Shivaji University Kolhapur (M.S.)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CHAPTER: ± PETE YADGAON: HISTORY AMP INDUSTRIAL BACKGROUND. 1.1 LOCATION of PETE YADGAON: Peth Tadgaon Is Situated 20 K.M. T&Am
CHAPTER: ± PETE YADGAON: HISTORY AMP INDUSTRIAL BACKGROUND. 1.1 LOCATION OF PETE YADGAON: Peth Tadgaon is situated 20 K.m. t&; the north-east of , * Kolhapur* It is a small town in Hatkanangle Taluka of Kolhapur District# " Kolhapur-Yadgaon road breaks away from ' 1 ' / Pune-Bangalore National High-way npar Top* As there is a road joining Vadgaon-Hatkanangle; Vadgaon is also connected with Sangli and lohalkaranji. The west road links 'Malkapur, Ratnagiri eto* Thus Yadgaon is trafically linked with hig •1 cities.'* The location of Yadgaon in Maharashtra is shown in figure 1* K — 1*2 HISTORICAL BACKGROUND OF PETH YADGAON: Yadgaon is having different names which are explained i here. Mhile entering Yadgaon, you come across big bunyan trees. Every enteranoe to vadgaon is guarded by these tall trees, as if they are placed there to Wel-come the Visitors. As Yadgaon is situated on low lying land, from a distance you l can only see these bunyan trees. Thus the name Yadgaon is derived from two words "Vad” means bunyan tree and ” gaon" \ means town. Yadgaon is called as Kasaba Yadgaon. As there is a big market of grains, clothes and cattles it is also called as Bazar or Peth Yadgaon. M Yadgaon is known as a famous Fia. 1 2 market place, So the adjective Peth (market place) comes before Tadgaon. Kings liked this town and used to spend some time here, so some time call it 'Rajache* means King's 'Tadgaon, So Kasaba, Peth or Bazar and Raj ache Tadgaon is 2 still known by these three names," As far as the historical background of Peth Tadgaon is concerned, it has been noted that " during the^egiail of "7 Sambhaji ( ,1712-1760) Tadgaon was favorite residence of the Kolhapur family and had a strong detachment of horse. -

KURANE CHANDRAKANT PARASHARAM 2 Educational Qualification : MA, M.Phil, P
Photo PERSONAL PROFILE PERSONAL INFORMATION: 1 Name : KURANE CHANDRAKANT PARASHARAM 2 Educational Qualification : M.A., M.Phil, P.hD. 3 Subject : History 4 Area of specialization : History of Maratha 5 Designation : Associate Professor 6 Date of Birth : 07/01/1966 7. Gender Male 20/06/1990 9. Date of Retirement : 8 Date of Appointment : – 30/01/2026 10 Address : - Office Address Gopal Krishna Gokhale College, Subhash Road, Kolhapur – 416 008. : Residential Address : Rajgruh Plot No.9/A, Shivtej Colony, Near Shriram Petrol Pump, Kasaba Bavada, Kolhapur 416 006. – 11. Phone Number Mobile : 9960994794 Resi. : - : Office : 0231-2642540 12. E-mail : [email