top Left) a. ***NOTE – If you use Word, Excel, etc. online with OneDrive, it automatically saves your work as you go. That is the reason there is no Save button, only a Rename button. 7. Click Rename this file (default is document1, but give it a name you will remember later) 8. -

Microsoft Onedrive What Is Microsoft Onedrive?
Microsoft OneDrive What is Microsoft OneDrive? Microsoft OneDrive is a free online cloud based storage service that comes free with your FPU Microsoft Office365 account. With a storage limit of 1TB you can save thousands of documents and Files without worry. Gone are the days of losing completed papers and projects because of a computer crashing or a lost flash drive. Once your documents are saved within OneDrive you will be able to access them from any PC, tablet, or mobile device! How do I access Microsoft OneDrive? To access your OneDrive account you will need to sign into your Student Office365 account by going to Https://Mail.Office365.com and signing in with your entire FPU email address and password. Once logged in click on this symbol in the top left corner Now select the OneDrive tab and you are in! What are some advantages of OneDrive? Security - Anytime you’re relying on email to share information it is always a risk that you’ll attach the wrong document or email the wrong person. One of the main benefits of using services like Microsoft OneDrive is that you add another layer of security. When using Microsoft OneDrive your files aren’t shared with other people unless you save them to the Public folder or choose to share them. Microsoft also saves multiple copies of each file on different drives and servers to prevent document loss from hardware failure Collaboration - By creating a document and sharing it amongst fellow students in OneDrive you can rest assured that everyone will be working on the same page and that any changes to the file will be made at the same time. -

How to Use Microsoft Onedrive Instructions for Saint Paul College Students
How to use Microsoft OneDrive Instructions for Saint Paul College Students Table of Content What is OneDrive? ....................................................................................... 2 How do I access OneDrive? ......................................................................... 2 How do I upload documents to OneDrive? ................................................... 3 How do I create new documents directly within OneDrive? ......................... 4 How do I upload files from my OneDrive into D2L Brightspace? .................. 5 How do I save files to OneDrive using a locally-installed version of Microsoft Office on my computer? ............................................................... 7 How do I share my OneDrive files with others? ......................................... 10 How do I attach files from OneDrive to an email message? ....................... 12 How to use Microsoft OneDrive rev. October 2020 Page 1 of 16 What is OneDrive? OneDrive is your personal file storage in the “cloud” (part of Office 365). It allows you to store files and access them from virtually any device with internet access. How do I access OneDrive? Access OneDrive by logging into your Saint Paul College email account. From the Saint Paul College website (https://www.saintpaul.edu), click the Student Email Login using the “Student Login” drop down arrow located on the top menu. 1. Type your [email protected] and click Next. 2. Type your StarID password, then click Sign in. 3. Optional: Check “Don’t show this again and click Yes. 4. Once you are logged in the Office 365 App Launcher will be launched. Click on OneDrive. How to use Microsoft OneDrive rev. October 2020 Page 2 of 16 How do I upload documents to OneDrive? 1. Once you have accessed your OneDrive, click on Upload on the “Documents” page. -

Important Notice for City Staff Regarding the Use of Microsoft Onedrive, Skype, Or Office 365
Important Notice for City Staff regarding the use of Microsoft OneDrive, Skype, or Office 365. The City is in the process of migrating to Office 365 and Exchange Online. This migration will affect you if you have subscribed to any of Microsoft’s online services using your City of Tulsa email account ([email protected] or [email protected]). These services include: Office 365 (Personal or Enterprise) Skype OneDrive OneNote To ensure that you do not lose access to the data currently saved in these services, you need to immediately (no later than December 8, 2017) change the registered email with these services to your personal email. Important Note: If you use Microsoft One Note, you are typically also using OneDrive to store your notebooks. You will need to change the registered email with this account as well. We apologize for any inconvenience that this may cause. Please see the instructions below for changing the registered email for some of the more popular Microsoft Services: Instructions for changing default email addresses Skype: 1. Sign in to your account. 2. Click your profile picture, or select Edit Profile in the Account details section at the bottom of the page. In Skype for Business 2016, this is located in the upper portion of the login screen and accessed by clicking the 3. Select “Personal” from the left menu and the change the Sign‐In address. Click “OK” at the bottom of the page. OneDrive and OneNote: 1. Browse to www.Microsoft.com 2. Click on your profile in the upper right corner ‐ or if you are not logged in, log into the account the OneDrive is tied to 3. -

