Connecting Devices Wirelessly with Bluetooth Wireless Technology
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Palm Security WP.Qxd
Palm® Mobility Series: Security Smartphone and handheld security for mobile business. Mobile computing: Opportunities and risk By providing professionals with convenient mobile access to email, business applications, customer information and critical corporate data, businesses can become more productive, streamline business processes and enable better decision making. With the new ease of access to information comes a responsibility to protect the organization's data as well as the investment in mobile devices. In many ways, security risks for mobile computing are similar to those for other computing platforms. There are the usual concerns of protecting data, authenticating users, and shielding against viruses and other malicious Contents code. But because of their mobility and compact size, smartphones and handhelds present some additional challenges: Mobile computing: Opportunities and risk...................................................... 1 Know thy enemy: Security risks...................................................................... 2 • Smartphones and handhelds are more easily lost or stolen than Theft and loss ............................................................................................ 2 laptop or desktop computers. Password cracking .................................................................................... 2 Data interception ...................................................................................... 2 • Users often treat smartphones and handhelds as personal devices Malicious code -

C.V. Ice, Mcgowan Water Bring Their Drivers Into the 21St Century with Tungsten Handhelds
Field Force Automation: C. V. Ice and McGowan Water C.V. Ice, McGowan Water Bring Their Drivers Into the 21st Century With Tungsten Handhelds Challenge C.V. Ice Company and McGowan Water Conditioning may run their operations in very different climates-C.V. Ice delivers ice to retail stores throughout southern California and parts of Arizona, while McGowan serves residential water needs in Minnesota-but both companies shared a common problem: a reliance on an antiquated, paper-based system for handling their drivers’ delivery routes. McGowan was also using that method to handle its service technicians’ calls. Both companies estimate that several hours were spent every day generating invoices, setting up routes for drivers, and fielding calls from customers who needed deliveries or other services, or who simply had “Efficiency levels went questions about their bills. Drivers for both companies had little account through the roof once information to give customers when making deliveries, and McGowan’s our drivers became service technicians had to call the office every time they wanted to check comfortable with the the status of a particular part. In addition, reliance on paper increased the technology. “ likelihood of costly errors. Kevin Mason C.V. Ice, Inc. As a result, both firms had customers who felt like they had to constantly Technical Highlights worry about the status of their deliveries, for fear they wouldn’t get what they needed, when they needed it. On top of that, the companies had n Palm® Tungsten™ handhelds difficulty expanding their businesses because of the amount of overhead n Prism Visual Software’s MiniMate each customer required. -

PEPIDTM WIRELESS Mobile Technology
for use in any wireless environment PEPID™ WIRELESS Mobile can be used in any environment that supports wireless communications. No downloading and installation on a PDA is required. No updating required as the wireless environment is serviced from our host server. Easy access and simple implementation are driving factors behind using wireless. Benefits include: • True mobility without physical cable to the network; • Increased productivity – continuous, 24x7 access to information; • Wider network access – provides network access where it was previously difficult to deploy traditional wired LANs (e.g. manufacturing, warehousing, temporary office space, leased buildings, etc.); • Broad OS support – Windows, Macintosh, Palm OS, etc.; • No installation and rapid deployment ; • Lower long-term costs and immediate increased productivity. With PEPID WIRELESS Mobile, critical data is just one URL away. PEPIDTM WIRELESS Mobile Technology PEPID uses the following tools to implement our wireless services: • ASP.Net Mobile Web Application • Microsoft Mobile Internet Toolkit: ◦.NET Framework. The .NET Framework is a component of the Microsoft Windows® operating system used to build and run Windows-based applications. ◦ Web Forms ◦ Web Services ◦ Win Forms ◦ ADO.Net ◦ Common Language Runtime Palm OS Windows Mobile PEPID™ Online ASP.Net-based Palm Treo 650 Palm Treo 700 Mobile Web application can be Palm T│X Dell Axim x51v displayed on a wide range of the Palm LifeDrive Mobile Manager HP iPAQ h6315, hw6515 mobile wireless devices. Palm Tungsten C, E2, T3, T5 Samsung SCH-i730 Compatible devices include: Zire 72 Siemens SX66 i-mate PDA2k WIRELESS Mobile Implementation • The PEPID Web server and PEPID mobile Web application are deployed on the Internet. -