protected] 13. Hobbies : Reading A) EDUCATIONAL QUALIFICATION: Exam. Board/ Percentage Subjects Year Passed University / Grade Pune Board Marathi,Hindi,Eng, S.S.C. Mar-82 IInd Class Maths, Sci. Marathi, English, Pune Board H.S.C. Sociology, Psychology. Mar-84 Pass class Politics, Geo. Shivaji University, June- B.A. Kolhapur. History IIndCclass 1987 Shivaji University, June- IInd Class M.A. History Kolhapur. 1989 B+ Page 1 of 9 Shivaji University Life & work of May- M.Phil. B Grade Dadasaheb Shirke. 1994 Dalit Movement in Shivaji University Kolhapur State & Dec. Ph.D. Kolhapur District 1894 2011 to 1970. Modi Script Government of Exam Pass Maharashtra B) RESEARCH EXPERIENCE & TRAINING: Research University where the Completed Title of work/Theses Stage work was carried out, Year & Grade M.Phil. - - - Ph.D. - - - C) RESEARCH PROJECTS CARRIED OUT (MAJOR/MINOR) FUNDED BY GOVT./NGO/INDUSTRY Name of the Funds Academic Title of the Project funding Received Remarks Year Agency In Rs. - - 1 - - - - - 2 - - - D) DETAILS OF THE REFRESHER/ORIENTATION/SHORT TERM COURSES ATTENDED Orientation/ Refresher Course Name of ASC / University Date 1 Orientation Course Tata Institute of Social Science, Mar-11 to Page 2 of 9 Mumbai. -

Form IEPF-2 2012-13
Note: This sheet is applicable for uploading the particulars related to the unclaimed and unpaid amount pending with company. Make sure that the details are in accordance with the information already provided in e‐form IEPF‐2 CIN/BCIN U65191PN1943PLC007308 Prefill Company/Bank Name RBL BANK LIMITED Date Of AGM(DD‐MON‐YYYY) 30‐AUG‐2013 Sum of unpaid and unclaimed dividend 1153291.00 Sum of interest on matured debentures 0.00 Sum of matured deposit 0.00 Sum of interest on matured deposit 0.00 Sum of matured debentures 0.00 Sum of interest on application money due for refund 0.00 Sum of application money due for refund 0.00 Redemption amount of preference shares 0.00 Sales proceed for fractional shares 0.00 Validate Clear Proposed Date of Investor First Investor Middle Investor Last Father/Husband Father/Husband Father/Husband Last DP Id‐Client Id‐ Amount Address Country State District Pin Code Folio Number Investment Type transfer to IEPF Name Name Name First Name Middle Name Name Account Number transferred (DD‐MON‐YYYY) WARD NO‐10, H.NO‐2374, MAIN ROAD, ICHALKARANJI DIST‐ RBL00000000000003 Amount for unclaimed and ABDAN KUBER MALLAPPA NA KOLHAPUR ICHALKARANJI INDIA Maharashtra 416115 979 unpaid dividend 30.00 02‐Nov‐2020 C/O HARSHAL MATERNITY AND NURSING HO 1ST FLR PARMANAND APARTMENT NEAR DAMODARBHAGW INDORA SQUARE KAMPTEE ROAD IN300360‐10348486‐ Amount for unclaimed and ABHIJIT DAMODAR GAURKHEDE ANGAURKHEDE NAGPUR MAHARASHTRA INDIA Maharashtra 440017 0000 unpaid dividend 719.00 02‐Nov‐2020 YOGESHBRIJENDR VIVEKANAND COLONY, MANE 12028900‐00057040‐ -