Windows 10-New Features & Apps
Windows 10-New Features & Apps By Tom Krauser This article discusses some of the new features and apps that come packaged in Windows 10. It is only a brief summary of these features. For more information you can search the internet or check YouTube for instructional videos on your topic of interest. The following links provide some good basic information on Windows 10 and should be helpful to you. https://support.microsoft.com/en-us/products/windows?os=windows-10 https://support.microsoft.com/en-us/help/4043948/windows-10-whats-new-in-fall-creators-update-1709 The following article from PC World Magazine provides articles on a lot of new features in Windows 10. https://www.pcworld.com/tag/windows10/ The following article by CNET discusses some of new features in the latest update to Windows 10. https://www.cnet.com/how-to/windows-10-tips-best-features/ Alarms & Clocks: A combination of alarm clock, world clock, timer, and stopwatch. Set alarms and reminders, check times around the world, and time your activities, including laps and splits. The following link discusses how to set timers, alarms, and stopwatches: https://www.howtogeek.com/225211/how-to-set-timers-alarms-and-stopwatches-in-windows-10/ Camera: Many modern devices with Windows include a webcam and, to use it, you need an app that helps you take pictures, record videos or stream video while video chatting. For this purpose, Microsoft has built an app called Camera, which is available by default in Windows 10. Connect: Use Connect App to Cast Your Smartphone Screen to Your PC. -

Store and Share Files Inside and Outside Your Organization to Work Securely Across Organizational Boundaries
Store and share files inside and outside your organization to work securely across organizational boundaries Cumbersome restrictions and limitations on mobile devices, apps, and remote access can be taxing from an IT perspective and frustrating for your employees. Users need to be able to create, access, and share files from anywhere, but you also need to ensure that these actions are safe and secure. Microsoft 365 offers security solutions that can help secure your collaboration and productivity apps, including third-party apps, so that your employees can connect and communicate wherever they are, using the tools they are familiar with, as securely as if they were right at their desks. How can I securely share documents outside my organization? Microsoft Azure Information Protection Azure Information Protection provides classification, labeling, and protection so you can track and control how information is used. Data can be classified as public or confidential according to standards you define for content, context, and source. These classifications can be applied automatically or manually, or you can suggest classifications so that your employees can decide what to apply. Azure Information Protection is integrated with other Microsoft cloud services, such as Microsoft Office 365 and Azure AD. It can be used with your in-house line-of-business applications and information protection solutions from software vendors, whether these applications and solutions are on-premises or in the cloud. To classify documents using Azure Information Protection, you must first configure your company’s classification policy. Configure the policy by signing in to the Azure portal as an administrator, selecting Azure Information Protection in the apps list. -

Microsoft Onedrive Training
Microsoft OneDrive Training Introduction to OneDrive • Secure, cloud storage service • Virtual access from any device with internet access • Enables file sharing and collaboration • Document scanning on mobile devices Access OneDrive from Your Browser • Login.microsoftonline.com o Navigating the O365 dashboard § App launcher § Install Office (Employee Benefit: can install up to 5 copies of Microsoft Office on personal computers per license agreement with Microsoft) § Profile picture (account) § Settings § Search • Overview of the Office 365 dashboard o Tiles o Recommended o Recent | Pinned | Shared with me | Discover | Upload and open | View options o OneDrive Recent Folders | Sharepoint Frequent Sites and Following • About SharePoint Navigating OneDrive’s Interface • Navigation panel o My files | Recent | Shared | Discover | Recycle bin o Shared libraries o Get the OneDrive Apps | Return to Classic OneDrive § Differences between modern and classic: https://support.microsoft.com/en- us/office/differences-between-modern-and-classic-experiences-for-lists-and- libraries-30e1aab0-a5cc-4363-b7f2-09e2ae07d4dc o Files o Top navigation bar: New | Upload | Sync | Automate o Right navigation: Sort | View | Activity information Accessing OneDrive from Desktop • How to display user files 1. Right click on desktop 2. Personalize 3. Themes 4. Desktop icon settings R Computer Patti Heisler 1 | Page R Users files R Recycle bin • Access Users Files from desktop, click OneDrive o Notes: OneDrive within Users Files are local copies. Changes can be made to these files without internet access. When internet access is available, those copies sync with OneDrive online. o See OneDrive icon in system tray. You can check in sync status and more. • Folder and file information: o Share | More Options | Modification date | Modified by | File size | Sharing o More Options - folders: Share Manage access (…) = panel Designate permissions, add email, message. -

