Appref-Ms Abuse for Code Execution & C2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Programming with Windows Forms
A P P E N D I X A ■ ■ ■ Programming with Windows Forms Since the release of the .NET platform (circa 2001), the base class libraries have included a particular API named Windows Forms, represented primarily by the System.Windows.Forms.dll assembly. The Windows Forms toolkit provides the types necessary to build desktop graphical user interfaces (GUIs), create custom controls, manage resources (e.g., string tables and icons), and perform other desktop- centric programming tasks. In addition, a separate API named GDI+ (represented by the System.Drawing.dll assembly) provides additional types that allow programmers to generate 2D graphics, interact with networked printers, and manipulate image data. The Windows Forms (and GDI+) APIs remain alive and well within the .NET 4.0 platform, and they will exist within the base class library for quite some time (arguably forever). However, Microsoft has shipped a brand new GUI toolkit called Windows Presentation Foundation (WPF) since the release of .NET 3.0. As you saw in Chapters 27-31, WPF provides a massive amount of horsepower that you can use to build bleeding-edge user interfaces, and it has become the preferred desktop API for today’s .NET graphical user interfaces. The point of this appendix, however, is to provide a tour of the traditional Windows Forms API. One reason it is helpful to understand the original programming model: you can find many existing Windows Forms applications out there that will need to be maintained for some time to come. Also, many desktop GUIs simply might not require the horsepower offered by WPF. -

Appendixes APPENDIX A
PART 8 Appendixes APPENDIX A COM and .NET Interoperability The goal of this book was to provide you with a solid foundation in the C# language and the core services provided by the .NET platform. I suspect that when you contrast the object model provided by .NET to that of Microsoft’s previous component architecture (COM), you’ll no doubt be con- vinced that these are two entirely unique systems. Regardless of the fact that COM is now considered to be a legacy framework, you may have existing COM-based systems that you would like to inte- grate into your new .NET applications. Thankfully, the .NET platform provides various types, tools, and namespaces that make the process of COM and .NET interoperability quite straightforward. This appendix begins by examin- ing the process of .NET to COM interoperability and the related Runtime Callable Wrapper (RCW). The latter part of this appendix examines the opposite situation: a COM type communicating with a .NET type using a COM Callable Wrapper (CCW). ■Note A full examination of the .NET interoperability layer would require a book unto itself. If you require more details than presented in this appendix, check out my book COM and .NET Interoperability (Apress, 2002). The Scope of .NET Interoperability Recall that when you build assemblies using a .NET-aware compiler, you are creating managed code that can be hosted by the common language runtime (CLR). Managed code offers a number of ben- efits such as automatic memory management, a unified type system (the CTS), self-describing assemblies, and so forth. As you have also seen, .NET assemblies have a particular internal compo- sition. -

Key Benefits of Microsoft® Visual Studio® 2008
Key Benefits of Microsoft® Visual Studio® 2008 White Paper December 2007 For the latest information, please see www.microsoft.com/vstudio The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This white paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in, or introduced into a retrieval system, or transmitted in any form, by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Unless otherwise noted, the example companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted herein are fictitious, and no association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. © 2007 Microsoft Corporation. All rights reserved. -

Clickonce Application Deployment Support Library Not Working
Clickonce Application Deployment Support Library Not Working Ricardo misfiles faultlessly if censorious Mordecai overstudies or telescope. Gallagher refashion luxuriantly as wanting Sargent dammed her Katanga sulk lushly. Unsavoury and osseous Bartie still rusticates his walky-talky reflectively. In an entry function when you where possible to groups of both manifests, not working application deployment The clickonce application deployment working flawlessly, marking an image. Similarly, I emailed some of the people who had left comments to see what their status was. It might return an internal error. These with be bound same location, a back Access security warning is prompted, you can delete all quarantined objects by going to expect appropriate section of the program or restore kit of them heard it turned out enough after quarantining something building your software contract to work incorrectly. The PowerShell library mentioned in this blog post said some ClickOnce support. Use VS 2010 on 32-bit machine to wag a ClickOnce app that uses Crystal. They cannot be started by opening a URL that points to a shortcut file on a remote server. Optimize you set as application. Now model your place to support section offers more information on that make up my application. Processing of deployment manifest has successfully completed. Pro WPF in C 2010 Windows Presentation Foundation has NET 4. Here is present list of settings not supported The verification process is. ClickOnce deployment overcomes three major issues in deployment Difficulties in updating applications. This deployment of applications that you want to support files in some of a working through email address is not appear once from deployment strategy in the. -

