Volume Ii of Ii Record of Teksavvy Solutions Inc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Teksavvy Solutions Inc. Consultation on the Technical and Policy
TekSavvy Solutions Inc. Reply Comments in Consultation on the Technical and Policy Framework for the 3650-4200 MHz Band and Changes to the Frequency Allocation of the 3500-3650 MHz Band Canada Gazette, Part I, August 2020, Notice No. SLPB-002-20 November 30, 2020 TekSavvy Solutions Inc. Reply Comments to Consultation SLPB-002-20 TABLE OF CONTENTS A. Introduction ____________________________________________________________ 1 B. Arguments for option 1 and against option 2 _________________________________ 1 a. Contiguity ______________________________________________________________ 1 b. Availability of ecosystem in the 3900: impacts on viability_________________________ 3 c. Moratorium ____________________________________________________________ 4 d. Arguments for Improvements to Option 1 _____________________________________ 4 C. 3800 MHz Auction _______________________________________________________ 5 a. Value _________________________________________________________________ 5 b. Procompetitive Measures _________________________________________________ 5 c. Tier 4 and 5 Licensing Area ________________________________________________ 6 TekSavvy Solutions Inc. Page 1 of 6 Reply Comments to Consultation SLPB-002-20 A. INTRODUCTION 1. TekSavvy Solutions Inc. (“TekSavvy”) is submitting its reply comments on ISED’s “Consultation on the Technical and Policy Framework for the 3650-4200 MHz Band and Changes to the Frequency Allocation of the 3500-3650 MHz Band”. 2. TekSavvy reasserts its position in favour of Option 1 in that Consultation document, and its strong opposition to Option 2, as expressed in its original submission. TekSavvy rejects Option 2 as disastrous both for WBS service providers’ ongoing viability and availability of broadband service to rural subscribers. 3. TekSavvy supports Option 1, wherein WBS Licensees would be allowed to continue to operate in the band of 3650 to 3700 MHz indefinitely as the only option that enables continued investment in rural broadband networks and continued improvement of broadband services to rural subscribers. -

Broadcasting Decision CRTC 2016-196
Broadcasting Decision CRTC 2016-196 PDF version Reference: 2016-147 Ottawa, 24 May 2016 Various licensees Various locations across Canada Various terrestrial broadcasting distribution undertakings – Administrative renewals 1. The Commission renews the broadcasting licences for the terrestrial broadcasting distribution undertakings set out in the appendix to this decision from 1 September 2016 to 30 November 2016, subject to the terms and conditions in effect under the current licences. 2. This decision does not dispose of any issue that may arise with respect to the renewal of these licences, including past non-compliance issues. The Commission is considering the renewal of these licences in Call for licence renewal applications: Submission of renewal applications for broadcasting licences of terrestrial distribution undertakings (BDUs) that will expire in 2016 and 2017; implementation of certain conditions of licence and review of practices in regard to the small basic and flexible packaging requirements for all BDU licensees, Broadcasting Notice of Consultation CRTC 2016-147, 21 April 2016. Secretary General *This decision is to be appended to each licence. Appendix to Broadcasting Decision CRTC 2016-196 Terrestrial broadcasting distribution undertakings for which the broadcasting licences have been administratively renewed until 30 November 2016 Licensee Locations Access Communications Co-operative Limited Regina (including White City), Saskatchewan Cogeco Cable Canada GP Inc. (the general Belleville, Burlington, Georgetown, partner) -