056 Mr Patil Arun Pandurang F
LIST OF CORPORATE MEMBERS ATTACHED TO KOLHAPUR LOCAL CENTRE AS ON 31 MAR 2020 F-125147-5 AG/ 056 M-134081-0 AG/ 056 MR PATIL ARUN PANDURANG FIE MR AJAY BHASKAR DESHPANDE MIE S-4 SHIVNNERI TOWERS R-9 ATHARV AYODHYA PARK 8TH LANE 2019 KH TARARANI CHOWK RAJARAMPURI KAWALA NAKA KOLHAPUR KOLHAPUR (M.S.) 416008 416005 Email: [email protected] Email: [email protected] Mobile: 9960729333 Mobile: 9403600034 M-134573-1 AG/ 056 M-148259-3 AG/ 056 MR PATIL MAHESH PANDURANGRAO MIE MR PRAVIN DHANGOPAL UKEY MIE 203 HR - 1 ROYAL RETREAT GANESH APARTMENT NEAR RUIKAR COLONY NR POST OFFICE BHAJI MARKET KOLHAPUR AT/PO- PETH VADGAON MAHARASHTRA TAL- HATKANANGALE , DIST- KOLHAPUR 416001 416112 Email: [email protected] Email: [email protected] Mobile: 7588470031 Mobile: 9923671433 M-156836-6 AG/ 056 AM094760-4 AG/ 056 MR RATHOD SHRIMANT DHIRU MIE MR JADHAV KISHOR DINKAR AMIE AGRICULTURAL RESEARCH STATION HOUSING COLONY NARP KASABE DIGRAJ A/P KODOLI TAL PANHALA TAL MIRAJ DIST KOLHAPUR DIST SANGLI MAHARASHTRA 416305 416114 Email: [email protected] Email: Mobile: 9850236103 Mobile: AM094762-0 AG/ 056 AM094763-9 AG/ 056 MR GURAV GAJANAN BHIMRAO AMIE MR PATIL SUHAS BAPUSO AMIE A/P KODOLI A/P BHADOLE TAL PANHALA TAL HATKANANGALE DIST KOLHAPUR DIST KOLHAPUR 416114 416112 Email: [email protected] Email: [email protected] Mobile: Mobile: 9823381191 AM094909-7 AG/ 056 AM148965-0 AG/ 056 MR GATADE AMOL BABANRAO AMIE MR GHATGE JAYANT SARJERAO AMIE NEAR POST OFFICE HOUSE NO 123 A/P PETH VADGAON HOUSING SOCIETY KODOLI TAL HATAKNANGALE -

Re-Accreditation Report
Dr. Babasaheb Ambedkar Mahavidyalaya, Peth Vadgaon Dist Kolhapur (M.S.) RE-ACCREDITATION REPORT SUBMITTED TO NATIONAL ASSESSMENT AND ACCREDITATION COUNCIL (NAAC), BANGALORE FOR INSTITUTIONAL RE-ACCREDITATION BY JAYPRAKASH EDUCATION SOCIETY’S DR. BABASAHEB AMBEDKAR MAHAVIDYALAYA BR. TATYASAHEB MANE VIDYANAGAR PETH VADGAON, DIST. KOLHAPUR (M.S.)-416112 PRINCIPAL 1 RAR Dr. Babasaheb Ambedkar Mahavidyalaya, Peth Vadgaon Dist Kolhapur (M.S.) INDEX Sr. Content Page No. No. 1 NAAC Steering Committee 4 2 Preface 5-6 3 Principal’s Message 7 4 8-10 A. Executive Summary 5 11-22 B. Profile of the Affiliated College 6 23-156 C. Criterion-wise Analytical Report 23-41 Criterion I: Curricular Aspects 42-64 Criterion II: Teaching-Learning and Evaluation 65-82 Criterion III: Research, Consultancy and Extension 83-101 Criterion IV: Infrastructure and Learning Recourses 102-121 Criterion V: Student Support and Progression 122-141 Criterion VI: Governance, Leadership