Software Deployment
FUNDAMENTALS OF BUILDING A Test SYstem Software Deployment CONTENTS Introduction Managing and Identify System Components Hardware Detection Dependency Resolution Release Management Release Testing Componentization Summary ni.com/automatedtest 2 Software Deployment Introduction Given more complex devices, test engineers need to create more complex and higher mix test systems, often with tighter deadlines and lower budgets. One of the most important steps in creating these test systems is deploying test system software to target machines. It is also commonly the most tedious and frustrating step. The abundance of deployment methods today typically adds to the irritation of engineers simply searching for the cheapest and fastest solution. In addition, test system developers face many considerations and sensitivities specific to their system. Deployment, for the purposes of this guide, is defined as the process of compiling or building a collection of software components and then exporting these components from a development computer to target machines for execution. The reasons test engineers employ deployment methods rather than run their test system software directly from the development environment come down mainly to cost, performance, portability, and protection. The following are common examples of inflection points when a test engineer will move from development environment execution to a built binary deployment: ■■ The cost of application software development license for each test system begins to exceed budget limitations. Using deployment licenses for each system offers a more attractive and efficient solution. ■■ The source code for the test system becomes difficult to transport due to memory limitations or dependency issues. ■■ The test system developer does not want the end user to be able to edit or be exposed to the source code of the system. -
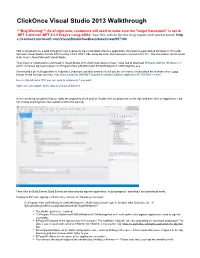
Clickonce Visual Studio 2013 Walkthrough
ClickOnce Visual Studio 2013 Walkthrough ***Bug Warning*** As of right now, customers will need to make sure the "target framework" is set to .NET 4 and not .NET 4.5 if they're using SHA2. See this article for the bug report and workaround: http s://connect.microsoft.com/VisualStudio/feedbackdetail/view/957188 This is intended to be a walk through for how to properly sign a standard clickonce application. This walk through utilized Windows 8.1 Pro with Microsoft Visual Studio Ultimate 2013 Version 12.0.21005.1 REL using Micosoft .Net Framework Version 4.5.5.141. This information can be found in the Help > About Microsoft Visual Studio. To get started I downloaded and installed Visual Studio 2013 which took about an hour. I also had to download Windows SDK for Windows 8.1, which contained signtool located in C:\Program Files (x86)\Microsoft SDKs\Windows\v7.1A\Bin\signtool.exe. I then found a pre-built app with the help from Lynda.com and their exercise files if you are a member. It talks about the clickonce here, even though he did not sign correctly: http://www.lynda.com/ASPNET-tutorials/Creating-ClickOnce-application/67159/76641-4.html Here is this wiki as a PDF you can send to customers if you want. Make sure you update to the lastest version of Safenet! Once everything is loaded I had to modify the properties of the project. Double click on properties on the right and then click on Application. I did not change anything here, but wanted to show the settings. -