Introducint Your Palm Treo 750V Smartphone Quick Reference Guide
Final Draft Palm, Inc. Confidential Introducing Your Palm® Treo™ 750v Smartphone Final Draft Palm, Inc. Confidential Intellectual property notices © 2006 Palm, Inc. All rights reserved. Trademark, copyright, patent, and other intellectual property notices are set forth on page ii within the User Guide, entitled Yo u r Pa l m ® Treo™ 750v Smartphone, installed on the user’s computer. The Treo trademark is used by Palm, Inc. in Sweden and Denmark with the express consent of Pfizer and its affiliated companies. The products marketed and/or sold by Palm, Inc. under the Treo trademark are in no way affiliated with Pfizer or its business. Disclaimer and limitation of liability Palm, Inc. and its suppliers assume no responsibility for any damage or loss resulting from the use of this guide. Palm, Inc. and its suppliers assume no responsibility for any loss or claims by third parties that may arise through the use of this software. Palm, Inc. and its suppliers assume no responsibility for any damage or loss caused by deletion of data as a result of malfunction, dead battery, or repairs. Be sure to make backup copies of all important data on other media to protect against data loss. PN: 406-10703-00 v 0.0 Final Draft Palm, Inc. Confidential Contents Chapter 1: Moving around on your smartphone . 1 What’s in the box? . 3 Palm Treo 750v smartphone overview . 4 Maximizing battery life . 6 Navigating around the screen . 7 Using the keyboard . 14 Opening and closing applications . 16 Using your Today screen. 17 Chapter 2: Your phone . 19 Turning your smartphone on/off . -

Palm Treo 700Wx Smartphone User Guide
User Guide Intellectual property notices Palm Take Back and Recycling Program © 2007-2008 Palm, Inc. All rights reserved. Trademark, copyright, This symbol indicates that Palm products patent, and other intellectual property notices are set forth on page ii should be recycled and not be disposed of in within Quick Reference, which can be found in your smartphone unsorted municipal waste. Palm products package. should be sent to a facility that properly recycles electrical and electronic equipment. Disclaimer and limitation of liability For information on environmental programs visit: palm com/environment Palm, Inc. and its suppliers assume no responsibility for any damage or loss resulting from the use of this guide. Palm, Inc. and its As part of Palm’s corporate commitment to be a good steward of the suppliers assume no responsibility for any loss or claims by third environment, we strive to use environmentally friendly materials, parties that may arise through the use of this software. Palm, Inc. and reduce waste, and develop the highest standards in electronics its suppliers assume no responsibility for any damage or loss caused recycling. Our recycling program keeps Palm handheld devices, by deletion of data as a result of malfunction, dead battery, or repairs. smartphones, and mobile companions out of landfills through Be sure to make backup copies of all important data on other media evaluation and disposition for reuse and recycling. to protect against data loss. Palm customers may participate in the recycling program free of charge. Visit palm.com/recycle or in the US call 877-869-7256 for additional details and information about how you can help reduce electronic waste. -

Your Palm® Treo™ 750 Smart Phone User Guide
Your Palm® Treo™ 750 Smart Device Intellectual property notices End user notice © 2006 Palm Inc. All rights reserved. Palm, Treo, and the Palm and NOTE The Voice Command application is not available in all Treo logos are among the trademarks or registered trademarks languages. See Setting up voice commands . owned by or licensed to Palm Inc. All other brand and product names are or may be trademarks of, and are used to identify products or ® ® services of, their respective owners. Microsoft Voice Command Version 1.5 for Windows Mobile This product is protected by one or more of the following United IMPORTANT Do not become distracted from driving safely if States patents: operating a motor vehicle while using Device Software. 7,007,239; 6,976,226; 6,975,304; 6,965,375; 6,961,567; 6,961,029; 6,957,397; 6,952,571; 6,950,988; 6,947,975; 6,947,017; 6,943,667; Operating certain parts of this Device requires user attention. 6,940,490; 6,924,752; 6,907,233; 6,906,701; 6,906,741; 6,901,276; Diverting attention away from the road while driving can possibly 6,850,780; 6,845,408; 6,842,628; 6,842,335; 6,831,662; 6,819,552; cause an accident or other serious consequences. Even occasional, 6,804,699; 6,795,710; 6,788,285; 6,781,824; 6,781,575; 6,766,490; short diversions of attention can be dangerous if your attention is 6,745,047; 6,744,451; 6,738,852; 6,732,105; 6,724,720; 6,721,892; diverted away from your driving task at a critical time. -
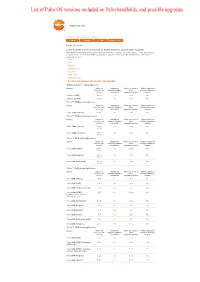
List of Palm OS Versions Included on Palm Handhelds, and Possible Upgrades
List of Palm OS versions included on Palm handhelds, and possible upgrades www.palm.com < Home < Support < Knowledge Library Article ID: 10714 List of Palm OS versions included on Palm handhelds, and possible upgrades Palm OS® is the operating system that drives Palm devices. In some cases, it may be possible to update your device with ROM upgrades or patches. Find your device below to see what's available for you: Centro Treo LifeDrive Tungsten, T|X Zire, Z22 Palm (older) Handspring Visor Questions & Answers about Palm OS upgrades Palm Centro™ smartphone Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Centro (AT&T) 5.4.9 No N/A No Centro (Sprint) 5.4.9 No N/A No Treo™ 755p smartphone Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 755p (Sprint) 5.4.9 No N/A No Treo™ 700p smartphones Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 700p (Sprint) Garnet Yes N/A No 5.4.9 Treo 700p (Verizon) Garnet No N/A No 5.4.9 Treo™ 680 smartphones Device Palm OS Handheld Palm OS version Palm Desktop & version (out- Upgrade/Update after HotSync Manager of-box) available? upgrade/update update Treo 680 (AT&T) Garnet Yes 5.4.9 No 5.4.9 Treo 680 (Rogers) Garnet No N/A No 5.4.9 Treo 680 (Unlocked) Garnet No N/A No 5.4.9 Treo™ 650 smartphones Device Palm OS -