January 11, 2019 the Broadcasting and Telecommunications Legislative Review Panel C/O Innovation, Science and Economic Devel
January 11, 2019 The Broadcasting and Telecommunications Legislative Review Panel c/o Innovation, Science and Economic Development Canada 235 Queen Street, 1st Floor Ottawa, Ontario K1A 0H5 VMedia Inc. (“VMedia”) is grateful for the opportunity to submit comments on the broadcasting and telecommunications legislative review (the “Review”) initiated by Innovation, Science and Economic Development (“ISED”) Canada. Executive Summary The Review ES1.The issues outlined in the terms of reference and the themes described by the panel appointed by ISED to review the relevant legislation (the “Panel”) are extensive. There are seven terms of reference relating to issues to consider in connection with the Telecommunications and Radiocommunication Acts, and eight in connection with the Broadcasting Act. In addition, there are four themes set out by the Panel intended to “help guide its work and structure meaningful dialogue during its consultation process”. ES2.Among those 19 elements of consideration, we note that the word competition is mentioned only twice, with little elaboration or context. ES3.As the second point under both the Telecommunications and Radiocommunication Acts, under the heading “Competition, Innovation, and Affordability”, the question is asked, “Are legislative changes warranted to better promote competition, innovation and affordability?” ES4.In addition, competition is mentioned at the very end of the first of the Panel’s themes, “Reducing Barriers to Access by All Canadian to Advanced Telecommunications Networks”. All of the rest of that theme focuses on the achievements of telephone and cable companies, and the heavy lifting ahead of them as they keep up with digital transformation. ES5.There is no mention at all of competition in the terms of reference relating to the Broadcasting Act. -
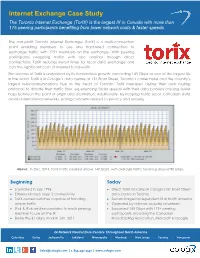
Cologix Torix Case Study
Internet Exchange Case Study The Toronto Internet Exchange (TorIX) is the largest IX in Canada with more than 175 peering participants benefiting from lower network costs & faster speeds The non-profit Toronto Internet Exchange (TorIX) is a multi-connection point enabling members to use one hardwired connection to exchange traffic with 175+ members on the exchange. With peering participants swapping traffic with one another through direct connections, TorIX reduces transit times for local data exchange and cuts the significant costs of Internet bandwidth. The success of TorIX is underlined by its tremendous growth, exceeding 145 Gbps as one of the largest IXs in the world. TorIX is in Cologix’s data centre at 151 Front Street, Toronto’s carrier hotel and the country’s largest telecommunications hub in the heart of Toronto. TorIX members define their own routing protocols to dictate their traffic flow, experiencing faster speeds with their data packets crossing fewer hops between the point of origin and destination. Additionally, by keeping traffic local, Canadian data avoids international networks, easing concerns related to privacy and security. Above: In Dec. 2014, TorIX traffic peaked above 140 Gbps, with average traffic hovering around 90 Gbps. Beginning Today Launched in July 1996 Direct TorIX on-ramp in Cologix’s151 Front Street Ethernet-based, layer 2 connectivity data centre in Toronto TorIX-owned switches capable of handling Second largest independent IX in North America ample traffic Operated by telecom industry volunteers IPv4 & IPv6 address provided to each peering Surpassed 145 Gbps with 175+ peering member to use on the IX participants, including the Canadian Broke the 61 Gbps mark in Jan. -

TX-NR636 AV RECEIVER Advanced Manual
TX-NR636 AV RECEIVER Advanced Manual CONTENTS AM/FM Radio Receiving Function 2 Using Remote Controller for Playing Music Files 15 TV operation 42 Tuning into a Radio Station 2 About the Remote Controller 15 Blu-ray Disc player/DVD player/DVD recorder Presetting an AM/FM Radio Station 2 Remote Controller Buttons 15 operation 42 Using RDS (European, Australian and Asian models) 3 Icons Displayed during Playback 15 VCR/PVR operation 43 Playing Content from a USB Storage Device 4 Using the Listening Modes 16 Satellite receiver / Cable receiver operation 43 CD player operation 44 Listening to Internet Radio 5 Selecting Listening Mode 16 Cassette tape deck operation 44 About Internet Radio 5 Contents of Listening Modes 17 To operate CEC-compatible components 44 TuneIn 5 Checking the Input Format 19 Pandora®–Getting Started (U.S., Australia and Advanced Settings 20 Advanced Speaker Connection 45 New Zealand only) 6 How to Set 20 Bi-Amping 45 SiriusXM Internet Radio (North American only) 7 1.Input/Output Assign 21 Connecting and Operating Onkyo RI Components 46 Slacker Personal Radio (North American only) 8 2.Speaker Setup 24 About RI Function 46 Registering Other Internet Radios 9 3.Audio Adjust 27 RI Connection and Setting 46 DLNA Music Streaming 11 4.Source Setup 29 iPod/iPhone Operation 47 About DLNA 11 5.Listening Mode Preset 32 Firmware Update 48 Configuring the Windows Media Player 11 6.Miscellaneous 33 About Firmware Update 48 DLNA Playback 11 7.Hardware Setup 33 Updating the Firmware via Network 48 Controlling Remote Playback from a PC 12 8.Remote Controller Setup 39 Updating the Firmware via USB 49 9.Lock Setup 39 Music Streaming from a Shared Folder 13 Troubleshooting 51 Operating Other Components Using Remote About Shared Folder 13 Reference Information 58 Setting PC 13 Controller 40 Playing from a Shared Folder 13 Functions of REMOTE MODE Buttons 40 Programming Remote Control Codes 40 En AM/FM Radio Receiving Function Tuning into stations manually 2. -