and Management 142-156 Criterion VII: Innovations and Best Practices 7 157-200 D. Evaluative Reports of the Departments Department of English 157-161 Department of Economics 162-166 Department of Sociology 167-171 Department of History 172-176 Department of Geography 177-181 Department of Marathi 182-186 Department of Political Science 187-190 Department of Commerce 191-195 Department of BCA 196-199 2 RAR Dr. Babasaheb Ambedkar Mahavidyalaya, Peth Vadgaon Dist Kolhapur (M.S.) Other Subjects 200 8 201-202 E. Post-accreditation Initiatives 9 203 F. Declaration by the Head of the Institution 10 G. Annexure 204-232 I: Approval of Courses of Affiliating University 204 II: UGC 2(f) and 12B certificate 205 III: Letter of Permanent Affiliation 206-207 IV: Certificate of last Accreditation 208 V: Audited Income and Expenditure Statement 209-215 VI: Letter of Grant Received Recently from UGC 216 VII: Master Plan of the Campus Area 217-219 VIII: Peer Team Report 220-232 11 233-237 H. -

Youth Development Co-Op. Bank Ltd.,Kolhapur
YOUTH DEVELOPMENT CO-OP. BANK LTD.,KOLHAPUR List of Dormant Accounts which is non operative for 10 years and above (DEAF) Please contact Bank to make it operative Note - To search a specific name please press Control F button of your computer SR.NO. NAME ADDRESS Flat No.5,Pallavi Apartment,Nalala Park,KOlhapur. 1 ARALEKAR DASHARATH N AND RAMCHANDRA D KOLHAPUR Flat No.5,Pallavi Apartment,Nalala Park,KOlhapur. 2 ARALEKAR DASHARATH N AND RAMCHANDRA D KOLHAPUR 3 DHEKALE DINKAR SAKHARAM. At Post Rashiwade,Tal. Radhanagari,Dist.Kolhapur. AT-POST-K.BORGAON,TAL-PANHALA,DIST. 4 PATIL VITTHAL ABA. KOLHAPUR. 5 URUNKAR PRADEEP MURLIDHAR . 2331, C WARD,SHANIWAR PETH,KOLHAPUR. 6 PAWAR SHRIPAD VASANTRAO. 2250,B,MANGALWAR PETH,KOLHAPUR.KOLHAPUR VISHALGADKAR HOUSING COMPOUND, 7 PATIL AVINASH VISHWASRAO. KOLHAPUR.KOLHAPUR 1325/37,B,SHIVAJI UDYAMNAGAR,KOLHAPUR. 8 DESAI RAGHUNATH DATTOBA. KOLHAPUR 9 GAIKWAD RAMCHANDRA MARUTI. 1424/C, LAXMIPURI,KOLHAPUR.KOLHAPUR 10 MOMIN IBRAHIM MIRASAHEB. 2239/C,SOMWAR PETH,KOLHAPUR.KOLHAPUR 1944/C, SOMWAR PETH, LAXMIROADKOLHAPUR. 11 KARIGAR ABDULRASID ABDULMAJID. KOLHAPUR 12 PAI NIRANJAN SHESHGIRI. 2547/B,MANGALWAR PETH,KOLHAPUR.KOLHAPUR 260/E,DAPHALE HOUSE,TARABAI PARK, 13 DHAPALE CAP.RAJENDRA VIJAYSINGH. KOLHAPUR. 1842 "C" WARD,SOMWAR PETH,KOLHAPUR. 14 PAWAR BALKRISHNA BABASAHEB. KOLHAPUR 680/E,SHAHUPURI, 2ND LANE,NIMBALKAR BULDG., 15 PANCHAL JAGADISH UTTAMRAO. KOLHAPUR. 16 SARAWATE VILAS GOVINDRAO. 2394,D, SHUKRAWAR PETH,KOLHAPUR.KOLHAPUR 17 KHOCHAGE SUMITRA APPASAHEB. 1004/19 "A", NEWMAHADWAR ROAD,KOLHAPUR. 18 BARASKAR MAHANMAD YUSUF YASIN. 1040 "D" WARD,SHANIWAR PETH,KOLHAPUR. 1888 "D" WARD, SHANIWAR PETH,KOLHAPUR. 19 BARASKAR HURAMATBI YUSUF. KOLHAPUR 20 PATIL SURYAKANT BAPURAO. -