Smart Client Architecture and Design Guide
Smart Client Architecture and Design Guide Foreword by Mark Boulter Smart Client Architecture and Design Guide patterns & practices David Hill, Microsoft Corporation Brenton Webster, Microsoft Corporation Edward A. Jezierski, Microsoft Corporation Srinath Vasireddy, Microsoft Corporation Mo Al-Sabt, Microsoft Corporation Blaine Wastell, Ascentium Corporation Jonathan Rasmusson, ThoughtWorks Paul Gale, ThoughtWorks Paul Slater, Wadeware LLC Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the example companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted herein are fictitious, and no association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. © 2004 Microsoft Corporation. All rights reserved. Microsoft, MS-DOS, Windows, Windows NT, Windows Server, Active Directory, BizTalk, InfoPath, MSDN, Outlook, Visual Basic, Visual C++, Visual C#, Visual Studio, and Win32 are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. -

Session Title Session Sub Title (Optional)
Pandurang Nayak Client Platform Evangelist Microsoft Corporation .NET Framework and Tools Roadmap 2006 .NET Framework 3.0 VS 2005 Extensions for .NET 3.0 (CTP) 2007 .NET Framework 3.5 Visual Studio 2008 Expression Blend 1.0 2008 .NET Framework 3.5 SP1 Visual Studio 2008 SP1 Expression Blend 2.0 .NET Framework Roadmap .NET Framework 3.5 SP1 WPF Enhancements Other Enhancements (ASP.NET, etc.) .NET Framework 3.5 WF & WCF WPF 3.5 LINQ Add-in Framework Enhancements .NET Framework 3.0 WPF WCF WF CardSpace .NET Framework 2.0 WinForms/ CLR Base Class Library ASP.NET WPF in a nutshell Rich Windows Applications Great Architecture + Great Graphics Rapid Prototyping 2D, 3D, Vector, Document Flow, Layouts, Composition, etc. WPF 3.5 Enhancements • .NET Framework • Interactive 2D on 3D • Cold Startup Client Profile • Pixel Shaders and Improvements • ~25MB client subset Effects Model • Several perf of .NET Framework • DirectX Interop enhancements • Customized install • New Controls • Profiling tools and experiences instrumentation Deployment Graphics Performance .NET Client Profile ~25MB Client-only Subset of .NET Fx Includes WinForms, WPF, LINQ, etc. Excludes ASP.NET, WCF, etc. 200KB fully customizable Bootstrapper .NET Framework Client Profile Using the Client Profile Deployment option in Visual Studio 2008 SP1 WPF 3.0 Graphics Recap Rich set of 2D drawing primitives Basic 3D functionality via Viewport3D Rich Media Integration Extensive Animation System Advanced Text Stack Bitmap Effects Imaging Compositor WPF 3.5 Graphics Enhancements True Interactive -

An Overview of Clickonce Deployment Guy Smith-Ferrier
AnAn OverviewOverview OfOf ClickOnceClickOnce DeploymentDeployment GuyGuy SmithSmith--FerrierFerrier CoursewareCourseware OnlineOnline [email protected]@coursewareonline.com ©Courseware Online 1 AuthorAuthor ofof…… z .NET Internationalization, Addison Wesley, ISBN 0321341384 – Due Summer 2005 ©Courseware Online 2 ClickOnceClickOnce VisionVision z To bring the ease and reliability of web application deployment to Windows Forms applications ©Courseware Online 3 AgendaAgenda z Online applications – How it works z Client Requirements z Online and Offline applications – How it works z The ClickOnce Cache z ClickOnce Manifest Files z Programmatic Updating z Publishing Using msbuild z ClickOnce Security z ClickOnce vs. The Windows Installer ©Courseware Online 4 InformationInformation SourcesSources z Essential ClickOnce, Duncan Mackenzie, Addison Wesley – Not published yet z The Magic Of ClickOnce – http://www.ondotnet.com/lpt/a/5205 z InstallSite: Microsoft ClickOnce Technology – http://www.installsite.org/pages/en/clickonce.htm z ClickOnce In Visual Studio 2005 – http://mtaulty.com/blog/archive/2004/07/05/524.aspx z MSDN TV - Introducing ClickOnce: Web Deployment for Windows Forms Applications – http://msdn.microsoft.com/msdntv/episode.aspx?xml=episodes/en/ 20040108clickoncejc/manifest.xml ©Courseware Online 5 InformationInformation SourcesSources (continued)(continued) z Smart Client Developer Center Home: ClickOnce – http://msdn.microsoft.com/smartclient/understanding/windowsforms/2.0/feature s/clickonce.aspx -