QUESTION 20-1/2 Examination of Access Technologies for Broadband Communications
International Telecommunication Union QUESTION 20-1/2 Examination of access technologies for broadband communications ITU-D STUDY GROUP 2 3rd STUDY PERIOD (2002-2006) Report on broadband access technologies eport on broadband access technologies QUESTION 20-1/2 R International Telecommunication Union ITU-D THE STUDY GROUPS OF ITU-D The ITU-D Study Groups were set up in accordance with Resolutions 2 of the World Tele- communication Development Conference (WTDC) held in Buenos Aires, Argentina, in 1994. For the period 2002-2006, Study Group 1 is entrusted with the study of seven Questions in the field of telecommunication development strategies and policies. Study Group 2 is entrusted with the study of eleven Questions in the field of development and management of telecommunication services and networks. For this period, in order to respond as quickly as possible to the concerns of developing countries, instead of being approved during the WTDC, the output of each Question is published as and when it is ready. For further information: Please contact Ms Alessandra PILERI Telecommunication Development Bureau (BDT) ITU Place des Nations CH-1211 GENEVA 20 Switzerland Telephone: +41 22 730 6698 Fax: +41 22 730 5484 E-mail: [email protected] Free download: www.itu.int/ITU-D/study_groups/index.html Electronic Bookshop of ITU: www.itu.int/publications © ITU 2006 All rights reserved. No part of this publication may be reproduced, by any means whatsoever, without the prior written permission of ITU. International Telecommunication Union QUESTION 20-1/2 Examination of access technologies for broadband communications ITU-D STUDY GROUP 2 3rd STUDY PERIOD (2002-2006) Report on broadband access technologies DISCLAIMER This report has been prepared by many volunteers from different Administrations and companies. -

BCE Inc. 2015 Annual Report
Leading the way in communications BCE INC. 2015 ANNUAL REPORT for 135 years BELL LEADERSHIP AND INNOVATION PAST, PRESENT AND FUTURE OUR GOAL For Bell to be recognized by customers as Canada’s leading communications company OUR STRATEGIC IMPERATIVES Invest in broadband networks and services 11 Accelerate wireless 12 Leverage wireline momentum 14 Expand media leadership 16 Improve customer service 18 Achieve a competitive cost structure 20 Bell is leading Canada’s broadband communications revolution, investing more than any other communications company in the fibre networks that carry advanced services, in the products and content that make the most of the power of those networks, and in the customer service that makes all of it accessible. Through the rigorous execution of our 6 Strategic Imperatives, we gained further ground in the marketplace and delivered financial results that enable us to continue to invest in growth services that now account for 81% of revenue. Financial and operational highlights 4 Letters to shareholders 6 Strategic imperatives 11 Community investment 22 Bell archives 24 Management’s discussion and analysis (MD&A) 28 Reports on internal control 112 Consolidated financial statements 116 Notes to consolidated financial statements 120 2 We have re-energized one of Canada’s most respected brands, transforming Bell into a competitive force in every communications segment. Achieving all our financial targets for 2015, we strengthened our financial position and continued to create value for shareholders. DELIVERING INCREASED -