Personal Report 2018-19 Dr. Atigre Rajaram Hindurao 1. AWARDS And
Personal Report 2018-19 Dr. Atigre Rajaram Hindurao 1. AWARDS and FELICITATIONS: - I. Honoured with “Best Teacher Award” by Lions International’s, ‘Lions Club of Kolhapur’ on 22nd October 2016 II. Felicitated by Vadgaon Municipal Corporation for obtaining Ph. D. Degree in Zoology on Friday, 26- 01- 2018 2. RESEARCH PUBLICATION: - I. Bakare R. V., R. H. Atigre and S. R. Patil (2012), “Biodiversity of free living fresh water Protozoans in lentic and lotic ecosystems around Wai, Dist. Satara, MS, India.” International journal ‘World Genius’ Volume-1, Issue-2, Pp 31-35, ISSN NO. 2277-8381 II. Atigre R. H. and S. R. Patil (2012), “Hydrography of Bhose MI water tank, Bhose, Dist. Sangli, MS, India.” ‘Thematics Journal of Zoology’, Volume-1, Issue-3, Pp 15-17, ISSN NO. 2277-2960. III. Atigre R. H., S. R. Patil and C. B. Mane (2012), “Seasonal Variations in Some Physical Parameters of Bhose MI Water Tank, Bhose, Dist. Sangli, M.S, India” ‘Journal of Science Information’ Volume-3, Issue-1, Pp 64- 67, ISSN NO. 2229-5836. IV. Patil Sarjerao R., R. H. Atigre and S. V. Patil (2012), “First record of Mugger crocodile Crocodylus palustrius (Lesson, 1831) from river Kadavi at Sarud, Tal Shahuwadi, Dist. Kolhapur, MS, India.” ‘International Proceedings of CBEES’s Agriculture and Animal Science’, organized by Chemical, Biological and Environmental Engineering Society, Hong Kong at Bangkok, Thailand, Volume-47 Pp 100-104, ISSN NO. 2010-4618. V. Mane C. B. and R. H. Atigre (2012), “Role of Ionic Liquids in Green Chemistry” ‘Counter-View’ Volume-1, Issue-4, Pp 72-76, ISSN NO. -

New Jan to June 2020.Cdr
COLLEGE Of AGRICULTURE TALSANDE NEWS LETTER January – June 2020 Volume 05, Issue No. 01 Dr. D. Y. Patil College of Agriculture, Talsande College Code : 11141 For Admission 2020-21 - 9637605606/7066944959 SPECIAL EVENTS Poster Presentation Competition on “AGRICULTURE & TECHNOLOGY” On the occasion of birthday of Hon'ble Chairman Dr. Sanjay D. Patil Sir, DYP Agriculture campus Talsande along with Technical campus Talsande organized poster presentation competition on Agriculture & Technology. Total 108 students from all over Maharashtra participated in this event. Themes of this event were Dairy and food technology, Engineering and Technology, Architecture and Agri. & Food startups. The event was an opportunity for the students to unite their knowledge with their creative streak and express their views using the colors of imagination. This event was graced by Chief Guest Mr. Manas Mehta, CEO, Sphurti Dairy, Kolhapur to appear for this examination. 