User Guide Mobile Device Setup
USER GUIDE MOBILE DEVICE SETUP Merit Network, Inc. 1000 Oakbrook Drive, Suite 200, Ann Arbor, Michigan 48104-6794 Phone: (734) 527-5700 Fax: (734) 527-5790 E-mail: [email protected] TABLE OF CONTENTS - MERITMAIL, MOBILE DEVICE SETUP MeritMail Mobile Overview 3 Configuring a Windows Mobile 5 device 4 Configuring a Windows Mobile 6 device 5 Resetting your device 5-6 Why is a full resync necessary Performing a full resync Windows Mobile Palm devices (Versamail) Nokia symbian devices Other devices Setup for specific devices 7-13 Motorola Q Phone Nokia E51 Nokia E61 Nokia E62 Nokia E65 Nokia E90 Palm Treo 650 Palm Treo 680 Palm Treo 700w Palm TX Sony Ericsson P910i Sony Ericsson P990i Cingular 8525 Qtek A9100 Limitations 14 2 MeritMail Mobile Overview MeritMail Mobile is the MeritMail synchronization program that provides ‘over-the-air’ mobile data access (email, contacts, calendar) to devices using the native software / UI installed on the device. It works with Symbian S60/S80, Windows® Mobile (WM5), and Palm smartphones. Devices listed below can be configured to work with MeritMail Mobile out of the box. Many more devices work with MeritMail Mobile natively but a sync plug-in is not bundled with the device (plug-in is available via a 3rd party - DataViz). You enable MeritMail Mobile in the ZCS COS or for individual Accounts. Users configure the device’s soft- ware for MeritMail Mobile similarly to how they configure the device to sync against Microsoft® Exchange. The following may need to be configured: . Server address. Type the fully qualified hostname of the user’s MeritMail Collaboration Suite mailbox server. -

44 43% 25% 37% 14
MobileDevices Q Creating Cases Cases as of 7/1/2010 Total from Last Week Cases Created, Year Ago to Date Average Per Day Now Year Ago Change this week 4.3 1.6 173% last 3 months 2.4 1.4 74% last 12 months 2.2 1.9 16% 118 44 Actual Per Day, Last Week vs Qtrly Average 72 76 10 64 70 70 70 6 58 57 58 8 7 44 47 48 49 Last Week 6 4 3 3 Avg This Q 2 0 09 10 10 09 10 09 09 09 09 09 10 10 09 10 - - - - - - - - - - - - Mon Tue Wed Thu Fri Jul Oct Apr Jun- Jan Jun- Mar Feb Nov Dec Aug Sep May May * latest month is month-to-date The Queue Calendar Age of Open Cases Currently Pending Last 12 Months Last 3 months Last Week 100 100 100 14 50 50 50 11 10 4 2 1 1 1 1 1 2 2 more 10 7 4 1 13 11 9 7 5 3 1 7 6 5 4 3 2 1 months ago weeks ago days ago Time Since Last Activity of Any Kind, in Cases that are currently Open Last 12 Months Last 3 months Last Week 100 100 100 50 50 50 14 14 9 1 4 more 10 7 4 1 13 11 9 7 5 3 1 7 6 5 4 3 2 1 months ago weeks ago days ago Closing Cases Estimated Pending Queue over the last six months more than 7 days 80 70 43% 60 3 to 7 days 50 40 25% 30 < 3 days 20 10 37% 0 (over the last six weeks) 1/7 1/21 2/4 2/18 3/4 3/18 4/1 4/15 4/29 5/13 5/27 6/10 6/24 Net change in Q over six months: -4 Prepared by Rob Smyser 7/1/2010 Page 1 MobileDevices Q Cases as of 7/1/2010 Time Worked SyncML This Month SyncML Cases Created TimeWorked on SyncML cases 4.5 4 SyncML cases are software distributions to end-users. -