Media and Internet Concentration in Canada, 1984-2018
MEDIA AND INTERNET CONCENTRATION IN CANADA, 1984-2018 REPORT DECEMBER 2019 Canadian Media Concentration Research Project Research Canadian Media Concentration www.cmcrp.org Candian Media Concentration Research Project x The Canadian Media Concentration Research project is directed by Professor Dwayne Winseck, School of Journalism and Communication, Carleton University. The project was funded by the Social Sciences and Humanities Research Council between 2012 and 2018, after which the Faculty of Public Affairs at Carleton University generously stepped in to provide bridge funding for the next two years of the project. The overall objective of the CMCR Project is to develop a comprehensive, systematic and long-term analysis of the telecoms, internet and media industries in Canada to better inform public and policy-related discussions about these issues. Professor Winseck can be reached at either [email protected] or 613 769- 7587 (mobile). Open Access to CMCR Project Data CMCR Project data can be freely downloaded and used under Creative Commons licensing arrangements for non-commercial purposes with proper attribution and in accordance with the ShareAlike principles set out in the International License 4.0. Explicit, written permission is required for any other use that does not follow these principles. Our data sets are available for download here and also available in our long term data archive hosted on the CMCRP Dataverse. Dataverse is a publicly-accessible repository of scholarly works created and maintained by a consortium of Canadian universities. All works and datasets deposited in our CMCRP Dataverse are given a permanent DOI, so as to not be lost when a website becomes no longer available—a form of “dead media”. -

Air Carrier Traffic at Canadian Airports
Catalogue no. 51-203-X Air Carrier Traffic at Canadian Airports 2009 How to obtain more information For information about this product or the wide range of services and data available from Statistics Canada, visit our website at www.statcan.gc.ca,[email protected], or telephone us, Monday to Friday from 8:30 a.m. to 4:30 p.m., at the following numbers: Statistics Canada’s National Contact Centre Toll-free telephone (Canada and the United States): Inquiries line 1-800-263-1136 National telecommunications device for the hearing impaired 1-800-363-7629 Fax line 1-877-287-4369 Local or international calls: Inquiries line 1-613-951-8116 Fax line 1-613-951-0581 Depository Services Program Inquiries line 1-800-635-7943 Fax line 1-800-565-7757 To access this product This product, Catalogue no. 51-203-X, is available free in electronic format. To obtain a single issue, visit our website at www.statcan.gc.ca and browse by “Key resource” > “Publications.” Standards of service to the public Statistics Canada is committed to serving its clients in a prompt, reliable and courteous manner. To this end, Statistics Canada has developed standards of service that its employees observe. To obtain a copy of these service standards, please contact Statistics Canada toll-free at 1-800-263-1136. The service standards are also published on www.statcan.gc.ca under “About us” > “Providing services to Canadians.” Statistics Canada Transportation Division Air Carrier Traffic at Canadian Airports 2009 Published by authority of the Minister responsible for Statistics Canada © Minister of Industry, 2010 All rights reserved. -

Application for Forbearance from the Regulation of Residential Local Exchange Services
Telecom Decision CRTC 2018-109 PDF version Ottawa, 29 March 2018 Public record: 8640-S22-201711648 Saskatchewan Telecommunications – Application for forbearance from the regulation of residential local exchange services The Commission approves SaskTel’s request for forbearance from the regulation of residential local exchange services in the exchange of North Battleford, Saskatchewan. Application 1. The Commission received an application from Saskatchewan Telecommunications (SaskTel), dated 15 December 2017, in which the company requested forbearance from the regulation of residential local exchange services1 in the exchange of North Battleford, Saskatchewan. 2. The Commission received a submission regarding SaskTel’s application from Rogers Communications Canada Inc. (RCCI). Commission’s analysis and determinations 3. Pursuant to the Commission’s requirements in Telecom Decision 2006-15, SaskTel provided evidence to support its forbearance request, including competitor quality of service (Q of S) results for the six months preceding its application, and a draft communications plan for the Commission’s approval. The Commission has assessed SaskTel’s application based on the local forbearance test set out in Telecom Decision 2006-15 by examining the four criteria set out below. Product market 4. The Commission received no comments with respect to SaskTel’s proposed list of residential local exchange services. 5. SaskTel is seeking forbearance from the regulation of 11 tariffed residential local exchange services. The Commission notes that 10 of these services were included in the list of services set out in Telecom Decision 2005-35-1. The other service, Feature 1 In this decision, “residential local exchange services” refers to local exchange services used by residential customers to access the public switched telephone network and any associated service charges, features, and ancillary services. -