2) Selection of students in University team and ICAR team Following students of our college selected in University team 1. Tushar S. Deshmukh – Kho-Kho (M) 2. Pooja S. Magdum – Kho-Kho (W) 3. Sneha M. Mali – Kho-Kho (W) 4. Pallavi M. Sabale – Volley Ball (W) 5. Vaibhavi M. Mahadik – Kabaddi (W) University team Pooja S. Magdum – Kho-Kho (W) Selected as a team Member of Kho – Kho (All India Inter Agriculture University Sports and Game Meet 2019-2020 ). Winner National level tournament 3) Online photography Our second year student Ms. Soniya Patil got 1st prize in Online Photography held at SPARDHA - 2020, VAMNICOM, Pune on 16th February, 2020. STUDENT ACHIEVEMENTS 1) MCAER achievement : PG entrance test Our 30 students got rank in first 1000 students for M.Sc. -
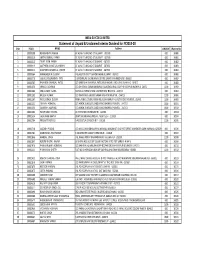
Statement of Unpaid & Unclaimed Interim Dividend for FY 2019-20
INDIA GLYCOLS LIMITED Statement of Unpaid & Unclaimed Interim Dividend for FY2019‐20 S No FOLIO NAME Address AMOUNT Warrant No 1 00000108 RENUKA BIPIN PARIKH AT ALINA TA NADIAD ST GUJARAT ‐387305 600 30480 2 00000110 SMITA PARIMAL PARIKH AT ALINA TA NADIAD ST GUJARAT ‐387305 600 30481 3 00000112 TRUPT JATIN PARIKH AT ALINA TA NADIAD ST GUJARAT ‐387305 600 30482 4 00000113 LASTYBEN JAYANTILAL PARIKH AT ALINA TA NADIAD ST GUJARAT ‐387305 600 30483 5 00000114 MALTYBEN JAYANTILAL PARIKH AT ALINA TA NADIAD ST GUJARAT ‐387305 600 30484 6 00000364 KAMALABEN M GURJAR VILLAGE POR DISTT GANDHINAGAR GUJARAT ‐382421 600 30486 7 00000378 GOKALDAS SOMABHAI PATEL 5 SARDARKUNJ SOC NR BAHAI CENTRE SHAHPUR AHMEDABAD ‐380001 600 30487 8 00000587 PASHIBEN ISHVARLAL PATEL C/O BABU BHAI ISHVARLAL PATEL KRISHNASARU IIND LANE UNJHA N G ‐384170 600 30488 9 00001152 URMILA AGARWAL C/O SH KESHAV SARAN AGARWAL VILLAGE KACHNAL GAZI P O KASHIPUR KASHIPUR ‐244713 1200 30492 10 00001182 ANIL KUMAR GURIA MOHALLA RAHEM KHANI KASHIPUR DIST NAINITAL ‐244713 600 30494 11 00001192 BRIJESH KUMAR C/O RAM NIWAS SHIVRAJ SARAN KASHIPUR NAINITAL ‐244713 1200 30496 12 00001207 PHOOL SINGH DOGRA RAMA AGRICULTURAL FARM VILLAGE KHAMRIA P O BAZPUR DIST NAINITAL ‐262401 1800 30498 13 00001231 GAVRAV AGRAWAL C/O ASHOK JEWELLERS SABZI MANDI KASHIPUR NANITAL ‐244713 1800 30501 14 00001232 SAUARBH AGARWAL C/O ASHOK JEWELLERS SABZI MANDI KASHIPUR NANITAL ‐244713 1800 30502 15 00001604 FAQIR SINGH BHATIA 29 JYOTI PARK GURGAON HR ‐122001 600 30503 16 00001654 SALIG RAM BHATIA B6/47 SAFDARJANG -
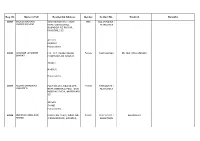
Reg. No Name in Full Residential Address Gender Contact No