Students, Faculty and Staff Guide for Windows 10
Students, Faculty and Staff Guide for Windows 10 Prepared by Information Technology Division Lehman College, CUNY Revised - January 31, 2020 This document was originally prepared by Microsoft. It was modified and adapted for use at Lehman College. Information Technology Division Lehman College, CUNY Guide contents The purpose of this guide is to introduce you to the key features in Windows 10, and give you tips and tricks on how to get started using those features. You’ll find information on the following topics: A few feature highlights Cortana Using Microsoft Office Personalization • Start menu • What can Cortana do? 365 with Windows 10 and Settings • Access your email • A new look • How to search • Cortana’s Notebook • Use Office 365 on • Personalize your lock • Using tiles Microsoft Edge mobile devices screen • Task view • Hub • Use Office 365 with • Get started with themes • Virtual desktops OneDrive for Business to • Web Notes • Change your desktop work with files anywhere • Windows behavior in • Reading List background and color modern applications • Sign in to Office 365 Apps and the • Charms functionality in Setting things up • Create a file action center modern applications • Set up your email and • Share a file calendar • Snap enhancements • Synchronize a file • Change your • Quick access tools account picture • Protect your PC Information Technology Division Lehman College, CUNY A few feature highlights in Windows 10 Windows 10 is designed to please both touch and mouse users. It’s also designed to be intuitive for users of both Windows 7 and Windows 8.1, incorporating the “best of both worlds” to enhance your experience and help you be more productive. -
![Windows 10 Forensics]](https://docslib.b-cdn.net/cover/7817/windows-10-forensics-887817.webp)
Windows 10 Forensics]
[Windows 10 Forensics] 175 Lakeside Ave, Room 300A Phone: (802)865-5744 Fax: (802)865-6446 02/02/2016 http://www.lcdi.champlain.edu Disclaimer: This document contains information based on research that has been gathered by employee(s) of The Senator Patrick Leahy Center for Digital Investigation (LCDI). The data contained in this project is submitted voluntarily and is unaudited. Every effort has been made by LCDI to assure the accuracy and reliability of the data contained in this report. However, LCDI nor any of our employees make no representation, warranty or guarantee in connection with this report and hereby expressly disclaims any liability or responsibility for loss or damage resulting from use of this data. Information in this report can be downloaded and redistributed by any person or persons. Any redistribution must maintain the LCDI logo and any references from this report must be properly annotated. Contents Introduction ............................................................................................................................................................................ 3 Background: ........................................................................................................................................................................ 3 Purpose and Scope: ............................................................................................................................................................. 3 Research Questions: ........................................................................................................................................................... -

OEM Windows Co-Brand Guide
OEM Windows Co-Brand Guide March, 2016 Microsoft Confidential Welcome to the OEM Windows Co-Brand Guide! This guide contains important Windows 10 and Office brand elements and guidelines to help tell our brand story together. Our logo is a window—and an iconic symbol known the world over. This symbol has an active feeling to it, representing a person’s unique perspective on their world. When communicating general Windows brand information, use the Windows logo with no The Windows logo includes the Windows symbol and logotype, which version attached. must be used together in a horizontal lockup. The symbol must not be used by itself, and OEMs must not put a box, circle, or other confining When the conversation is shape around the Windows logo. specific to Windows 10 or Trademark symbols highlighting Windows 10 specific features, always use the Logos provided without trademark symbols (TM and ®) should Windows 10 logo lockup. be used in marketing materials only. Trademark symbols are still required in certain places in and on product, and on Minimum size product packaging. More trademark information http://www.microsoft.com/en- us/legal/intellectualproperty/Trademarks/EN-US.aspx Clear space Clear space We respect the logo by giving it some space. The preferred clear space is equivalent to the height of the symbol. Minimum size In print, the logo should never appear smaller than 1” (25 mm). On-screen, it must appear at least 70 pixels wide. Download the Windows logo here: https://omap.microsoft.com/ The Logo Artwork Is Available in Three sizes Windows Logo Color Select the appropriate asset by determining the height Contrast is important — use a white logo on color backgrounds and required for your layout.