Palm OS Is One of the Most Popular Handheld Operating Systems on the Planet
Palm and Treo Hacks By Scott MacHaffie ............................................... Publisher: O'Reilly Pub Date: October 2005 ISBN: 0-596-10054-X Pages: 234 Table of Contents | Index Palm OS is one of the most popular handheld operating systems on the planet. From the newest Tungstens and Treos all the way down the family tree, Palms are everywhere. Although the Palm OS is simple to learn and use, there is more to it than meets the eye--from new features in the Palm to capabilities you can get with add-on software, the Palm can be made to do quite a lot. Palm and Treo Hacks gives you tips and tools that show you how to make the most of your Palm. A few minutes spent reading some of the hacks in this book will save you hours of research. Inside this book, you'll learn how to: Find great applications for your Palm and make the most of the ones you're using now Get super-organized, getting more from the built-in Personal Information Manager and learning how to manage complex projects with your Palm Extend the Palm with must-have software and hardware add-ons Take your Palm online, reading email, surfing the web, and sending instant messages Get some rest and relaxation with your Palm, whether it's listening to music, playing classic games, or watching video Written for beginning to experienced Palm users, Palm and Treo Hacks is full of practical, ingenious tips and tricks you can apply immediately. Whether you're looking to master the built-in applications or you want to trick out your Palm to its fullest extent, this book will show you how to get it. -

Noviiremote Deluxe for Palm OS ®, Ver 3.5 User's Guide
__________________________________________________________ For Palm OS Devices NoviiRemote turns your handheld computer into a Universal Learning Remote Control! You can control all of your home entertainment equipment with one easy-to-use program. Table of Contents Introduction ...............................................................................................................................2 1. Getting Started......................................................................................................................2 2. Install NoviiRemote Deluxe...................................................................................................3 3. Setup Form ...........................................................................................................................4 4. Remote Screen Form............................................................................................................5 5. Add New Device Wizard .......................................................................................................7 6. Learning IR Codes................................................................................................................8 7. Hot Buttons Form................................................................................................................10 8. Hard Buttons Form .............................................................................................................12 9. Preferences for Multiple Rooms..........................................................................................14 -

For Smartphones?
15.912 TECHNOLOGY STRATEGY SPRING SEMESTER 2005 FINAL PAPER SHOULD MOTOROLA EMBRACE 100% THE LINUX OPERATING SYSTEM (OS) FOR SMARTPHONES? Silvia Battigelli Alberto Farronato Carlos Mazariegos 15.912 - Technology Strategy Final Paper 1. Introduction In a period when the market for mobile devices is changing and moving towards convergence of multiple products into one single device, it is time for the big players in all related industries to reconsider their strategy to capture more of the value that convergence will create. Motorola, the second largest manufacturer of mobile handsets, recently adopted a new open source OS in a completely new market, such as the one of smartphones in China, and the question is: should they strongly adopt the new standard in all of the new products and in all of the markets? We believe that the answer is yes, and in this paper we will explain why. 2. An Overview of Motorola Motorola was originally founded as the Galvin Manufacturing Corporation in 1928 by Paul V. Galvin and his brother Joseph E. Galvin in Chicago, Illinois. Galvin Manufacturing Corporation's first product was a battery eliminator, a device that allows battery-powered radios to run on standard household electric current. In the 1930’s the company introduced one of the first commercially successful car radios and a single-frequency mobile radio receiver for police broadcasts. The company had just entered into the new field of mobile radio communications with net annual sales of $287,256. In the 1940’s, after Galvin Manufacturing Corporation becomes Motorola and offers first public stock, and into the 1950’s Motorola kept growing with new technological and commercial innovations in radio devices, television and personal pagers.