Reg. No Name in Full Residential Address Gender Contact No. Email id Remarks 40001 SHUKLA RAJMANI JANBHAGYODAYA CHAWL Male 022 28704928 / JAGDISHPRASAD KAMETI NANJIWADI, 9619503869 GAONDEVI RD POISAR, KANDIVALI (E) 400101 MUMBAI Maharashtra 40002 KHARABE JAYSHREE P.N. 117, ULHAS NAGAR Female 09438267463 PH. NO. 0712-2745880 SHARAD MANEWADA RD NAGPUR 440027 NAGPUR Maharashtra 40003 KEDARI SARASWATI FLAT NO.103, RIDDHI APT. Female 8983442510 / JANARDEN NEAR JONDHALE POLE TECH, 8446348463 MORIVALI PADA, AMBERNATH (E) 421501 THANE Maharashtra 40004 MUKADAM ASMA RAFI BLOCK NO. 5/A/5, ROAD NO. Female 9222161823 / 9664908761 AHMED 8 BAIGANWADI, GOVANDI, 9920870355 400043 MUMBAI Maharashtra 40005 MISTRY RASHMI BLOCK NO.7, PRATHAMESH Female 28386396 / CHANDRAKANT APT DEOLWADI, NR. SAHAR 9324906120 RD CHAKALA, ANDHERI(E) 400099 MUMBAI Maharashtra 40006 SINGH BABITA DIWAKAR FLAT NO.410, MIT NIKETAN Female 022 28701024 / TOWER OPP.90FEET ROAD, 9867396844 THAKUR COMPLEX, KANDIVLI (E) 400101 MUMBAI Maharashtra 40007 SHETTY DEEPA SANJEVA 204, RLA TOWER TANK RD Female PH. NO. 022-25952941 BHANDUP(W) MUMBAI 400078 MUMBAI MAHARASHTRA 40008 CHANDIWADE SHRIKANT A/P - LAVEL, TAL - KHED Male 9422595982 RAMCHANDRA 415708 RATNAGIRI Maharashtra 40009 BHALE MADHAVI MAHSUL COLONY, NR NEW Female 9422396506 / RENEWAL UP TO 2015 PRABHAKARRAO BUS STAND, NR JUJGAR 9422337341 HOSPITAL, MAJALGAON 431131 BEED Maharashtra 40010 POL AMOL BHASKAR A/P=DOMGAON, TAL- Male 9527213713 PARANDA DIST-OSMANABAD 413202 USMANABAD Maharashtra 40011 KASTURE SUCHITA SHARDA NAGAR, DEGLOOR Female PH. NO. 9423485733 DEFAULTER SURYAKANTRAO KRISHI DHAN NIWAS NEAR DHAGE , TAL-DEGLOOR NANDED 431717 NANDED MAHARASHTRA 40012 OMBASE MANOJ AT-DHAKANI, PO-DIWAD TAL- Male 8380802882 RAMCHANDRA MAN, 415509 SATARA Maharashtra 40013 SHIRKANDE RAHUL C/O POOJA Male 9766923235 MURLIDHAR RESIDENCY,ANAND NAGAR COLONY,NEAR NH-4 OVER BRIDGE (W), GODOLI 415001 SATARA Maharashtra 40014 GAVADE NAYANESH NITIN CLINIC, A/P - ARAWALI Male 02366 227052 / NAMADEV TAL - VENGURLA 9764593184 416518 SINDHUDURG Maharashtra 40015 HARER PADMAJA GOVT. -

Reg. No Name in Full Residential Address Gender Contact No
Reg. No Name in Full Residential Address Gender Contact No. Email id Remarks 35001 KAWISHWAR AJINKYA "YUGANTAR, TILAK NAGAR Male 07263 252705 / 9822567483 RENEWAL UP TO 24/03/2018 VIRENDRA ZUNZUNWAL PLOT, KHAMGAON 252360 444303 BULDHANA Maharashtra 35002 HASHMI SYEDA FATIMA H.NO -716, BEHIND KARI Female 0241 2347661 / RENEWAL UP TO 24/03/2018 SYED AHMED MOHIUDDIN MASJID, ZENDI GATE, 9763389079 414001 AHMEDNAGAR Maharashtra 35003 JAYKAR ATUL TULSHIDAS AT POST - KEDGAON, TAL-- Male 9890364177 / NOT RENEW DAUND 7588955085 412203 PUNE Maharashtra 35004 RAJPUT ISHWARSINGH A/P-LEHA, TAL-BHOKARDHAN Male 02485--248035 