The Relationship Between Local Content, Internet Development and Access Prices
THE RELATIONSHIP BETWEEN LOCAL CONTENT, INTERNET DEVELOPMENT AND ACCESS PRICES This research is the result of collaboration in 2011 between the Internet Society (ISOC), the Organisation for Economic Co-operation and Development (OECD) and the United Nations Educational, Scientific and Cultural Organization (UNESCO). The first findings of the research were presented at the sixth annual meeting of the Internet Governance Forum (IGF) that was held in Nairobi, Kenya on 27-30 September 2011. The views expressed in this presentation are those of the authors and do not necessarily reflect the opinions of ISOC, the OECD or UNESCO, or their respective membership. FOREWORD This report was prepared by a team from the OECD's Information Economy Unit of the Information, Communications and Consumer Policy Division within the Directorate for Science, Technology and Industry. The contributing authors were Chris Bruegge, Kayoko Ido, Taylor Reynolds, Cristina Serra- Vallejo, Piotr Stryszowski and Rudolf Van Der Berg. The case studies were drafted by Laura Recuero Virto of the OECD Development Centre with editing by Elizabeth Nash and Vanda Legrandgerard. The work benefitted from significant guidance and constructive comments from ISOC and UNESCO. The authors would particularly like to thank Dawit Bekele, Constance Bommelaer, Bill Graham and Michuki Mwangi from ISOC and Jānis Kārkliņš, Boyan Radoykov and Irmgarda Kasinskaite-Buddeberg from UNESCO for their work and guidance on the project. The report relies heavily on data for many of its conclusions and the authors would like to thank Alex Kozak, Betsy Masiello and Derek Slater from Google, Geoff Huston from APNIC, Telegeography (Primetrica, Inc) and Karine Perset from the OECD for data that was used in the report. -

Telecom Decision CRTC 2007-59
Telecom Decision CRTC 2007-59 Ottawa, 25 July 2007 Bell Aliant – Applications for forbearance from the regulation of residential local exchange services Reference: 8640-B54-200706096, 8640-B54-200706111, 8640-B54-200706129, 8640-B54-200706153, 8640-B54-200706632 (New Brunswick); 8640-B54-200705551, 8640-B54-200705809, 8640-B54-200705824, 8640-B54-200705874, 8640-B54-200705890, 8640-B54-200705957, 8640-B54-200705981, 8640-B54-200705999, 8640-B54-200706020, 8640-B54-200706038, 8640-B54-200706731 (Nova Scotia); 8640-B54-200706046, 8640-B54-200706054, 8640-B54-200706062, 8640-B54-200706070, 8640-B54-200706723 (Prince Edward Island); and 8640-C12-200706351 (general) In this Decision, the Commission approves Bell Aliant Regional Communications, Limited Partnership's (Bell Aliant) request for forbearance from the regulation of residential local exchange services in 72 exchanges in New Brunswick, Nova Scotia, and Prince Edward Island. The Commission denies Bell Aliant's request for forbearance in 8 exchanges. Introduction 1. The Commission received applications by Bell Aliant Regional Communications, Limited Partnership (Bell Aliant), dated between 11 and 30 April 2007, in which the company requested forbearance from the regulation of residential local exchange services1 in 80 exchanges in New Brunswick, Nova Scotia – including exchanges in the priority census metropolitan area (CMA) of Halifax2 – and Prince Edward Island. 2. In a letter dated 7 May 2007, the Commission directed incumbent local exchange carriers (ILECs), competitive local exchange