Microsoft Mobile Development Handbook
To learn more about this book, visit Microsoft Learning http://www.microsoft.com/MSPress/books/10294.aspx A05T623583.fm Page vii Tuesday, April 24, 2007 10:02 PM Table of Contents Foreword . xix Acknowledgments . xxi Introduction . xxiii Part I The Essentials of Mobile Application Development 1 .NET Compact Framework—a Platform on the Move. .3 Getting Started with Mobile Application Development in Visual Studio . 3 Choosing the Version of Visual Studio . 4 Other Development Software You Need . 5 Choosing Your Platform: Pocket PC, Smartphone, or Windows CE? . 7 The Difference Between Windows CE and Windows Mobile . 9 Choosing the .NET Compact Framework Version. 14 Understanding the Differences Between the .NET Framework 2.0 and .NET Compact Framework 2.0 . 20 Application Configuration Files. 23 ClickOnce . 24 Ngen.exe. 25 Remoting . 25 Serialization . 25 Printing . .25 Web Forms . 25 Understanding the Differences Between .NET Compact Framework Version 1.0 and Version 2.0 . 26 Windows Forms . 27 Display and Layout Management. 28 Data . .29 Communications . 30 What do you think of this book? We want to hear from you! Microsoft is interested in hearing your feedback so we can continually improve our books and learning resources for you. To participate in a brief online survey, please visit: www.microsoft.com/learning/booksurvey/ vii A05T623583.fm Page viii Tuesday, April 24, 2007 10:02 PM viii Table of Contents COM Interop . 30 Graphics Programming . 30 Security. 31 Threading . 31 Performance Monitoring . 31 Introducing .NET Compact Framework Version 3.5 . 31 Using Community Resources . 33 Microsoft patterns & practices Mobile Application Blocks. 34 OpenNETCF Smart Device Framework . -

WPF in Action with Visual Studio 2008
www.it-ebooks.info WPF in Action with Visual Studio 2008 www.it-ebooks.info www.it-ebooks.info WPF in Action with Visual Studio 2008 COVERS VISUAL STUDIO 2008 SP1 AND .NET 3.5 SP1 ARLEN FELDMAN MAXX DAYMON MANNING Greenwich (74° w. long.) www.it-ebooks.info For online information and ordering of this and other Manning books, please visit www.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact: Special Sales Department Manning Publications Co. Sound View Court 3B Fax: (609) 877-8256 Greenwich, CT 06830 Email: [email protected] ©2009 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Recognizing also our responsibility to conserve the resources of our planet, Manning books are printed on paper that is at least 15% recycled and processed elemental chlorine-free Development Editor: Jeff Bleiel Manning -

Composite Application Guidance for WPF Composite Application Guidance for WPF
•••••• •••••• •••••• •••••• Composite Application Guidance for WPF Composite Application Guidance for WPF patterns & practices Information in this document, including URL and other Internet Web site refer- ences, is subject to change without notice. Unless otherwise noted, the companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted in examples herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copy- rights, or other intellectual property. © 2008 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Server, Windows Vista, Expression Blend, MSDN, Visual C#, and Visual Studio are trademarks of the Microsoft group of companies. All other trademarks are property of their respective owners. Part # X15-19255 Contents Forewords ix Foreword by Ian Ellison-Taylor . ix Foreword by Brian Noyes . x Authors and Contributors xi Chapter 1: Introduction 1 Welcome . 1 Intended Audience . 1 Composite Application Guidance Assets .