DEFAULTER HARISHCHANDRA DIST-JALNA NAME REMOVED JALNA MAHARASHTRA 35005 MIRAJGAONKAR KETAKI BEHIND TELEPHONE BHAVAN, Female 0240-2352637 / NOT RENEW PRAFULLA AJAB NAGAR, KRANTI CHOWK, 9423782362 AURANGABAD 431001 AURANGABAD Maharashtra 35006 THAKARE MOHASINA SHRIHARI NAGAR, ARJUN NAGAR Female 9923681768 / RENEWAL UP TO 2018 SANJAY NAGPUR ROAD, TAL- AMRAVATI, 9422779944 444603 AMRAVATI Maharashtra 35007 KADU VAISHALI MR DNYANESHWAR B. Female 9921607869 [email protected] NOT RENEW GANGADHARRAO PATHARKAR H- 401, UJWAL TERRACES, RAJKAR NAGAR, DHAYRI 411041 PUNE Maharashtra 35008 ARALEKAR VIKRAM E-G 22/95, SANKAPAL NAGAR, Male 0231 2601660 / NOT RENEW ANANDRAO KASABA, BAWADA, KOLHAPUR 9822601680 416006 KOLHAPUR Maharashtra 35009 BACHATE SAGAR A/P - KUDITRE, TAL - KARVEER Male 9921392185 NOT RENEW PRABHAKAR KOLHAPUR Maharashtra 35010 PATIL PRAVEEN MAIIGILT HOSPITAL, WAGHBILL, Male 9595187177 / NOT RENEW PANDURANG NEAR FORT ACADEMY, -

I.O.N to O.E. - 4 Section SHIVAJI UNIVERSITY, KOLHAPUR Date : 02/06/2017
I.O.N to O.E. - 4 Section SHIVAJI UNIVERSITY, KOLHAPUR Date : 02/06/2017 Refund List for Accounts of B.E. Examination December 2016 After revaluation of the following papers as per existing rules, the candidate will be refunded following amount Sr. Reciept Receipt Refund App. No. Seat No. Student Name Address Payment Bank Name A/C No. IFSC Code No. Date No. Amount DKTE TEXTILE AND ENGG INSITUTE ICHALKARANJI - RAJWADA CHOWK - 1 336265 37333 GHORPADE SNEHA SHRIKANT ICHALKARANJI - 28/02/2017 43554 500 500 ICHALKARANJI - KOLHAPUR - - 416115 C/O NANASAHEB DESAI RENUKA NAGAR - MAIN ROAD 2 336301 31409 RAJMANE AMRUTA MADHUKAR KASABA BAWADA KOLHAPUR - 20/02/2017 103605 1000 500 - KOLHAPUR - KOLHAPUR - MAHARASHTRA - 416006 20/276 LIGADE MALA ICHALKARANJI - ICHALKARANJI - 3 336307 24780 JANTRE ARCHANA DILIP ICHALKARANJI - 28/02/2017 43554 500 500 ICHALKARANJI - KOLHAPUR - MAHARASHTRA - 416115 54/A SHUKRAWAR PETH PLOT NO 26 NEAR BADAMI VIHIR - 4 336334 32266 GHODKE SAISH GAJANAN SATARA - - SATARA - SATARA - 20/02/2017 43303 1000 500 MAHARASHTRA - 415001 SANJOT NIVAS, GANESHNAGAR POTDAR SAMIKSHA - SHIROL - - SHIROL - 5 336373 11160 28/02/2017 43554 500 500 SANJAYKUMAR KOLHAPUR - MAHRASHTRA - 416103 PUNDLIK BELGAOKER NEAR PRAKRUTI HOSPITAL - BIRANJE PANAD RATNADIP COLONY - 6 336399 37142 TIVALE KAVALJEET KIRAN KASABA BAWADA KOLHAPUR - 20/02/2017 103605 1000 500 KARVIR - KOLHAPUR - MAHARASHTRA - 416006 265 YADO GOPAL PETH SATARA 7 336404 35191 GHATGE KULDIP SUNILRAO - - - SATARA - SATARA - 28/02/2017 43506 1500 500 MAHARASHTRA - 415002 Page No : 1/410 I.O.N to O.E. - 4 Section SHIVAJI UNIVERSITY, KOLHAPUR Date : 02/06/2017 Refund List for Accounts of B.E.